Iranian Hackers Join Forces with Ransomware Groups, BlackByte’s Tactics Unveiled, RansomHub Compromises 200+ Organizations, New CVE-2023-22527 Exploits Deliver Godzilla Webshell, and CISA Updates
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Iranian Hackers Team Up with Ransomware Groups to Target US Organizations
- Inside BlackByte’s Signature Tactics
- Exposing RansomHub, the Group Behind 200+ Compromised Organizations
- New CVE-2023-22527 Exploit Method Delivers Godzilla Webshell
- 136 Firms Listed on Data Leak Sites in a Week: Professional Services Top the List
- CISA Adds VigorConnect and WPS Office Vulnerabilities to Exploited List
Iranian Hackers Team Up with Ransomware Groups to Target US Organizations
The Rundown
Iranian state-sponsored attackers are intensifying their efforts to gain and maintain access to US organizations, collaborating with ransomware groups to lock critical data and infrastructure and extort victims for financial gain.
This escalating threat directly endangers various industries in the US by facilitating the disruption of their operations and jeopardizing sensitive data. The attackers’ deepening ties with ransomware affiliates amplify the potential damage, making it crucial for organizations to fortify their defenses against these coordinated attacks.
Source Material: CISA
Inside BlackByte’s Signature Tactics
The Rundown
The BlackByte ransomware group is evolving into a more dangerous and persistent threat, using signature methods and exploiting newly disclosed vulnerabilities to infiltrate and cripple systems.
As BlackByte adopts innovative techniques and targets critical infrastructure, it poses a significant challenge for organizations to defend against. This evolution in ransomware tactics underscores the urgent need for adaptive security measures to protect sensitive data and operational continuity.
Source Material: Cisco Talos
Exposing RansomHub, the Group Behind 200+ Compromised Organizations
The Rundown
The FBI, CISA, and HHS warn that RansomHub, a fast-rising ransomware group, has compromised over 200 organizations across critical sectors since its inception in February 2024.
RansomHub’s rapid rise and high-profile affiliates with ties to notorious ransomware variants like LockBit and ALPHV signal an escalating threat to vital infrastructure, putting sensitive data, operational processes, and public safety at severe risk.
Source Material: CISA
New CVE-2023-22527 Exploit Method Delivers Godzilla Webshell
The Rundown
Attackers are using a new method to exploit CVE-2023-22527. This method allows attackers to inject a loader, which then injects the Godzilla web shell into Atlassian Confluence servers, creating a backdoor that enables persistent and encrypted communication with a command-and-control (C2) server.
This sophisticated attack chain not only compromises server security by allowing unauthorized remote access but also indicates a high level of persistence. It suggests that attackers are setting the stage for long-term control and further exploitation, potentially constructing a botnet for future malicious activities.
