Building and maintaining a modern security operations center (SOC) in-house is a dynamic and expensive endeavor. As the volume of log data grows, so must your team. As new threats emerge, the technology and time needed to find hidden vulnerabilities require continuous improvement and often additional investment.
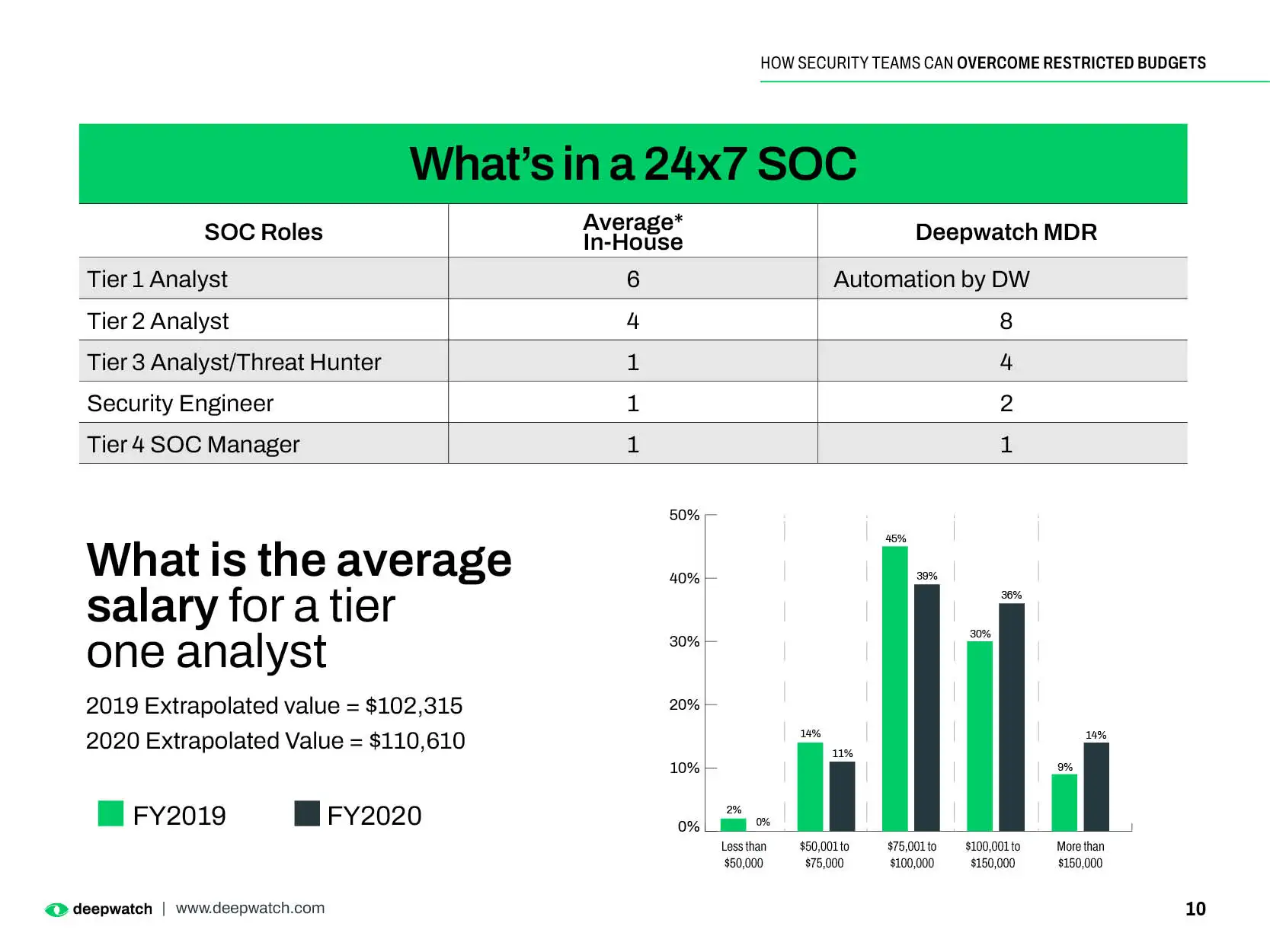
That investment can be expensive, particularly when it comes to headcount. Funding an in-house security team including management, analysts, security engineers, and threat hunters with the necessary expertise and experience often eclipses seven figures in salaries alone, to say nothing of retention and training costs.
