Since the first ransomware attack in 1989, an attack on a healthcare organization that foreshadowed its richest target vertical, ransomware has evolved. First simple lockers infected individual computers, asking for paltry sums by today’s standards. Two years in the history of ransomware stand out: 2009 and 2019.
2009 is significant because that was the year Satoshi Nakamoto introduced the world to bitcoin and cryptocurrency. Let’s face it, even those of us who believe in the utility and math behind Bitcoin must admit that the cybercrime of ransomware would not be as prevalent today without this “financial instrument of trust.” According to Chainalysis, the cryptocurrency forensics company, crypto payments to ransomware attackers hit $449.1 million in the first half of 2023, up $175.8 million from the same period last year. To put those numbers in perspective, at the time of writing this, the entire market cap of Bitcoin is approximately $750 Billion dollars.
2019 is significant because that was the year ransomware evolved from simple lockers–but now infecting cloud networks–to the complex double-extortion of seizure and data exfiltration. We began to also see supply chain infections impacting hundreds, even thousands of unsuspecting victims all at once. The city of Baltimore remembers 2019 well.
2023 Another Watershed Year
According to a recent report by cyber underwriter Corvus Insurance, ransomware attacks continue at a record-breaking pace in 2023, with Q3 global ransomware attack frequency up 11% over Q2 and 95% year-over-year (YoY).1
1-Dark Reading, “2023 Ransomware Attacks Up More Than 95% Over 2022, According to Corvus Insurance Q3 Report”
Certainly attack volume continues to increase year over year, but what makes it a watershed year is the evolving sophistication of attacks, and the increasing potential of a single attack impacting multiple other organizations.
“2023 saw two of the largest third party or supply chain based ransomware events ever: MoveIT and CitrixBleed,” said Bill Bernard, Deepwatch VP Security Strategy. “In both cases actions taken by the impacted companies did not prevent PII, PHI, and other data from 3rd parties to those impacted companies being made publicly available. The legal repercussions of these breaches have yet to be resolved.”
A good example of this interconnectivity is the recent ransomware attack against the technology firm Treallance which caused widespread service impacts and directly damages 60 region credit unions.
“In the last few years ransomware tactics have moved away from smash and grab style attacks, to now more punishing attacks that exfiltrate and then encrypt. Double extortion has now morphed into double infection and double extortion,” said Neal Humphrey, Deepwatch AVP Market Strategy.
“Attackers can add another piece of ransomware to their droppers and increase their chances of success, lower the chances of defense, and cause additional complexity on the clean up, restoration and validation of impacted systems. Unfortunately it sounds like more paying victims. We expect to see more double double attacks in the new year.”
A Growing Ecosystem
Since 2019, in less than 5 years, ransomware has become a billion dollar industry, one that is lucrative not only to cybercriminals such as ransomware-as-a-service (RaaS) affiliates, access brokers, and dark data dealers, but also to an entire ecosystem of ransomware negotiators, cyber insurers, DFIR responders, and email filtering SaaS providers.
You can argue that cybersecurity is part of that ecosystem, and it’s true that Deepwatch combats ransomware for customers everyday. Unlike other security companies however, we are realistic about the problem of ransomware and prepare our customers to be resilient against it–to accept that given the continued rise in attacks and their sophistication, every large enterprise will have to deal with these attacks in the near future. There is no software solution, no training program, no automation alone that can currently stop them.
Each week, an average of 50 to 100 new victims appear on these websites–sites that have become so normalized they include professional branding efforts and victim customer service tools that would rival any legitimate enterprise.
Deepwatch reports on attacks each week in our Cyber Intelligence Brief. What are the top targets and ransomware types based on reporting?
Lockbit, CL0P, ALPHV, Black Basta, and Play have listed the most victims on their data leak sites in 2023.
