LNK Attacks, Black Basta Malware, and a Surge in Leak Site Activity Highlight as CISA Highlights Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- LNK File Targeting Manufacturing Sectors Delivers Lumma Stealer and Amadey
- Black Basta Campaign Uses Teams to Deliver Zbot, DarkGate, and Custom Malware
- Leak Sites: 188 Firms Listed, Professional, Scientific, and Technical Services Tops the List
- CISA Adds Microsoft and CyberPanel Vulnerabilities to Exploited List
LNK File Targeting Manufacturing Sectors Delivers Lumma Stealer and Amadey
The Rundown
Cyble has published an analysis of a malicious campaign they assessed is targeting the manufacturing sector. The campaign leverages a malicious LNK file hosted on a WebDAV server disguised as a PDF document that delivers Lumma Stealer and Amadey Bot. This LNK file leverages Windows utilities such as ssh.exe and mshta.exe to execute malicious PowerShell commands, delivering the payloads in a multi-stage process. While the initial delivery vector is unknown, it was likely delivered via a phishing email, which included a link that points to the file.
The attackers rely heavily on obfuscated PowerShell scripts, encoded content, and encrypted payloads to bypass detection. These scripts execute processes in memory, sideload malicious DLLs, and ultimately deploy the final payloads into legitimate processes like explorer.exe and msiexec.exe. URL shortening and Google’s Accelerated Mobile Pages (AMP) framework further enhance the campaign’s stealth and effectiveness.
This campaign underscores the evolving sophistication of threat actors targeting critical industries like manufacturing. The reliance on Living-off-the-Land Binaries (LOLBins) and advanced evasion techniques highlights the challenges defenders face in detecting and mitigating such threats. The attackers’ focus on the exfiltration of sensitive data and establishing long-term persistence represents a significant risk to operational continuity and intellectual property.
Source Material: Cyble
Black Basta Campaign Uses Teams to Deliver Zbot, DarkGate, and Custom Malware
The Rundown
Rapid7 has released a report on Black Basta, a Ransomware-as-a-Service (RaaS) platform, detailing a renewed and evolving campaign conducted by its affiliates targeting organizations with a blend of social engineering techniques and custom malware. Beginning in October 2024, affiliates have leveraged email bombing and impersonation of IT support personnel via Microsoft Teams to deceive victims into installing remote management tools. These tactics enable initial access to networks, which affiliates use to deploy a diverse malware suite for data exfiltration and ransomware deployment.
The malware arsenal utilized by these affiliates includes Zbot, a banking trojan designed for credential theft, and DarkGate, a remote access trojan known for persistence, data exfiltration, and remote access capabilities. The campaign also incorporates custom-built credential harvesters tailored to specific targets. Together, these tools enable affiliates to escalate privileges, compromise sensitive information, and lay the groundwork for ransomware deployment, demonstrating the adaptability and effectiveness of Black Basta affiliates.
Recent campaigns demonstrate that leveraging spam email bombing and messaging via Microsoft Teams for initial access is not exclusive to Black Basta affiliates. Deepwatch recently published a Customer Advisory detailing our observation of similar activity, potentially attributed to Sangria Tempest, further underscoring the broader adoption of these techniques among threat actors.
Both campaigns reflect the increasing sophistication of ransomware ecosystems, where traditional phishing is combined with abuse of widely used collaborative platforms to deceive users and bypass standard defenses. This convergence of tactics emphasizes the need for organizations to implement robust endpoint hardening and security, comprehensive user awareness training, and vigilant system monitoring to defend against these widespread and evolving threats.
