OpenMetadata Vulnerabilities Mine Crypto, Spoofed IP Scanning Websites Target IT Teams, and DuneQuixote Campaign Includes Spanish Poetry to Deliver CR4T Backdoor
This week: threat actors target internet-exposed Kubernetes workloads of OpenMetadata to mine crypto, IT teams become targets of spoofed IP scanning sites, a malware campaign includes Spanish poetry, and there are 4 new CVEs to contend with.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Adversaries Exploit OpenMetadata Vulnerabilities for Cryptomining
Vulnerability Exploitation – Cryptomining – Cryptominer – Hacking Tool – Netcat – OpenMetadata Kubernetes CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, CVE-2024-28254 – Industries/All
Threat Analysis
In one disclosed case, the adversary likely identified and targeted internet-exposed Kubernetes workloads of OpenMetadata for initial access. Once they identified a vulnerable workload, the adversary exploited one of the vulnerabilities to gain code execution on the container running the vulnerable OpenMetadata image.
The adversary then attempted to validate their exploitation attempt and assess their level of control over the compromised system. This validation step often involved contacting a publicly available service. In the one disclosed case, the adversary sent ping requests to domains that end with oast[.]me and oast[.]pro, which are associated with Interactsh, an open-source tool for detecting out-of-band interactions.
After validating their initial access, the adversary performed reconnaissance by running a series of commands to gather information about the victim’s environment, such as the network and hardware configuration, OS version, active users, etc.
The adversary also read the environment variables of the OpenMetadata workload. Those variables might contain connection strings and credentials for various services used for OpenMetadata operation, which the adversary could leverage to move to additional resources.
Once the adversary confirmed their access and connectivity, they downloaded the cryptominer payload from a remote server in China. This remote server hosted additional crypto mining-related malware for Linux and Windows OS.
The downloaded payload’s permissions are then elevated to grant execution privileges. The adversary then executes the downloaded cryptominer and removes the initial payloads from the workload. The adversary also added a personal note to the victims, pleading with them to let their malware run.
Lastly, for hands-on keyboard activity, the adversary initiated a reverse shell connection to their remote server using the Netcat tool, which allowed them to access the container remotely and gain better control over the system. However, Microsoft did not disclose the hands-on keyboard activity. Additionally, to maintain the persistence of the cryptominer, the adversary used cron jobs for task scheduling, enabling the execution at predetermined intervals.
Risk & Impact Assessment
Given the widespread deployment of Kubernetes and OpenMetadata’s metadata management across various data sources, organizations are likely to be targeted by this cryptomining campaign. Organizations that utilize internet-exposed Kubernetes to orchestrate containers, particularly those running versions of OpenMetadata vulnerable to the disclosed CVEs, are at risk. This vulnerability allows adversaries to execute arbitrary code remotely, presenting a substantial risk to affected organizations. Such threats are particularly concerning given the growing reliance on Kubernetes environments for critical operations, heightening the potential for impactful security breaches.
The adverse outcomes of this cryptomining campaign on impacted organizations can be extensive and severe. Cryptominers can lead to degraded system performance and increased operational costs due to the unauthorized use of computing resources. Additionally, exploitation of these vulnerabilities could lead to more destructive attacks, such as data theft or ransomware deployment. The operational impact of this campaign includes immediate resource drainage and potential disruption to critical data management processes.
Financially, organizations may face increased costs for incident response and heightened cybersecurity measures. Moreover, if the breach becomes public, the reputational damage could result in loss of customer trust and potential legal ramifications. Strategically, prolonged exposure to such threats can erode competitive advantage and increase vulnerability to future attacks, making it imperative that organizations prioritize securing their Kubernetes environments and updating their OpenMetadata installations promptly.
