PEAKLIGHT Memory-Only Malware Uncovered, Qilin Ransomware Strikes, ShinyHunters Target AWS in Extortion Campaign, 65 Firms Leaked, and CISA Adds New Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
New Memory-Only Malware Dropper, PEAKLIGHT, Discovered
The Rundown
A sophisticated, memory-only malware dropper named PEAKLIGHT, discovered by Mandiant, has emerged as a serious threat due to its ability to evade detection and deliver malware-as-a-service (MaaS) infostealers across various sectors.
PEAKLIGHT’s advanced multi-stage attack, which exploits legitimate utilities and content delivery networks, highlights a concerning shift in cyber threats, making it difficult to detect and eradicate. PEAKLIGHT escalates the risk of data breaches, particularly in high-value sectors, presenting a significant challenge to cyber resilience.
Source Material: Mandiant
Qilin Ransomware Steals Credentials, Encrypts Systems in July Attack
The Rundown
In July 2024, the Qilin ransomware group introduced a novel method to steal credentials saved in Google Chrome. They did this by deploying a harmful script via a Group Policy Object (GPO).
This event highlights the critical need for businesses to go beyond merely blocking ransomware encryption. Companies must also protect credentials that could be misused in future breaches. A well-rounded cybersecurity strategy is key, which should include multi-factor authentication (MFA), strong password management practices, and restricting the storage of passwords within browsers.
Source Material: Sophos
Extortion Campaign by ShinyHunters Targets AWS
The Rundown
A recent Palo Alto Unit 42 blog post describes a cloud extortion campaign similar to their previous blog post. These attacks are attributed to Bling Libra, the attackers behind the data extortion group ShinyHunters. The blog post highlights how Bling Libra gained access to AWS environments using access keys exposed in sensitive files.
This extortion campaign marks an evolution in Bling Libra’s attacks, demonstrating how they leverage exposed files for initial access and WinSCP to delete S3 buckets. The implications for organizations are severe, extending beyond immediate financial loss and data destruction to long-term risks in supply chain integrity. The incident underscores the urgent need for enhanced cloud security practices.
Source Material: Palo Alto
65 Firms Listed on Data Leak Sites in a Week: Manufacturing and Professional Services Top the List
The Rundown
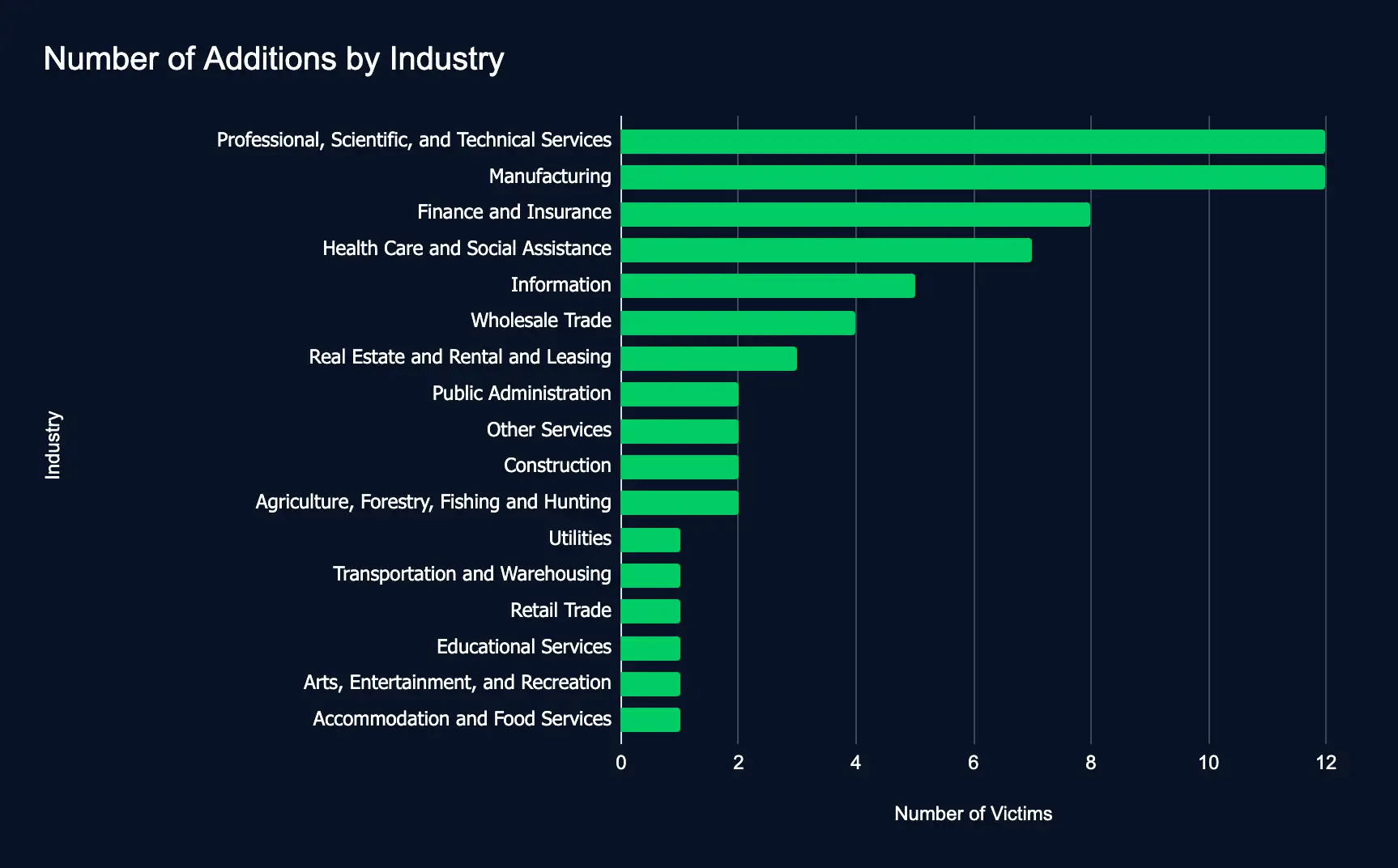
Between August 19 and 25, 2024, 23 data leak sites added 63 organizations, a decline from previous weeks. These organizations span 17 industries across 17 countries. Most of these organizations operate in the Professional, Scientific, Technical Services, and Manufacturing sectors, maintaining their long-standing prominence on data leak sites. These additions underscore attackers’ consistent targeting of critical industries and the need for more robust cybersecurity measures.
CISA Adds Chromium, OFBiz, and Director Vulnerabilities to Exploited List
The Rundown
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added four new vulnerabilities (Google Chromium CVE-2024-7965 & CVE-2024-7971, Apache OFBiz CVE-2024-38856, and Versa Director CVE-2024-39717) to its Known Exploited Vulnerabilities (KEV) catalog.
These vulnerabilities have been actively exploited, and their inclusion in the KEV catalog is a critical warning, signifying that they should be addressed by the recommended mitigation due date.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share