Lazarus Group Deploys RATS, Malware Steals Funds from Brokerage Accounts, and Barracuda’s ESG Vulnerability Keeps Taking Bites
This week: Lazarus Group deploys QuiteRAT along with new CollectionRAT, threat actors exploit WinRAR vulnerability to steal funds from brokerage accounts, Chinese nation-state actor Flax Typhoon seen exploiting known vulnerabilities, and there’s new information on how UNC4841 continues to exploit a vulnerability in Barracuda ESG. All this and the latest from data leak sites and new CVEs.
In our latest Cyber Intelligence Brief, we look at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Cisco Talos: Lazarus Group’s infrastructure reuse leads to discovery of new malware.
- Group-IB: Traders’ Dollars in Danger: CVE-2023-38831 Zero-Day Vulnerability in WinRAR Exploited by Cybercriminals to Target Traders.
- NSFOCUS: Operation DarkCasino: In-Depth Analysis of Attacks by APT Group Evilnum
- Microsoft: Flax Typhoon using legitimate software to quietly access Taiwanese organizations.
- Mandiant: Diving Deep into UNC4841 Operations Following Barracuda ESG Zero-Day Remediation (CVE-2023-2868).
- Seqrite: Exploring Mallox Ransomware: Tactics, Techniques, and Defense.
- The DFIR Report: HTML Smuggling Leads to Domain Wide Ransomware.
- The Latest Additions from Data Leak Sites
- CISA Adds 2 CVEs to its Known Exploited Vulnerabilities Catalog
Lazarus Group: Exploitation of ManageEngine Vulnerability to Deploy QuiteRAT, and Infrastructure Reuse Leads to Discovery of CollectionRAT
A new report aims to provide actionable intelligence to understand the initial access methods and toolsets employed by the Lazarus Group in their most recent campaign. Focusing on these topics, the report aims to equip cybersecurity professionals with the critical information needed to assess risk and fortify defenses against this persistent and evolving threat actor. The scope of this report encompasses the analysis of tactics, techniques, and procedures (TTPs), malware characteristics, and infrastructure details based on two Cisco Talos blog posts to provide a comprehensive understanding of Lazarus Group’s current operational landscape.
In Cisco Talos blog posts, they observed Lazarus Group, an umbrella term used to denote all North Korean threat actors, in early 2023, compromise an internet backbone infrastructure provider in Europe to deploy QuiteRAT. This campaign is their third to be documented in less than a year. Lazarus Group continues using the same infrastructure they used in previously reported campaigns. Their continued use of the same infrastructure and tactics, techniques, and procedures (TTPs), many of which are publicly known, indicates the group’s confidence in their operations. However, this infrastructure reuse led Cisco Talos to identify a new remote access tool called CollectionRAT and additional open-source tools.
In early 2023, the actors exploited CVE-2022-47966, a vulnerability in ManageEngine ServiceDesk, to gain initial access. The successful exploitation triggered the immediate download and execution of a malicious binary via the Java runtime process, which led to the execution of the QuiteRAT, activating the RAT on the infected server. Once the RAT starts running, it sends preliminary system information to its command and control (C2) servers. Then, it waits for the C2 to respond with a command to execute on the endpoint.
QuiteRAT, a derivative of MagicRAT, is a remote access trojan (RAT) that leverages a compact set of statically linked Qt libraries, a framework typically used for developing Graphical User Interfaces (GUIs), though this RAT lacks a GUI. Using Qt increases code complexity, hinders human analysis, and makes machine learning and heuristic analysis detection less reliable. Unlike other RATs, QuiteRAT lacks an in-built persistence mechanism, instead achieving persistence via the registry. Upon infection, it gathers basic information about the endpoint to calculate an MD4 hash for victim identification and communication with the C2 server. The RAT’s functionality includes running a ping command on randomly generated IP addresses, sleeping for specified periods to remain dormant, and receiving URLs from the C2 server to execute commands and payloads on the infected system, tactics likely employed to ensure continued access to compromised networks. The use of MagicRAT’s derivative implant, QuiteRAT, beginning in May 2023, suggests the actor is changing tactics, opting for a smaller, more compact Qt-based implant.
While investigating the infrastructure used by Lazarus Group, Cisco Talos discovered a new RAT. Cisco Talos calls this new RAT CollectionRAT, and it includes standard RAT capabilities, such as running arbitrary commands and managing files on the infected endpoint. It is constructed using a packed Microsoft Foundation Class (MFC) library-based Windows binary, which serves as a complex, object-oriented wrapper to decrypt and execute the malware code. Though traditionally used for creating Windows applications’ user interfaces, MFC, in this context, allows seamless interaction between malware components and abstracts the inner workings of the Windows OS, making human analysis challenging. In CollectionRAT, MFC is used as a wrapper/decrypter for the malicious code. Upon infection, the RAT gathers system information for fingerprinting and communicates with the C2 server to receive commands. Its functionalities include creating a reverse shell, reading and writing files, spawning new processes to download and deploy additional payloads, and even removing itself from the endpoint as directed by the C2 server.