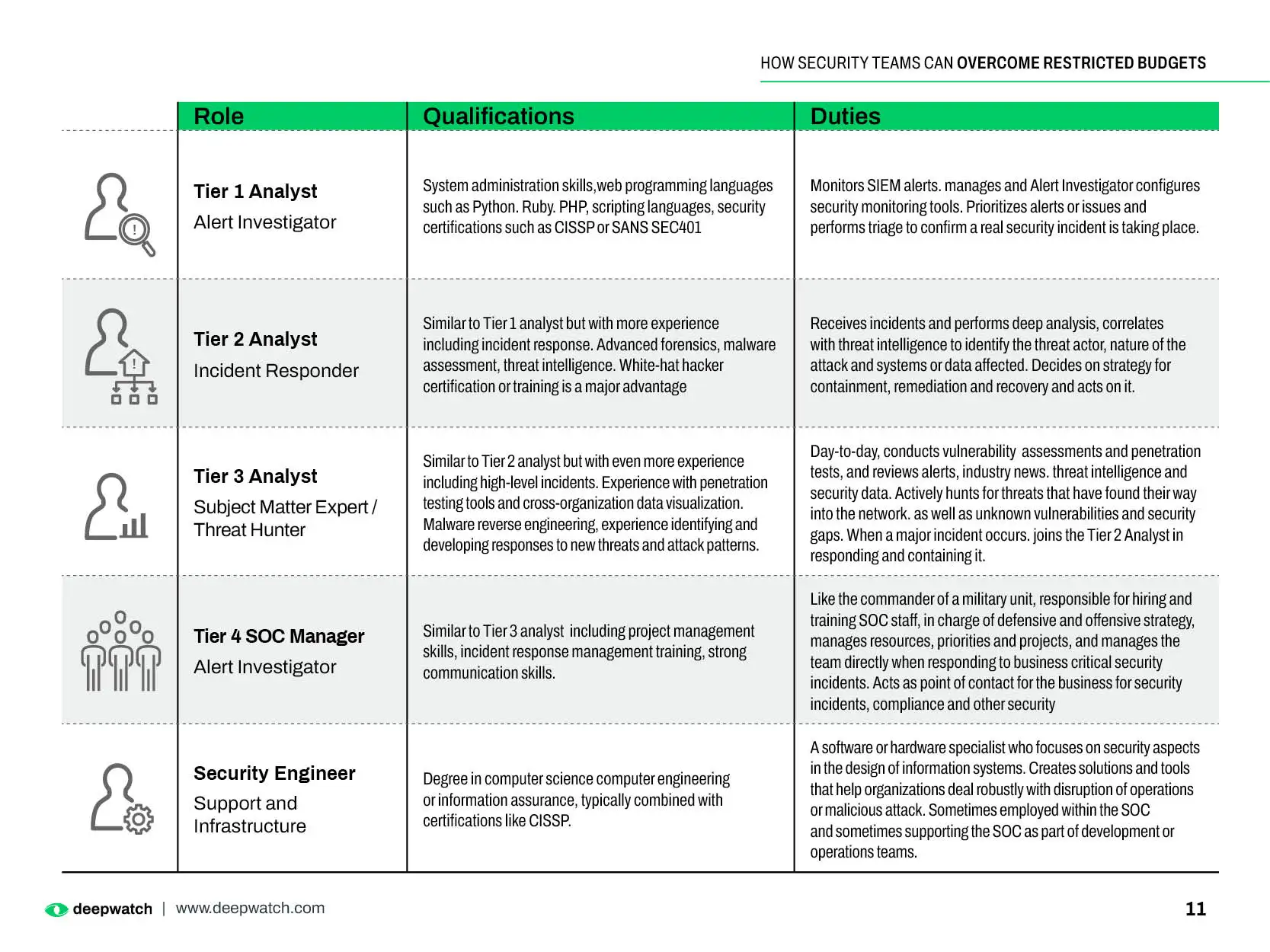
To operate efficiently and effectively, a SOC needs the right people, processes, and technologies, such as up-to-date threat intelligence systems. They need to be staffed with enough analysts possessing the right capabilities and experience to evaluate what artificial intelligence (AI) cannot.
