Malware via Teams and Ransomware on C2 Servers Dominate Threats as CISA Flags 8 Vulnerabilities, Including Apache Struts2
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Another Attack Leveraging Teams to Deliver Malware
- Apache ActiveMQ CVE-2023-46604 Exploitation: C2 Server Hosts Ransomware, Elevating the Threat
- Leak Sites: 81 Firms Listed, Professional Services Tops the List
- CISA Adds 8 Vulnerabilities to Exploited List, Plus an Apache Struts2 Vulnerability Expected to be Added in the Future
Another Attack Leveraging Teams to Deliver Malware
The Rundown
Trend Micro’s recent blog post, “Vishing via Microsoft Teams Facilitates DarkGate Malware Intrusion,” examines how attackers use voice phishing (vishing) on Microsoft Teams to distribute the DarkGate malware. This sophisticated malware poses a significant threat with its multi-functional capabilities, including data theft, backdoor access, and cryptojacking. The report highlights the increasing prevalence of social engineering attacks targeting corporate communication platforms.
The significance of this threat lies in its potential to exploit trust within organizational environments. In this incident, the attackers capitalized on human susceptibilities by impersonating IT personnel, making it easier to bypass security measures. For organizations, this method undermines internal trust, disrupts operations, and exposes sensitive data, underscoring the critical need for heightened vigilance and robust cybersecurity defenses. Notably, over the past month, Deepwatch has collected intelligence reporting on attackers leveraging Microsoft Teams during the initial access phase, indicating an increasing trend.
The attack was initiated through phishing and vishing tactics, followed by the execution of a malicious AutoIT script. The A3x script facilitates further stages, including system discovery via Windows Management Instrumentation (WMI) and the execution of defense evasion techniques like process hollowing to inject malware into legitimate processes, culminating in delivering the final payload, DarkGate. Post-installation activities include the creation of multiple files and a Registry Run key for persistence.
Among the key findings, the report highlights the attackers’ use of scripting frameworks like AutoHotKey and AutoIT to evade detection and execute malicious payloads. Its layered approach, combining social engineering, process injection, and persistent registry modifications, exemplifies the increasing sophistication of modern malware campaigns. These developments emphasize the importance of vigilance and multi-layered defenses in combating evolving threats.
Source Material: Trend Micro
Apache ActiveMQ CVE-2023-46604 Exploitation: C2 Server Hosts Ransomware, Elevating the Threat
The Rundown
ASEC’s recent blog post, “Mauri Ransomware Threat Actors Exploiting Apache ActiveMQ Vulnerability (CVE-2023-46604),” details how attackers are exploiting a remote code execution (RCE) vulnerability in Apache ActiveMQ servers to create a backdoor account and deploy malware, such as cryptominers and FRP (Fast Reverse Proxy). The vulnerability, identified as CVE-2023-46604, allows attackers to send malicious packets that exploit insecure class-loading mechanisms, enabling arbitrary code execution.
The significance of this threat lies in its potential for widespread exploitation, particularly in systems running unpatched versions of Apache ActiveMQ. Exploitation of the vulnerability allows attackers to gain an initial foothold with minimal effort, increasing the risk for organizations with exposed infrastructure. This exploitation demonstrates a broader trend of threat actors rapidly adopting known vulnerabilities in widely-used software, underscoring the critical importance of patch management and proactive defense strategies.
The attack chain begins with the exploitation of CVE-2023-46604, where malicious packets are sent to vulnerable ActiveMQ servers, which reference externally hosted configuration files, resulting in code execution. Exploitation could lead to account creation and the installation of malware and tools. In one observed attack, the command and control server hosts Quasar RAT and a Mauri ransomware binary, which could lead to operational disruption and extortion. However, deployment of this malware has not been confirmed.
The Deepwatch Threat Intelligence Team conducted a Shodan query, revealing almost 3,000 potentially vulnerable Apache ActiveMQ servers exposed to the internet, with the majority located in China (1,558) and the United States (270). It should be noted that CVE-2023-46604 was added to CISAs Known Exploited Vulnerabilities catalog on November 02, 2023, and had a recommended mitigation due date of November 23, 2023.