Source Material: Microsoft, Attackers exploiting new critical OpenMetadata vulnerabilities on Kubernetes clusters
Popular IP Scanning Websites Spoofed to Target IT Teams, Delivering Backdoors
Spear-Phishing – Malvertising – Threat Actor – Malware – Backdoor – DLL Sideloading – Living Off The Land Binaries and Scripts (LOLBAS) – Carbanak – MadMxShell – PowerShell Execution – FIN7 – Manufacturing – All industries
Overview
In late 2023, BlackBerry identified a spear-phishing campaign targeting employees in the IT department with higher administrative rights of a large automotive manufacturer in the United States. They used the lure of a free IP scanning tool to deploy the Carbanak backdoor and gain an initial foothold by utilizing living off-the-land binaries, scripts, and libraries (LOLBAS). There is evidence that this attack was part of a broader campaign by the adversary.
Beginning in March of 2024, Zscaler identified a malicious Google advertising campaign (malvertising) that targeted IT teams with higher administrative rights. They used the lure of a free IP scanning tool to deploy a previously unobserved backdoor and gain an initial foothold leveraging multiple stages of DLL sideloading, abusing the DNS protocol for communicating with the command-and-control (C2) server, and evading memory forensics security solutions.
Due to its level of sophistication, the spear-phishing campaign is highly likely conducted by a group (BlackBerry attributes the campaign to FIN7). In contrast, the malicious advertising campaign could have been undertaken by a group member or someone who has knowledge of the group’s operations.
Threat Analysis
Spear-Phishing Campaign
In the case observed by BlackBerry, IT employees with high levels of access were sent spear-phishing emails that linked to the website “advanced-ip-sccanner[.]com”, a malicious URL masquerading as the legitimate website “advanced-ip-scanner[.]com”, a free online scanner.
The adversary registered multiple domains within minutes of the original on the same provider, indicating that this campaign was not limited to the one detected but may, in fact, be part of a wider campaign by the adversary.
This fake site redirected visitors to “myipscanner[.]com”, which redirected them to an adversary-owned Dropbox that downloaded the malicious executable WsTaskLoad.exe onto the victim’s machine. WsTaskLoad.exe has a multi-stage execution to run the final Carbanak backdoor.
WsTaskLoad.exe first loads jutil.dll, which executes the exported function SizeSizeImage. Then, jutil.dll reads and decrypts infodb\audio.wav at offset 0x30f21 with size 0x256e; the decrypted blob is a shellcode that is copied from the previously loaded mspdf.dll and executed via EnumWindows().
The shellcode reads and decrypts infodb\audio.wav at offset 0xc2bc1 with size 0x150600; the decrypted blob is a loader, which is later loaded and executed by the shellcode.
Finally, the loader looks for files in the current directory and checks for a specific mark: the mark matches on dmxl.bin and dfmopen.db; during execution, BlackBerry observed dmxl.bin being used as likely open.db for redundancy. The decrypted dmxl.bin is the Carbanak backdoor, with the campaign ID “rabt4201_x86.”
Later, WsTaskLoad.exe manages the dissemination of scripts and establishes persistence. The first thing WsTaskLoad.exe runs upon installation is a POWERTRASH-obfuscated PowerShell script, 3CF9.ps1. POWERTRASH is a custom obfuscation of the shellcode invoker in PowerSploit. WsTaskLoad.exe then checks system and network information on the host machine, gathering user information.
Next, OpenSSH, a connectivity tool for remote login with the SSH protocol, is installed to establish persistence. A scheduled task is then created for OpenSSH, and ports in the firewall are opened. WsTaskLoad.exe then collects basic system information. Post-compromise, the adversary used OpenSSH for external access.
Malvertising Campaign
In another likely separate but similar campaign, Zscaler discovered an adversary registered multiple look-alike domains spoofing popular port scanning software and ran Google Ads campaigns so they would appear at the top of Google search results, a technique widely known as malvertising. Users were served these ads when they searched for keywords related to legitimate port scanning and IT management software, such as Advanced IP Scanner, Angry IP Scanner, Manage Engine, and Scanning IP protocol.
