Russian Adversaries Exploit Device Code Authentication, Earth Preta Uses MAVInject for Stealthy Attacks, Ransomware Trends Shift, and CISA Adds New Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Russian Adversaries Abuse Device Code Authentication for Persistent Access and Credential-Free Compromise
- Living-Off-The-Land: Earth Preta’s Process Injection with MAVInject.exe
- Ransomware and Data Extortion Trends (Feb. 10 – 16)
- Exploited Vulnerabilities in SimpleHelp, PANOS, and SonicWall Added to CISA’s Catalog – Immediate Mitigation Recommended
Russian Adversaries Abuse Device Code Authentication for Persistent Access and Credential-Free Compromise
The Rundown
Since August 2024, adversaries have exploited Microsoft’s Device Code Authentication flow in phishing campaigns to steal authentication tokens and gain persistent access to Microsoft 365 accounts.
This method allows attackers to bypass MFA while avoiding the need for passwords and granting long-term access to email, cloud storage, and other services. The stolen tokens enable data theft, lateral movement, and internal phishing, making detection and mitigation more challenging than traditional credential-based attacks.
Multiple Russian-aligned threat actors have leveraged this technique against government agencies, NGOs, and research institutions, but the risk is broader. Cybercriminals, including ransomware operators, business email compromise (BEC) actors, and initial access brokers, could adopt the same method.
Security teams should anticipate wider adoption of this low-cost, high-reward attack and implement defenses against token-based authentication abuse.
Source Material: Microsoft and Volexity
Living-Off-The-Land: Earth Preta’s Process Injection with MAVInject.exe
The Rundown
Earth Preta is using the Microsoft Application Virtualization Injector (MAVInject.exe) to stealthily inject malware, which could soon be adopted by a broader range of cybercriminals.
The use of MAVInject.exe for process injection is a low-cost, high-reward technique that could be adopted by other adversaries. By leveraging Living-Off-The-Land Binaries (LOLBins), attackers can bypass security detections designed to flag malicious process creation events. Therefore, security teams should expect broader use of MAVInject.exe-based injection in various attack scenarios and strengthen defenses accordingly.
The China-linked intrusion set Earth Preta (activities often overlap with Mustang Panda) is leveraging the legitimate Microsoft Application Virtualization Injector, MAVInject.exe, to stealthily inject its TONESHELL backdoor into waitfor.exe, a benign Windows process. This method enables the backdoor to be executed undetected. The attack likely began with a spear-phishing email delivering an executable dropper, which deploys multiple legitimate and malicious files, including a decoy PDF, an executable, and a modified DLL.
The dropper executes the dropped executable, which sideloads the malicious DLL and then checks for specific antivirus processes before injecting the payload into waitfor.exe via MAVInject.exe or direct process injection APIs. Once active, TONESHELL establishes command-and-control (C2) communication with its command-and-control server, enabling remote control, file manipulation, and persistence.
Source Material: Trend Micro
Ransomware and Data Extortion Trends (Feb. 10 – 16)
The Rundown
Ransomware and data extortion activity surged between February 10 and 16, with an 83% increase in listed organizations compared to the previous week.
This escalation reinforces the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
In the reporting time frame, 256 organizations across 20 industries were listed on 24 ransomware and data extortion leak sites, marking a 116-listing increase from the previous week’s 140 victims. This sharp rise highlights the persistent and evolving threat posed by ransomware actors.
Key Trends:
- Most targeted industries: Manufacturing, Professional Services, and Retail Trade.
- Most affected countries: United States, Canada, and Australia.
- Most active leak sites: Clop, Ransomhub, and Akira.