Additionally, Lazarus Group appears to be shifting its tactics, increasingly relying on open-source tools and frameworks in the initial access phase of their attacks instead of strictly employing them in the post-compromise phase. Lazarus Group previously relied on custom-built malware such as MagicRAT, VSingle, DTrack, and Yamabot to establish persistent initial access on a successfully compromised system. These malware are then used to deploy various open-source or dual-use tools to perform many malicious hands-on-keyboard activities in the compromised enterprise network. These include proxy tools, credential-dumping tools, such as Mimikatz, and post-compromise reconnaissance and pivoting frameworks, such as Impacket. However, these open-source or dual-use tools have primarily been used in the post-compromise phase of the intrusion. However, in Lazarus Group’s latest campaign, the actors deployed the DeimosC2 open-source C2 framework as a means of initial and persistent access. DeimosC2 is a GoLang-based C2 framework supporting a variety of RAT capabilities similar to other popular C2 frameworks such as Cobalt Strike and Sliver.
Unlike other malware on their infrastructure, the DeimosC2 is a Linux ELF binary, signaling the group’s intention to deploy it on Linux-based servers during initial access. This Linux ELF binary is an unmodified copy of the regular beacon produced by the DeimosC2’s C2 server, containing standard URI paths consistent with an out-of-the-box configuration. The absence of heavy customization suggests that the operators of DeimosC2 may still be adapting to and integrating the framework into their latest campaign. The DeimosC2 framework possesses various RAT capabilities, including executing arbitrary commands and shellcodes, stealing credentials, dumping the registry, managing files with the C2 server, and uninstalling the malware.
Another open-source tool Cisco Talos observed Lazarus Group using is the reverse tunneling tool PuTTY Link (Plink). In the past, Cisco Talos observed Lazarus Group use Plink to establish remote tunnels. However, Cisco Talos found that Lazarus Group has started generating malicious Plink binaries out of PuTTY’s source code to embed the reverse tunnel command strings in the binary. The malicious Plink will also create a mutex before establishing the remote tunnel to ensure only one connection between the local machine and C2.
Risk & Impact Assessment
The Lazarus Group’s continued reliance on known infrastructure and tactics, techniques, and procedures (TTPs) presents a nuanced risk profile. On the one hand, the group’s use of previously identified and documented methods may lower the likelihood of a successful intrusion for organizations that have implemented recommended mitigative actions, maintained up-to-date threat intelligence, and adapted their defenses to known threats. However, the group’s evolving use of open-source tools and frameworks, such as the DeimosC2 framework for initial access, adds a layer of complexity to the threat landscape. This evolution indicates a willingness to innovate and adapt, potentially circumventing defenses solely focused on previously known TTPs. The group’s ability to shift tactics and incorporate new tools may still pose a risk to organizations that are not continually updating their threat intelligence and adapting their security measures. Furthermore, the Lazarus Group’s targeting of specific vulnerabilities, such as the ManageEngine ServiceDesk, highlights the importance of timely patching and vulnerability management. Organizations that have not addressed these specific vulnerabilities may still be at risk, despite awareness of the group’s known infrastructure and TTPs.
The impact of the Lazarus Group’s activities on organizational operations and corporate assets is substantial. A successful compromise could lead to unauthorized access, disclosure, modification, destruction, or loss of data or information systems, resulting in significant operational disruptions, financial losses, and potential damage to reputation. Deploying various malware families, with their abilities, can lead to extensive data exfiltration and manipulation. Using various open-source tools, like DeimosC2 for initial and persistent access, along with the malicious version of Plink for reverse tunneling, adds to the complexity of the threat, potentially extending the reach and depth of an intrusion.
Threat Actors Exploit WinRAR Vulnerability to Deploy Malware, Withdraw Funds From Brokerage Accounts
This week we look at a report that aims to furnish actionable intelligence of how threat actors can craft malicious ZIP archives to exploit a specific vulnerability in the widely-used WinRAR software, identified as CVE-2023-38831. This exploitation can serve as a delivery mechanism for various malware families, posing a multi-faceted cyber threat. The intelligence is derived from an in-depth analysis of a blog post published by Group-IB, titled “Traders’ Dollars in Danger: CVE-2023-38831 Zero-Day Vulnerability in WinRAR Exploited by Cybercriminals to Target Traders.” A second source, titled “Operation DarkCasino: In-Depth Analysis of Attacks by APT Group Evilnum (Part 2),” supplemented our analysis and was published by NSFOCUS.
The blog post by Group-IB, titled “Traders’ Dollars in Danger: CVE-2023-38831 Zero-Day Vulnerability in WinRAR Exploited by Cybercriminals to Target Traders,” provides an in-depth analysis of a vulnerability in WinRAR that has been actively exploited as a zero-day since April 2023. The blog post details the tactics, techniques, and procedures (TTPs) the threat actors employed to distribute weaponized ZIP archives through specialized trading forums. Once executed, these ZIP archives enable the threat actors to compromise brokerage accounts, leading to the withdrawal of funds from these accounts. The blog post further delves into two malware families observed in the weaponized ZIP archives, DarkMe and GuLoader, detailing their functionalities and delivery methods. The post concludes with recommendations for mitigating the risks associated with this vulnerability, emphasizing patch management and caution when dealing with attachments from unknown sources.
