China-Linked Cyber Espionage Exploits IIS, Black Basta and Cactus Ransomware Show Overlapping Tactics, and CISA Flags New Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- China-Linked Cyber Espionage: Exploiting IIS Vulnerabilities for Persistent Access via Squidoor Malware
- Black Basta and Cactus: Shared Tactics, Infrastructure, and the Evolution of Ransomware Operations
- Ransomware and Data Extortion Trends (Feb. 24 – Mar. 02)
- Exploited Vulnerabilities in Progress, Microsoft, Hitachi, Cisco, VMware, and Linux Added to CISA’s Catalog – Immediate Mitigation Recommended
China-Linked Cyber Espionage: Exploiting IIS Vulnerabilities for Persistent Access via Squidoor Malware
The Rundown
A campaign conducted by a China-based threat actor has exploited Internet Information Services (IIS) vulnerabilities to gain initial access, allowing them to deploy web shells and a newly discovered sophisticated backdoor. Observed attacks have compromised entities in government, defense, telecommunications, education, and aviation sectors across Southeast Asia and South America.
This campaign exemplifies a highly coordinated cyber-espionage operation that leverages sophisticated tooling to ensure long-term access to targeted environments.
Post access, attackers leverage cURL and Impacket to move laterally, deploying additional web shells across the network. The Squidoor malware is installed by executing shellcode via Microsoft Console Debugger. Once installed, Squidoor exhibits advanced capabilities, including host reconnaissance, arbitrary command execution, file exfiltration, and lateral movement using Windows Remote Management (WinRM) and pass-the-hash attacks. The malware establishes persistence through scheduled tasks and uses various covert communication methods, including HTTP, TCP, UDP, ICMP tunneling, and Outlook API.
Source Material: Palo Alto Unit 42
Black Basta and Cactus: Shared Tactics, Infrastructure, and the Evolution of Ransomware Operations
The Rundown
Two major ransomware groups, Black Basta and Cactus, are using identical attack chains to infiltrate organizations, deploying Quick Assist and BackConnect malware for remote access and persistence.
This development confirms a direct link between Black Basta and Cactus, as recent leaks reveal that several Black Basta members have joined Cactus. This has resulted in Black Basta tactics, infrastructure, and command-and-control (C2) servers appearing in Cactus attacks, making attribution harder and introducing difficulties in response efforts.
Both groups leveraged social engineering via Microsoft Teams, Quick Assist, and OneDriveStandaloneUpdater.exe to gain initial access, execute malware, and establish persistence. Both attacks involve DLL sideloading.
The Cactus ransomware attack expanded its reach, targeting ESXi servers and leveraging SystemBC malware, as well as WinSCP and WinRM for lateral movement and potential data exfiltration. The overlapping membership and shared attack techniques suggest that future Cactus attacks will mirror Black Basta’s previous campaigns, requiring organizations to rapidly adapt their response plans.