Once the user clicks on any adversary-controlled Google Ads, they are redirected to a look-alike site for the corresponding IP scanning software. One such site is advansed-ip-scanner[.]net, a look-alike site of the legitimate Advanced IP scanner software www.advanced-ip-scanner[.]com. The complete source code of this fake website mirrors the legitimate site, except for minor edits to JavaScript (JS) code, which results in the download of a malicious ZIP archive named Advanced-ip-scanner.zip when the user clicks the download button.
The ZIP archive contains two files: Advanced-ip-scanner.exe, a renamed copy of the legitimate Microsoft executable oleview.exe, and IVIEWERS.dll, a 22 MB DLL padded with an unused overlay of 10 MB. This DLL contains the stage two payload, and the padding likely prevents scanning by security products that limit the size of files that can be analyzed.
When Advanced-ip-scanner.exe is run, it sideloads IVIEWERS.dll, which executes a series of heavily obfuscated shellcodes extracted from various locations within DLL. The final shellcode extracts and decodes an executable file from a resource of the DLL and injects it into a new Advanced-ip-scanner.exe process via process hollowing.
The injected executable file is 10MB and contains the payloads for the subsequent stage in its resources, which are encoded and compressed with zlib. After decoding and decompressing the payloads, two files, OneDrive.exe and Secur32.dll, are dropped into % LOCALAPPDATA%MicrosoftOneDriveUpdate.
The injected executable then deletes the stage 1 executable, Advanced-ip-scanner.exe, before executing the dropped OneDrive.exe with ShellExecuteExW. OneDrive.exe, a legitimate signed Microsoft executable, then sideloads Secur32.dll, which sets up persistence for OneDrive.exe before executing the embedded final shellcode.
Secur32.dll then attempts to disable Windows Defender by setting HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware to 1 in the registry. It then configures a scheduled task named “OneDrive Update” that executes OneDrive.exe when the current user logs on to Windows before redirecting to the final stage.
The final payload is a backdoor that allows the threat actor to collect system information, execute commands via cmd.exe, and perform basic file manipulation operations such as reading, writing, and deleting files.
The backdoor sends requests to the command and control (C2) server, litterbolo[.]com, by encoding the data in the subdomain(s) of the Fully Qualified Domain Name (FQDN) in a DNS MX query packet. The C2 responds similarly by encoding its commands as subdomain(s) in the corresponding DNS MX response packet.
A custom encoding scheme transfers binary data, converting each byte into a pair of alphanumeric characters. This process is carried out using a 36-character lookup table. To represent a subdomain name, blocks of 60 alphanumeric characters are separated by a “.” character. However, because the FQDN’s maximum limit is 224 characters, and the C2 domain name cannot encode data, each DNS packet can only transfer up to 103 bytes. If the data to be transferred exceeds this size, it is split into multiple DNS packets and sent sequentially after receiving an acknowledgment of receipt of the previous packet from the client.
Possibly due to the limited bandwidth of the C2 protocol, the adversary configured this backdoor with 3-second intervals between requests. Because of this, its C2 traffic is significantly more noisy than the typical malware utilizing HTTP for C2 communication.
For each session, the backdoor first sends a registration request (type 1) to the C2 server. Once the C2 server acknowledges the registration request, the backdoor sends a heartbeat status (type 0) to the C2 server. For example, the C2 server for this sample always responded with the following heartbeat status: 33qqooggxr77mdxx88jj6600ev44yyzz9bee99wwuu.litterbolo.com. Zscaler has developed Python code for decoding subdomains in DNS MX queries and responses.
The adversary can then send commands, such as collecting system information, executing commands, or performing various file actions. The backdoor will then acknowledge the command by sending a command acknowledgment status (type 2) before executing the specified command. After completing the commands, the backdoor sends the results to the C2 server. The malware then repeats the process by sending a heartbeat status (type 0) to retrieve the following command.
During their investigation, Zscaler observed that the backdoor received the following commands from the C2 server:
- Collect system information (command type 4).
- Run systeminfo and ipconfig via cmd.exe (command type 5).
- Enumerate drives and specific directories, particularly the Windows system and user directories (command type 6).