Source Material: Rapid7
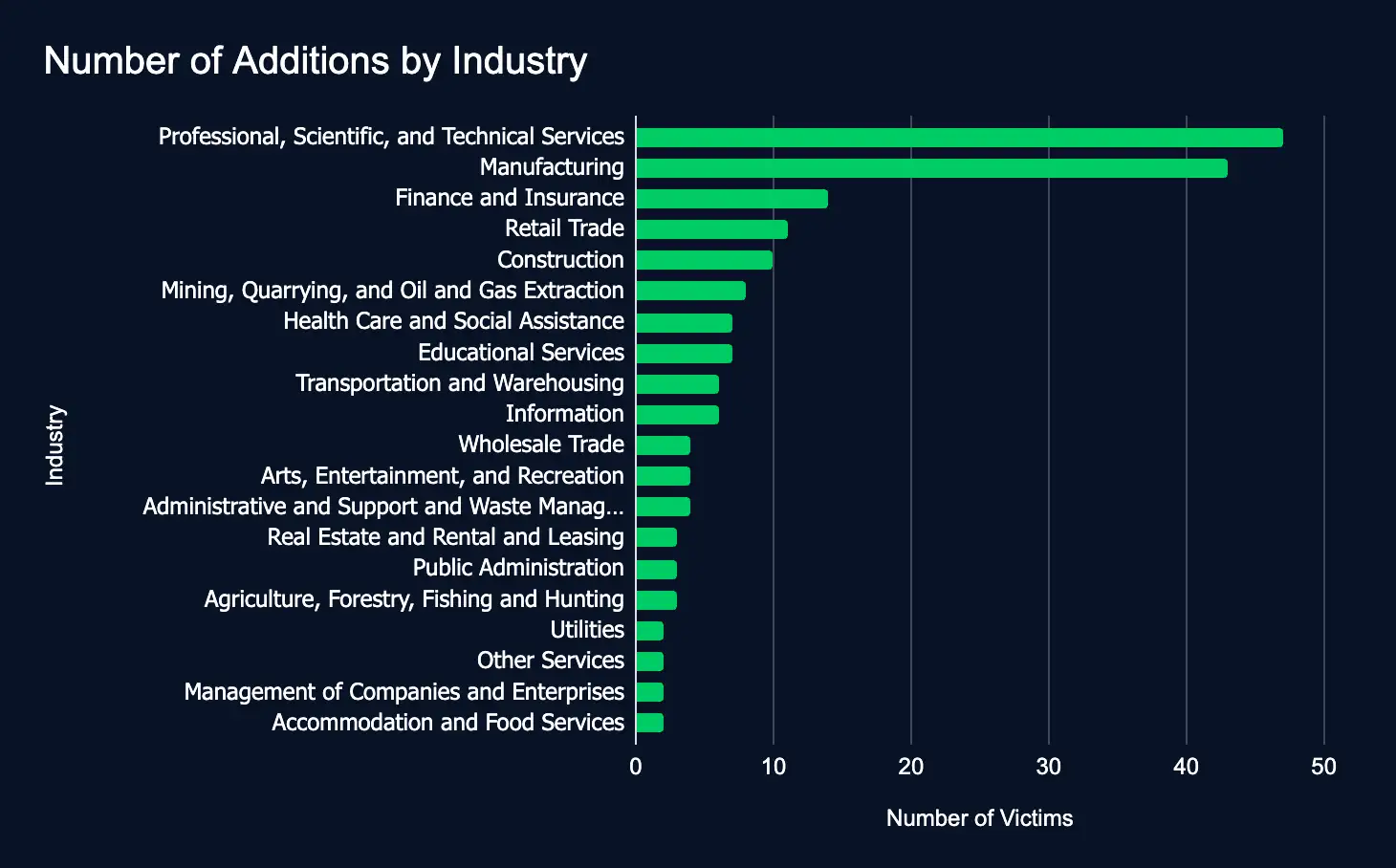
Leak Sites: 188 Firms Listed, Professional, Scientific, and Technical Services Tops the List
The Rundown
From December 2nd to December 8th, 25 ransomware and data extortion leak sites added 188 organizations from 20 different industries. The top industries were Professional, Scientific, and Technical Services; Manufacturing; and Finance and Insurance. The top regions were the United States, Germany, and the United Kingdom. The top leak sites were CL0P, Akira, and RansomHub. The increase in new additions, 107 from the previous week, underscores the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and ensure operational resilience globally.
CISA Adds Microsoft and CyberPanel Vulnerabilities to Exploited List
The Rundown
Between December 4th and the 11th, two vulnerabilities affecting Microsoft (CVE-2024-49138) and CyberPanel (CVE-2024-51378) products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. Failure to patch the Microsoft flaw could lead to Privilege Escalation, and Exploiting CyberPanel could lead to authentication bypass and arbitrary command execution. Timely action will be crucial to prevent the exploitation of these vulnerabilities.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share