Source Material: Trend Micro
Ransomware and Data Extortion Trends (Feb. 24 – Mar. 02)
The Rundown
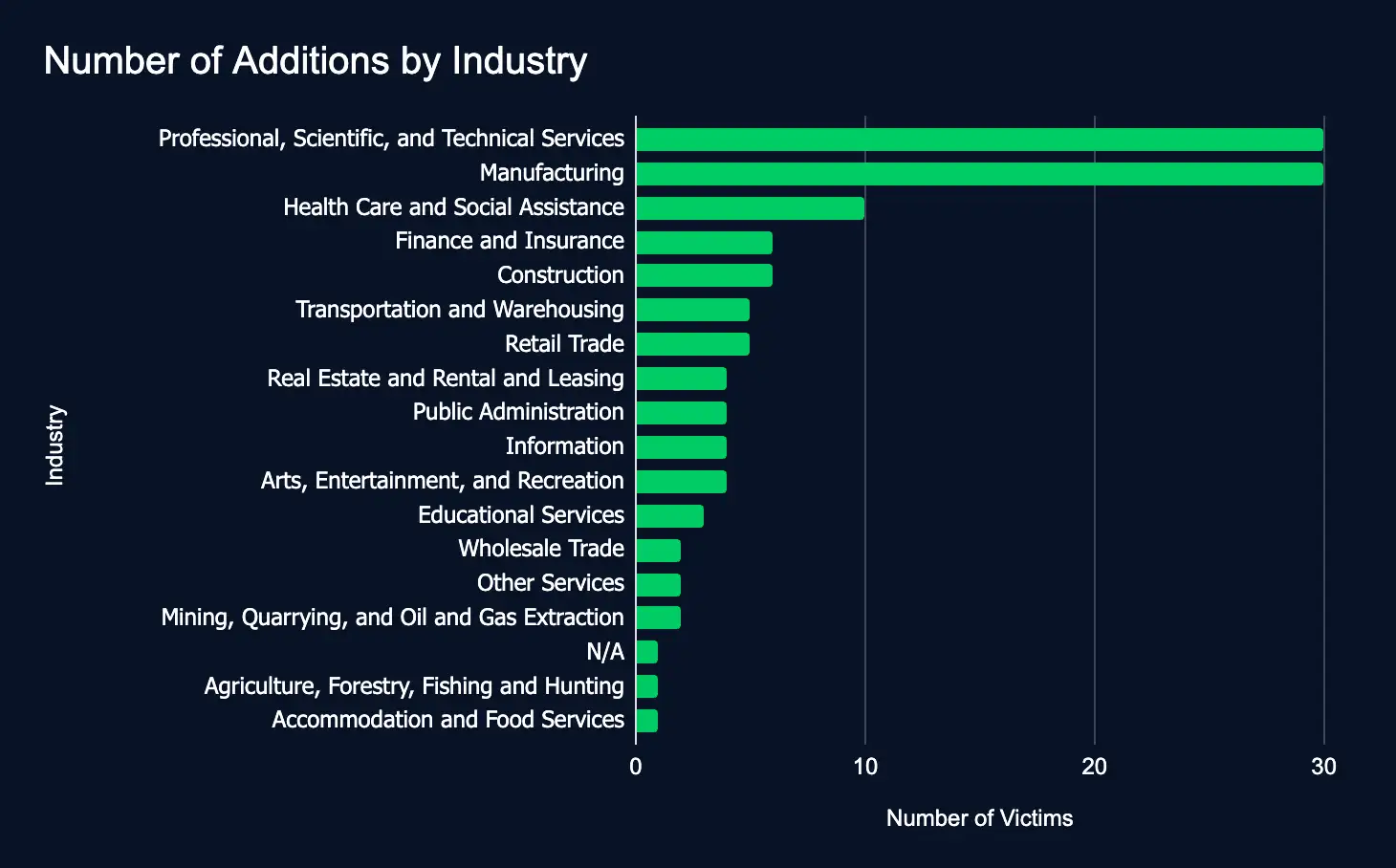
Ransomware and data extortion leak sites listed 120 organizations across nearly all industries between February 24 and March 02, a 19% drop in reported listings from the previous week.
This decline reinforces the unpredictable nature of ransomware activity. It’s almost certainly not a trend that will continue in the future. Therefore, with new additions listing organizations in nearly all industries, organizations must strengthen cybersecurity measures to bolster cyber resilience.
Key Trends:
- Most targeted industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Health Care and Social Assistance.
- Most affected countries:
- United States
- Canada
- Germany
- Most active leak sites:
- Ransomhub
- Cactus
- Akira
Exploited Vulnerabilities in Progress, Microsoft, Hitachi, Cisco, VMware, and Linux Added to CISA’s Catalog – Immediate Mitigation Recommended
The Rundown
Between February 27 and March 05, nine vulnerabilities affecting Progress, Microsoft, Hitachi, Cisco, VMware, and Linux products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share