CISA Exposes Phobos Affiliates, New Attack Chain Steals NTLM, Plus Terminator and BABYSHARK
This week: CISA exposes TTPs and IoCs of Phobos, threat actors reveal a new attack chain that steals NTLM information, a new malicious tool called Terminator is leveraging vulnerable Zemana drivers, and TODDLERSHARK seen in ScreenConnect attacks–all this and over 100 new data leak victims.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Customer Awareness Advisory: Threat Actor Exploits Critical TeamCity Vulnerability to Deploy Malware
- CISA Published Phobos Ransomware Affiliates Known TTPs and IoCs
- TA577 Employs New Attack Chain to Steal NTLM Information
- Threat Actors Use Terminator to Disable Security Solutions and Leverage Vulnerable Drivers in Attacks
- BABYSHARK Variant Deployed following Exploited ScreenConnect Vulnerability
- Latest Additions to Data Leak Sites
- CISA Adds CVE-2024-1709 CVEs to Known Exploited Vulnerabilities Catalog
Customer Awareness Advisory: Threat Actor Exploits Critical TeamCity Vulnerability to Deploy Malware
Recently, Rapid7 published technical details of two vulnerabilities (CVE-2024-27198 and CVE-2024-27199) impacting JetBrans TeamCity server versions 2023.11.3 and earlier. Within hours, Proof-of-Concept exploits targeting CVE-2024-27198 were published to GitHub. Deepwatch has confirmed a threat actor compromised an organization in the Finance and Insurance sector, exploiting the TeamCity vulnerability CVE-2024-27198 to gain initial access and laterally move to other systems. Read the full Customer Awareness Advisory.
CISA Published Phobos Ransomware Affiliates Known TTPs and IoCs
Ransomware – Phishing – RDP Abuse – Phobos Ransomware – SmokeLoader – Angry IP Scanner – Mega[.]io – Industries/All
Threat Analysis
Threat actors affiliated with the Phobos ransomware ransomware-as-a-service (RaaS) gain access to vulnerable networks typically through the following methods:
- Phishing campaigns with email attachments embedded with hidden payloads, such as SmokeLoader. Then, use the malware’s functionality to download the Phobos payload and exfiltrate data from the compromised system.
- Leveraging exposed Remote Desktop Protocol ports using IP scanning tools like Angry IP Scanner. Then, use open-source brute force tools to gain access.
- Leveraging RDP on Microsoft Windows environments.
Once access is gained, affiliates have been observed performing the following activities:
- Using Windows Command Shell to perform commands with Windows shell functions.
- Use open-source tools to enumerate the active directory.
Phobos operations featuring SmokeLoader employ the following three-phase process to decrypt a payload, allowing affiliates to deploy additional destructive malware:
- Injects code into running processes, allowing the malware to evade network defense tools.
- Uses a stealth process to obfuscate command and control (C2) activity by producing requests to legitimate websites. Within this phase, the malware prepares a portable executable for deployment in the final stage.
- Unpacks and sends a program-erase cycle from stored memory, extracting it from a SHA 256 hash as a payload. Following successful payload decryption, affiliates can begin downloading additional malware.
Phobos affiliates have been observed evading defenses by:
- Modifying system firewall configurations using commands like netsh firewall set opmode mode=disable.
- Using Universal Virus Sniffer, Process Hacker, and PowerTool.
To maintain persistence, affiliates have been observed performing:
- Use commands such as Exec.exe or the bcdedit[.]exe control mechanism.
- Use Windows Startup folders and Run Registry Keys such as C:/Users\Admin\AppData\Local\directory.
To elevate privileges, affiliates have been observed:
- Using built-in Windows API functions to steal tokens, bypass access controls, and create new processes, leveraging the SeDebugPrivilege process.
- Attempting to authenticate using cached password hashes on victim machines until they reach domain administrator access.
For discovery and credential access, affiliates have been observed performing the following activities:
- Using open-source tools such as Bloodhound and Sharphound to enumerate the active directory.
- Exporting browser client credentials using Mimikatz, NirSoft, and Remote Desktop Passview.
- Phobos ransomware can enumerate connected storage devices and running processes.
