Phishing Exploits TryCloudflare for RATs, Stealthy Windows Backdoor, Russian APT’s Free Service Malware, StormBamboo’s DNS Poisoning, RAT Unveiled in Ransomware Attack, Ransomware Activity Declines, and CISA Updates
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- How Phishing Emails Use TryCloudflare to Spread RATs
- New Stealthy Backdoor Utilizes Windows Built-in File Transfer Service
- Phishing Campaign by Russian APT Leverages Free Services to Spread Malware
- StormBamboo’s DNS Poisoning Attack Exposes Critical Software Update Flaws
- RAT Used for Initial Access Unveiled in Ransomware Attack
- Ransomware Activity Falls; US Manufacturing Still Most Affected
- CISA Adds CVE-2018-0824 to Known Exploited Catalog
How Phishing Emails Use TryCloudflare to Spread RATs
Phishing – Malware – Remote Access Trojan – AsyncRAT – Xworm – VenomRAT – GuLoader – Remocos – All Industries
The Rundown
Proofpoint is tracking phishing campaigns that use a TryCloudflare subdomain to deliver various remote access trojans (RATs). First observed in February 2024, the cluster escalated its activity from May through July. Later campaigns delivered AsyncRAT and Xworm RAT, while previous campaigns also delivered VenomRAT, GuLoader, and Remcos.
While the attack chain requires significant victim interaction, which provides multiple opportunities to identify suspicious activity, TryCloudflare provides attackers with free temporary infrastructure that doesn’t require the attacker to make an account, giving them the flexibility to build and take down instances. This temporary infrastructure makes it harder for defenders as traditional security measures and static blocklists are ineffective.
Source Material: Proofpoint
New Stealthy Backdoor Utilizes Windows Built-in File Transfer Service
Malware – Backdoor – Background Intelligent Transfer Service (BITS) – BITSLOTH – Targeted Latin America (LATAM) – All Industries
The Rundown
Elastic Security Labs has discovered a new Windows backdoor dubbed BITSLOTH. It uses the BITS for command and control communications and has advanced data collection, keylogging, and screen capture capabilities.
BITSLOTH’s use of BITS for command and control communications allows it to blend in with legitimate network traffic, making it extremely difficult for traditional detection systems to identify and block. This backdoor’s advanced capabilities can lead to significant data breaches and compromises of sensitive information. Understanding BITSLOTH’s mechanisms is crucial for organizations to enhance security measures and protect against stealthy threats.
Discovered during an investigation into an intrusion in South America, BITSLOTH exploits the Background Intelligent Transfer Service (BITS) to seamlessly integrate its malicious activities into legitimate network traffic, making it exceptionally difficult to detect.
This report provides a high-level overview of BITSLOTH’s communication methods, persistence mechanisms, and detection challenges to help organizations safeguard against this sophisticated threat. For a deeper technical analysis, please consult Elastic Security Lab’s report.
Source Material: Elastic
Phishing Campaign by Russian APT Leverages Free Services to Spread Malware
Russian Threat Actor – Phishing – Malware – Backdoor – HeadLace – All Industries
The Rundown
A recent Palo Alto Unit 42 blog post details a phishing campaign by Russian threat actor Fighting Ursa, targeting diplomats with a “car for sale” lure. The post highlights the group’s use of free, legitimate services for malware deployment and the persistent and evolving threat from advanced persistent threats (APTs).
This campaign, active since March 2024, demonstrates how Fighting Ursa, also known as APT28 or Fancy Bear, exploits legitimate web services like Webhook.site to deliver the HeadLace backdoor. The use of such services not only complicates detection efforts but also serves as a potential blueprint for other cybercriminals, amplifying the threat landscape.
Source Material: Palo Alto Unit 42
StormBamboo’s DNS Poisoning Attack Exposes Critical Software Update Flaws
DNS Poisoning – Malware – MACMA (macOS) – POCOSTICK (Windows) – RELOADEXT – StormBamboo – Evasive Panda – Chinese APT – All Industries
The Rundown
A recent Volexity blog post details a DNS response poisoning attack conducted by StormBamboo, a notorious and highly skilled Chinese threat group that has successfully compromised an Internet Service Provider (ISP) to abuse insecure software update mechanisms, targeting macOS and Windows systems. This breach has led to the deployment of POCOSTICK, new variants of the MACMA malware, and a malicious Chrome extension, RELOADEXT.
This attack underscores the critical weaknesses in current software update practices. By compromising an ISP, StormBamboo deployed malware that could exfiltrate sensitive data, highlighting the urgent need for organizations to ensure secure update mechanisms, such as using HTTPS and validating digital signatures, are used to protect against sophisticated cyber threats.
StormBamboo has demonstrated a sophisticated approach by compromising third parties to breach their intended targets. The variety of malware employed in various campaigns by StormBamboo indicates significant effort, with payloads developed for macOS, Windows, and network appliances. The group has shown capabilities to intercept and poison DNS requests, redirecting them to malicious IP addresses and exploiting automatic update mechanisms that use HTTP rather than HTTPS.
Source Material: Volexity
RAT Used for Initial Access Unveiled in Ransomware Attack
Ransomware – Malware – Remote Access Trojan (RAT) – Typosquatted Domains – Hunters International – SharpRhino – All Industries
The Rundown
In an August 2nd blog post, Quorum Cyber unveiled their discovery of a new Remote Access Trojan (RAT) named SharpRhino that used a valid code certificate identified during an investigation of a Hunters International ransomware incident.
