Threat Actors Evolve Tactics, North Korean Group Targets Developers, and CISA Flags SonicWall Vulnerability
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
A New Playbook for Threat Actor Resilience
The Rundown
A new cybersecurity threat targeting Fortinet’s FortiGate devices has emerged, prompting warnings from both Fortinet and the U.S. Cybersecurity and Infrastructure Security Agency (CISA). Cybercriminals are taking advantage of previously known vulnerabilities to maintain unauthorized access to affected systems—even after companies have applied standard security patches. By creating hidden system shortcuts (known as symbolic links), these attackers can quietly access sensitive system information, increasing the risk of data breaches or further compromise.
The issue primarily impacts organizations that have used the SSL-VPN feature on FortiGate devices. If that feature was ever turned on, attackers could have left behind hidden tools that remain active despite patching. This means even after IT teams believe the issue has been resolved, attackers could still be watching, waiting, or collecting information. It’s not just about fixing a vulnerability—it’s about ensuring nothing dangerous was left behind.
To help mitigate this threat, Fortinet has released updated software that not only patches the vulnerabilities but also actively removes any unauthorized system changes made by attackers. Business leaders are strongly encouraged to ensure their security teams install these updates immediately, review system logs for unusual activity, and consider resetting any potentially compromised credentials. Taking quick, decisive action is essential to maintaining the trust and integrity of your organization’s digital environment.
Source Material: CISA Fortinet
Job Offer or Cyber Trap? North Korean Group Slow Pisces Targets Developers
The Rundown
A North Korean state-sponsored threat group known as Slow Pisces has launched a sophisticated cyber campaign targeting software developers through fake job opportunities. By posing as recruiters from reputable companies on platforms like LinkedIn, the attackers entice victims with supposed coding challenges. These tests are actually a delivery mechanism for custom malware designed to infiltrate and compromise the victim’s system.
Once the developer runs the provided Python-based test files, two custom malware tools—“RU Loader” and “RU Stealer”—are deployed. These tools enable the attackers to steal sensitive data, including credentials and cryptocurrency-related information. The campaign is notably well-crafted, leveraging professional interactions and open-source platforms like GitHub to appear legitimate and bypass initial suspicion.