WinRAR, a file archiver utility with over 500 million users worldwide, is a widely used tool for compressing and decompressing files. Its widespread use makes it an attractive target for cybercriminals seeking to exploit vulnerabilities. CVE-2023-38831 is a zero-day vulnerability that affects the processing of ZIP file formats in WinRAR. This security flaw allows threat actors to craft ZIP archives that serve as carriers for various malware families. The vulnerability was discovered by Group-IB’s Threat Intelligence unit and reported to RARLAB, which released a patched software version. The MITRE Corporation assigned the vulnerability the identifier CVE-2023-38831 on August 15, 2023.
DarkMe, initially discovered by NSFOCUS researchers, is a VisualBasic spy Trojan attributed to the financially motivated group Evilnum. DarkMe has multiple modules to support various functions, including executing commands; copying, writing to, renaming, deleting, and reading files; and creating or deleting directories.
GuLoader is a sophisticated malware downloader that has been observed in various campaigns. It is known for evading traditional security solutions through anti-analysis techniques. GuLoader has been used to distribute different types of malware, including Remcos, AgentTesla, FormBook, Nanocore, NETWIRE, Lokibot, and Xloader. The malware employs multiple stages and has been observed using file-sharing sites and cloud-hosting services for payload storage and delivery.
The exploitation of CVE-2023-38831 in WinRAR hinges on manipulating the software’s ZIP file processing capabilities. Specifically, the vulnerability allows the spoofing of file extensions within a ZIP archive, effectively disguising malicious scripts as benign file types such as ‘.jpg’ or ‘.txt.’ Exploiting this vulnerability could let these files bypass security solutions and deliver malicious payloads. When a victim opens a specially crafted ZIP archive, the archive may contain what appears to be a benign (decoy) file and a folder bearing the same name. Clicking on the decoy file triggers the execution of a malicious script, initiating the next stage of the infection chain. This exploitation technique leverages a modified file structure within the ZIP archive, ensuring that the image and script are launched, thereby partially or fully succeeding in the intrusion.
In one campaign exploiting the vulnerability, Group-IB observed threat actors posting malicious ZIP archives on at least eight popular trading forums, ultimately delivering DarkMe and GuLoader malware, which enabled the threat actors to withdraw funds from brokerage accounts.
The threat actors used a complex, multi-stage launch process initiated by the earlier script to launch a Cabinet Self-extractor file (SFX CAB). The main executable, written in VisualBasic, triggers various malicious modules through custom ActiveX controls saved as “.ocx” files. These controls perform specific tasks, such as registering a COM object in the Windows registry and creating a malicious DLL. The control flow is carefully timed and ultimately launches the DarkMe backdoor.
Risk & Impact Assessment
Due to its widespread prevalence, the exploitation of CVE-2023-38831 in WinRAR poses a significant risk to organizations across various sectors. The likelihood of an incident is elevated due to the observed active exploitation by threat actors. Successful exploitation could allow threat actors unauthorized access, disclosure, and modification of data, compromising information systems’ confidentiality, integrity, and availability (CIA). Threat actors have been observed exploiting the vulnerability to deliver sophisticated malware families DarkMe and GuLoader. These malware strains have capabilities ranging from loading other malware to remote access, thereby posing a multi-faceted threat. Organizations that do not promptly address vulnerabilities risk severe disruptions to operations, including potential financial loss and damage to reputation. Organizations that fail to promptly address this vulnerability risk severe operational disruptions, including the potential for financial loss and reputational damage.
The impact of CVE-2023-38831 exploitation is multi-dimensional and extends beyond mere technical ramifications. On an operational level, the vulnerability can compromise sensitive data, including customer and proprietary data, affecting an organization’s core mission and functions. Financially, the exploitation has been observed to facilitate unauthorized transactions, leading to direct monetary losses. Moreover, the impact is not confined to the targeted organization alone. The impact could extend to clients/customers, partners, and stakeholders who may suffer from data compromise or financial loss, eroding trust and confidence in the organization. The reputational damage can have long-term consequences, including loss of market share and increased costs associated with legal fees and regulatory fines.
Chinese Nation-State Threat Actor, Flax Typhoon, Exploits Known Vulnerabilities, Uses Web Shells, and Deploys LOLBins
A recent blog post by Microsoft provides an in-depth analysis of the Chinese nation-state threat actor Flax Typhoon’s recent operation. The blog’s primary focus is to shed light on their unique tactics, techniques, and procedures (TTPs) targeting Taiwanese organizations. Their minimal use of malware highlights the group’s operations. Instead, they primarily rely on built-in operating system tools and benign software. Microsoft aims to raise awareness about the threat actor’s techniques and to inform better defenses against future operations, emphasizing the need for broader community awareness due to the potential for further impact on its customers.
Flax Typhoon has been active since mid-2021, and prior operations have focused on Taiwanese organizations across various sectors, including public administration, education, manufacturing, and information. However, the group has also been observed targeting entities in North America, Southeast Asia, and Africa. Flax Typhoon is adept at maintaining persistence, moving laterally, and accessing credentials within compromised networks. The group has used various tools, including China Chopper web shell, Metasploit, Juicy Potato privilege escalation tool, Mimikatz, and SoftEther VPN client. However, its operations primarily rely on living-off-the-land techniques and hands-on-keyboard activity.