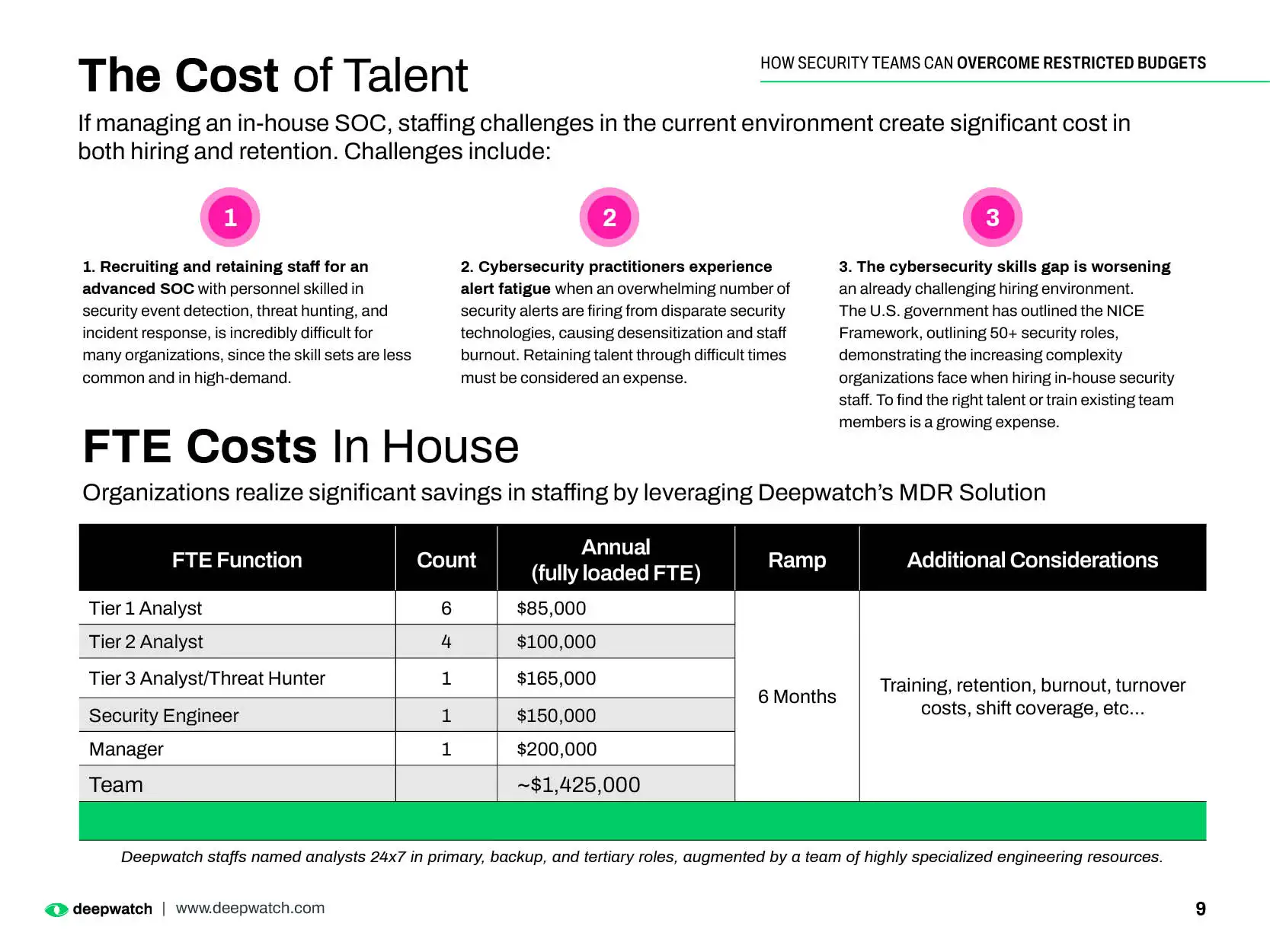
The Cost of Talent
If managing an in-house SOC, staffing challenges in the current environment create significant cost in both hiring and retention. Challenges include:
- Recruiting and retaining staff for an advanced SOC with personnel skilled in security event detection, threat hunting, and incident response, is incredibly difficult for many organizations, since the skill sets are less common and in high-demand.
- Cybersecurity practitioners experience alert fatigue when an overwhelming number of security alerts are firing from disparate security technologies, causing desensitization and staff burnout. Retaining talent through difficult times must be considered an expense.
- The cybersecurity skills gap is worsening an already challenging hiring environment. The U.S. government has outlined the NICE Framework, outlining 50+ security roles, demonstrating the increasing complexity organizations face when hiring in-house security staff. To find the right talent or train existing team members is a growing expense.
Legacy Systems Hide Growing Costs
Maintaining legacy systems often hide costs that only increase over time. Tuning, licensing, upgrades, increased bandwidth fees, subscriptions, training, and implementation all silently drain budgets. Many legacy AV or EDR solutions can’t uncover new sophisticated techniques such as fileless attacks, breaches through cloud misconfigurations, or open source vulnerabilities.
Expense of Underutilized Security Investments
To cope with tight security budgets and the inability to find skilled staff, businesses often expand their security operations and SOCs by investing in additional security tools like security information and event monitoring (SIEM) solutions and intrusion detection systems (IDS), incorrectly assuming that automation and AI and ML can augment skills gaps.
Advanced technology still can’t fully compensate for the skills and expertise that an experienced cybersecurity professional can bring to SOC activities.
Securing additional in-house technology to improve overall performance may be attractive, but organizations must evaluate solutions, onboard technology, and customize tools to meet unique business objectives. They must train staff and maintain updates and privileged access. Often turnover of engineers and analysts leave gaping holes in coverage and expertise, leaving tools and subscriptions underutilized. What’s more, security teams invested in SIEM or SOAR solutions often find they don’t have the time to customize or fully utilize the tools they have in place.
How Deepwatch Can Help
Deepwatch was created to help security teams do more with less. Our managed detection and response services are the fastest, most cost effective way to address the growing volume and complexity of threats including ransomware, supply chain attacks, or data theft.
Deepwatch managed services including EDR, MDR and MXDR cost-effectively address the growing attack surface by filling security gaps, allowing in-house teams to focus on other business objectives. With the right MDR, organizations can expand coverage and continue to mature at the speed of change while controlling costs.
↑
Share