Affiliates use the following tools and techniques to exfiltrate targeted legal documentation, financial records, technical documents (including network architecture), and databases for commonly used password management software, typically archived as either a .rar or .zip file:
- WinSCP and Mega.io for file exfiltration.
- Use WinSCP to connect directly from a victim network to an actor-controlled FTP server.
- Install Mega.io and use it to export victim files directly to a cloud storage provider.
After exfiltrating sensitive data, affiliates then:
- Use vssadmin.exe and Windows Management Instrumentation command-line utility (WMIC) to discover and delete volume shadow copies in Windows environments.
- Encrypt all connected logical drives using the Phobos ransomware. After the ransom note has been populated on infected workstations, Phobos ransomware continues to search for and encrypt additional files.
Affiliates have been observed using the following methods to contact and extort victims, forcing them to pay ransoms:
- Some affiliates extort victims via email, while others have used voice calls to contact victims.
- Some affiliates use data leak sites to list victims and host stolen victim data.
- Some use instant messaging applications such as ICQ, Jabber, and QQ to communicate with victims.
Risk & Impact Assessment
Phobos Ransomware presents a significant risk to organizations due to its various affiliates, which broadens its reach and potential impact across multiple sectors. The risk associated with Phobos Ransomware is intensified by its proven ability to exfiltrate sensitive data and make systems inaccessible. While the exact number of victims is unknown, these methods demonstrate a likelihood of Phobos Ransomware impacting organizations, exacerbated by its affiliates’ tactics to evade detection and use of sophisticated tools for data exfiltration and encryption. The unpredictable nature of its affiliate model, where different actors may deploy the ransomware in varied ways, further complicates the risk assessment, making it a considerable threat to any organization lacking stringent cybersecurity measures.
The impact of a Phobos Ransomware attack on an organization can be severe and multifaceted. Financial repercussions are often immediate, with demands for ransom payments coupled with the costs associated with system downtime, data recovery, and potential breaches of compliance with data protection regulations. Beyond the direct financial strain, organizations face the prospect of reputational damage, which can lead to lost business and eroded trust among clients and partners. The operational disruption, potential loss of sensitive or proprietary information, and the time and resources required to remediate the infection and strengthen defenses post-attack all contribute to the long-term impacts on an organization’s financial health and competitive position. Given these considerations, recognizing and mitigating the risks associated with Phobos Ransomware cannot be overstated.
Source Material: CISA, #Stop Ransomware: Phobos Ransomware
TA577 Employs New Attack Chain to Steal NTLM Information
Threat Actor – Phishing – NTLM Hash Theft – TA577 – Impacket – All Industries
Threat Analysis
TA577 actors sent tens of thousands of emails targeting hundreds of organizations globally. Emails masqueraded as or were replies to previous emails, a technique known as thread hijacking, with a zipped archive attached containing an HTML file.
In one example, the email inquired if the recipient saw the document they sent previously and included content that appeared to be from a previous email, providing the document name and a password. Each attached ZIP file has a unique file hash. Proofpoint states that each recipient’s HTML file is unique, possibly using the same document name provided in the email. When the recipient opened the HTML file, it triggered a connection to one of 15 known Server Message Block (SMB) servers that hosted a .txt file with names like 2.txt, A.txt, and yEZZ.txt (for example, file://66[.]63[.]188[.]19/bmkmsw/2[.]txt).
At this time, malware delivery from the SMB servers has not been observed. However, any allowed connection could compromise NTLM hashes, along with revealing other sensitive information such as computer names, domain names, and usernames in clear text. Based on the characteristics of the attack chain and tools used, Proofpoint assesses with high confidence that TA577’s objective is to capture NTLMv2 Challenge/Response pairs from the SMB server to steal NTLM hashes.
The reason TA577 delivered the malicious HTML files in a zip archive was to generate a local file on the host. If the threat actors sent the URI directly in the email body to recipients using Outlook mail clients patched since July 2023, the attack would fail. Furthermore, disabling guest access to SMB would not mitigate the attack since the file must attempt to authenticate to the external SMB server to determine if it should use guest access.
