What You Need to Know
- A vulnerability exists in Confluence’s Questions for Confluence Server and Data Center application, tracked as CVE-2022-26138.
- When an organization adds the Questions for Confluence app, an account “disabledsystemuser” is created with a hardcoded password and added to the confluence-users group. The account details, including the hardcoded password, have been leaked on Twitter. Even if organizations delete the app, the account may still exist.
- If the account is active, it allows the editing and viewing of any pages to which the group “confluence-users” has access.
- Deepwatch Squads are identifying customers that this vulnerability may impact and evaluating the detection strategy for this exploitation.
Executive Summary
On July 20, Atlassian released a security advisory warning organizations about a vulnerability in its “Questions for Confluence” application for Confluence Server and Data Center, tracked as CVE-2022-26138. The “Questions for Confluence” app allows organizational users to share knowledge, ask questions, and find answers. According to the Atlassian Marketplace application page, this app has been installed over 8,000 times, and the vulnerability affects versions 2.7.34, 2.7.35, and 3.0.2.
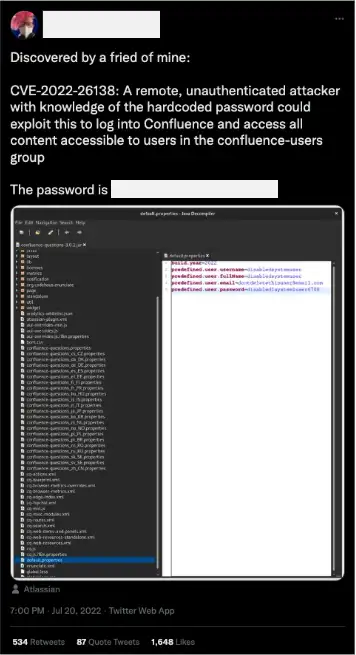
This vulnerability exists because a Twitter user leaked the hardcoded password for the user, “disabledsystemuser.” The account “disabledsystemuser” is created when an organization adds the “Questions for Confluence” app and aids administrators in migrating data from the app to Confluence Cloud. This account may also exist even if you uninstalled the application.
Key Findings
- Starting on July 20, threat actors have likely attempted to log in to Confluence instances; some of these attempts may have been successful.
- Threat actors are highly likely to attempt exploitation of this vulnerability over the coming weeks to view or edit the pages accessible to the confluence-users group with the intent of conducting espionage, exposing sensitive data, or reconnaissance.
Note: To convey the possibility or probability of our hypothesis, the Deepwatch Threat Intel Team employs probabilistic language in our assessments. Because analytical assessments are not certain, we use terms (highly unlikely, unlikely, likely, and highly likely) that denote that our hypothesis has a greater or lower than even chance of possibility or probability. A “roughly even chance” demotes that our hypothesis has a roughly 50% possibility or probability of occurring. In addition, terms such as “might,” “could,” or “may” reflect situations in which we are unable to assess the likelihood, generally because relevant information is unavailable, sketchy, or fragmented.
CVE-2022-26138 Details
The vulnerability, CVE-2022-26138, exists when an organization adds the Confluence app “Questions for Confluence.” Adding the app creates a new user, “disabledsystemuser,” with a hardcoded password and is added to the confluence-users group.
According to Atlassian’s Marketplace application page, this app has been installed over 8,000 times (Figure 1).
On July 20, a Twitter user leaked the hardcoded password (Figure 2). Threat actors who discover this password, and if the account is still active, can log on to Confluence, and any pages to which the group (confluence-users) has access will have the ability to view or edit them.
Affected Products
The vulnerability affects “Questions for Confluence” application versions 2.7.34, 2.7.35, or 3.0.2. These versions create the disabledsystemuser account with the hardcoded password. However, according to Confluence’s security advisory, they note that “Confluence installations that do not actively have any of these versions of the app installed may still be affected.”
If you previously installed and uninstalled the “Questions for Confluence” app, it is possible that this account still exists and may be active. If you cannot locate this account as an active user, your Confluence instance is not affected.
Your Confluence Server or Data Center instance is affected if it has an active user account with the following information:
User and Username: disabledsystemuser
Email: [email protected]
What You Need to Do
Atlassian has provided two options to mitigate this vulnerability.
Option one entails updating your vulnerable version of “Questions for Confluence” to 2.7.38, for Confluence versions 6.13.18 through 7.16.2, or 3.0.5, compatible with Confluence versions 7.16.3 and later.
If you cannot update the app at that time or your Confluence is configured to use a read-only external directory, you will have to use option two.
Option two entails searching for the disabledsystemuser account and either disabling it or deleting it. Atlassian has provided instructions on how to disable or delete an account. You can view these steps in the “Delete or Disable Users” Confluence documentation.
For those organizations whose Confluence is configured to use a read-only external directory, refer to the Delete from a read-only external directory, or multiple external directories section.