Flax Typhoon employs a multi-faceted approach to gain initial access to target networks. The group exploits known vulnerabilities in public-facing servers, including VPN, web, Java, and SQL applications. The payload for these exploits is typically a web shell, such as China Chopper, allowing remote code execution on the compromised server. This initial access serves as the foothold from which the group conducts its subsequent activity.
When the process, compromised by the web shell, does not have local administrator privileges, Flax Typhoon downloads and runs malware, such as Juicy Potato, BadPotato, and other open-source tools, that exploits one or more known vulnerabilities to obtain local system privileges.
To maintain persistence on compromised systems, Flax Typhoon employs various procedures, including Windows Management Instrumentation Command-Line (WMIC), PowerShell, or the Windows Terminal with local administrator privileges. One such procedure involves manipulating the Remote Desktop Protocol (RDP) settings. Specifically, the group disables Network-Level Authentication (NLA) for RDP. They also replace the Sticky Keys binary to establish a VPN connection, allowing them to interact with the Windows sign-in screen without authenticating, thereby maintaining a persistent presence.
For command and control (C2), Flax Typhoon deploys SoftEther VPN, downloaded from their network infrastructure. They use Living-off-the-Land Binaries (LOLBins) and various procedures, such as PowerShell’s Invoke-WebRequest utility, certutil, or bitsadmin, to download the VPN executable. Once downloaded, the group creates a Windows service using the Service Control Manager (SCM) that launches the VPN connection automatically upon system start, enabling the group to monitor the availability of the compromised system and establish an RDP connection when needed.
To laterally move within the environment, Flax Typhoon employs LOLBins, including Windows Remote Management (WinRM) and WMIC. The group routes network traffic to other targeted systems through the SoftEther VPN bridge installed on compromised systems. This traffic includes network scanning, vulnerability scanning, and exploitation attempts, further expanding their reach within the target network.
Once established on the target system, Flax Typhoon conducts credential access activities using common tools and techniques. They frequently target the Local Security Authority Subsystem Service (LSASS) process memory and the Security Account Manager (SAM) registry hive using tools like Mimikatz to dump these stores when improperly secured automatically. Both of these stores contain hashed passwords for users signed into the local system. The resulting password hashes can be cracked offline or used in tactics like pass-the-hash (PtH) to access other resources on the compromised network.
However, Microsoft has observed minimal activity after Flax Typhoon established persistence. While their observed behavior suggests intentions to perform espionage, their discovery and credential access activities do not appear to enable further data collection and exfiltration, as no actions on final objectives have been observed in their operations. Flax Typhoon may pass access to another threat actor for data collection and exfiltration after targets have been vetted against intelligence collection requirements.
Risk & Impact Assessment
Flax Typhoon poses an urgent, multi-dimensional risk to customers, especially considering they have previously targeted organizations in North America. They exploit known vulnerabilities in public-facing servers and use living-off-the-land techniques that evade traditional security measures. Their use of web shells and privilege escalation tools, coupled with tactics for persistence and disguised command and control activities, complicates detection and poses technical and operational risks. The group’s focus on long-term access threatens the confidentiality of sensitive data, as they can move laterally within networks and risk unauthorized data access, modification, and destruction.
A successful intrusion by Flax Typhoon could pose a severe, long-term impact, given the group’s focus on maintaining persistent access for espionage activities. Their ability to operate covertly within a network allows them to access sensitive intellectual property, financial data, or strategic information over extended periods, which has a cascading impact on an organization’s competitive advantage and market reputation. Additionally, using legitimate software and operating system tools for malicious purposes complicates detection efforts and may force organizations into costly and disruptive countermeasures, such as isolating or decommissioning affected systems. These actions could result in operational disruptions, financial burdens associated with incident response, and potential legal ramifications. Furthermore, Flax Typhoon’s adeptness at disguising its activities makes it challenging to differentiate between malicious and legitimate network traffic, extending the window of opportunity for the group to operate undetected, thereby exacerbating the potential for significant operational and financial damage.
Latest Developments in UNC4841’s Exploitation of Barracuda’s ESG Vulnerability
The latest blog post by Mandiant, titled “Diving Deep into UNC4841 Operations Following Barracuda ESG Zero-Day Remediation (CVE-2023-2868),” provides an in-depth analysis of the cyber-espionage activities carried out by the threat actor UNC4841. The post details Mandiant’s analysis of the tactics, techniques, and procedures (TTPs) employed by UNC4841 in exploiting a zero-day vulnerability in Barracuda’s Email Security Gateway (ESG) software, now identified as CVE-2023-2868. The analysis provides actionable intelligence to understand the threat landscape and bolster defensive measures. The report is particularly relevant in the wake of the remediation efforts for the vulnerability and offers a granular look at how UNC4841 adapted its operations post-remediation.
UNC4841 is a sophisticated cyber-espionage group, a Chinese state-sponsored group with a history of targeting organizations across various sectors. The group has been particularly adept at exploiting zero-day vulnerabilities to gain unauthorized access to systems. CVE-2023-2868 is a critical zero-day vulnerability in Barracuda’s Email Security Gateway software, allowing remote code execution. The exploitation of this vulnerability by UNC4841 was part of a campaign executed between October 2022 and June 2023 aimed at data exfiltration and establishing a persistent foothold in targeted networks. The campaign is noteworthy for its complexity and the advanced TTPs employed, including custom malware and evasion techniques. The remediation of CVE-2023-2868 by Barracuda led to a shift in UNC4841’s operational tactics.