Proofpoint assesses that TA577’s likely objective is to exploit these hashes for password cracking or facilitate “Pass-The-Hash” attacks using other vulnerabilities within the targeted organization to move laterally within an impacted environment. Evidence supporting this hypothesis can be observed in the packet capture where the default NTLM server challenge “aaaaaaaaaaaaaaaa” and the default session ID “Acct: admin Domain:USER-PC Host:USER-pC” are shown in the traffic, which is uncommon in standard SMB servers, and indicates the use of the open-source toolkit Impacket.
High-level overview of TA577’s new attack chain:
- Initial Access (T1566.001 Phishing: Spearphishing Attachment): TA577 actors sent phishing emails with a ZIP archive attached containing an HTML file.
- Execution (T1204.002 User Execution: Malicious File): The recipient opens the malicious HTML file.
- Credential Access (T1557.001 Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay): Opening the HTML file triggers a connection to an external SMB server, capturing NTLMv2 Challenge/Response pairs.
- Command and Control (T1071.002 Application Layer Protocol: File Transfer Protocols): The threat actors used SMB servers to interact with the victim’s machine and host the .txt files, facilitating unauthorized access to sensitive data.
- Lateral Movement (T1550.002 Pass the Hash): The ultimate goal of capturing NTLM hashes may suggest an intent to use this information for lateral movement within the network, mainly through Pass-the-Hash attacks, exploiting these hashes to gain unauthorized access to other systems or data.
OR
- Credential Access (T1110.002 Brute Force: Password Cracking): Another goal of capturing NTLM hashes is to use this information to access credentials, mainly through brute force cracking, exploiting these hashes to gain unauthorized access to systems or data.
Proofpoint assesses that the rate at which TA577 adopts and employs new tactics, techniques, and procedures (TTPs) demonstrates that the threat actor likely has the time, resources, and experience to rapidly iterate and test new delivery methods. Additionally, Proofpoint states that TA577, in addition to other initial access brokers (IABs), appears to closely monitor the threat landscape and knows when and why specific attack chains fail to be effective and will quickly develop new methods to bypass detections to increase the effectiveness and likelihood of victim engagement with their payload. Furthermore, Proofpoint has also seen an increase in multiple threat actors abusing file scheme URIs to direct recipients to external file shares, such as SMB and WebDAV, to access remote content for malware delivery.
Risk & Impact Assessment
The emergence of TA577’s new attack chain presents a considerable risk to organizations globally. This risk is primarily due to the nature of the phishing campaign and the subsequent stages of the attack, which are designed to steal and exploit NTLM hashes. Given the targeted and deceptive approach of thread hijacking (or using emails that appear as replies) and using unique HTML files to circumvent detection, the likelihood of TA577’s campaign impacting an organization is significant. The campaign’s effectiveness is further compounded by its ability to bypass conventional security measures and the actors’ demonstrated adaptability in employing new tactics to maintain the efficacy of their attacks. While quantifying the exact likelihood is challenging without specific data on the campaign’s victimology, the nature of the attack, combined with the actors’ persistent innovation and the global scale of the campaign, while limited to hundreds of organizations, suggests a likelihood that organizations will be targeted.
The impact of a cyberattack leveraging TA577’s attack chain could be severe for an affected organization. The theft of NTLM hashes poses immediate security risks, including compromising credentials and unauthorized system access. This could lead to further malicious activities, such as lateral movement within the network, escalation of privileges, and, potentially, the deployment of additional payloads such as ransomware.
From a financial perspective, the implications could be substantial, encompassing operational disruptions, data breach response costs, legal fees, and potential regulatory fines. The reputational damage from such an attack could significantly undermine stakeholder confidence, leading to lost business and diminished customer trust. Moreover, the strategic impact of sensitive data loss or compromise could have enduring effects on the organization’s competitive position and operational integrity. Given these potential consequences and the likelihood of being targeted, organizations must recognize the gravity of this threat and consider prioritizing measures to mitigate the associated risks.