This discovery underscores the continuous evolution of cyber threats and the necessity for robust detection and response mechanisms. Hunters International’s use of typosquatting and legitimate code certificates highlights attackers’ increasing sophistication, necessitating vigilance, and advanced threat intelligence among cybersecurity professionals.
Source Material: Quorum Cyber
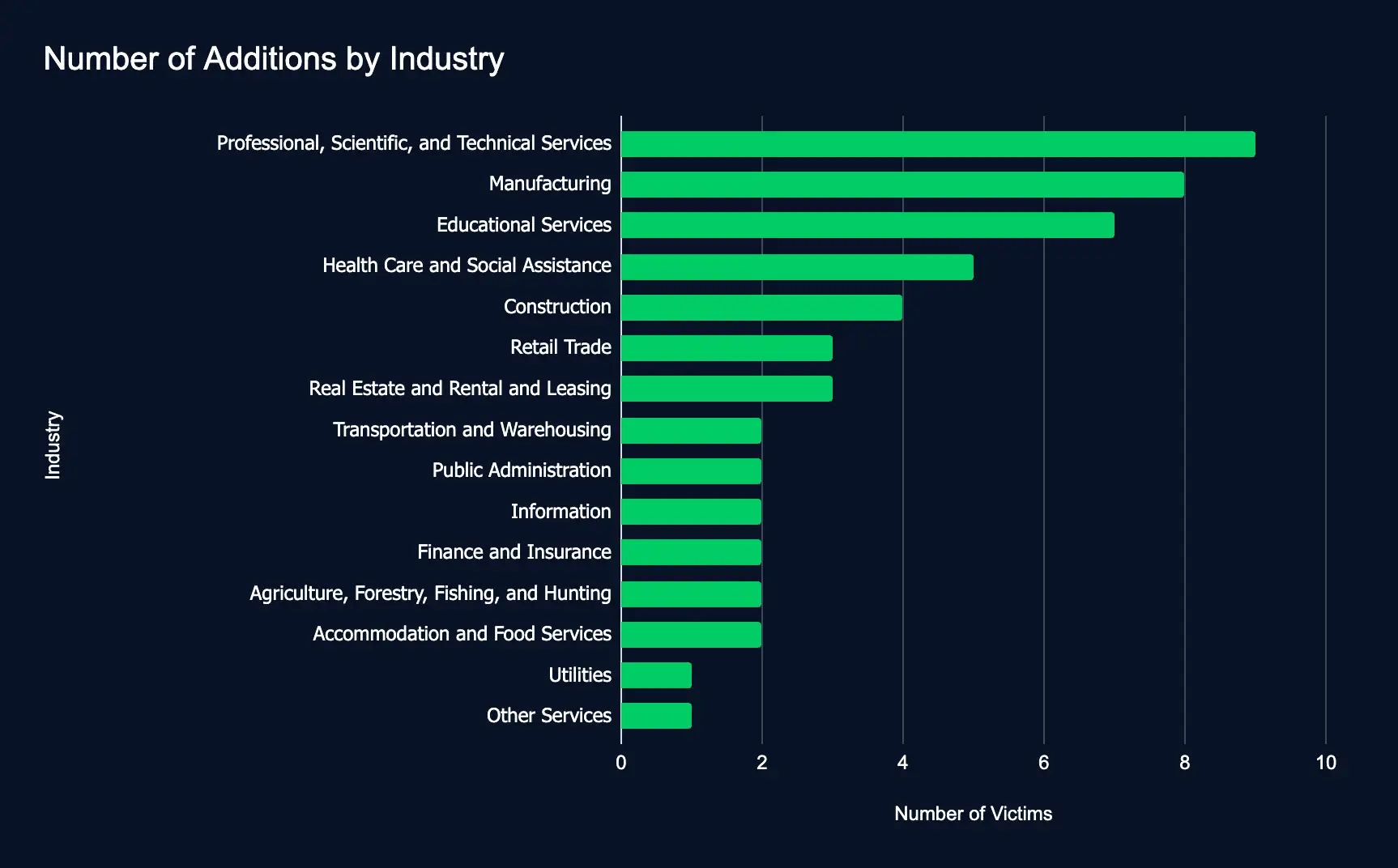
Ransomware Activity Falls; US Manufacturing Still Most Affected
Professional, Scientific, and Technical Services – Manufacturing – Educational Services – Health Care and Social Assistance
The Rundown
Ransomware attacks significantly dropped from last week’s 100, adding 53 organizations to data leak sites. The Professional, Scientific, Technical Services, and Manufacturing sectors bore the brunt of the impact.
This decrease in ransomware attacks still highlights the persistent threat to organizations. The Professional, Scientific, Technical Services, and Manufacturing sectors were the most targeted in the past week, and have been this year, underscoring the need for robust cybersecurity measures.
CISA Adds CVE-2018-0824 to Known Exploited Catalog
Microsoft COM for Windows CVE-2018-0824
The Rundown
CISA has added the high-severity Microsoft COM for Windows vulnerability CVE-2018-0824 to its Known Exploited Vulnerabilities (KEV) catalog. APT41 has been observed exploiting this vulnerability to escalate privileges.
This vulnerability in Microsoft COM for Windows allows for remote code execution and privilege escalation, posing a significant threat to systems worldwide. Its inclusion in CISA’s KEV catalog underscores the urgency for users to update their systems to the latest versions to mitigate potential attacks.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share