0.0.0.0 Day Browser Vulnerability Exposes Networks, CISA & FBI Update on Royal Ransomware, Cloud-Based Threats Rise, Qilin Ransomware’s Global Impact, Earth Baku Expands Espionage, and Lockbit Leads Ransomware Surge
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- 0.0.0.0 Day: A New Browser Vulnerability Exposes Local Networks
- CISA and FBI Update Advisory on Rebranded Royal Ransomware
- GoGra, Grager, and MoonTag: The Rise of Cloud-Based Cyber Threats
- Exposé: Qilin Ransomware’s Advanced Tactics and Global Impact
- Earth Baku Expands Cyber Espionage Operations to Europe and the Middle East
- New Ransomware Group Sends AnyDesk Connection Request to Gain Access and Steal Data
- Ransomware Surge: Lockbit Leads Wave of Attacks Amid Fluctuating Leak Site Additions
- CISA Adds Microsoft, Android, and Apache Vulnerabilities to Exploited List
0.0.0.0 Day: A New Browser Vulnerability Exposes Local Networks
Vulnerability – All Major Browsers – Access to Local Network – Access to Non-Internet Exposed Services – All Industries
The Rundown
In a recent Oligo blog post, they detail their discovery of a new vulnerability, dubbed “0.0.0.0 Day,” exposing local network services to attacks from malicious websites via all major web browsers. This vulnerability exploits the IP address 0.0.0.0 to bypass security mechanisms, leading to unauthorized access and potential remote code execution.
This issue arises from inconsistent security implementations and a lack of browser standardization. All major browsers are affected, with varied levels of response to the vulnerability. An attacker exploiting this vulnerability can access the internal private network of the victim, opening a wide range of attack vectors, highlighting the need for unified security measures to protect local networks from external threats.
Source Material: Oligo
CISA and FBI Update Advisory on Rebranded Royal Ransomware
Ransomware – Royal – BlackSuit – Tactics, Techniques, and Procedures (TTPs) – All Industries
The Rundown
On August 7, CISA and the FBI issued an updated Advisory warning about Royal Ransomware’s rebranding as BlackSuit. The Advisory updates the tactics, techniques, and procedures (TTPs), Indicators of Compromise (IOCs), and detection methods related to BlackSuit ransomware.
The rebranding and evolution of Royal Ransomware into BlackSuit signifies a growing and more sophisticated threat to critical infrastructure. With new tactics and enhanced capabilities, BlackSuit poses a significant risk, and understanding and mitigating these threats is crucial to safeguarding sensitive data and maintaining operational continuity in essential services.
Source Material: CISA
GoGra, Grager, and MoonTag: The Rise of Cloud-Based Cyber Threats
Malware – Cloud Services – Backdoor – GoGra – Grager – MoonTag – All Industries
The Rundown
A recent Symantec blog post details how malicious actors are increasingly abusing legitimate cloud services like Microsoft Graph API and Google Drive for command and control (C2) and data exfiltration.
Abusing trusted cloud services lets attackers blend malicious traffic with legitimate activity, making detection harder. This trend highlights the need for advanced security strategies and vigilance to protect sensitive data from evolving cyber threats and enhance cyber resiliency.
Source Material: Symantec
Exposé: Qilin Ransomware’s Advanced Tactics and Global Impact
Ransomware – Qilin – Tactics, Techniques, and Procedures (TTPs), Educational Services – Health Care and Social Assistance – Professional, Scientific, and Technical Services – Real Estate and Rental and Leasing – Manufacturing
The Rundown
A recent Group-IB blog post shows that Qilin ransomware has swiftly evolved into a formidable cybersecurity threat, leveraging advanced tactics and a flexible Ransomware-as-a-Service model to infiltrate and cripple over 150 organizations across the globe. The blog post details the group’s evolution, methods of attack, and substantial impact.