This attack underscores a growing trend of using social engineering tactics to target professionals with access to high-value digital assets. Businesses in the cryptocurrency and tech sectors should remain vigilant, especially when their developers are approached with unsolicited job offers. Employee awareness and strong endpoint security measures are essential to preventing these types of threats.
Source Material: Palo Alto Unit 42
Ransomware and Data Extortion Trends (Apr. 7 – 13)
The Rundown
Ransomware and data extortion activity includes a sharp increase between April 7 – 13, with a 58% decrease in listed organizations compared to the previous week.
The significant reduction of 138 ransomware incidents compared to the previous week suggests a deliberate shift in attacker strategy—favoring targeted, high-impact operations over broad-scale campaigns. This trend highlights the continued sophistication of ransomware threats and the critical need for organizations to stay ahead through strategic investment in cybersecurity resilience
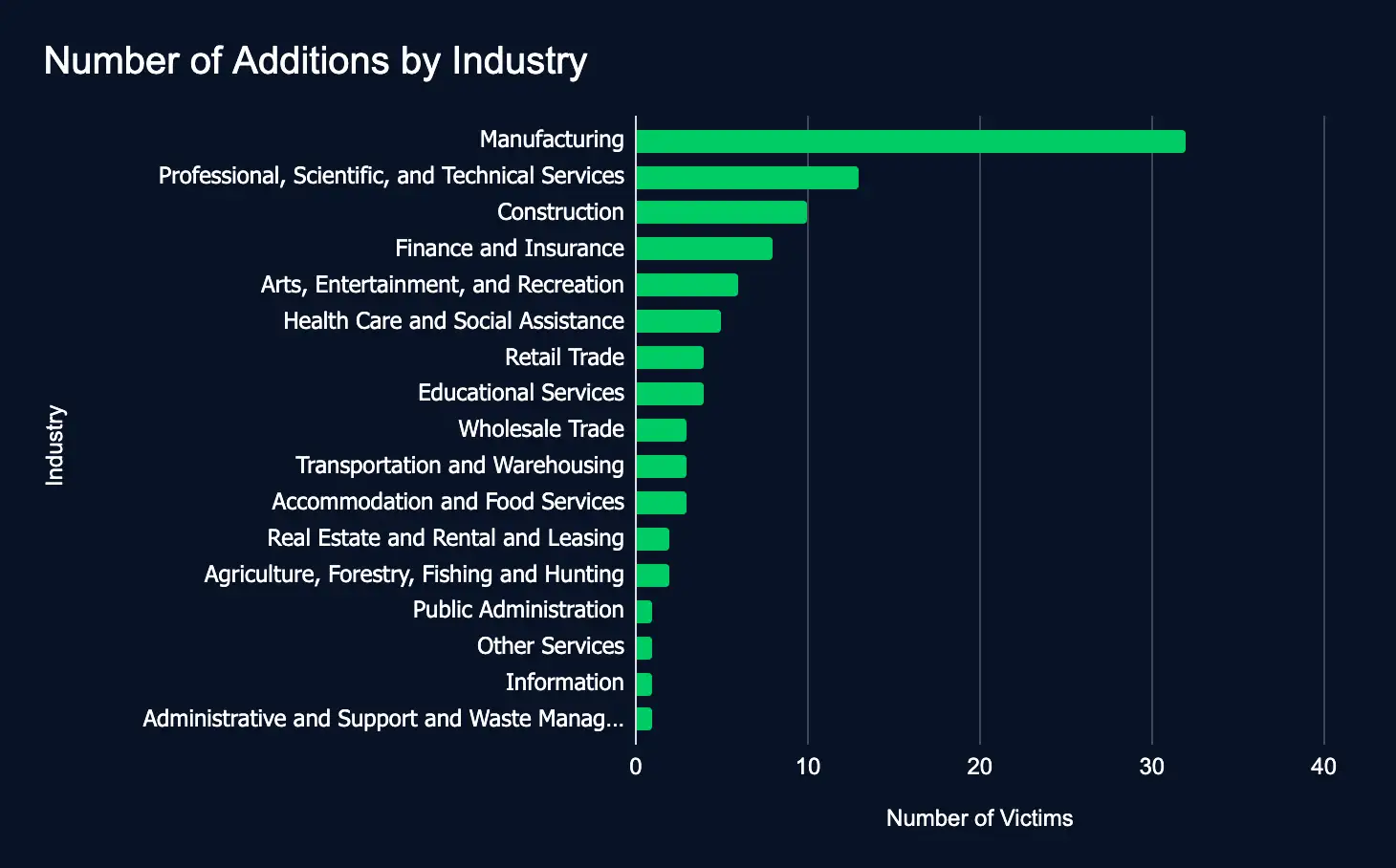
In the reporting time frame, 99 organizations across 17 industries were listed on 20 ransomware and data extortion leak sites, marking a sharp decrease from the previous week’s 237 victims.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Construction
- Most affected countries:
- United States
- United Kingdom
- Canada
- Most active leak sites:
- Qilin
- Akira
- INC Ransom
Exploited Vulnerability in a SonicWall Product Added to CISA’s Catalog
The Rundown
Between April 10th and 16th, 1 critical vulnerability affecting a SonicWall product was added to CISA’s Known Exploited Vulnerabilities catalog. If left unpatched, this vulnerability could leave organizations vulnerable to cyberattacks.
This vulnerability highlights critical risk for organizations dependent on widely used technologies. Given the potential targeting by state-sponsored and cybercriminal actors, swift action is crucial to prevent exploitation.
SonicWall | SMA100 Appliances CVE-2021-20035
- Vulnerability Description: SonicWall SMA100 appliances contain an OS command injection vulnerability in the management interface that allows a remote authenticated attacker to inject arbitrary commands as a ‘nobody’ user, which could potentially lead to code execution.
- Exploitation Details: This can lead to denial of service (DoS) by exploiting specific parameters via HTTP requests.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-16
- Recommended Mitigation Due Date: 2025-05-07
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share