Green Nailao Campaign Blurs Cybercrime and Espionage, LockBit Targets Confluence, Ransomware Trends Evolve, and CISA Adds New Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Ransomware or Espionage? Green Nailao Campaign Blurs the Line Between Cybercrime and State-Sponsored Operations
- LockBit Ransomware Exploits Confluence
- Ransomware and Data Extortion Trends (Feb. 17 – 23)
- Exploited Vulnerabilities in PAN-OS, Craft, Microsoft, Oracle, Adobe, and Synacor Added to CISA’s Catalog
Ransomware or Espionage? Green Nailao Campaign Blurs the Line Between Cybercrime and State-Sponsored Operations
The Rundown
A cyber campaign leveraging Chinese espionage-linked malware and previously undocumented ransomware has targeted European organizations, raising questions about the attackers’ true intent.
Blending cyberespionage-linked tools with ransomware suggests an operation with unclear objectives—potentially combining data theft, financial extortion, and operational testing. The discrepancies between victim reporting and attack methodologies highlight intelligence gaps that complicate attribution and defensive measures.
In the latter half of 2024, Orange Cyberdefense and Trend Micro observed a series of cyberattacks impacting European organizations. Orange reported victims in the healthcare sector, while Trend Micro reported that most victims were in the manufacturing sector, with no victims in the healthcare sector.
Attackers may have exploited CVE-2024-24919 in Check Point VPN appliances and/or used compromised credentials to gain access. They then deployed ShadowPad and PlugX via DLL side-loading, maintaining persistence and enabling potential data exfiltration, including credential theft from ntds.dit databases.
NailaoLocker ransomware was later introduced using similar side-loading techniques, but Orange Cyberdefense reported that it had a simplistic design and the campaign had minimal financial gain, raising doubts about its primary purpose. While Orange Cyberdefense reported data archiving, suggesting a data theft objective, Trend Micro did not report exfiltration attempts, leaving its role in the attack uncertain.
Given these observations, the attackers’ objectives remain ambiguous, with three plausible explanations:
- Cyber Espionage: Targeting healthcare and manufacturing suggests interest in sensitive personal data and intellectual property.
- Financial Gain: Ransomware deployment could indicate monetary intent, though its effectiveness was limited.
- Operational Testing or Moonlighting: The mix of advanced and rudimentary tools suggests that espionage insiders are testing new techniques or conducting an unsanctioned “moonlighting” operation.
Both sources’ findings underscore the complexity of modern cyber threats, where espionage, financial motives, or other alternatives can overlap. This case highlights the need for correlating intelligence across multiple sources to accurately assess the full scope and intent of evolving cyber campaigns.
Source Material: Trend Micro and Orange Cyberdefense
LockBit Ransomware Exploits Confluence
The Rundown
Attackers affiliated with the LockBit ransomware operation exploited CVE-2023-22527 in Confluence to gain initial access before establishing persistence, escalating privileges, exfiltrating data, and ultimately distributing ransomware across the environment.
This attack underscores the critical risk posed by unpatched internet-facing applications and the increasing complexity of ransomware attacks.
The attack began with the exploitation of CVE-2023-22527, a remote code execution vulnerability in Confluence, allowing the threat actors to execute arbitrary commands. After breaching the system, they used PowerShell and Metasploit to establish persistence, conduct reconnaissance, and attempt to install the remote administration tool AnyDesk.
They also deployed Mimikatz to extract credentials, performed network enumeration using NetScan, and identified additional high-value targets, including a Veeam backup server and file shares. By leveraging stolen credentials, they moved laterally, gaining Domain Admin access before exfiltrating sensitive data to MEGA.io using Rclone.
The final phase involved LockBit ransomware deployment, initiated manually via RDP and scaled using PDQ Deploy, a legitimate enterprise software tool. The attackers also targeted the Exchange server to disrupt communications, systematically terminating critical services before executing ransomware across all accessible systems.
Their approach demonstrates an evolving ransomware threat model that integrates advanced penetration techniques with mass deployment strategies, significantly increasing the scope and damage of attacks.
Source Material: The DFIR Report
Ransomware and Data Extortion Trends (Feb. 17 – 23)
The Rundown
Ransomware and data extortion activity dropped between February 17 and 23, with a 42% decrease in listed organizations compared to the previous week.
This decline reinforces the unpredictable nature of ransomware activity. It’s almost certainly not a trend that will continue in the future. Therefore, with new additions listing organizations in nearly all industries, organizations must strengthen cybersecurity measures to bolster cyber resilience.
