Active Vulnerability Exploitation – Progress MoveIT CVE-2024-5806 – Authentication Bypass – All Industries
The Rundown
A newly disclosed MOVEit Transfer vulnerability (CVE-2024-5806) is being actively exploited after a proof-of-concept (PoC) was released publicly on 24 June.
The vulnerability allows attackers to bypass authentication and gain access to MOVEit Transfer and Gateway systems, posing severe risks to sensitive data and system integrity. Immediate patching is necessary to prevent potential breaches.
If you have questions or feedback about this intelligence, you can submit them here.
Vulnerability details:
CVE-2024-5806 is an authentication bypass vulnerability in MOVEit Transfer and Gateway. This flaw allows attackers to impersonate any user without valid credentials. Progress Software has released patches to address this critical issue. Versions affected include:
- From 2023.0.0 before 2023.0.11.
- From 2023.1.0 before 2023.1.6.
- From 2024.0.0 before 2024.0.2.
Exploiting this vulnerability requires attackers to meet three criteria:
- Knowledge of an existing username (username spraying could identify valid accounts).
- The target account must be able to authenticate remotely.
- The SFTP service must be exposed.
Active exploitation:
The Shadowserver Foundation has observed increased scanning activity targeting MOVEit Transfer instances shortly after a proof-of-concept exploit code was made publicly available. This indicates that attackers seek out unpatched systems to exploit CVE-2024-5806.
- Observed POST /guestaccess.aspx exploit attempts.
Exploit code:
watchTowr Labs has publicly released a proof-of-concept (PoC) for CVE-2024-5806 on GitHub. The PoC provides attackers with a detailed guide to exploit the vulnerability.
Risks & Impacts
The MOVEit Transfer vulnerability CVE-2024-5806 poses a significant threat due to its ability to bypass authentication and active exploitation following the release of a PoC. The likelihood of exploitation is high, and the potential impacts are severe, necessitating immediate patching and continuous monitoring to prevent possible breaches and ensure system integrity.
Threat:
The identified threat involves attackers exploiting the CVE-2024-5806 vulnerability, which allows unauthorized access to MOVEit Transfer and Gateway systems. These attackers can impersonate any user without valid credentials, leading to severe risks to sensitive data and overall system security.
Risk Factors
Unauthorized Access through Authentication Bypass:
- Likelihood: Highly likely. The PoC exploit is publicly available, and scanning activity targeting MOVEit Transfer instances has increased, indicating a high likelihood of exploitation.
- Impact: Severe. This vulnerability allows attackers to access sensitive data, leading to potential data breaches and significant operational disruptions.
Exploitation of Unpatched Systems:
- Likelihood: Highly likely. Despite Progress Software’s availability of patches, the presence of unpatched systems remains a significant risk, as evidenced by ongoing scanning activity and observed exploit attempts.
- Impact: Critical. Exploiting unpatched systems can lead to complete system compromise, data exfiltration, and potential loss of customer trust.
Username Knowledge and Remote Authentication:
- Likelihood: Likely. Successful exploitation requires knowledge of existing usernames, the ability for accounts to authenticate remotely, and the exposure of the SFTP service. These conditions are likely met in many environments, making exploitation feasible.
- Impact: High. Attackers gaining access through valid usernames can lead to targeted attacks, unauthorized data access, and potential lateral movement within the network.
Actions & Recommendations
The MOVEit Transfer vulnerability (CVE-2024-5806) requires immediate and strategic actions to mitigate the identified risks and protect organizational assets. Here are key actions and recommendations you should implement to enhance cyber resilience:
- Ensure all MOVEit Transfer and Gateway systems are updated to versions 2023.0.11, 2023.1.6, and 2024.0.2 or later.
- Disable the SFTP service if not required. Limiting the exposure of the SFTP service reduces the attack surface. Only enable essential services to minimize potential entry points for attackers.
- Implement strict monitoring and management of user accounts. Conduct an audit to identify and disable inactive accounts. To add an extra layer of security, implement multi-factor authentication (MFA) for all user accounts.