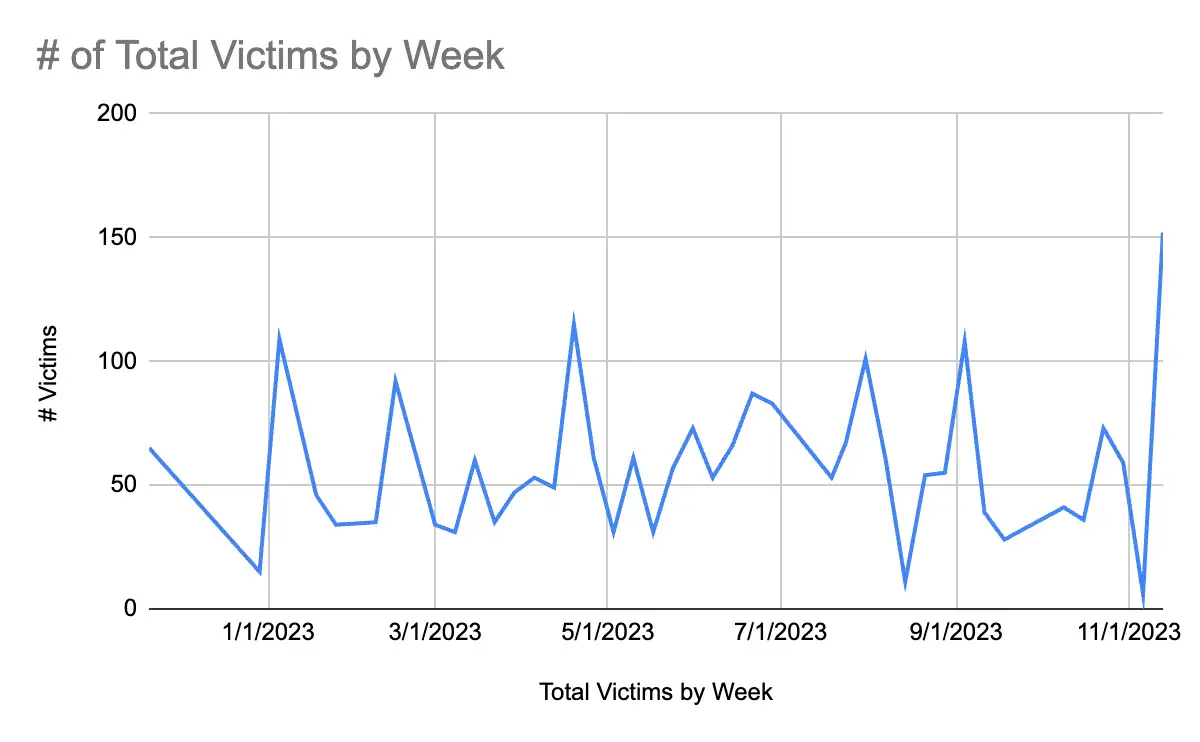
While not all victims can be verified, one thing is for sure: they’re not all of the ransomware victims in a given week. Threat actors use the data leak sites to pressure those victims who have yet to pay a ransom. Many more victims quietly pay the ransom and hope they can recover and purge their systems.
Law Enforcement Efforts in 2023
In June of this year, Ukrainian officials claimed to have taken down the CLOP ransomware gang’s infrastructure. In July CLOP began posting data stolen from the MOVEit vulnerability. Exploiting this zero-day allowed the threat actors to steal data from almost 600 organizations worldwide. With one zero-day vulnerability in MOVEit file transfer software, CLOP accounted for 13% of all ransomware victims in Q3.
Clop’s exploitation of a critical zero-day vulnerability (CVE-2023-34362) in Progress Software’s MOVEit Transfer is the third such effort ascribed to Clop targeting file transfer systems during the first half of 2023. They included the GoAnywhere incident in February and the PaperCut incident in April.
Has our collective response evolved to the threat of ransomware?
In March 2023, CISA rolled out the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA). This federal legislation requires critical infrastructure entities to report cyber incidents and ransom payments to CISA. What’s interesting here is that critical infrastructure companies will be notified that CISA knows something about their systems.
The Cyber Incident Reporting for Critical Infrastructure Act of 2022, directed entities in 16 critical infrastructures including financial services, information technology, energy, healthcare and public health, food and agriculture, critical manufacturing, chemicals, communications, defense industrial base, emergency services, to report ransomware no later than 72 hours after the affected entity reasonably believes that the covered cyber incident has occurred. The impacts of the Act have yet to be fully realized in 2023.
In May this year, the White House released an Executive Order aimed partly to address the ransomware challenge. The White House Executive Order on Improving the Nation’s Cybersecurity called for “bold action.” Of course, executive orders merely ask agencies to begin evaluation with some deadlines for response.