Identifying Possible Exploitation
To identify a list of users with their last login time and whether it was successful or unsuccessful, Atlassian has provided the following queries:
List of users whose last successful or unsuccessful login to Confluence on a defined time frame interval.
PostgreSQL:
Note: Replace ‘<group-name>’ with a group name (confluence-users).
WITH last_login_date AS
(SELECT user_id
, to_timestamp(CAST(cua.attribute_value AS double precision)/1000) AS last_login
FROM cwd_user_attribute cua
WHERE cua.attribute_name = 'lastAuthenticated'
AND to_timestamp(CAST(cua.attribute_value AS double precision)/1000) < (CURRENT_DATE))
SELECT c.user_name
, c.lower_user_name
, c.email_address
, c.display_name
, c.last_name
, g.group_name
, l.last_login
FROM cwd_user c
INNER JOIN last_login_date l ON (c.id = l.user_id)
INNER JOIN cwd_membership m ON (c.id = m.child_user_id)
INNER JOIN cwd_group g ON (m.parent_id = g.id)
WHERE g.group_name = '<group-name>'
ORDER BY last_login DESC;MySQL:
select cu.user_name
, cu.lower_user_name
, cu.email_address
, cu.display_name
, cu.last_name
, cua.attribute_value
, FROM_UNIXTIME(cua.attribute_value/1000) as lastAuthenticated
FROM cwd_user cu left join cwd_user_attribute cua on cu.id = cua.user_id and cua.attribute_name = 'lastAuthenticated'
order by lastAuthenticated descList of users who last successfully logged in to Confluence on a defined time frame interval.
PostgreSQL:
Note: Replace ‘<group-name>’ with a group name (confluence-users).
WITH last_login_date AS
(SELECT user_id
, to_timestamp(CAST(cua.attribute_value AS double precision)/1000) AS last_login
FROM cwd_user_attribute cua
WHERE cua.attribute_name = 'lastAuthenticated'
AND to_timestamp(CAST(cua.attribute_value AS double precision)/1000) < (CURRENT_DATE))
SELECT c.user_name
, c.lower_user_name
, c.email_address
, c.display_name
, c.last_name
, g.group_name
, li.successdate
FROM cwd_user c
INNER JOIN last_login_date l ON (c.id = l.user_id)
INNER JOIN cwd_membership m ON (c.id = m.child_user_id)
INNER JOIN cwd_group g ON (m.parent_id = g.id)
INNER JOIN user_mapping um ON (c.user_name = um.username)
INNER JOIN logininfo li ON (um.user_key = li.username)
WHERE g.group_name LIKE '<group-name>'
ORDER BY successdate DESC;List of unsuccessful user logins to Confluence on a defined time frame interval.
PostgreSQL:
Note: Replace ‘<group-name>’ with a group name (confluence-users).
WITH last_login_date AS
(SELECT user_id
, to_timestamp(CAST(cua.attribute_value AS double precision)/1000) AS last_login
FROM cwd_user_attribute cua
WHERE cua.attribute_name = 'lastAuthenticated'
AND to_timestamp(CAST(cua.attribute_value AS double precision)/1000) < (CURRENT_DATE))
SELECT c.user_name
, c.lower_user_name
, c.email_address
, c.display_name
, c.last_name
, g.group_name
, li.faileddate
FROM cwd_user c
INNER JOIN last_login_date l ON (c.id = l.user_id)
INNER JOIN cwd_membership m ON (c.id = m.child_user_id)
INNER JOIN cwd_group g ON (m.parent_id = g.id)
INNER JOIN user_mapping um ON (c.user_name = um.username)
INNER JOIN logininfo li ON (um.user_key = li.username)
WHERE g.group_name LIKE '<group-name>' AND
li.faileddate IS NOT NULL
ORDER BY faileddate DESC;Conclusion
Now that the hardcoded password for “disabledsystemuser” has been leaked and available for five days, it is imperative that organizations identify any possible exploitation attempts and remediate this vulnerability as soon as possible.
Analyst Note: Threat actors have likely attempted to log in to Confluence instances; some of these attempts may have been successful. Additionally, it is highly likely that threat actors will attempt to exploit this vulnerability over the coming weeks to view or edit the pages accessible to the confluence-users group with the intent of conducting espionage, exposing sensitive data, or reconnaissance.
Deepwatch Threat Intel Team has noticed a pattern of critical vulnerabilities over the past few years, affecting the Atlassian Confluence web application and threat actors exploiting these vulnerabilities. However, taking risk reduction measures to not expose this application to all of the Internet. Instead, allowing access to it once authenticated or only allowing access from a trusted source could limit the impact of these vulnerabilities from exploitation until organizations can implement the recommendations listed in the “What You Need to Do” section above.
↑
Share