- Deploy Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and Web Access Firewalls (WAF) to monitor for indicators of compromise such as unusual POST /guestaccess.aspx attempts. Set up alerts for abnormal login attempts and access patterns.
- Raise employee awareness about the new threat. Conduct immediate training sessions to inform employees about the vulnerability, the importance of using strong, unique passwords, and recognizing phishing attempts.
In addition, the Adversary Tactics and Intelligence team uses this intelligence report to improve our correlation rules and detections and conduct threat hunting. However, due to limitations in log sources received by Deepwatch, not all activity can be monitored.
Threat Hunting Guidance
We recommend that all customers retrospectively hunt for malicious activity, which will likely indicate compromise, using the Be On the Lookout (BOLO) guidance provided below:
- Inbound HTTP POST requests to https://<SERVER>/guestaccess.aspx (especially from python-related user agents that may indicate usage of POC exploit code)
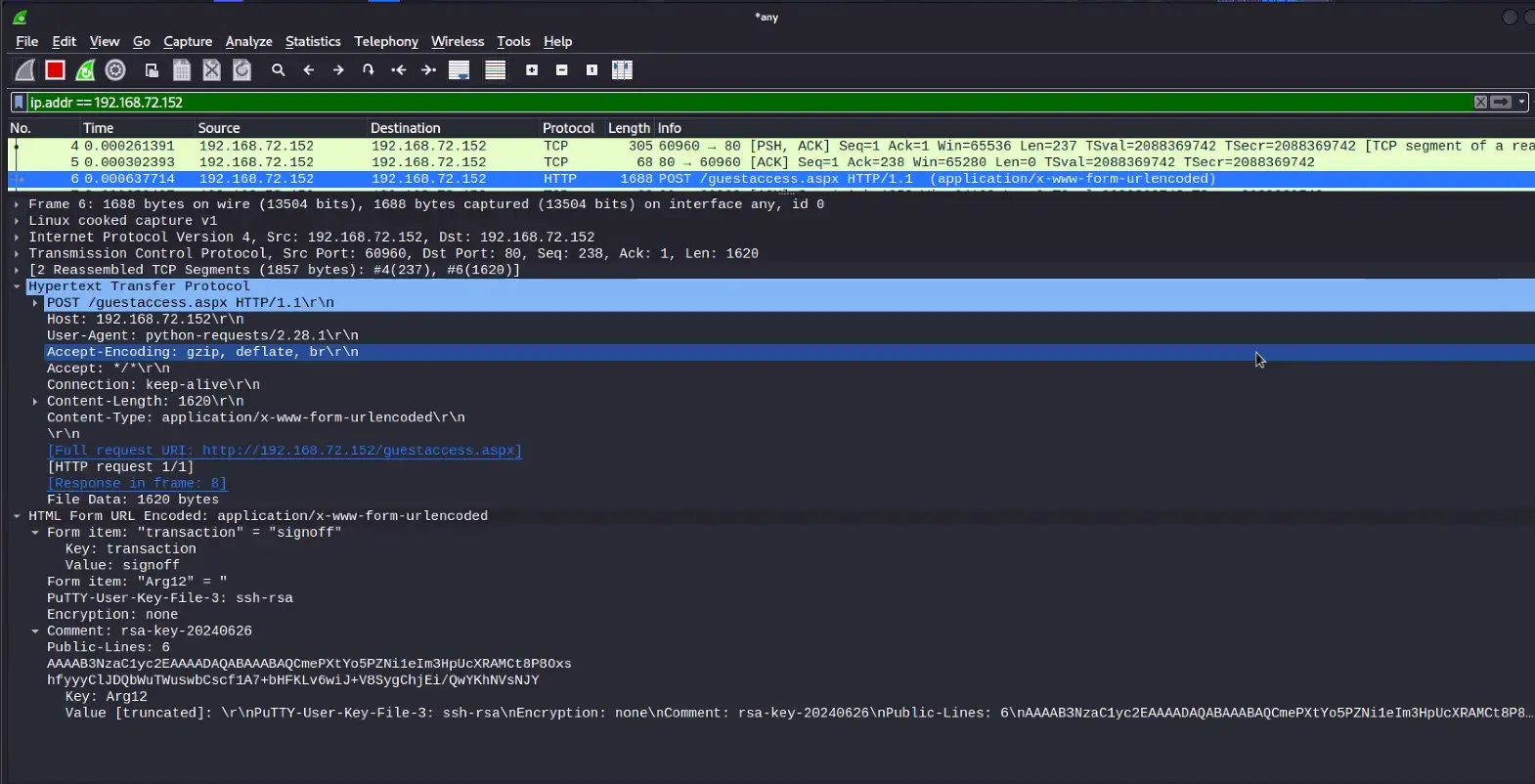