The UNC4841 campaign targeting a Barracuda ESG zero-day vulnerability (CVE-2023-2868) began in October 2022, with an initial surge of activity occurring in early November 2022. Post Barracuda’s remediation efforts, the group quickly adapted where they retooled their malware and changed persistence methods. This rapid adaptation suggests a high level of situational awareness and the ability to pivot rapidly in response to evolving defensive measures. The campaign culminated in early June with the highest intensity of activity observed, where the group attempted to maintain access to compromised environments, deploying the new malware families SKIPJACK, DEPTHCHARGE, and FOXTROT/FOXGLOVE.
SKIPJACK is a passive backdoor malware designed to compromise Barracuda ESG modules by injecting malicious Lua code. The malware activates its backdoor functionalities by scanning for specific email headers and subjects, decoding and executing their content. It employs AES-256 encryption and Base64 decoding techniques to execute commands piped to a system shell. Mandiant observed UNC4841 using bash scripts to inject this backdoor into Barracuda ESG modules, particularly targeting government and technology organizations. SKIPJACK was the most widely deployed and variant-rich malware in UNC4841’s arsenal for this campaign, found on approximately 5.8% of all compromised ESG appliances. The malware’s adaptability is evidenced by the multiple unrecovered variants, each suspected to use different sections of an email message to conceal its encrypted commands.
DEPTHCHARGE is a sophisticated passive backdoor malware deployed by UNC4841, designed to persist on Barracuda ESG appliances even after remediation efforts. Packaged as a Linux shared object library, it is pre-loaded into the Barracuda SMTP daemon and listens for encrypted commands from a command and control server. The malware is installed through a complex execution chain involving MySQL triggers, enabling it to infect clean appliances when victims restore backup configurations from compromised devices. Deployed roughly a week after Barracuda’s initial notification about the vulnerability, DEPTHCHARGE was found on about 2.64% of compromised appliances, targeting U.S. and foreign government entities and tech companies. Its intricate deployment and persistence mechanisms indicate UNC4841’s extensive knowledge of the Barracuda ESG system and suggest a well-funded, non-opportunistic campaign to maintain access to high-value targets.
FOXTROT and FOXGLOVE are malware families selectively deployed by UNC4841, primarily targeting government or government-related organizations considered high-priority by the People’s Republic of China (PRC). FOXGLOVE is a configurable launcher for FOXTROT, employing various encryption techniques for argument passing. FOXTROT is a versatile backdoor capable of multiple functions, including keystroke capture and file transfer, and it shares code overlaps with the open-source REPTILE shell. Unlike other malware used by UNC4841, these two are not explicitly designed for Barracuda ESGs. They are likely intended for broader deployment on Linux-based devices for lateral movement and credential theft.
In the wake of Barracuda’s public disclosure of CVE-2023-2868, Mandiant observed UNC4841 engaging in internal reconnaissance and lateral movement within select victim environments. The threat actor utilized open-source tools like fscan for various reconnaissance activities and harvested credentials from temporary storage locations on compromised ESG appliances. These credentials were then used to gain unauthorized access via Outlook Web Access (OWA), primarily for intelligence gathering rather than immediate exploitation. UNC4841 also demonstrated the ability to move laterally through various means, including SSH to VPNs and Proxy Servers, and by creating backdoor accounts on compromised appliances. Notably, the group accessed a Windows Server Update Services (WSUS) server using a domain administrator account, a tactic previously seen in China-nexus espionage activities aimed at deploying malware through fake updates. This multifaceted approach to lateral movement underscores UNC4841’s advanced capabilities and persistent threat to victim organizations.
Mandiant assesses with high confidence that UNC4841 conducts intelligence collection operations in support of the People’s Republic of China, a conclusion corroborated by independent government assessments. The group’s activities overlap with other China-nexus actors, such as UNC2286, sharing infrastructure and tooling, likely due to common anonymization services or infrastructure providers. UNC3886’s recent campaigns also exhibit similarities in malware characteristics and tactics, pointing to broader trends in Chinese cyber intelligence collection operations. These trends indicate a move towards more targeted, stealthy, and effective operations that exploit zero-day vulnerabilities and deploy custom malware, complicating attribution and detection efforts.
Mandiant’s analysis reveals that UNC4841 has targeted a wide range of sectors globally, focusing on national and local governments and high-tech and information technology (IT) entities. Nearly a third of the affected organizations were government agencies, and the campaign displays elements of espionage motivations. Post-remediation malware deployments were notably skewed toward government and tech sectors, suggesting a prioritization of conventional espionage targets. Local government entities in North America were also targeted, particularly in the initial months of the campaign. IT and managed service providers experienced significant early-stage targeting, possibly to establish initial footholds within Barracuda ESG environments. UNC4841 also targeted sectors critical to global technological and economic competitiveness and religious-based organizations impacting China. The earliest compromises were traced back to mainland China, with evolving tactics observed in the use of communication ports.
