Cyberhaven Chrome Extension Attack Unveiled as CISA Highlights Palo Alto PAN-OS Vulnerability Amid Rising Data Leaks
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Breaking the Chain: Analyzing the Cyberhaven Chrome Extension Attack
The Rundown
A recent Cyberhaven blog post, “Cyberhaven’s Preliminary Analysis of the Recent Malicious Chrome Extension,” sheds light on a supply chain attack conducted on December 24, 2024. The attack compromised a Cyberhaven employee’s access to the Google Chrome Web Store, enabling the attacker to publish a malicious version of Cyberhaven’s Chrome extension (version 24.10.4). This malicious extension was designed to exfiltrate cookies and authenticated sessions for specific websites. To date, targeted data has revolved around Facebook Ads accounts. Evidence suggests this incident is part of a broader campaign targeting various Chrome extensions.
This attack underscores the inherent risks of browser extensions, which, while intended to enhance user experience, can become significant security risks when compromised. It highlights the critical need for robust account security measures and rigorous monitoring of extension integrity to prevent unauthorized access and mitigate the risk of data breaches.
The breach originated from a phishing email that tricked the employee into authorizing a malicious OAuth application named “Privacy Policy Extension.” This authorization allowed the attacker to upload the compromised extension to the Chrome Web Store and distribute it to users. The attacker exploited a legitimate Google authorization process that bypassed multi-factor authentication, effectively circumventing standard security defenses.
Once installed, the malicious extension maintained continuous communication with a command-and-control server (cyberhavenext[.]pro), receiving configurations and executing unauthorized actions. This incident highlights the increasing sophistication of phishing attacks and the exploitation of legitimate authentication mechanisms to achieve malicious objectives.
The following section highlights the key takeaways to help you understand the broader implications of this attack.
Key Takeaways
This supply chain attack is a stark reminder of the evolving threats posed by compromised browser extensions. While designed to enhance productivity and user experience, these extensions can be exploited to bypass traditional security measures, steal sensitive information, and disrupt operations.
This incident highlights the dual risks posed by browser extensions. First, users inadvertently downloading a malicious extension can experience significant consequences, including unauthorized data exfiltration, compromised user accounts, and reputational damage. These extensions, when weaponized, can bypass traditional security measures and operate covertly within legitimate environments.
Second, attackers targeting an organization’s browser extension to compromise the extension’s users amplify the scale of the threat, transforming a single point of vulnerability into a widespread attack vector. Attackers can undermine an organization’s credibility and compromise its infrastructure by exploiting trust in legitimate extensions.
This can lead to significant reputational and operational damage beyond the initial compromise.
This incident demonstrates the far-reaching implications of browser extension threats and the growing sophistication of adversaries leveraging this attack surface. The following sections provide a detailed breakdown of the attack, including the attack chain, the malicious extension’s structure, and its operational mechanisms.
Source: Cyberhaven
Leak Sites: 93 Firms Listed, Professional Services and Manufacturing Top the List
The Rundown
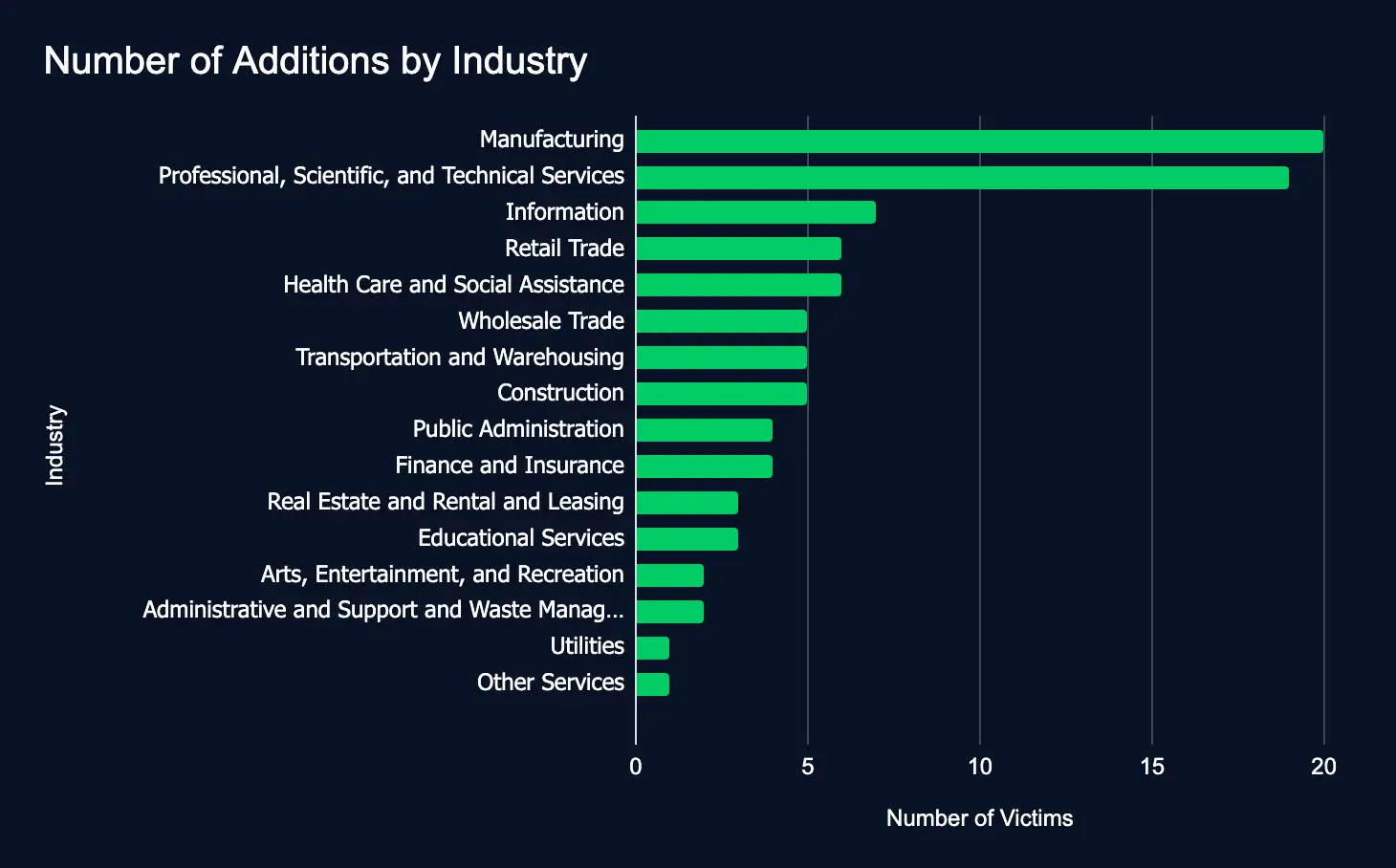
From December 23 to December 29, 22 ransomware and data extortion leak sites added 93 organizations from 17 industries. The top sectors were Manufacturing, Professional Services, and Information. The top regions were the United States, Israel, and Canada. The top leak sites were Funksec, Arcus Media, and Akira. The increase in new additions, 12 additions above the previous week, underscores the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
CISA Adds Palo Alto PAN-OS Vulnerability to Exploited List
The Rundown
Between December 25 and 31, CISA added one vulnerability (CVE-2024-3393) affecting Palo Alto PAN-OS to its Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
This newly cataloged vulnerability highlights looming risks for organizations using Palo Alto firewalls. Failure to patch this flaw could lead to denial of service, disrupt network traffic, and leave systems unprotected from external threats. If state-sponsored and cybercriminal attackers focus on this vulnerability, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share