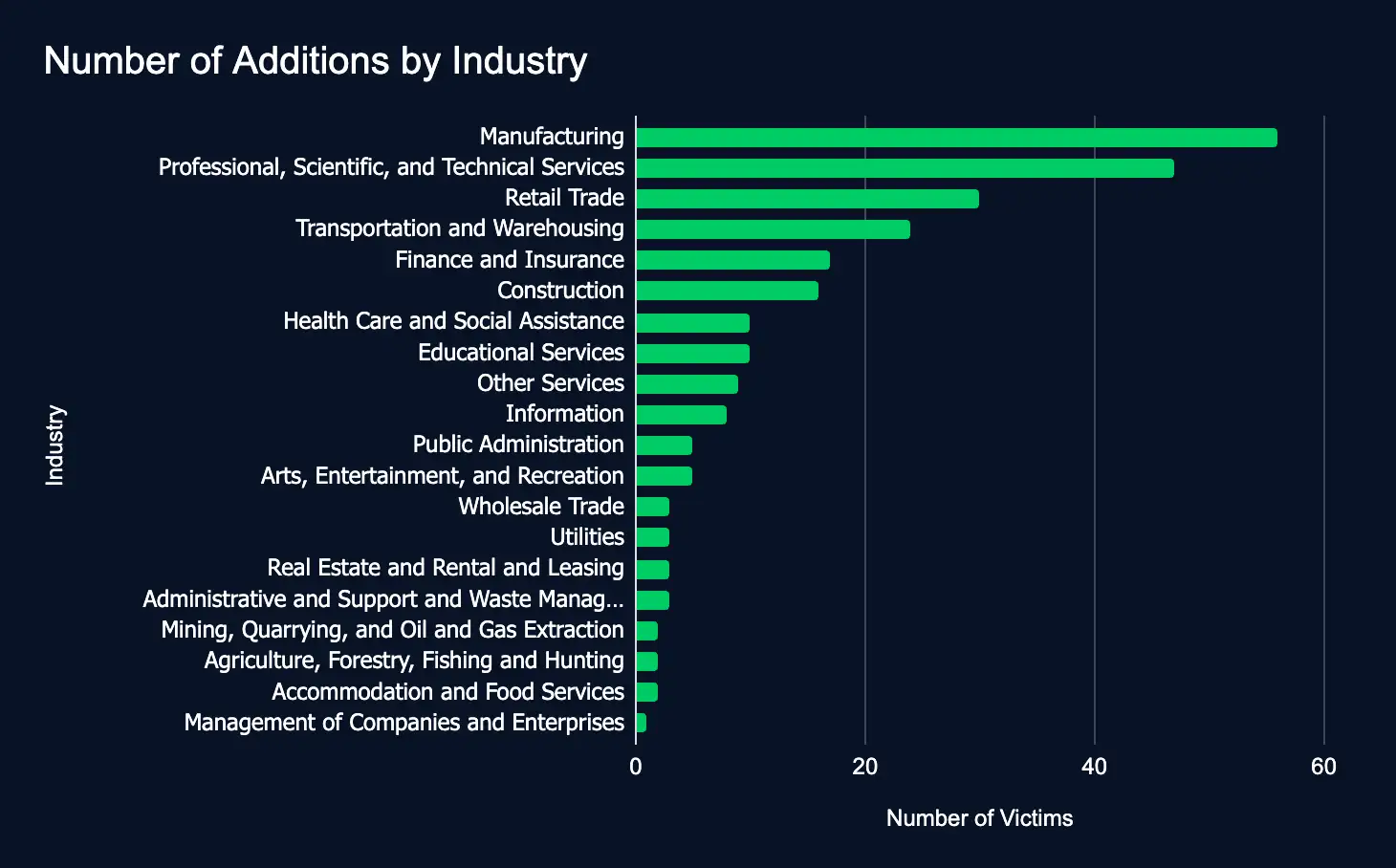
Exploited Vulnerabilities in SimpleHelp, PANOS, and SonicWall Added to CISA’s Catalog – Immediate Mitigation Recommended
The Rundown
Between February 13 and 19, three vulnerabilities affecting SimpleHelp (CVE-2024-57727), PANOS (CVE-2025-0108), and SonicWall (CVE-2024-53704) products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share