The overarching intention of UNC4841 appears focused on intelligence operations, highly likely aimed at gathering sensitive information for geopolitical leverage. UNC4841’s objectives align with their intentions, actively seeking unauthorized access to email data. UNC4841 possesses a high level of technical expertise, as evidenced by their rapid adaptation to the remediated Barracuda ESG vulnerability and sophisticated toolset. They have demonstrated the ability to operate stealthily, maintain persistence, and move laterally within compromised environments. Their operational security is robust, suggesting a well-resourced and highly skilled team. The group’s capabilities are further amplified by what appears to be state sponsorship, providing them with additional resources and intelligence support.
Risk & Impact Assessment
The UNC4841 threat actor group poses a significant risk to various organizations, particularly those in the government, technology, and information technology sectors. The group’s rapid adaptation to defensive measures indicates a high level of situational awareness and agility. This adaptability enhances the likelihood of successful compromise and persistence in targeted environments. The group’s use of sophisticated malware families, each with unique capabilities and evasion techniques, further elevates the risk. These tools enable UNC4841 to achieve unauthorized access, maintain persistence, and perform lateral movement within compromised networks. The group’s state sponsorship heightens the risk, which likely provides them with additional resources and support.
The impact of UNC4841’s activities on organizational operations and assets is substantial and multifaceted. Their ability to maintain persistence post-remediation actions could lead to prolonged operational disruption and data exposure. The group’s lateral movement capabilities introduce additional vectors for data compromise and operational disruption, extending the impact beyond the initially compromised systems. The group’s focus on intelligence collection directly threatens the confidentiality of sensitive information, resulting in the disclosure of sensitive data, with cascading impacts on organizational reputation and stakeholder trust. Furthermore, UNC4841’s activities provide evidence of a broader trend of increasingly sophisticated, stealthy, and effective Chinese cyber intelligence collection operations. This evolving threat landscape complicates attribution and detection efforts, requiring organizations to adapt their defensive postures continually.
Mallox Ransomware Tactics, Techniques, and Procedures
A new blog post titled “Exploring Mallox Ransomware: Tactics, Techniques, and Defense” by Seqrite serves as an in-depth analysis of Mallox Ransomware, a cyber threat that has been active since mid-2021. The post aims to elucidate the ransomware’s tactics, techniques, and procedures (TTPs), offering a comprehensive understanding of its operation. The blog also provides defensive measures to mitigate the risks associated with this particular ransomware. The content is structured to guide the reader through the ransomware’s attack vectors, infection chain, and technical aspects of its payload, ultimately aiming to equip cybersecurity professionals and organizations with actionable insights.
Mallox ransomware is a strain of ransomware that primarily targets Microsoft Windows systems. It has been active since June 2021 and has gained attention for exploiting unsecured MS-SQL servers as a penetration vector to compromise victims’ networks. The ransomware follows the double extortion trend, where it steals data from the victim’s environment before encrypting it, then threatens to publish the stolen data on a leak site if the ransom demands are not met. Mallox is also known for its attempts to disable services, delete shadow copies, clear event logs, and change file permissions to impede data restoration and forensic analysis. The group behind Mallox claims to have breached hundreds of organizations worldwide, with victims spanning various industries such as manufacturing, professional and legal services, and wholesale and retail. The ransomware has seen a significant increase in activity, with a 174% surge in 2023 compared to the previous year.
Mallox Ransomware primarily targets unsecured Microsoft SQL Servers to gain initial access. The threat actors use brute force on publicly exposed MSSQL servers to gain initial access to the victims’ networks. Once initial access is achieved, the ransomware uses the MSSQL service’s sqlservr.exe command line to implant malicious files and payloads onto the victim’s machine.
Mallox Ransomware initiates its infection chain upon gaining access by executing a batch file. This batch file injects code into the Aspnet_Complier.exe process and subsequently drops and executes another batch file. The latter is designed to delete unwanted services and terminate tasks to ensure the encryption process’s success.
The ransomware employs a .NET payload responsible for injecting the ransom code. This payload downloads another encrypted VDF from a remote server, decrypted directly into the system’s memory. The decrypted DLL file is further obfuscated using an IntelliLock obfuscator and is loaded into another process using the process hollowing technique.
The injected ransom code performs multiple functions, including checking the default language ID to exclude certain countries from targeted attacks. It also deletes registry keys and shadow copies, modifies boot configurations, and terminates specific processes. The code also disables system options to prevent users from shutting down or restarting their systems.
Mallox Ransomware can exfiltrate data from targeted systems before encryption. The ransomware collects and transfers system information to its Command and Control (C2) server.
The ransomware creates encryption threads based on the number of existing processors, with a maximum limit of 64 threads. It employs the sala20 encryption algorithm and appends a .Mallox extension to encrypted files.
The intention behind Mallox Ransomware’s threat actors is financial gain through extortion. By encrypting sensitive data, threatening public disclosure, and demanding a ransom, the actors aim to monetize their activities.
The primary objective of the threat actors is targeting unsecured Microsoft SQL Servers, which often contain sensitive and valuable data. Once inside the network, the ransomware aims to encrypt as many files as possible, including those on local and network-shared drives. The ransomware also seeks to exfiltrate data, indicating an objective to compromise sensitive information for further exploitation.