Source Material: Sophos, TA577’s Unusual Attack Chain Leads to NTLM Data Theft
Threat Actors Use Terminator to Disable Security Solutions and Leverage Vulnerable Drivers in Attacks
Vulnerable Driver Abuse – Bring Your Own Vulnerable Driver – Security Solution Disabling – Terminator – Zemana Anti-Logger Driver – Zemana Anti-Malware Driver – All Industries
Threat Analysis
Sophos recently disclosed that threat actors are leveraging a tool known as Terminator to disable security solutions in attacks. Terminator was first released in May 2023 and employs the Bring Your Own Vulnerable Driver (BYOVD) technique, leveraging vulnerable Zemana drivers. Since the initial release of Terminator, multiple variations of the tool, including open-source versions, a C# port, and a version written in Nim, have been released.
According to Sophos, the BYOVD technique is increasingly becoming popular with ransomware actors and lower-tier threat actors, possibly due to the sheer number of vulnerable drivers (as of 4 March 2024, there are 364 “vulnerable drivers” listed on the open-source vulnerable driver repository loldrivers.io). Coupled with the proliferation of vulnerable drivers is the advent of off-the-shelf kits and tools that use Bring Your Own Vulnerable Driver (BYOVD) techniques, like Terminator, that are now widely bought and sold on criminal forums.
Analysis of Terminator shows that it appears to be leveraging the BYOVD technique, leveraging two Zemana vulnerable drivers, zam64.sys (Zemana Anti-Logger) or zamguard64.sys (Zemana Anti-Malware, or ZAM). These drivers contain the same vulnerability and insufficient verification of processes that can send IOCTL codes to the driver and request various functionalities. These drivers maintain an ‘allow list’ of legitimate, trustworthy processes. However, a threat actor can add their own process to the allow list by sending a specific IOCTL code and passing a running processes ID as a parameter. Once added, the threat actor can request several functionalities from the driver, including terminating a targeted process, such as an Endpoint Detection and Response solution, by sending a specific IOCTL request code.
However, to utilize the driver in this way, a threat actor would need administrative privileges and a User Account Control (UAC) bypass to install the driver, or they would need to trick a user into installing the driver via social engineering. While leveraging vulnerable legitimate drivers could undoubtedly allow a threat actor to terminate security solution processes, it’s not necessarily straightforward, and escalating privileges could trigger other security protections.
Reviewing behavioral detection telemetry for the past six months, Sophos discovered several incidents in which threat actors used the Zemana Anti-Logger or Anti-Malware drivers. In some cases, threat actors ported the open-source Terminator projects to different languages or obfuscated them through packers to circumvent detection. The following provides an overview of attacks that are illustrative of the patterns Sophos observed across their telemetry data:
On 13 September and 10 October 2023, two attacks using very similar methodologies likely exploited a vulnerable Citrix application to gain initial access. From there, the threat actors injected a payload into the Windows Error Reporting process, wermgr.exe. Next, they tried to disable Sophos by issuing two commands, wmic service where \”PathName like ‘%sophos%’\” call stopservice /nointeractive and wmic service where \”PathName like ‘%sophos%’\” call delete /nointeractive.
The targeted devices had tamper protection enabled, so the attempts to disable and remove the Sophos services failed. Adjusting to the failed attempts, the threat actor dropped a driver and then deployed an EXE file named ter.exe. The binary unpacks itself to a slightly modified version of Terminator.
Upon execution, the binary loads the driver (“BINARY” resource) and decrypts via AES-256, with a hardcoded key in the binary. Finally, the binary writes the decrypted content into a newly allocated section and executes it. However, the attempt to load the driver was blocked. The PDB path string in the ter.exe binary noted the original project name, “Terminator-master,” which may suggest the threat actor modified code from the Terminator GitHub repository.
In another attack on 15 December 2023, threat actors targeted a healthcare organization, gaining initial access to an exposed server. However, if it was known, Sophos did not disclose the exact access method. Immediately after gaining initial access, the threat actors attempted to execute a PowerShell command to download a text file containing a PowerShell script from a command and control (C2) server. This PowerShell script tried to install the XMRig cryptominer on the targeted system. However, this was blocked. Due to this failed attempt, the threat actors tried to disable the Endpoint Detection and Response (EDR) client by running the Nim version of Terminator. However, the effort to load the driver was also blocked.
In an attack on 25 December 2023, the threat actor gained access to a single machine by an unknown means. First, they tried to load the Zemana Anti-Logger driver (zam64.sys), masquerading it as updatedrv.sys, from two different locations, %sysdir%\drivers\updatedrv.sys and <d>\programdata\usoshared\updatedrv.sys.