Qilin ransomware’s sophisticated methods and fast-paced evolution highlight a significant challenge for security teams. It continues to exploit vulnerabilities, evade detection, and expand its reach across various industries. The impact, including disrupted operations and substantial financial demands, highlights the severe impact this group can have on organizations across multiple industries.
Source Material: Group-IB
Earth Baku Expands Cyber Espionage Operations to Europe and the Middle East
Threat Actor – Chinese Threat Actor – Vulnerability Exploitation – IIS Servers – Malware – Earth Baku – Godzilla – WebShell – StealthVector – StealthReach – Cobalt Strike – SneakCross – Health Care and Social Assistance – Information – Educational Services – Public Administration
The Rundown
A recent Trend Micro blog post details how Earth Baku, a cyber espionage group linked to the Chinese-linked APT41, has expanded its reach into Europe, the Middle East, and Africa, targeting key sectors with advanced malware.
This escalation highlights Earth Baku’s global reach and underscores the severe risks posed by state-sponsored cyber threats to various industries worldwide, demanding urgent and enhanced cybersecurity measures.
Source Material: Trend Micro
New Ransomware Group Sends AnyDesk Connection Request to Gain Access and Steal Data
Ransomware – Remote Access Tool – Data Theft – Mad Liberator – AnyDesk – All Industries
The Rundown
A recent Sophos X-Ops report details a new ransomware group, Mad Liberator, that uses AnyDesk to gain access and exfiltrate data from organizations, marking a dangerous shift in cyberattack strategies.
Emerging in mid-2024, Mad Liberator has quickly distinguished itself from traditional ransomware groups by using sophisticated social engineering tactics to infiltrate systems. Unlike the typical ransomware that encrypts data and demands payment for its release, Mad Liberator employs a more insidious method—data theft under the guise of legitimate IT operations.
Source Material: Sophos
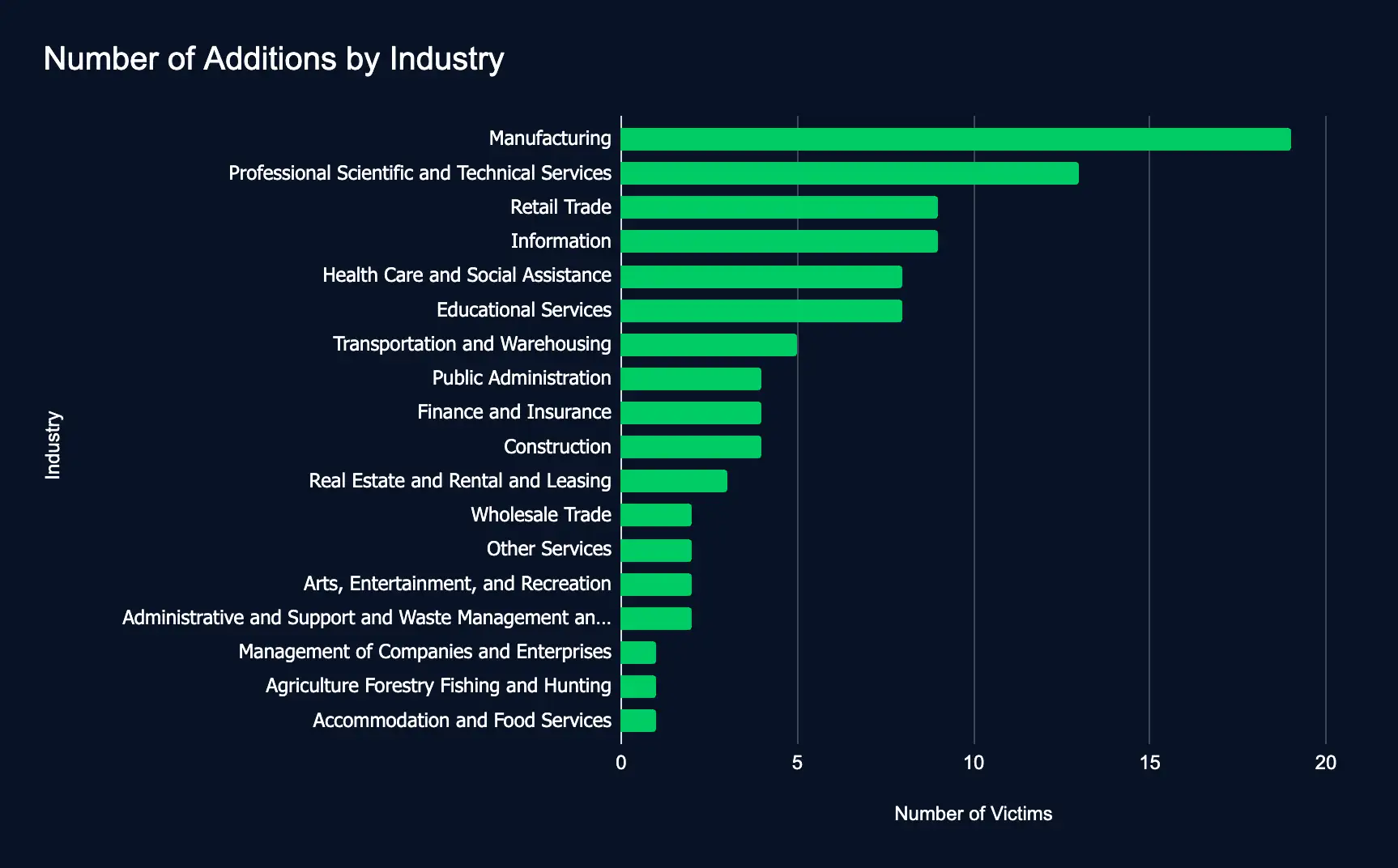
Ransomware Surge: Lockbit Leads Wave of Attacks Amid Fluctuating Leak Site Additions
Manufacturing – Professional Scientific and Technical Services – Retail Trade – Information – Health Care and Social Assistance – Educational Services
