FOG Ransomware Masquerades as Legit Software, Fake CAPTCHAs Fuel Lumma Stealer Infections, and CISA Flags New Microsoft and Apple Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Inside FOG: The Ransomware Cloaked in Legitimate Software
The Rundown
Trend Micro’s investigation into the FOG ransomware campaign uncovers a stealthy and methodically layered attack structure. The ransomware is hidden within multiple binary loaders that are chained together, with each component designed to obscure the presence and function of the next. This loader chaining significantly complicates detection and analysis, as it masks the actual payload and allows the attack to unfold in stages without immediate exposure.
The threat actors behind FOG utilize advanced evasion techniques such as DLL sideloading and process injection to bypass security tools and operate within legitimate-looking system processes. These methods make the ransomware extremely difficult to detect using traditional endpoint protection solutions. The use of fileless components and encrypted payloads further enhances its ability to evade analysis and persist undetected within compromised systems.
Trend Micro emphasizes that FOG ransomware exemplifies how attackers are adopting increasingly complex, stealth-focused delivery mechanisms. The report warns that such threats not only demonstrate the growing sophistication of ransomware campaigns but also highlight the urgent need for organizations to stay ahead of these tactics by closely monitoring evolving threat behaviors and adapting their security postures accordingly.
Source Material: Trend Micro
Beyond the Checkbox: How Fake CAPTCHAs Facilitate Lumma Stealer Attacks
The Rundown
This threat intelligence explores how cybercriminals are employing fake CAPTCHA pages to distribute the Lumma Stealer malware, a tool designed to extract sensitive information such as passwords and cryptocurrency wallet details. These deceptive CAPTCHA pages mimic legitimate verification checks, prompting users to execute commands that inadvertently install the malware on their systems. This tactic is part of a broader trend where attackers exploit familiar web elements to bypass user skepticism and security measures.
The campaign’s reach is extensive, targeting individuals across various industries and countries. By leveraging malvertising—malicious advertising content—attackers redirect users to these counterfeit CAPTCHA pages. The malware operates on a malware-as-a-service (MaaS) model, allowing cybercriminals to rent its capabilities, thereby lowering the barrier to entry for conducting such attacks. This approach not only facilitates widespread distribution but also complicates attribution and mitigation efforts.
For businesses, this underscores the importance of comprehensive cybersecurity strategies that include employee education on recognizing social engineering tactics, regular system updates, and the deployment of advanced threat detection tools. Understanding the evolving methods of malware distribution is crucial in developing effective defenses against such sophisticated attacks.
Source Material: Securelist
Ransomware and Data Extortion Trends (Apr. 14 – 20)
The Rundown
