Security platforms and market consolidation in 2024
This week we’ve seen a change in SIEM technology with several pieces moving around the board from existing large market players. The announcement of the merger of Exabeam and LogRhythm along with the acquisition of IBM’s QRadar by Palo Alto Networks continues a trend of SIEM market changes kicked off with Cisco’s acquisition of Splunk and marks impacts to 4 of the top 6 SIEMs by current market share.
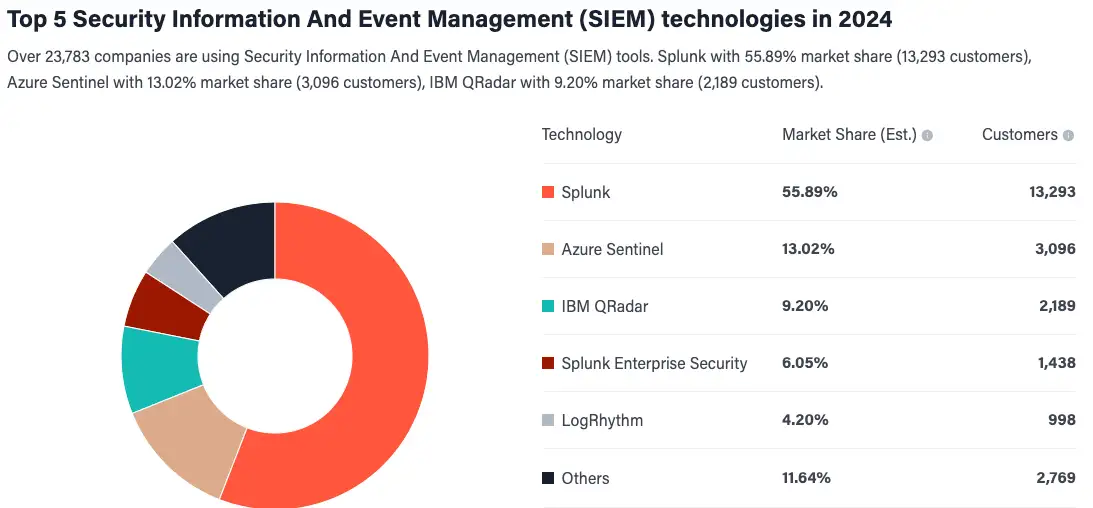
I don’t think we can call these small changes or updates; 75% of the existing market leaders of SIEM technology are changing hands, and 19% of the market is consolidating. All in less than a year. That leaves only 25% of the market untouched – so far.
What does this mean for SIEM and MSSP/MDR customers?
We know when competing software solutions merge, the resulting organization generally consolidates on one codebase or the other, or creates some other hybrid. Over the years, there have been many acquisitions and mergers of different tools or customer bases to varying levels of capability and success. Prominent examples include Snort and Sourcefire code being merged into ASA’s, Meraki’s, and RSA enVision and NetWitness integration, both announced years ago with one of them having been broken out on its own again recently. We can’t predict the future of what these changes mean for each of the engines, but we are confident in saying that an end-of-support and then an end-of-life date will be announced in the next two to three years for versions of these SIEMs. Such mergers also provide aircover for consolidating deployment models; we expect to see support for existing on-premise support and licensing to be phased out in favor of solutions hosted in vendor-owned clouds.
MSSP/MDR customers who have “managed SIEM” style solutions from their providers should anticipate some difficult conversations shortly as well. I’d recommend giving your service provider no more than 60 days before asking them how they’re planning to pivot if the SIEM they’re supporting is one of those recently impacted. Their answers will depend on roadmaps released by the newly combined SIEM software vendors, meaning their responses may be delayed, incomplete, or simply unavailable.
In the long term, we’re already seeing the shift from all security data flowing through a single SIEM to interacting with the data where it resides, wherever that may be. This doesn’t mean the SIEM necessarily goes away, but its role becomes more specialized – as the place where raw data from systems that don’t have any other analysis and parsing platform is focused. This change is being enabled through tools like hyperautomation, and Deepwatch’s own Open Security Data Architecture. This should make customer security operations smoother and more effective with reasonable cost savings, once the remaining SIEM solutions reach their steady-state codebases, which could still take a few years.
Different Options
There is an exit ramp from this highway to instability. The issues SIEM customers will face over the next couple of years are rooted in the decision to purchase and own a SIEM in the first place. Choosing an MDR/MSSP who will take responsibility and ownership of the analysis tech stack, while still offering the transparency of interacting directly with the data and analysis tools is a fantastic alternative. It eliminates the need for in-house expertise for some of the most complicated and complex cybersecurity tools on the market today. It also means that this new era of SIEM consolidation and change is the provider’s problem, not yours. At Deepwatch, we can not only support you with this model, but we can support multiple SIEM solutions through our Open Security Data Architecture model already, meaning we can begin to support your data where it lives instead of requiring an in-house engineering and management team for a legacy SIEM solution.
Alternatively, now is a tremendous time to consider a security stack consolidation. CrowdStrike’s consolidated security stack includes solutions beyond their traditional EDR solution to support identity and cloud security, along with exposure management and their release of a next generation SIEM Combining the CrowdsStrike Falcon platform and Deepwatch’s holistic security operations capabilities provides a comprehensive cybersecurity operations capability that includes protection, detection, and response across the enterprise in a more consumable and effective package.
Either of these options will provide cost-effective security operations capabilities without disrupting the next few years of SIEM consolidation worries.
Moving Forward
I encourage customers who have been impacted by these recent moves to look into the concepts of Open Security Data Architecture, while at the same time looking through the new hyperscalers and platforms or platformizations that are developing.
We have been leading Managed Detection and Response for years and have been forward-leaning on technology integration and capability. That being said, we keep returning to the hard truth of security operations. AI and platforms are going to be incredible force multipliers for increasing the efficiency and effectiveness of detection and response, but the managed term is the first for a reason. The platforms and platformization movement is predicated on consistent technology deployed correctly and consistently managed. This is the daily grind, or slog, of security operations and must be operationalized to perform holistic security operations where enterprises must ingest and understand logs from systems that are not part of a native platform to secure the business and be cyber resilient.
Open Security Data Architecture allows the holistic operationalization and review of your data and security architecture in conjunction with new abilities to stream data to low-cost storage options, or to leave data in situ. This security partnership allows an enterprise to establish and maintain freedom from the tool changes and consolidations that are sure to continue. As the originators of Open Security Data Architecture concepts, Deepwatch stands ready to help you understand your current ingestion types and levels, and to help you determine and create a new data architecture strategy.
Establish YOUR effective security data strategy.
↑
Share