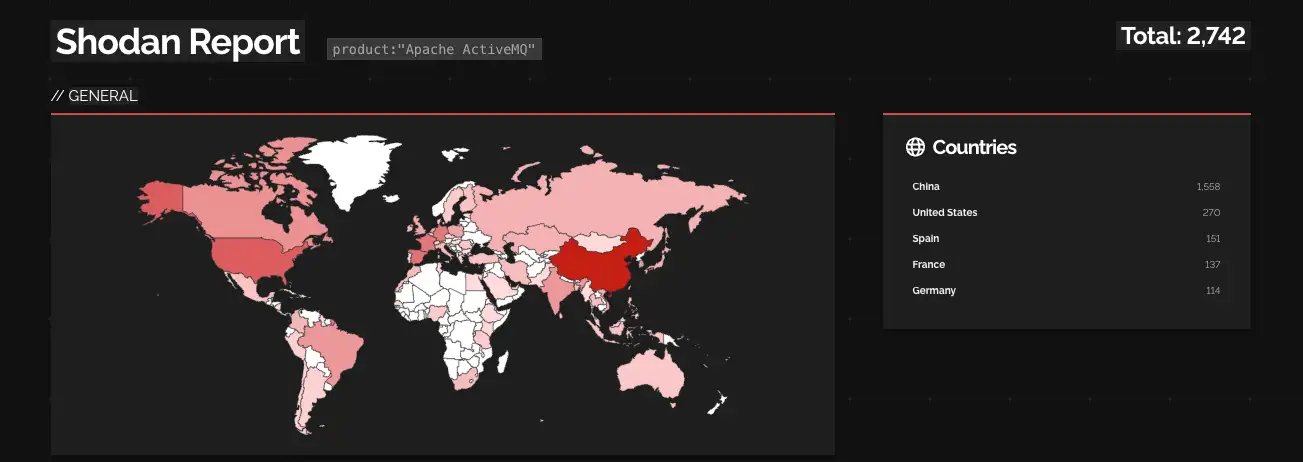
Source Material: AhnLab
Leak Sites: 81 Firms Listed, Professional Services Tops the List
The Rundown
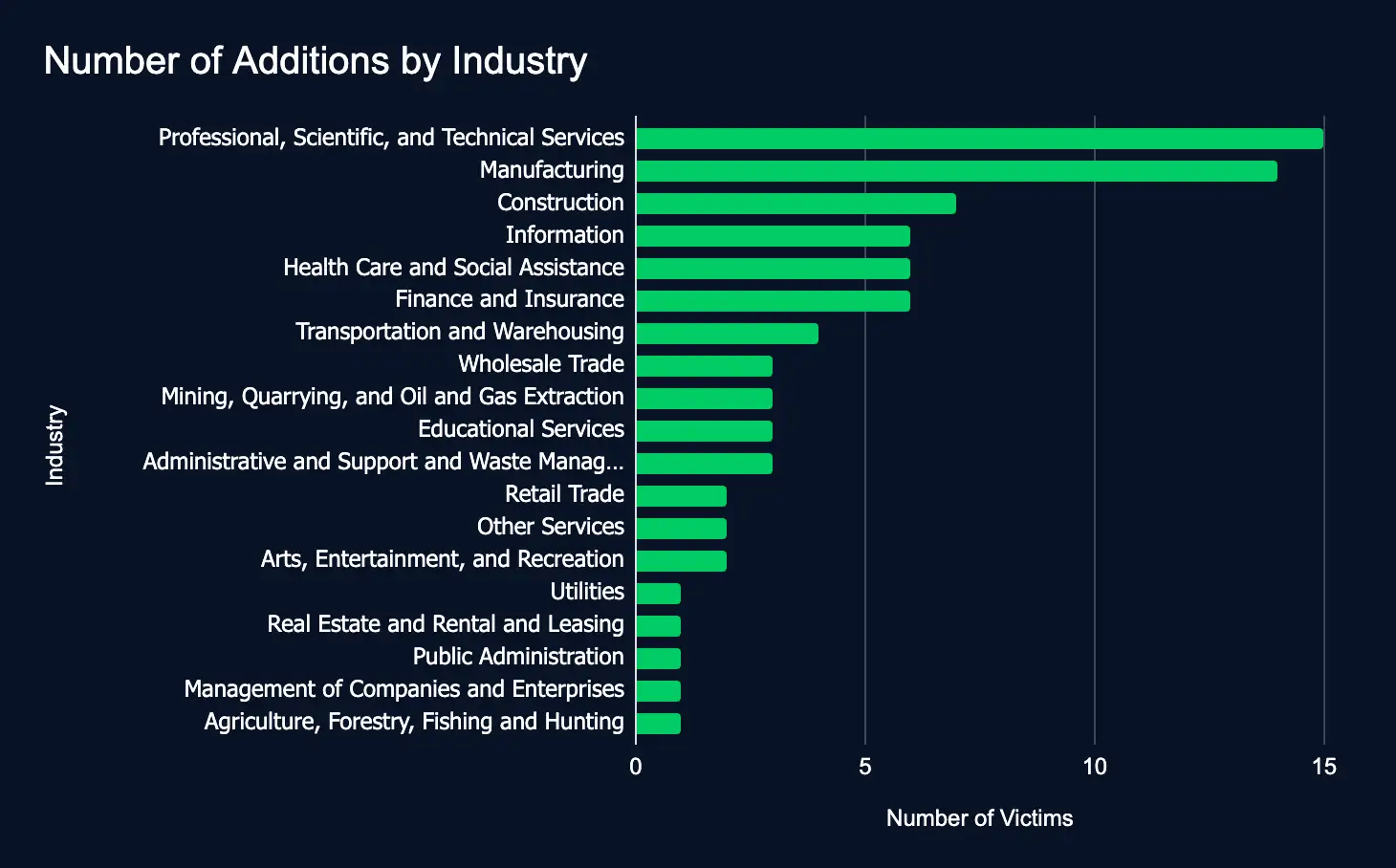
From December 9 to 15, 25 ransomware and data extortion leak sites added 81 from 19 different industries. The top sectors were Professional, Services, Manufacturing, and Construction. The United States, United Kingdom, and Canada were the top regions. The top leak sites were Clop, Ransomhub, and Play.
The decrease in new additions—107 fewer than the previous week—should not be considered a reprieve. Instead, it highlights the inherent week-to-week variability in attack frequency. All sectors, including manufacturing, professional services, and healthcare, remain at risk, emphasizing the need for robust cybersecurity measures to counter unpredictability, protect sensitive data, and bolster cyber resilience.
CISA Adds 8 Vulnerabilities to Exploited List, Plus an Apache Struts2 Vulnerability Expected to be Added in the Future
The Rundown
Between December 12 and 18, eight (8) vulnerabilities affecting Adobe (CVE-2024-20767), Cleo (CVE-2024-55956 & CVE-2024-50623), Microsoft (CVE-2024-35250), NUUO (CVE-2018-14933 & CVE-2022-23227), and Reolink (CVE-2019-11001 & CVE-2021-40407) products were added to CISA’s Known Exploited Vulnerabilities catalog.
While it has not been added to the catalog yet, exploitation attempts targeting Apache Struts2 vulnerability, either CVE-2024-53677 or CVE-2023-50164, have been observed by the SANS Internet Storm Center. Both of these vulnerabilities allow remote code execution via arbitrary file upload. The Deepwatch Threat Intel team expects this vulnerability will be added to the catalog in the near future.
These newly cataloged vulnerabilities highlight looming risks for organizations using these technologies. Failure to patch these flaws could lead to data theft, persistent access, and code execution. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share