The threat actors demonstrate advanced capabilities, including using sophisticated payloads and a complex intrusion chain. Their use of obfuscation techniques, process hollowing, and data exfiltration mechanisms indicate a high level of technical expertise. The ability to disable system functions further underscores the advanced capabilities of these actors.
Risk & Impact Assessment
The risk landscape shaped by Mallox Ransomware is both immediate and severe, with a particular vulnerability for organizations operating unsecured Microsoft SQL Servers. The ransomware employs a sophisticated modus operandi, including brute force attacks, advanced payloads, and intricate infection chains. This multi-pronged approach significantly increases the likelihood of successful system infiltration if adequate preventive measures are not implemented. The primary risks involve the loss of availability due to file encryption and system function disablement, the loss of confidentiality due to the disclosure of sensitive data, and the loss of integrity via system configuration modifications. Additionally, the unauthorized access gained through brute force attacks further compromises the internal security posture of an organization, leading to a cascade of potential vulnerabilities and financial liabilities.
The impact of a successful Mallox Ransomware attack can be devastating on multiple fronts. Operationally, the encryption of critical files and systems can bring business operations to a standstill, affecting the organization’s mission and functional capabilities. This operational disruption can lead to service delays, potential contractual penalties, and a significant erosion of customer trust. Financially, the costs can be twofold: the immediate financial burden of the ransom and the additional, often hidden, costs related to system restoration, legal consultations, and potential regulatory fines. The reputational damage ensuing from a public disclosure of a ransomware attack can have long-term consequences, including the loss of customers and competitive standing.
TA551’s Initial Access Leads to Nokoyawa Ransomware
A blog post by The DFIR Report titled “HTML Smuggling Leads to Domain Wide Ransomware” comprehensively analyzes a Nokoyawa Ransomware incident from November 2022. The report attributes the activity to two threat actors, one of which is TA551, delving into the technical intricacies of how HTML Smuggling was leveraged for initial access and the delivery of Nokoyawa Ransomware across an entire domain. The scope of the analysis extends from the initial infection vector to the final encryption stage, offering a detailed walkthrough of the intrusion chain. The context is particularly pertinent given the increasing prevalence of ransomware attacks and adversaries’ evolving tactics, techniques, and procedures (TTPs). The report aims to equip cybersecurity professionals with the relevant information to increase readers’ understanding and mitigate such threats.
Nokoyawa Ransomware was first discovered in 2021 and is considered a variant of the well-known Phobos Ransomware. Nokoyawa Ransomware is typically distributed through various methods, including phishing emails, malicious downloads, exploit kits, or by exploiting vulnerabilities in software or operating systems. TA551 is an email-based malware distribution campaign primarily targeting English-speaking victims. It has been active since at least February 2019. Since mid-July 2020, TA551 has exclusively pushed IcedID malware. TA551 uses malspam to distribute malware and spoofs legitimate email chains based on data retrieved from previously infected Windows hosts. HTML smuggling is a technique used by cybercriminals to deliver malicious payloads using benign-looking files, usually HTML or JavaScript. When the recipient downloads and opens the file, it utilizes HTML5 or JavaScript functionalities to generate and run a malicious payload on the client side, bypassing traditional security mechanisms, as the malicious payload is constructed post-download.
The Nokoyawa Ransomware incident began with a thread-hijacked phishing email campaign in early November 2022. The email had an HTML file attached that employed HTML smuggling. The HTML file, when opened, presented a fake Adobe page and initiated the download of a ZIP file. This ZIP file contained an ISO file containing an IcedID payload. The only visible file to the user was an LNK file disguised as a document. These techniques overlap with those used by TA551, an initial access broker.
Upon clicking the LNK file, a series of commands were executed, including copying rundll32 and a malicious DLL (IcedID) from the ISO to the host system. IcedID then established a connection with the command and control servers. Simultaneously, the user was shown a legitimate-looking finance document, likely as a diversionary tactic. Persistence was established via a scheduled task set to run the IcedID malware every hour.
Approximately three hours post-initial execution, a cmd process was spawned from IcedID, which began beaconing to a Cobalt Strike server. At this juncture, the initial access broker likely transferred control to a Nokoyawa Ransomware affiliate, accessing LSASS to harvest credentials. After a brief pause, the affiliate resumed activity, identifying specific domain administrators and initiating an RDP session to move laterally to a domain controller. Further discovery actions were conducted, including Active Directory scans and network lookups.
The affiliate then executed an encoded PowerShell script (SessionGopher) to find and decrypt saved session information for remote access tools. They logged into additional hosts, including a backup and file share servers. The affiliate then utilized netscan to scan the network and PsExec and WMIC to move files across the network. The ransomware was then deployed across the domain, with a Time to Ransomware (TTR) of just over 12 hours from the initial infection.
The intentions of the threat actors behind the Nokoyawa Ransomware incident are financial. Initially, the affiliate performed extensive discovery actions, credential harvesting, and then ransomware deployment. The threat actors targeted various systems, from individual hosts to domain controllers, to gain unauthorized access, exfiltrate sensitive data (credentials), and deploy ransomware. The specific targeting of a backup server suggests an intent to interfere with recovery efforts, thereby increasing the likelihood of a ransom payment.