Source Material: Trend Micro
136 Firms Listed on Data Leak Sites in a Week: Professional Services Top the List
The Rundown
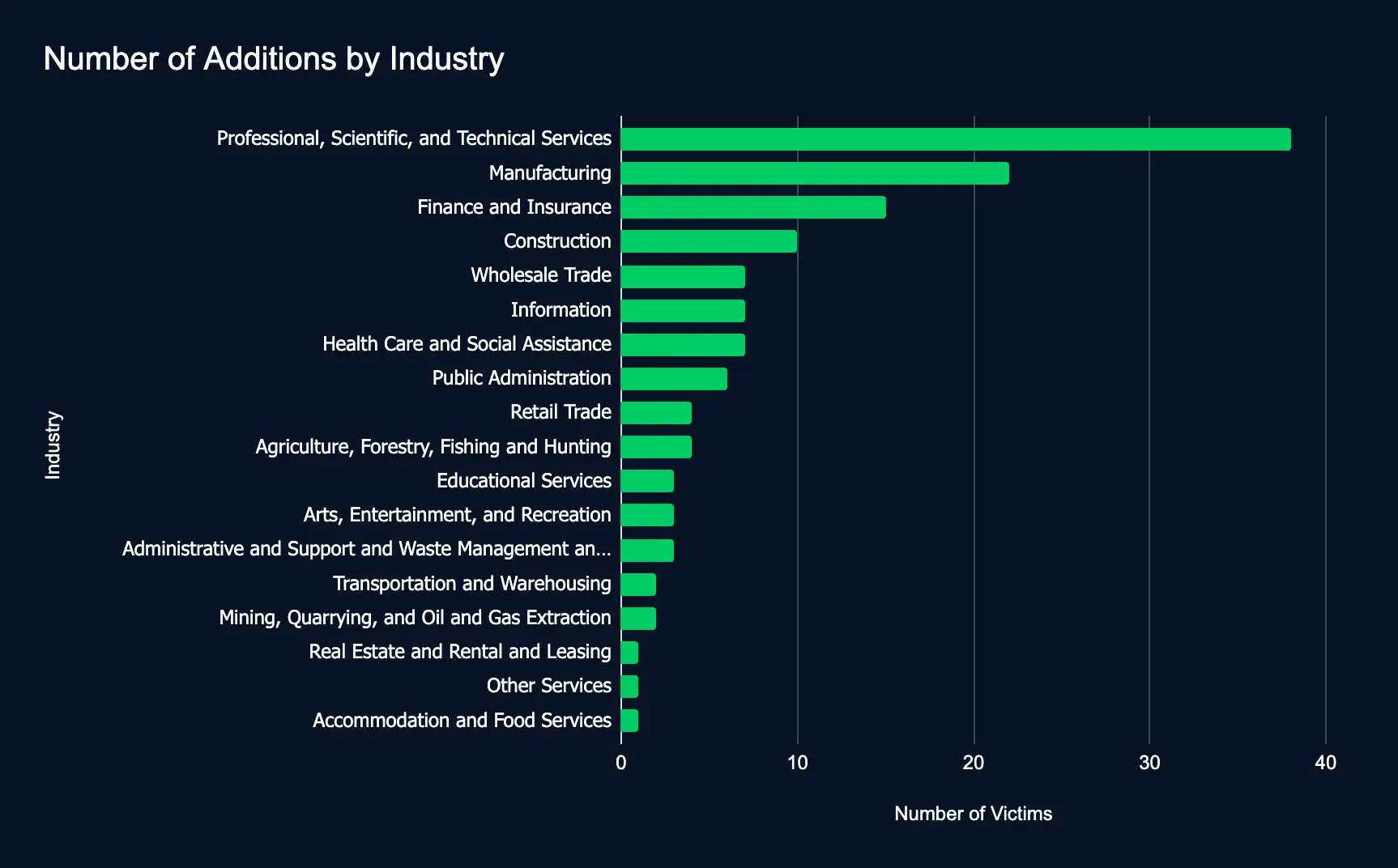
Ransomware and data extortion sites listed 136 organizations across 18 industries and 38 countries between August 26 and August 31, 2024, spotlighting the scale of these attacks and their intensifying threat to critical sectors.
The surge in ransomware attacks, doubling last week’s 65 additions, demonstrates a growing vulnerability across key sectors, such as professional services, healthcare, and manufacturing, potentially disrupting operations and endangering sensitive data globally.
CISA Adds VigorConnect and WPS Office Vulnerabilities to Exploited List
The Rundown
Three critical vulnerabilities, two affecting Draytek VigorConnect and one affecting Kingsoft WPS Office, were added to CISA’s Known Exploited Vulnerabilities catalog this week. If left unpatched, these vulnerabilities pose serious threats to businesses and individuals.
These vulnerabilities could allow attackers to access sensitive files or execute arbitrary code, potentially leading to ransomware attacks or data theft. Immediate action is required, as attackers may exploit these flaws to compromise a targeted organization.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share