Significant Changes to the PaaS Threat Landscape, Fortinet EMS Vulnerability Exploited, and CISA Exploited List Additions
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Shifting Sands: The Collapse of Rockstar2FA and the Bloom of FlowerStorm in the PaaS Threat Landscape
- Fortinet Endpoint Manager Server Vulnerability Exploited to Gain Unauthorized Access and Deploy RMM Tools
- 2024 Leak Site Recap: Over 4,000 Firms Listed, Manufacturing Tops the List
- CISA Adds Acclaim Systems and BeyondTrust Vulnerabilities to Exploited List
Shifting Sands: The Collapse of Rockstar2FA and the Bloom of FlowerStorm in the PaaS Threat Landscape
The Rundown
A recent Sophos report, “Phishing platform Rockstar 2FA trips, and ‘FlowerStorm’ picks up the pieces,” discusses the disruption of a significant phishing-as-a-service (PaaS) platform, Rockstar2FA, and the subsequent rise of a similar platform known as FlowerStorm.
In November 2024, Sophos observed a sudden cessation in detections related to Rockstar2FA. This service, evolving from DadSec, experienced a partial infrastructure failure, which appears to be due to technical issues rather than an external takedown, making its phishing pages inaccessible. This disruption occurred two weeks before TrustWave published research detailing the operation. Elements of Rockstar2FA’s infrastructure returned HTTP 522 responses, indicating connectivity issues with the Cloudflare content delivery network. Additionally, associated Telegram channels went offline.
Following Rockstar2FA’s disruption, activity increased from a PaaS platform known as “FlowerStorm.” This service shares similarities with Rockstar2FA and Tycoon, particularly regarding its use of Telegram bots to manage phishing campaigns. The name “FlowerStorm” derives from plant-related terms used in the HTML titles of its phishing pages, such as “Flower,” “Sprout,” “Blossom,” and “Leaf.”
Both Rockstar2FA and FlowerStorm operate by mimicking legitimate login behaviors of popular cloud and software-as-a-service platforms. Cybercriminals purchase access to these services through Telegram, receiving unique phishing pages and URLs for their campaigns. Victims clicking these links are directed to counterfeit login pages that capture credentials and multifactor authentication tokens. The stolen data is then transmitted to attacker-controlled backend servers, often hosted on the top-level domains .ru, .de, and .moscow.
The disruption of Rockstar2FA highlights the transient nature of cybercrime infrastructure. The swift emergence of FlowerStorm underscores the threat landscape and cybercriminals’ adaptability in establishing new offerings when criminal services face disruptions or are no longer available. Continuous monitoring and analysis of such platforms are essential for understanding and mitigating the evolving threats posed by phishing-as-a-service models.
Source Material: Sophos
Fortinet Endpoint Manager Server Vulnerability Exploited to Gain Unauthorized Access and Deploy RMM Tools
The Rundown
Kaspersky recently investigated an incident where attackers exploited a SQL injection vulnerability in FortiClient EMS (CVE-2023-48788). The vulnerability, affecting versions 7.0.1–7.0.10 and 7.2.0–7.2.2, allowed attackers to execute unauthorized commands via malicious SQL inputs. Attackers targeted exposed Windows servers used for secure device management and VPN policy distribution, infiltrating corporate networks by leveraging the vulnerability.
The incident highlights the persistent risk of unpatched systems. Exploitation of the vulnerability allowed attackers to gain unauthorized access and compromise sensitive data and systems. This underscores the critical importance of timely patch management and robust security configurations, particularly for internet-exposed assets in enterprise environments.
The attackers used a multi-stage attack chain, beginning with SQL injection, to enable remote command execution and deployment of remote monitoring and management (RMM) tools such as ScreenConnect and AnyDesk. Further activities included credential theft using tools like Mimikatz and defense evasion through manipulated security applications. Network enumeration, lateral movement, and persistence were achieved via payloads, including password recovery tools and remote access applications.
Notably, this campaign revealed the attackers’ use of dynamic infrastructure, such as altering ScreenConnect subdomains and employing services like webhook.site for reconnaissance and data collection. The adaptive techniques, like leveraging default configurations and publicly available binaries, highlight the evolving sophistication of attackers in exploiting enterprise vulnerabilities for widespread impact.