TA551 demonstrated advanced capabilities, including using HTML smuggling and tools like IcedID and Cobalt Strike. The affiliate’s ability to pause and resume activity may suggest a high level of operational security or other commitments that interfere with their malicious actions. Additionally, their use of multiple tools and techniques indicates technical proficiency.
Risk & Impact Assessment
The likelihood of an incident occurring is high, given the advanced capabilities demonstrated by the threat actors. Risks to the organization include the loss of confidentiality, integrity, and availability of data or information systems. The threat actors can gain unauthorized access, disclose sensitive information, modify data, and disrupt operations.
The impact of such an incident on organizational operations, including mission-critical functions and financial stability, is significant. Threat actors have demonstrated the capability to obtain unauthorized access, disclose sensitive information, modify data, disrupt operations, and even destroy data or information systems. This could result in substantial financial loss and reputational damage.
Latest Additions to Data Leak Sites
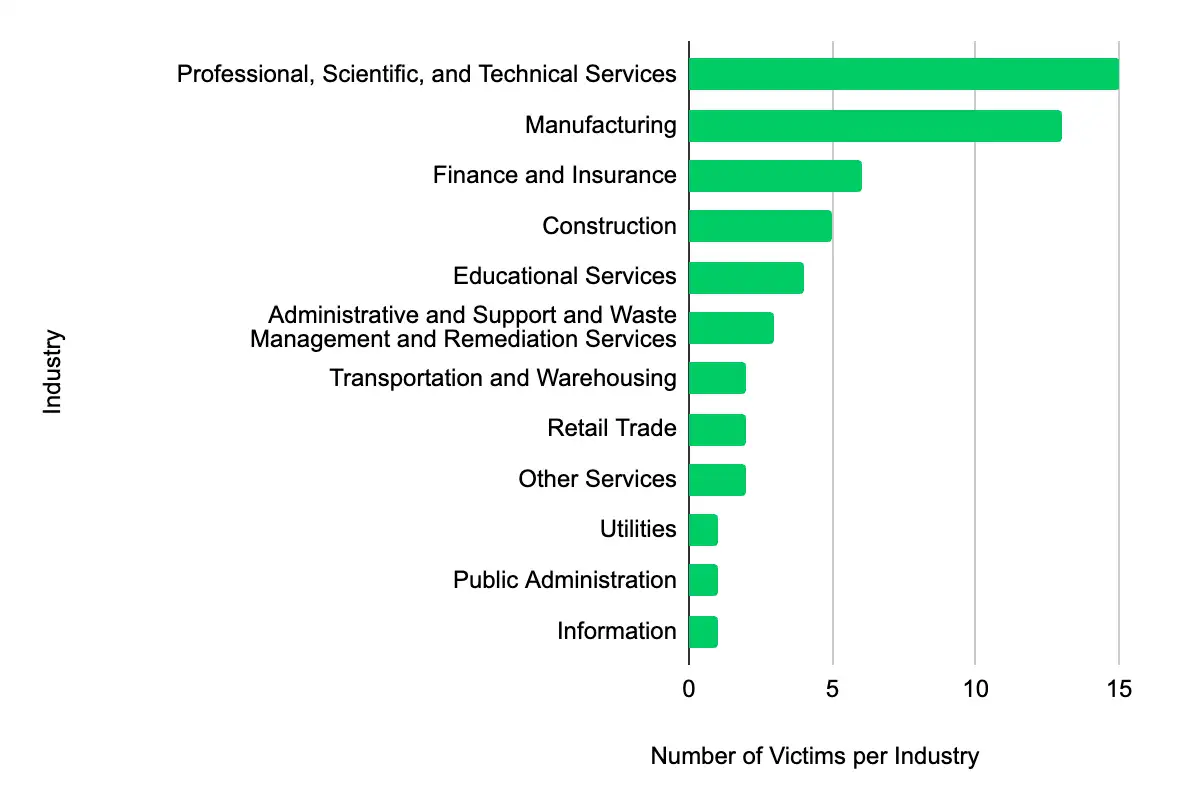
In the past week, monitored data extortion and ransomware threat groups added 55 victims to their leak sites. Of those listed, 18 are based in the US. The most popular industry listed was Professional, Scientific, and Technical Services, with 11 victims. They were followed by 13 in Manufacturing, six in Finance and Insurance, five in Construction, and four in Educational Services. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds 2 CVEs to its Known Exploited Vulnerabilities Catalog
Within the past week, CISA added two CVEs to the catalog, affecting RARLAB’s WinRAR and Ignite Realtime Openfire. The WinRAR vulnerability allows for remote code execution, and the Openfire vulnerability allows threat actors to access restricted pages in the Openfire Admin Console. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA setting a mitigation due date of 14 September 2023.
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-38831 | RARLAB | WinRAR | RARLAB WinRAR contains an unspecified vulnerability that allows an attacker to execute code when a user attempts to view a benign file within a ZIP archive. | 9/14/2023 |
| CVE-2023-32315 | Ignite Realtime | Openfire | Ignite Realtime Openfire contains a path traversal vulnerability that allows an unauthenticated attacker to access restricted pages in the Openfire Admin Console reserved for administrative users. | 9/14/2023 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share