Ransomware and data extortion activity includes a sharp increase between April 14 – 20, with a 38% increase in listed organizations compared to the previous week.
A rise of 37 ransomware Data Leak listings from the previous week points to a strategic shift by threat actors toward more targeted, high-impact attacks. This evolving threat landscape highlights the critical need for executive-level focus on strengthening cybersecurity frameworks and making strategic investments to ensure long-term organizational resilience.
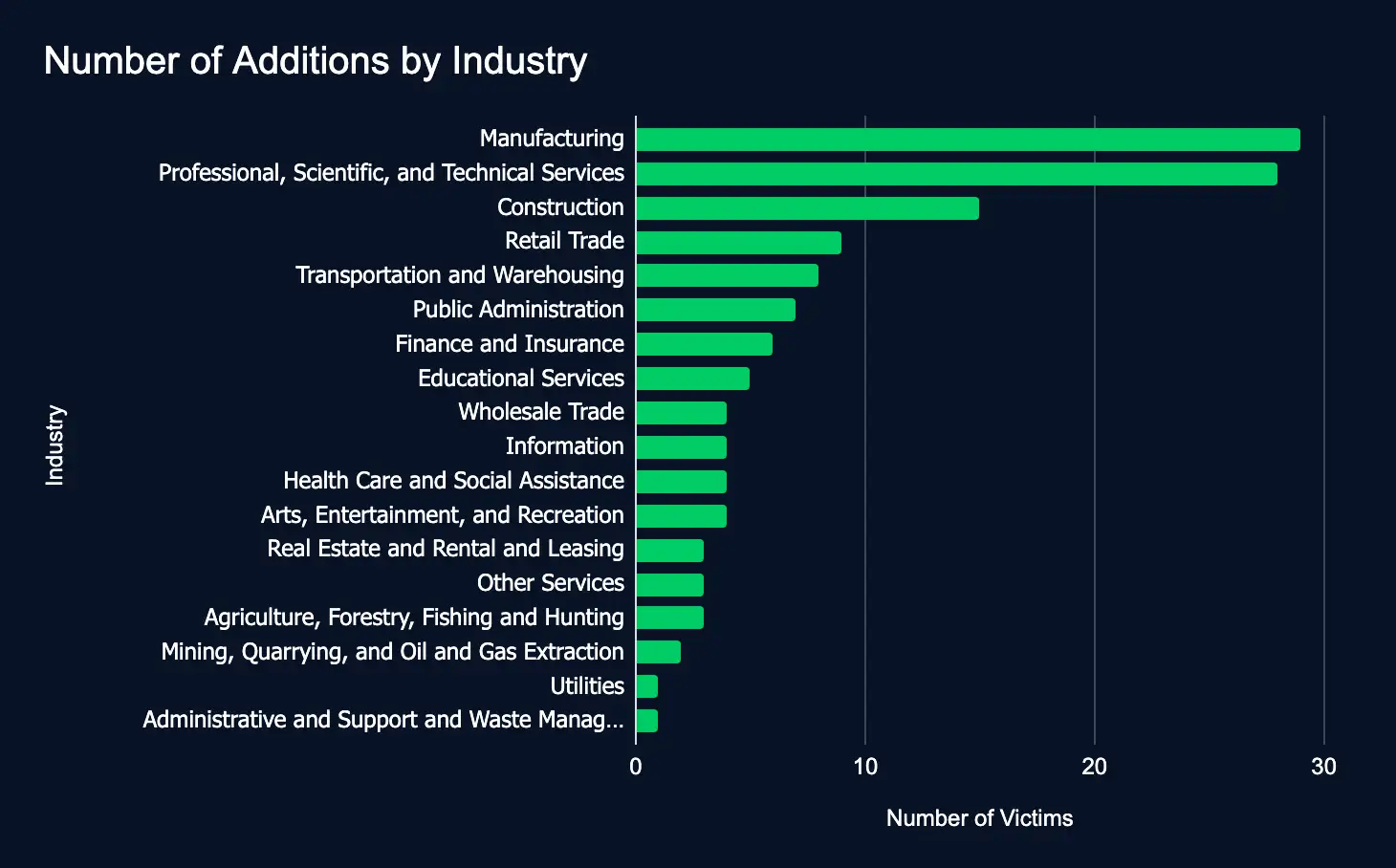
In the reporting time frame, 136 organizations across 18 industries were listed on 18 ransomware and data extortion leak sites, marking a moderate increase from the previous week’s 99 victims.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Construction
- Most affected countries:
- United States
- Germany
- Canada
- Most active leak sites:
- NightSpire
- Akira
- Qilin
Exploited Vulnerabilities in Microsoft and Apple Products Added to CISA’s Catalog
The Rundown
Between April 17th and 23rd, 3 critical vulnerabilities affecting Microsoft and Apple products were added to CISA’s Known Exploited Vulnerabilities catalog. If left unpatched, these vulnerabilities could leave organizations vulnerable to cyberattacks.
This vulnerability highlights a critical risk for organizations dependent on widely used technologies. Given the potential targeting by state-sponsored and cybercriminal actors, swift action is crucial to prevent exploitation.
Microsoft | Windows CVE-2025-24054
- Vulnerability Description: Microsoft Windows NTLM contains an external control of file name or path vulnerability that allows an unauthorized attacker to perform spoofing over a network.
- Exploitation Details: This vulnerability enables NTLM hash disclosure via spoofing, actively exploited in the wild since March 2025. Attackers leverage malicious .library-ms files to trigger automatic SMB authentication requests, capturing NTLMv2 hashes with minimal user interaction.
- On April 18, 2025 Checkpoint released information concerning research around Threat Actors exploiting this vulnerability.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-17
- Recommended Mitigation Due Date: 2025-05-08
Apple | Multiple Products CVE-2025-31201
- Vulnerability Description: Apple iOS, iPadOS, macOS, and other Apple products contain an arbitrary read and write vulnerability that allows an attacker to bypass Pointer Authentication.
- Exploitation Details:
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-17
- Recommended Mitigation Due Date: 2025-05-08
Apple | Multiple Products CVE-2025-31200
- Vulnerability Description: Apple iOS, iPadOS, macOS, and other Apple products contain a memory corruption vulnerability that allows for code execution when processing an audio stream in a maliciously crafted media file.
- Exploitation Details: This vulnerability affects CoreAudio, an API Apple devices use for processing audio. The memory corruption vulnerability can be triggered with a maliciously crafted media file: when the audio stream in it is processed, it allows attackers to execute malicious code.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-17
- Recommended Mitigation Due Date: 2025-05-08
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share