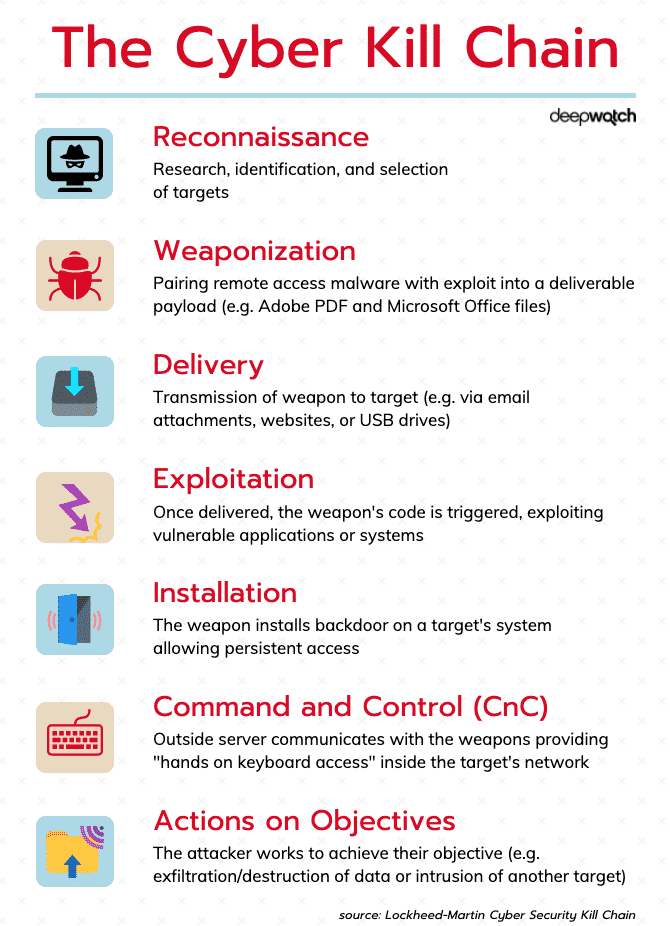
The term “kill chain” comes from a military concept that uses stages to outline the structure of an attack. “Breaking” the opponent’s kill chain refers to the ability to block an attack at any stage. In 2011 computer scientists at Lockheed-Martin corporation adapted this concept to develop the intrusion (cyber) kill chain framework which describes the steps used by attackers during cyber-based attacks. The seven stages (phases) include: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control (C2), and Action on Objectives.