After these attempts failed, the threat actor switched to AuKill, another known tool that can disable security solutions, where the Process Explorer driver was named ped.sys in the temp folder. However, this attack was likely blocked as well.
Risk & Impact Assessment
Terminator toolkit and its variants represent a substantial risk to organizations, mainly due to their ability to disable security solutions and facilitate further malicious activities. The risk associated with these toolkits arises from their BYOVD technique, which allows threat actors to gain kernel-level privileges and perform various destructive actions, such as disabling Endpoint Detection and Response (EDR) solutions. Given the observed adaptations and the proven capabilities of Terminator variants to bypass security solutions, there is a recognized potential for these tools to impact organizations. However, estimating this risk is challenging due to dynamic variables, including the evolving nature of the Terminator toolkit, the diversity and operational scale of the threat actors employing it, and the range of potential targets. These variables introduce a degree of uncertainty in our risk estimation. While the exact success rate of Terminator in compromising organizations is difficult to quantify, its technical sophistication, coupled with the increasing popularity of BYOVD techniques among threat actors, suggests a growing threat.
A cyberattack leveraging Terminator could have severe consequences for an organization. From an operational perspective, Terminator’s ability to disable security solutions can facilitate various actions, such as deploying additional malware, potentially leading to extensive system compromise and operational disruption. Financial implications may include significant expenditures on incident response, system remediation, legal fees, and potential fines for regulatory compliance violations. Moreover, the reputational damage from a successful breach could lead to loss of customer trust, attrition, and competitive disadvantage, especially if sensitive data is exfiltrated or tampered with. Considering these risks and impacts, organizations must assess their vulnerability to such threats and prioritize enhancing their defensive strategies against BYOVD techniques and tools like Terminator.
Source Material: Sophos, It’ll be back: Attackers still abusing Terminator tool and variants
BABYSHARK Variant Deployed following Exploited ScreenConnect Vulnerability
Vulnerability Exploitation – Malware – Threat Actor – BABYSHARK – TODDLERSHARK – Kimsuky – North Korea- ConnectWise ScreenConnect CVE-2024-1708 & CVE-2024-1709
Threat Analysis
During the attack, initial access was gained to the victim’s workstation by the threat actor through the exploitation of an exposed setup wizard of the ConnectWise ScreenConnect application.
With ”hands on keyboard” access the threat actors then used cmd.exe to execute mshta.exe with a URL to TODDLERSHARK, a Visual Basic (VB) based malware. The initial payload downloaded by the MSHTA utility was a VB script that was heavily obfuscated. The script includes randomly generated functions and variable names, as well as substantial amounts of hexadecimal encoded code and junk code. Each time the payload is downloaded it results in changes to the function names, variable names, junk code, and hexadecimal content, ensuring that the file’s hash will differ with each download.
- Furthermore, the addition of varying numbers of lines of junk code, containing randomized strings, serves to further obfuscate the meaningful code within the malware. After de-obfuscation, the code was found to initiate the download and execution of the next stage, a URL contained within the lengthy hexadecimal string (along with additional junk code). This URL also varies with each download of the initial payload. it is probable that a web application on the command and control (C2) server generates a unique payload, including a unique URL for the second stage, each time it is called.
When decoded, the second stage download contained a set of functionalities made up of three parts:- Setting windows registry keys
- Capturing and exfiltrating system information
- Setting up a scheduled task
To set Windows Registry keys, the TODDLERSHARK runs a series of commands. These commands configure the VBAWarnings keys in Word and Excel to a value of “1” across Office 2010, Office 2013, and Office 2016. This setting of “1” implies that both untrusted and trusted macros can execute without prompting the user, disabling certain macro security features in those versions.
The largest set of functionality within TODDLERSHARK is its ability to capture and exfiltrate data. The stolen information includes details such as host and user information, network and security software data, as well as installed software and running processes. After collecting the data, the tool utilizes the built-in Windows command certutil to encode the gathered information into a Privacy Enhanced Mail (PEM) certificate, which it then exfiltrated to the C2 web application. Hiding exfiltrated data within PEM files is a technique also previously used by Kimsuky. Upon completing its exfiltration task, the code deletes the captured data and the certificate file.