The backdoor received some of the commands 60 to 90 minutes after registering with the C2 server, which may indicate hands-on activity by the adversary or an anti-analysis technique to defeat sandboxes.
The domain advansed-ip-scanner[.] net’s WHOIS information revealed that the registration email address was wh8842480@gmail[.]com. A reverse WHOIS lookup on this email address revealed 45 domains spoofing various network scanning and IT management software were registered between November 2023 and March 2024. The adversary hosted these domains on servers exclusively leveraged by the adversary and belonged to the ASNs AS208312 (REDBYTES, RU) and AS16276 (OVH, FR). Furthermore, the C2 domain litterbolo[.]com used the dedicated nameservers coco.bunny.net and kiki.bunny.net.
Risk & Impact Assessment
Given the specific targeting and sophistication of the campaigns described, the likelihood of organizations being targeted is highly likely. For instance, the manufacturing sector is known to be targeted by ransomware actors due to their perceived likelihood of paying the ransom demanded. These tailored spear-phishing and malvertising techniques indicate a methodical approach to target IT employees who may need these tools to perform their day-to-day duties. The probability of further exploitation remains high if preventative measures are not implemented promptly.
The risks associated with these campaigns are significant. The deployment of the backdoors reflects a high level of adversarial capability, suggesting the potential for extensive unauthorized access to sensitive systems and data. Leveraging various techniques to mask command and control (C2) communications is particularly concerning, as it can be challenging to detect and mitigate. This challenge enables sustained access to targeted networks, escalating the risk of extensive data breaches, surveillance, and potentially disruptive actions against critical systems.
The impact on organizations affected by these campaigns can be profound. Successful deployment of the discussed backdoors allows adversaries to establish persistent access to network systems, enabling continuous monitoring and data extraction. This persistent access could lead to significant intellectual property theft, operational disruption, and financial loss.
The potential for these activities to escalate to more destructive actions, such as ransomware deployment, further increases the gravity of the impact. Additionally, the reputational damage and loss of customer trust in the event of a public breach disclosure are critical considerations for affected organizations. The strategic long-term implications include increased costs for cybersecurity enhancements, potential legal liabilities, and the need for extensive recovery efforts to restore trust and secure infrastructure.
Source Material: BlackBerry and Zscaler
Malware Campaign Deploys New CR4T Backdoor
Malware Campaign – Dropper – Backdoor – DuneQuixote Dropper – CR4T Backdoor – Public Administration, All Industries
The discovery of the DuneQuixote campaign by Kaspersky in February 2024 underscores a persistent and evolving threat landscape with potential implications for global cybersecurity. This campaign, characterized by deploying sophisticated malware, including the CR4T backdoor, signifies an advanced persistent threat with capabilities that could undermine national security and organizational integrity across various sectors.
Threat Analysis
The initial infection vector for the DuneQuixote malware campaign remains unknown, contributing to the complexity and stealth of the attacks. The initial artifact identified in the initial stage of the infection is a Windows x64 executable file, which was the initial DuneQuixote dropper. Notably, equivalent functionalities are observed in Dynamic Link Library (DLL) dropper versions, suggesting a versatile approach to maintain persistence and compatibility across different system configurations.
Regular DuneQuixote Dropper Analysis
The regular dropper is developed predominantly in C/C++ without using the Standard Template Library (STL). Not using STL indicates a deliberate avoidance of higher-level abstractions potentially to minimize the dropper’s footprint and detection surface. Furthermore, segments of the code are crafted in pure Assembler, which likely serves to optimize certain functionalities and evade signature-based detection mechanisms. A common trait across all analyzed samples is the presence of invalid digital signatures, which, while ostensibly legitimate, further hint at the sophisticated methods employed by the adversaries to mask their malicious intentions.
Upon execution, the regular dropper engages in anti-analysis and detection activities, notably making decoy API calls with no purpose, as various samples incorporate different snippets from Spanish poems. This unusual behavior not only masks this dropper’s actual operations but also alters its digital signature across different instances, making it challenging to detect through traditional signature-based methods.