“The United States faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people’s security and privacy. The Federal Government must improve its efforts to identify, deter, protect against, detect, and respond to these actions and actors… the Federal Government must also carefully examine what occurred during any major cyber incident and apply lessons learned.” 2
2. White House Executive Order on Improving the Nation’s Cybersecurity
During the third annual International Counter-Ransomware Initiative summit in Washington, D.C. this month, an alliance of 48 countries signed a pledge to stop paying ransoms. Such pledges have been signed every year since 2019 by one group or another. The FBI long ago changed its stance from “never pay ransoms” to “well…”
Addressing reporters in October, Anne Neuberger, the White House’s Deputy National Security Adviser for Cyber and Emerging Technology, implied this initiative is in response to record ransomware risks worldwide, with the U.S. being the target of approximately 46% of these incidents.
Ransomware Review 2023 & 2024 Predictions
As a precursor to their annual threat report to be published in January, I asked the Deepwatch Adversary Tactics and Intelligence team and other Deepwatch experts to give us their thoughts on the state of ransomware in 2023, what we’ve seen in our own environment, and what we can expect in the coming year.
By the end of Q3, 2023 ransomware victim counts already surpassed what was observed for the entirety of either 2021 or 2022. If things continue on the current trajectory, this could be the first year with over 4,000 ransomware victims posted on leak sites, according to cyber insurer Corvus.
“Tactics employed to social engineer help-desk teams into providing elevated credential user accounts to bad actors have had disappointingly successful results in 2023,” said Bernard. “Certainly this should be a reminder to all organizations that cyber security cannot just be left to technology solutions, but must focus on and reinforce processes around critical but routine tasks such as password resets and MFA credential assignment.”
Has Ransomware-as-a-Service Evolved?
“All of the top 5 groups run RaaS programs. Lockbit likely has the highest number of affiliates. RaaS programs themselves, I think have matured to a point that significant evolutions are unlikely,” said Eric Ford of Deepwatch ATI. “The biggest evolutions will come from smaller operations. For instance, there is speculation that the actors behind Rhysida are the same ones behind Vice Society, but have evolved to the point where they are now using their own ransomware strain.”
Why is the US the biggest target? Is it that American corporations are more willing and able to pay, or that there is no way to arrest and stop threat actors?
“Probably a combination, but also the US likely has the most businesses (largest market). I don’t think this is something that can be easily answered without talking to the TAs themselves,” Ford said.
“Affiliates appear to target specific sectors because one: so many organizations fall under the North American Industry Classification System (NAICS) designations for manufacturing and professional, scientific, and technical services. Two: a disruption to those operations is detrimental, giving victims no recourse but to pay, or three: the reputational harm is so great it would drastically affect their business”
“This is why manufacturing and professional, technical, and scientific services are so highly targeted sectors. If a manufacturing plant can’t produce or accept orders they lose money and they usually seem to be smaller manufacturing firms, or customers where the perception of leaking customer data would greatly affect revenue (lawyers and investment firms). For PST Services, leaking of data, like customers or clients would adversely affect their reputation and potentially cause regulatory issues.”
Ford noted the challenge in classifying victims. “We also have to account for how a business is classified. Most businesses do not easily or completely fall into a single industry classification. For instance, a business that manufactures a product but also distributes the product to other retailers, and sells that product in their own branded retail stores. Are they a manufacturer, wholesale trade, or retailer? Depending on the business, they may not fall under the Management of Companies and Enterprises, as these could be departments and not separate entities.”
How important is the human element in combating ransomware?
“Tools are important but human analysts are critical. You can develop detections that cover most MITRE ATT&CK techniques, but there are so many ways to accomplish a specific technique that if you are not tracking TAs, their specific procedures to achieve a specific technique, and their targets, you’re bound to be a victim,” Ford concluded.
Let’s not forget 2017.
In a recent Deepwatch webinar, we spoke with famous hacker and cybersecurity professional Marcus Hutchins, who single-handedly thwarted the 2017 WannaCry attack that infected over 300,000 victims worldwide. Watch it on demand as we discuss the evolution of ransomware including double-distortion and ransomware-as-a-service—and the need for human-led cybersecurity efforts to improve your resilience to ransomware.
Share