The last component of the malware involves creating a scheduled task. A script is first written into an Alternate Data Stream (ADS) of a file located within the ProgramData directory. This script includes a URL, which the scheduled task will query every minute. Any response from the URL is forwarded for immediate execution. Similar to the previously mentioned URLs, this URL is uniquely generated for each time the initial payload is executed. After creating the script, the malware establishes a scheduled task set to run every minute.
Risk & Impact Assessment
The exploitation of CVE-2024-1708 and CVE-2024-1709 presents a considerable risk to organizations using ScreenConnect versions before 23.9.8. The number of threat actors exploiting these ScreenConnect vulnerabilities for initial access is growing. In this case a likely new variant of BABYSHARK, TODDLERSHARK, was deployed after successful exploitation. The functionality of the malware poses a significant risk to organizations. Furthermore, due to TODDLERSHARK’s polymorphic behavior and use of uniquely generated command and control (C2) URLs, this malware can be difficult to detect in some environments.
A cyberattack facilitated by this TODDLERSHARK malware could profoundly impact an organization, Financially, it could lead to substantial losses due to operational downtime, data recovery efforts, legal fees, and potential fines for compliance violations. The reputational damage could erode stakeholder trust, affecting customer relationships and leading to a loss of business. Furthermore, the theft or compromise of sensitive data could have long-term implications on competitive advantage, exposing the organization to further targeted attacks.
Source Material: Kroll, TODDLERSHARK: ScreenConnect Vulnerability Exploited to Deploy BABYSHARK Variant
Latest Additions to Data Leak Sites
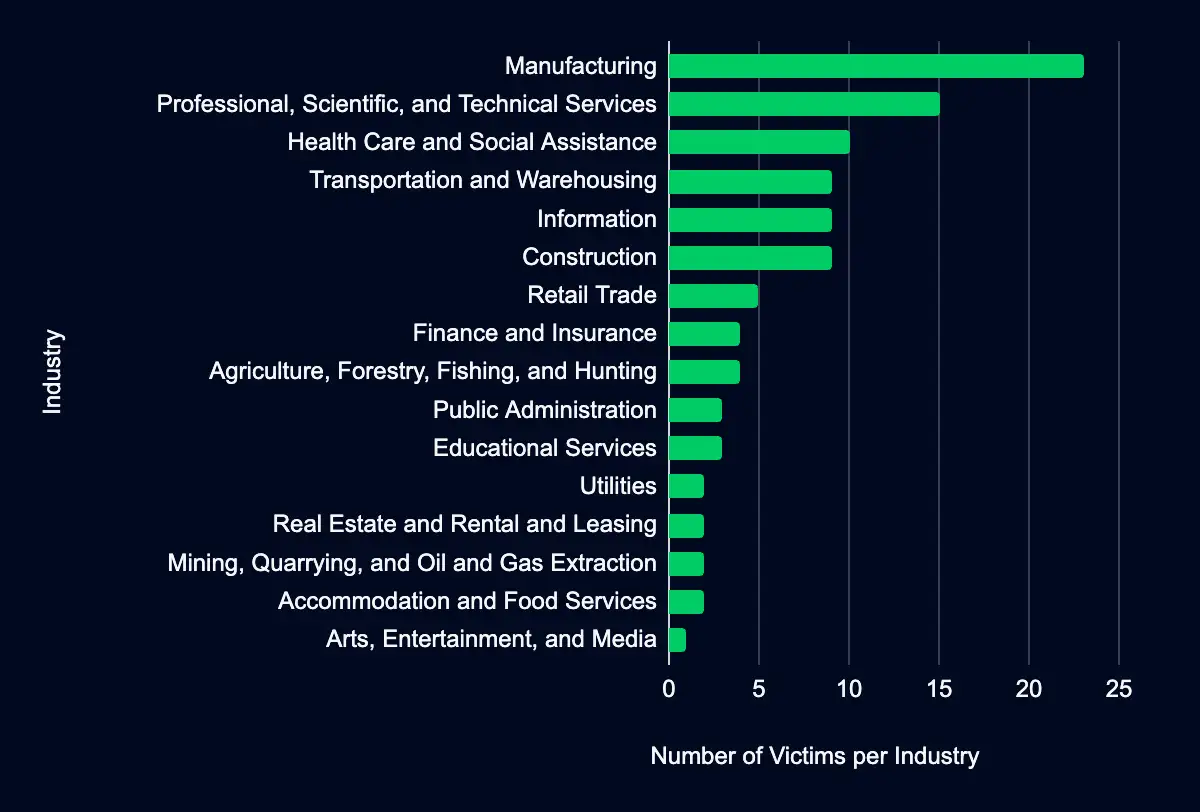
Manufacturing – Professional, Scientific, and Technical Services – Health Care and Social Assistance – Transportation and Warehousing – Information – Construction – Retail Trade
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. In the past week, 103 organizations have been listed as victims, with a marked concentration in the United States, accounting for 61% of the total victims. This geographic focus may indicate a higher targeting preference in this region due to the large base of potential victims or perhaps specific vulnerabilities associated with the region’s cyber infrastructure or prevalent business practices.