This dropper employs advanced techniques to dynamically resolve essential Windows API calls, which are critical for its operation and further evasion. It starts by decrypting the names of key system libraries using a simple XOR decryption algorithm, avoiding static detection tools that scan for known malicious signatures.
Furthermore, the regular dropper conceals its communication with the command-and-control (C2) server through a unique method that involves combining the executable’s filename with a hardcoded string from the aforementioned Spanish poems and then hashing the result. The hash is then used to decrypt the C2 server address. This method prevents automated analysis systems from obtaining the C2 server address.
Payload retrieval from the C2 server is only released when the backdoor receives a request with a specifically hardcoded ID as the user agent. During the investigation, Kaspersky could not obtain most payload implants from active C2 servers. This failure may result from the payload only being allowed to download once per victim or available for a brief period following the deployment of a dropper sample.
Once the payload is downloaded into the process’s memory, the dropper performs a verification check, likely confirming that the payload has an MZ file signature, indicating that it is a valid executable format.
Tampered Installer Analysis
The other DuneQuixote dropper, the tampered installer dropper, is the legitimate Total Commander software installer, with an added malicious file section (.textbss) and a modified entry point. This tampering invalidates the official digital signature of the Total Commander installer.
The tampered installer dropper retains the regular dropper’s core functionality but has several key differences. Unlike the regular dropper, it omits the use of Spanish poem strings and the execution of decoy functions. It also implements anti-analysis measures and checks that, if any of the conditions are true, it prevents a connection to the C2 server by removing the first “h” from the beginning of the C2 URL (“https“), effectively changing it to “ttps. “ As a result, the altered URL prevents establishing a connection to the C2 server.
Backdoor Analysis
The deployed payload is the backdoor, CR4T, which provides the adversary a console for command-line execution on the victim’s machine. Additionally, it facilitates file download, upload, and modification. There are two variants of the CR4T Backdoor: a C version and a Golang version.
Upon execution by the dropper, the CR4T Backdoor C version initiates a cmd.exe process in a hidden window and establishes inter-process communication. It then configures the user agent for communication with the C2 server as “TroubleShooter.”
After that, the backdoor retrieves the infected host’s computer name and the current user’s username. Then, it establishes a connection to the C2 server. After establishing the connection, the backdoor remains idle, awaiting an initial command from the adversary. A one-byte value represents these commands, each mapped to a specific action to be performed on the infected system. For instance, the value “C” provides access to the command line console, “D” downloads a file from the C2 server, “U” uploads a file to the C2 server, and “T” writes to a file.
The Golang variant of the CR4T Backdoor shares capabilities similar to the C version. However, there are notable differences. The Golang version can create scheduled tasks, leveraging the Windows Component Object Model (COM) object interfaces to interact with the Task Scheduler service.
During the analysis, it was discovered that the adversary was observed, likely using the Golang version, retrieving the names of all scheduled tasks on the infected machine beginning with “User_Feed_Sync. “ A file containing the following PowerShell command was created using the “T” command:
"powershell -c \"Get-ScheduledTask | Where-Object {$_.TaskName -like 'User_Feed_Sync*' -and $_.State -eq 'Running'} | Select-Object TaskName\"The Golang variant can also achieve persistence by utilizing the COM objects hijacking technique. Finally, it uses the Telegram API for C2 communications, implementing the public Golang Telegram API bindings. All the interactions are similar to those of the C/C++ version.
Risk & Impact Assessment
Considering the limitations in Kaspersky’s telemetry in the United States and other Western countries, the likelihood that U.S.-based organizations have been or will be targeted by the DuneQuixote campaign is likely. This assessment acknowledges the observed gaps in data due to the less widespread deployment of Kaspersky’s cybersecurity products in these regions, which obscures the full scale of the campaign.