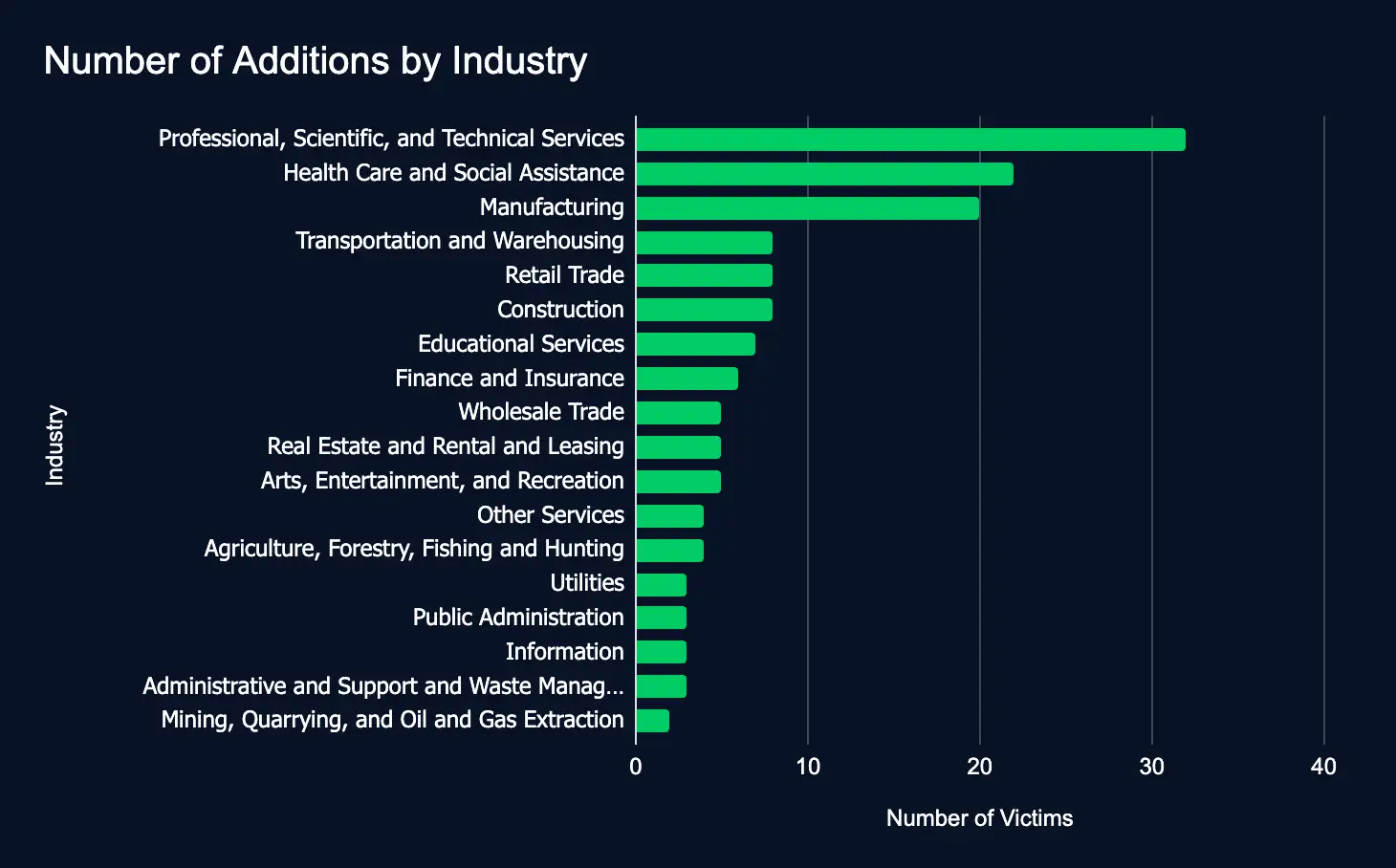
In the reporting time frame, 148 organizations across 18 industries were listed on 21 ransomware and data extortion leak sites, a decrease of 108 listings from the previous week’s 256 victims.
Key Trends:
- Most targeted industries: Professional, Scientific, and Technical Services, Health Care and Social Assistance, and Manufacturing.
- Most affected countries: United States, Canada, and Mexico.
- Most active leak sites: Ransomhub, Akira, and Killsecurity.
Exploited Vulnerabilities in PAN-OS, Craft, Microsoft, Oracle, Adobe, and Synacor Added to CISA’s Catalog – Immediate Mitigation Recommended
The Rundown
Between February 20 and 26, seven vulnerabilities affecting PAN-OS, Craft, Microsoft, Oracle, Adobe, and Synacor products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share