Regarding industry targeting, the data reveals a diverse range of sectors being affected, with Manufacturing leading the list at 22%, followed by Professional, Scientific, and Technical Services (15%), Health Care and Social Assistance (10%), Transportation and Warehousing, Information, Construction, and Retail Trade (9%), and Retail Trade (5%). This spread across various industries suggests that the actors are not discriminating much regarding the sector, aiming for a wide range of targets. It could also reflect the opportunistic nature of these actors, who may target organizations perceived as more likely to pay a ransom, regardless of their industry. The significant impact on the Manufacturing sector could suggest a higher susceptibility or perhaps a higher likelihood of paying ransoms due to the critical nature of manufacturing operations and the high cost of downtime.
Another possibility is that many organizations fall under these sectors, providing a broad and diverse target base. The fact that industries like Health Care and Social Assistance are also significantly targeted underscores the critical impact of ransomware attacks on public services and the potential for these incidents to have far-reaching consequences beyond financial loss, including impacts on health and safety.
The focus on industries like Professional, Scientific, and Technical Services, Information, and Retail Trade indicates a range of motives and methods among threat actors, possibly reflecting the varying levels of cybersecurity maturity and the differing value of data organizations hold in these sectors. The data underscores the need for heightened cybersecurity vigilance and preparedness across all industries, particularly those identified as top targets.
Recent data highlights the activities of several prominent ransomware actors, with Lockbit, Play, ALPHV, Black Basta, 8base, and Medusa standing out due to the number of victims listed on their leak sites. Notably, Lockbit seems to be back in full operation, with 47 victims added to its leak site, confirming reports that they were attempting to relaunch its operations following an international law enforcement takedown operation.
Lockbit has emerged prominently, affecting 47 organizations and accounting for 46% of the victims listed. This group’s targeting strategy seems geographically focused, with a significant preference for the United States (60%) and a notable presence in Germany (15%). Industry-wise, Lockbit shows a broad targeting range but has a particular focus on Manufacturing (30%) and Professional, Scientific, and Technical Services (15%). The diversity in their targeting, including sectors like Retail Trade, Real Estate, and Construction, indicates a versatile and opportunistic approach, aiming at industries where they can likely cause significant disruption or extract valuable data.
Play, with 16 victims and 16% of the victims listed, predominantly targets the United States (69%), suggesting an operational focus or success rate within this region. The Manufacturing and Information sectors appear to be a significant target for Play, comprising 50% of its attacks. This could indicate a strategy of targeting organizations where operational downtime would cause a substantial impact, potentially resulting in higher ransom demands. Other targeted sectors include Construction and Agriculture, Forestry, Fishing, and Hunting, showcasing a varied interest likely driven by the perceived value of the data or potential for disruption.
ALPHV (Black Cat) listed 12 victims on their leak site, accounting for 12% of the total victims. Their focus, especially in the United States (63%), aligns with this country’s overall trend of being a top target of ransomware actors. Manufacturing is particularly affected, with 50% of their attacks targeting this industry, possibly due to its lower tolerance for operational downtime. Other sectors like Retail Trade and Information reflect their broader strategic interests in sectors with valuable data or critical operational uptime requirements.