Furthermore, the submission of droppers from VPN exit nodes in countries like the United States further complicates this assessment, masking the actual origin of submissions. The likely assessment reflects this uncertainty and the possibility that U.S. organizations could become targets either directly or as collateral in broader campaigns intended for global reach. Given these considerations, U.S.-based organizations, particularly those with significant Middle Eastern interactions or that operate within critical infrastructure sectors, should maintain heightened vigilance.
The risk to organizations impacted by this campaign stems primarily from the sophistication of the malware involved. The impact of the sophisticated malware involved can be broadly categorized into operational, financial, strategic, and reputational effects.
Operational impacts primarily stem from disruptions caused by detection and remediation efforts rather than direct actions by malware. These disruptions include the temporary shutdown of systems, the diversion of IT resources to handle the incident, and potential slowdowns in regular activities as systems are checked and malware eradicated. Although the campaign’s primary aim is likely espionage, the necessity of thorough forensic investigations and remediations can lead to significant operational inefficiencies.
Further, the presence of a backdoor allows for persistent access, which carries the risk of future operational impacts if left undetected. This persistent access means that threat actors could potentially leverage the backdoor to conduct disruptive activities in the future if their goals change or if they seek to leverage their access for reasons beyond espionage, such as ransomware deployment.
Financially, organizations will incur expenses in identifying, containing, and eradicating the malware from their networks, along with restoring systems to normal operations. If data breaches involve sensitive or personal data, organizations may also face regulatory fines and legal challenges, adding to financial burdens.
Strategically, intellectual property theft could have long-term consequences, including loss of competitive advantage and damage to future business prospects. Addressing the risks exposed by such a campaign might also require substantial investment in upgrading cybersecurity measures, which could divert funds from other strategic initiatives.
Reputationally, a successful breach, especially of sensitive data, can significantly lose trust among stakeholders, partners, and the public. This is particularly damaging for entities where public trust is foundational. Furthermore, news of a significant cybersecurity breach can lead to immediate penalties and long-term damage to market position.
Given the complex and interconnected impacts identified, organizations must enhance their defensive and responsive cybersecurity capabilities and develop a holistic approach to risk management to anticipate and mitigate potential threats posed by campaigns like DuneQuixote.
Source Material: Kaspersky (SecureList), DuneQuixote campaign targets Middle Eastern entities with “CR4T” malware
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Information – Health Care and Social Assistance – Transportation and Warehousing
In the past week, 84 organizations were listed on various data leak sites, with the majority operating in the Manufacturing sector. Our analysis identifies “Lockbit,” “RansomEXX,” and “Alphalocker” as the top active leak sites over the observed period. These sites are crucial in the ransomware ecosystem for publicizing breaches and extorting victim organizations to comply with ransom demands.
Manufacturing, Professional, Scientific, Technical Services, and Information are the most heavily involved industries. These sectors are highlighted due to their significant representation in the listings, indicating a higher risk of exposure and potential targeting.
Geographically, the United States leads with the highest number of organizations geolocating to this region, followed by Canada and Taiwan. This distribution suggests a possible concentration of activities in these regions, reflecting either a higher number of potential targets or specific characteristics that make these countries appealing to cybercriminals.
Industry Analysis
Our industry-focused analysis delineates the sectors most prominently featured on the monitored leak sites, with 16 industries identified in the dataset. The Manufacturing sector leads, with 19 organizations listed, the Professional, Scientific, and Technical Services sector with 12, and the Information sector with ten listings.
