Key Points:
- Significant Increase In Ransomware Activity, Specifically the Conti Variant
- Highly Recommended to Review Best Security Practices (Multi-Factor Authentication, Patch Management, Understand Internet Exposed Technologies, especially Remote Desktop and Exchange)
- All Customers Should Operate Under the Assumption That Ransomware Could target them
Summary
Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) issued a joint advisory (PDF) yesterday regarding increased Conti ransomware activity and detailing observed tactics, techniques, and procedures (TTPs). According to the advisory, Conti ransomware has been used in over 400 attacks on US and international businesses.
Deepwatch’s Threat Intel Team has been tracking this activity to provide information as soon as possible. Please review our recent Significant Cyber Event Customer Advisory regarding Microsoft Exchange exploitation and the following headlines from our weekly Cyber Intelligence Brief (CIB):
- August 16 – “A Look Inside the Operations and Tradecraft of the Conti Ransomware Gang.”
- August 27 – “FBI Issues Alert Releasing IOCs for “OnePercent Group” Ransomware Affiliate.”
- September 7 – “CISA Issues Alert for Ransomware Awareness for Holidays and Weekends.”
- September 13 – “The Ideal Ransomware Victim: What Threat Actors Are Looking For.”
Conti is classified as ransomware-as-a-service (RaaS); however, its structure differs from a traditional affiliate model. Conti developers are more than likely to give ransomware affiliates a wage rather than a part of the proceeds from a successful assault.
According to the advisory, Conti affiliates used the following techniques to carry out their attacks:
- Spearphishing attacks.
- Remote monitoring and management software.
- The “PrintNightmare” & “Zerologon” vulnerabilities. And have been known to have used “ProxyShell” in attacks as well.
- Deepwatch encourages customers to reach out to their squad manager about our vulnerability management services.
While the techniques above are commonly utilized, other techniques have also been seen, and a defense-in-depth strategy coupled with best security practices is the strongest way to reduce risk.
Additionally, details from a previously released Conti “playbook” identify four IP addresses used in previous attacks as Cobalt Strike C2 servers (Please see Appendix A).
Mitigations:
CISA, the FBI, and the NSA recommend organizations employ the following mitigation strategies.
- Multi-factor authentication.
- Implement network segmentation and filter traffic.
- Scan for vulnerabilities and keep software updated.
- Remove unnecessary applications and apply controls.
- Implement endpoint and detection response tools.
- Limit access to resources over the network, especially by restricting RDP.
- Secure user accounts.
In addition to these recommendations, Deepwatch recommends customers implement the following measures:
- Evaluate your company’s technologies which are exposed to the Internet.
- Specifically On-Prem Exchange, Remote Desktop, and VPN Technologies
- Work with your security teams to closely monitor any single-factor authentication technologies on the Internet,
- Especially VPN technologies.
- Implement Multi-Factor authentication as soon as possible.
Common vulnerabilities exploited by ransomware threat actors:
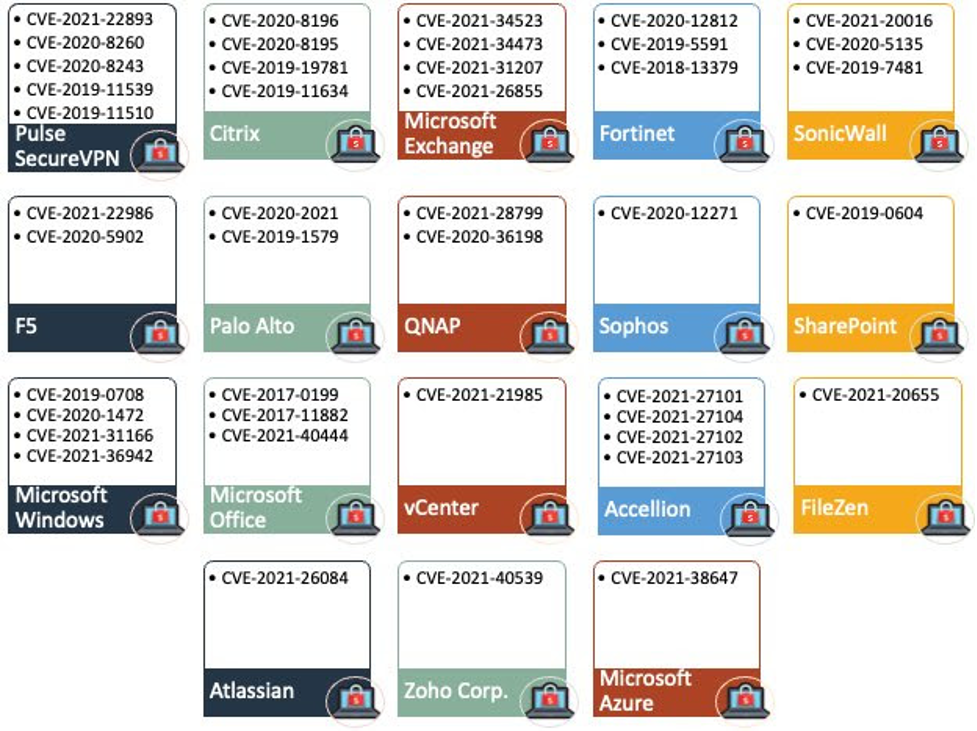
Source: Allan Liska via Twitter
Deepwatch Threat Intelligence Outlook
Deepwatch assesses with high confidence that ransomware attacks (including Conti) will continue due to insufficient prioritization of security hygiene for organizations’ Internet-facing systems coupled with the influx of recent vulnerabilities that affect externally facing systems.
Additionally, a recent discovery that REvil ransomware operators have been taking over ransom negotiations without their affiliate’s knowledge and pocketing the entire ransom payment themselves will likely cause potential affiliates to seek out other RaaS operators like Conti to facilitate their attacks.
Appendix A
IOCs
IP Addresses
- 162.244.80[.]235
- 85.93.88[.]165
- 185.141.63[.]120
- 82.118.21[.]1
These IP addresses were identified as Cobalt Strike servers previously used and leaked in Conti ransomware playbooks.
↑
Share