Black Basta and 8base appear to operate more globally, with their activities spread across multiple countries but primarily targeting the United States. This global footprint might reflect a more scattered or opportunistic targeting approach or a sophisticated capability to engage diverse targets. Manufacturing again stands out as a primary industry of focus, suggesting a consistent pattern among threat actors recognizing the sector’s vulnerabilities.
Lastly, Medusa has a more limited impact than the others but still presents a significant threat, especially in the United States. Their targeting across Manufacturing, Professional, Scientific, and Technical Services, Retail Trade, and Information shows no specific industry preference, perhaps indicating a more opportunistic approach or a testing phase of their capabilities.
The analysis of these actors provides critical insight into their operational patterns and preferences, underscoring the need for targeted defensive strategies across the highlighted regions and industries. Understanding these patterns can help organizations prioritize cybersecurity initiatives, focusing on the most relevant threats and actors.
Our analysis strives to be comprehensive, utilizing the most current data available. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we may have omitted victims we could not verify. Additionally, victims are classified based on the NAICS industry classification system. While we only list one industry classification per victim, it’s possible that a victim could fall under multiple industries classification, which may inadvertently skew results.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds 6 CVEs to Known Exploited Vulnerabilities Catalog
Microsoft Streaming Service CVE-2023-29360 – Microsoft Windows CVE-2024-21338 – Google Android Pixel CVE-2023-21237 – Sunhillo SureLine CVE-2021-36380 – Apple iOS and iPadOS CVE-2024-23225 & CVE-2024-23296
Within the past week, CISA added six (6) CVEs to its Known Exploited Vulnerabilities catalog, impacting products from Microsoft, Google, Sunhillo, and Apple. Threat actors can exploit these vulnerabilities to perform actions such as privilege escalation, information disclosure, and denial of service. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action between 21 March and 27 March 2024.
Microsoft Streaming Service CVE-2023-29360 targets Microsoft Streaming Service platforms, commonly used in various enterprise environments. With a critical impact, this vulnerability allows a local threat actor to gain SYSTEM privileges, signifying a high risk level, enabling privilege escalation. Notably, this vulnerability requires local access, thus limiting its exploitation to attackers who have already penetrated the network or system. CISA has set a mitigation due date of 21 March 2024. At this time, it is unknown if this vulnerability has been used in ransomware attacks.
Microsoft Windows CVE-2024-21338 affects the Windows Kernel and poses a significant threat due to its potential for privilege escalation through an exposed IOCTL in appid.sys. This specific vulnerability emphasizes the need for stringent access controls and monitoring of system calls to prevent exploitation. CISA has set a mitigation due date of 25 March 2024. At this time, it is unknown if this vulnerability has been used in ransomware attacks.
Google Android Pixel CVE-2023-21237 involves a misleading or insufficient UI in the Android Pixel’s Framework component, which could allow a local threat actor to disclose sensitive information. This vulnerability highlights the importance of UI integrity and the potential for information leakage even in seemingly secure user environments. CISA has set a mitigation due date of 26 March 2024. At this time, it is unknown if this vulnerability has been used in ransomware attacks.
Sunhillo SureLine CVE-2021-36380 features an OS command injection vulnerability that could lead to denial-of-service or unauthorized persistence on the network. Given its network-based attack vector, this vulnerability underscores the critical nature of validating external inputs and securing network interfaces. CISA has set a mitigation due date of 26 March 2024. At this time, it is unknown if this vulnerability has been used in ransomware attacks.
Apple iOS and iPadOS CVE-2024-23225 & CVE-2024-23296 both involve memory corruption vulnerabilities in the kernel and RTKit, respectively, allowing for kernel memory protections bypass. These vulnerabilities point to the sophisticated nature of attacks that can target even the most secure components of an operating system, highlighting the need for continuous security assessments and updates. CISA has set a mitigation due date of 27 March 2024. At this time, it is unknown if this vulnerability has been used in ransomware attacks.
The detailed analysis of these vulnerabilities demonstrates varied attack vectors and impacts, reinforcing the necessity for a multi-layered security approach. Organizations are advised to adhere to CISA’s mitigation timelines and remain vigilant in monitoring their security posture to counter these and future vulnerabilities effectively.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share