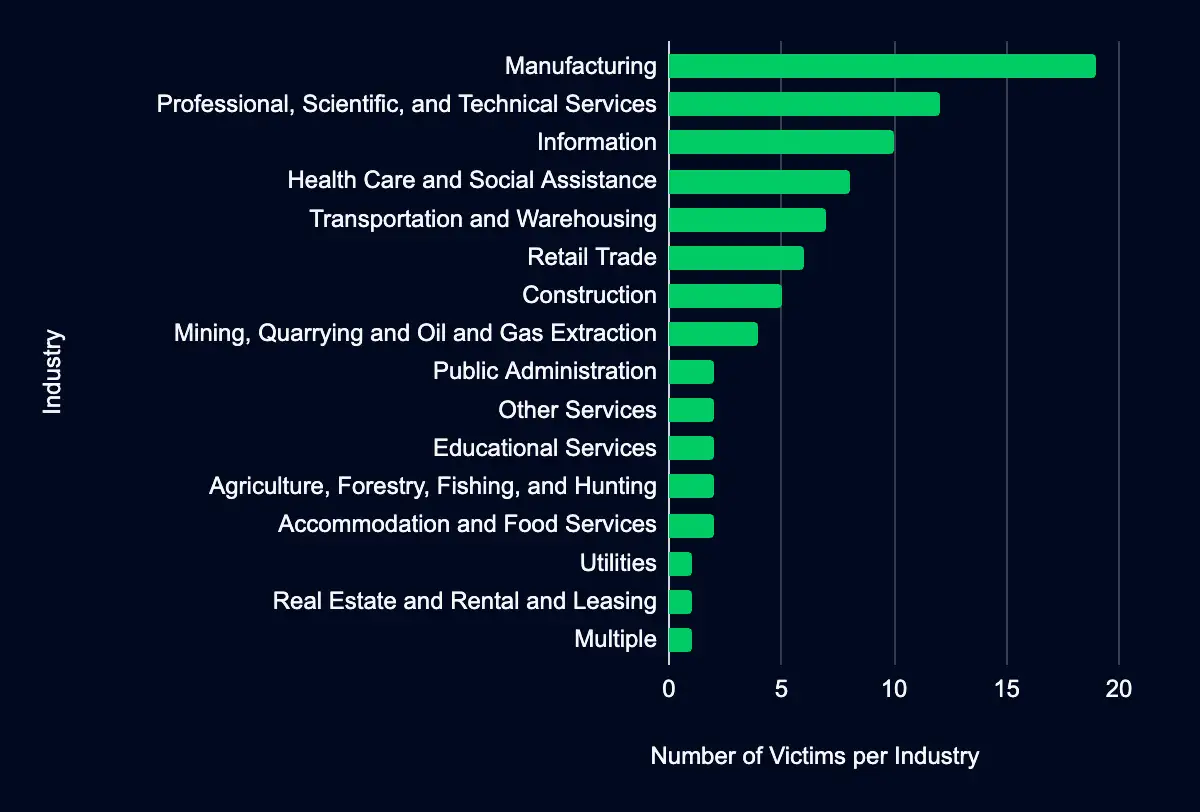
Implications
Data analysis from prominent leak sites such as Lockbit, RansomEXX, and Alphalocker yields critical insights for organizations within the most frequently targeted industries: Manufacturing, Professional, Scientific, and Technical Services, and Information. Organizations in these sectors are advised to promptly reassess their cybersecurity frameworks, particularly identifying and reinforcing any vulnerabilities that ransomware operators might exploit. This reassessment is especially crucial for industries that consistently appear across the leak sites, indicating a heightened risk of exposure and potential targeting.
Moreover, the data demands a strategic response from organizations in the countries most often listed, including the United States, Canada, and Taiwan. These organizations should leverage these findings to enhance their strategic approaches to cyber defense, concentrating efforts on industries disproportionately affected by the data leaks. Such proactive and informed responses are vital for mitigating risks tied to the ransomware landscape outlined in the leak site listings.
Organizations must consider these insights as part of a broader cybersecurity strategy. Integrating this data with additional intelligence and risk assessments will allow for developing a comprehensive and adaptive approach to cybersecurity. The objective is to leverage the data as a strategic tool to boost cybersecurity readiness and resilience, not to rely on it as the exclusive basis for security decisions.
Ultimately, the principal lesson from this analysis is the necessity of data-driven, targeted cybersecurity actions for the specified industries and countries. By tailoring their defense strategies to align with the particular risks and trends identified, organizations can proactively confront the challenges posed by ransomware threats, thus enhancing their overall cybersecurity posture in a dynamic threat landscape.