The Rundown
A surge in ransomware attacks last week saw nearly 100 organizations across various industries added to data leak sites. The notorious Lockbit group was responsible for nearly half of the breaches, signaling an alarming escalation in the global cyber threat landscape.
The latest wave of ransomware attacks, affecting 97 organizations between August 5 and August 11, 2024, underscores the scale of cyber threats. This development follows a period of fluctuating activity throughout the year, with certain weeks witnessing dramatic spikes in attacks. The trend highlights the volatility of the ransomware landscape and the urgent need for enhanced cybersecurity measures globally.
CISA Adds Microsoft, Android, and Apache Vulnerabilities to Exploited List
Microsoft Project CVE-2024-38189 – Microsoft Windows Scripting Engine CVE-2024-38178 – Microsoft Windows SmartScreen CVE-2024-38213 – Microsoft Windows Ancillary Function Driver for WinSock CVE-2024-38193 – Microsoft Windows Kernel CVE-2024-38106 – Microsoft Windows Power Dependency Coordinator CVE-2024-38107 – Android Kernel CVE-2024-36971 – Apache OFBiz CVE-2024-32113
The Rundown
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has expanded its Known Exploited Vulnerabilities (KEV) catalog by adding eight critical vulnerabilities actively exploited in the wild. This action underscores the urgent need for organizations to patch their systems immediately to prevent potential cyberattacks. These vulnerabilities, which affect widely used software from Microsoft, Android, and Apache, pose significant risks to organizations across various sectors.
These vulnerabilities are not just theoretical risks; they have been actively exploited, meaning that malicious actors have already used them in attacks to execute unauthorized actions on targeted systems. CISA’s decision to include these vulnerabilities in the KEV catalog signals that these flaws have proven exploitable in real-world conditions through successful or attempted exploitation. The inclusion of these vulnerabilities highlights the pressing need for organizations to take immediate action to secure their systems.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share