- Anomalous SFTP/SSH connections/logins by rare users or source addresses, especially when directly preceded by suspicious/repeated web requests as shown above (POC first contacts the web UI on port 443 and then attempts to connect to SFTP on port 22/TCP)
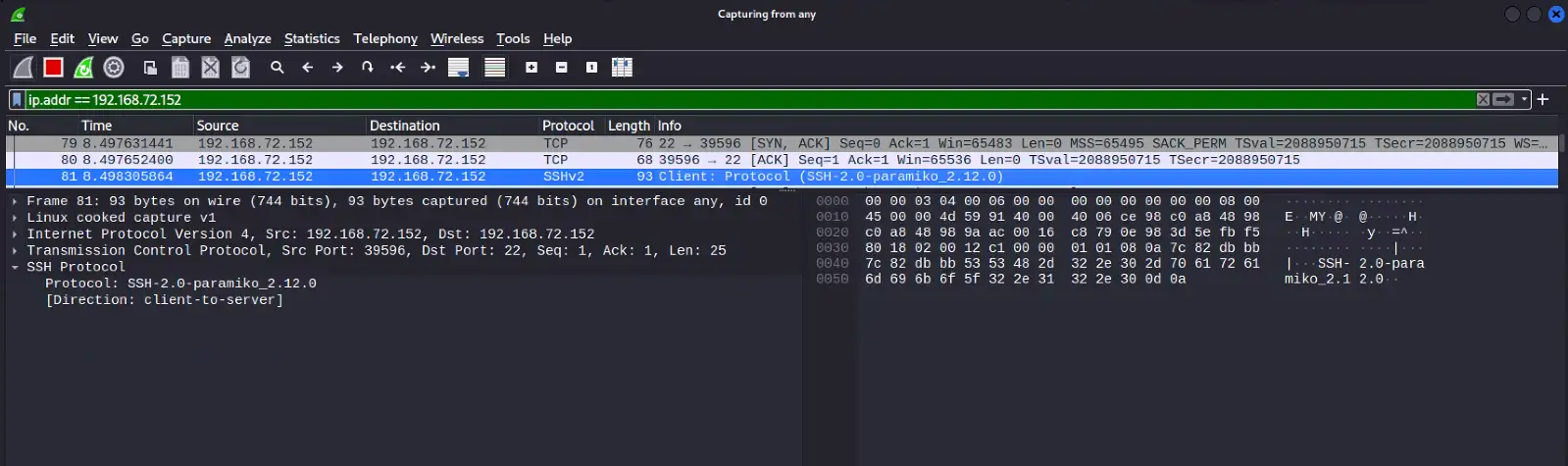
- Rare/anomalous file access/creation events relating to SftpServer.exe as shown here
- Outbound public SMB traffic from impacted appliances (forced authentication, NTLM credential leak)
- Rare/anomalous login/authentication activity relating to the service account provisioned to MoveIt
- Credential theft via NTLM leak/cracking may allow a threat actor to use the stolen service account password to gain access to additional systems/services across the network
- Entries in the application’s system log similar to below:
- SILUser.ExecuteAuthenticators: Authenticating user ‘<USER>’ with authenticator: MOVEit.DMZ.SftpServer.Authentication.SftpPublicKeyAuthenticator
- “Validating client key fingerprint for user” (truncated, note double space between “fingerprint” and “for”)
Share