Source Material: Securelist by Kaspersky
2024 Leak Site Recap: Over 4,000 Firms Listed, Manufacturing Tops the List
The Rundown
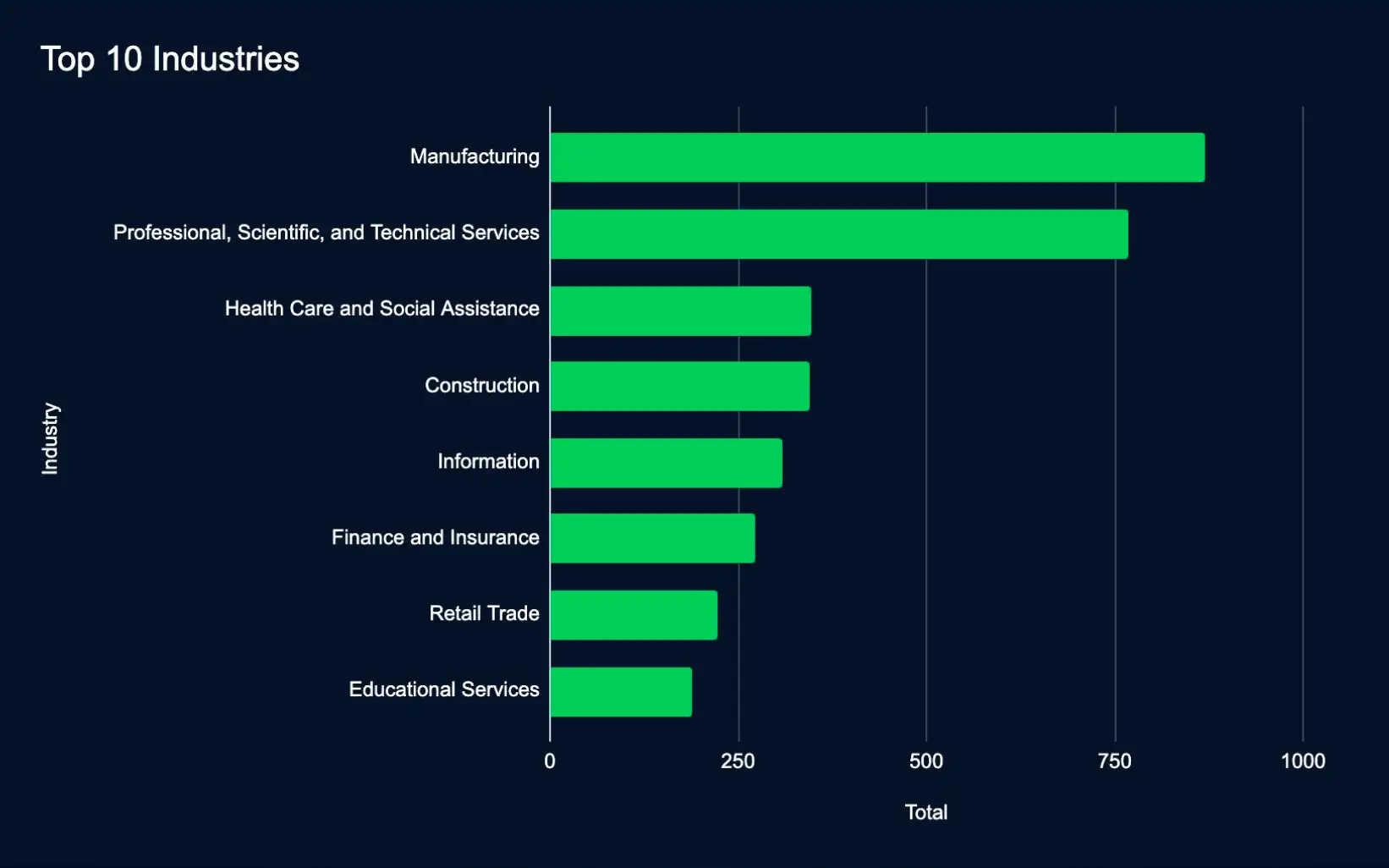
In 2024, 4,344 organizations were added to ransomware and data leak extortion sites. These organizations most frequently operated in Manufacturing, Professional, Scientific, and Technical Services, and Health Care and Social Assistance and were located in the United States, the United Kingdom, and Canada. The most active leak sites were Lockbit, Ransomhub, and Play. This activity underscores the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
CISA Adds Acclaim Systems and BeyondTrust Vulnerabilities to Exploited List
The Rundown
Between December 19 and 23, two vulnerabilities affecting Acclaim Systems (CVE-2021-44207) and BeyondTrust (CVE-2024-12356) products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. Failure to patch these flaws could lead to remote code execution. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share