CISA Adds 4 CVEs to Known Exploited Vulnerabilities Catalog
Cisco ASA and FTD CVE-2024-20353 & CVE-2024-20359 – CrushFTP VFS CVE-2024-4040 – Microsoft Windows Print Spooler CVE-2022-38028
In the past week, CISA added four (4) CVEs to its Known Exploited Vulnerabilities Catalog, impacting Cisco, CrushFTP, and Microsoft products. These vulnerabilities can have severe consequences, including arbitrary code execution. At this time, these vulnerabilities are not known to have been used in ransomware campaigns.
Analysis
CVE-2024-20353 and CVE-2024-20359 impact Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software. These vulnerabilities allow for the preloading of VPN clients and plug-ins and have been available in Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software, which could allow an authenticated, local adversary to execute arbitrary code with root-level privileges. Administrator-level privileges are required to exploit this vulnerability. CISA recommends that mitigation occur by 1 May 2024.
The vulnerabilities are due to improper file validation when files are read from system flash memory. An adversary could exploit this vulnerability by copying a crafted file to the disk0: file system of an affected device. A successful exploit could allow the adversary to execute arbitrary code on the affected device after the next device reboot, which could alter system behavior. Because the injected code could persist across device reboots, Cisco has raised this advisory’s Security Impact Rating (SIR) from Medium to High.
A state-sponsored adversary targeted perimeter network devices from multiple vendors since November 2023 to breach government networks worldwide. The adversary, identified as UAT4356 by Cisco Talos and STORM-1849 by Microsoft, began infiltrating vulnerable edge devices in early November 2023 in a cyber-espionage campaign tracked as ArcaneDoor. However, Cisco has not yet identified the initial attack vector; they did discover two vulnerabilities— CVE-2024-20353 (denial of service) and CVE-2024-20359 (persistent local code execution)—the adversary leveraged as zero-days in these attacks.
The two vulnerabilities allowed threat actors to deploy previously unknown malware and maintain persistence on compromised ASA and FTD devices. One of the malware implants, Line Dancer, is an in-memory shellcode loader that helps deliver and execute arbitrary shellcode payloads to disable logging, provide remote access, and exfiltrate captured packets. The second implant, a persistent backdoor named Line Runner, comes with multiple defense evasion mechanisms to avoid detection and allows the adversary to run arbitrary Lua code on the compromised systems.
CVE-2024-4040 impacts CrushFTP in all versions before 10.7.1 and 11.1.0 on all platforms. The vulnerability is a server-side template injection that allows an unauthenticated, remote adversary to read files from the filesystem outside of the VFS Sandbox, bypass authentication to gain administrative access and perform remote code execution on the server. This vulnerability has been patched in v11.1.0. According to Censys, there are currently 9,600+ internet-exposed CrushFTP hosts (virtual & physical), mainly in North America and Europe. However, a Shodan query shows that over 7,100 CrushFTP servers are publicly accessible. It is unclear how many of these systems are potentially vulnerable. CISA recommends that mitigation occur by 1 May 2024.
This vulnerability in CrushFTP was exploited in the wild against multiple U.S. entities before fixed versions became available. According to CrowdStrike, CVE-2024-4040 had been exploited in the wild as a zero-day. Specifically, the attacks are targeted , and compromises have been discovered at “multiple U.S. entities” with a focus on “intelligence-gathering” that is “possibly politically motivated.”
CVE-2022-38028 impacts Microsoft Windows Print Spooler service, which contains a privilege escalation vulnerability. An adversary may modify and execute a JavaScript constraints file with SYSTEM-level permissions. CISA recommends that mitigation occur by 14 May 2024.
The Russian-based threat actor Forest Blizzard (STRONTIUM) used the custom tool GooseEgg to exploit CVE-2022-38028, elevating privileges and stealing credentials in compromised networks. Microsoft has observed Forest Blizzard using GooseEgg as part of post-compromise activities against targets, including Ukrainian, Western European, and North American governments and non-governmental, education, and transportation sector organizations.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share