China-Linked Espionage Targets Ivanti, Scattered Spider Adapts with Broader Attacks, and CISA Adds Critical Vulnerabilities Across Multiple Platforms
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analyses and perspective to shine a light on a spectrum of cyber threats.
Contents
- China Nexus Aims at Ivanti: Exploiting Critical Vulnerability for Cyber Espionage
- Scattered Spider Evolves: 2025 Sees Broader Targets and Smarter Attacks
- Ransomware and Data Extortion Trends (Mar. 31 – Apr. 6)
- Exploited Vulnerabilities in Ivanti, CrushFTP, Microsoft, Gladinet, and Linux Products Added to CISA’s Catalog – Immediate Mitigation Recommende
China Nexus Aims at Ivanti: Exploiting Critical Vulnerability for Cyber Espionage
The Rundown
A recent report from Google Cloud’s Threat Intelligence team highlights that a state-affiliated hacking group tracked as UNC5221 has been actively exploiting a critical vulnerability in Ivanti Connect Secure VPN devices. This vulnerability, identified as CVE-2025-22457, enables attackers to gain unauthorized access to networks without requiring valid login credentials. The exploitation activity began shortly after the vulnerability was publicly disclosed, demonstrating how rapidly sophisticated threat actors like UNC5221 can take advantage of newly discovered security flaws.
These types of VPN appliances are widely used by businesses and government organizations to provide remote access to their networks. By exploiting this flaw, attackers can infiltrate internal systems, potentially access sensitive data, and remain hidden for long periods. Google’s report indicates that the China Nexus group used advanced techniques to maintain persistence and avoid detection, raising serious concerns about the sophistication and long-term impact of these attacks.
For business leaders, this incident underscores the importance of promptly applying software updates and closely monitoring cybersecurity alerts. Organizations that rely on Ivanti devices should ensure all patches are applied immediately and consider conducting a thorough review of their network traffic and access logs. This case is a stark reminder that even well-known infrastructure tools can become attack vectors if not properly secured, and that nation-state actors continue to target businesses for espionage or strategic advantage.
Source Material: Google Mandian
Scattered Spider Evolves: 2025 Sees Broader Targets and Smarter Attacks
The Rundown
Scattered Spider is a cybercriminal group known for executing highly targeted and sophisticated social engineering attacks, with activity tracked since at least 2022. In 2025, analysts observed an expansion in their operations, now targeting major services like Klaviyo, HubSpot, and Pure Storage, alongside prominent brands such as Nike, Louis Vuitton, Twitter/X, and Credit Karma. The group primarily focuses on harvesting usernames, passwords, and multi-factor authentication (MFA) tokens, enabling them to bypass standard security defenses and gain unauthorized access to enterprise systems.
Silent Push researchers identified five unique phishing kits attributed to Scattered Spider, some of which have been updated or replaced, indicating a shift in the group’s operational strategy. A newly uncovered version of the Spectre Remote Access Trojan (RAT) shows the group’s efforts to maintain long-term access to breached networks. In a notable move, Scattered Spider acquired a previously legitimate domain once owned by Twitter/X—”twitter-okta[.]com”—suggesting possible impersonation efforts aimed at Twitter/X’s infrastructure or users.
These patterns signal that Scattered Spider is not only increasing its technical sophistication but also broadening its target base across industries. Business leaders should take this as a warning to bolster their cybersecurity posture, proactively monitor for indicators of future attacks, and train staff to recognize and report phishing and impersonation attempts.
Source Material: Silentpush
Ransomware and Data Extortion Trends (Mar. 31 – Apr. 6)
The Rundown
Ransomware and data extortion activity includes a sharp increase between March 31 – April 6, with an 132% decrease in listed organizations compared to the previous week.
The sharp surge in new ransomware victims, 135 more than the previous week, underscores the rapidly escalating threat and relentless evolution of ransomware operations targeting organizations. This dramatic spike reflects how threat actors are not only increasing their attack volume but also diversifying their targets across industries and regions with alarming speed.
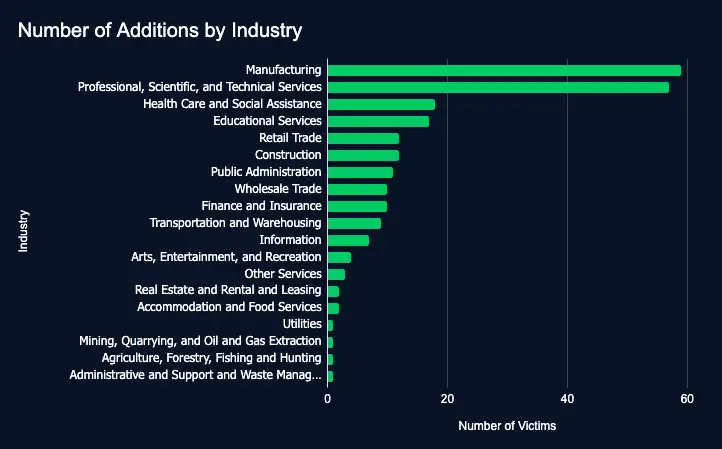
In the reporting time frame, 237 organizations across 19 industries were listed on 27 ransomware and data extortion leak sites, marking a sharp increase from the previous week’s 102 victims.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Health Care
- Most affected countries:
- United States
- Australia
- Germany
- Most active leak sites:
- Safepay
- Killsecurity
- Akira
Exploited Vulnerabilities in Ivanti, CrushFTP, Microsoft, Gladinet, and Linux Products Added to CISA’s Catalog
The Rundown
Between April 3rd and 9th, 7 critical vulnerabilities affecting Ivanti, CrushFTP, Microsoft, Gladinet, and Linux products were added to CISA’s Known Exploited Vulnerabilities catalog. If left unpatched, these vulnerabilities could leave organizations vulnerable to cyberattacks.
These newly discovered vulnerabilities highlight critical risks for organizations dependent on widely used technologies. Given the potential targeting by state-sponsored and cybercriminal actors, swift action is crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share