Threat Actors Exploit ASP.NET Machine Keys, Credential-Stuffing Attacks Target Mobile Apps, Ransomware Trends Evolve, and CISA Adds New Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Threat Actor Leverages Public ASP.NET Machine Keys for Persistent Access in IIS Environments
- Persistent Credential-Stuffing Attack Targets Mobile App
- Ransomware and Data Extortion Trends (Feb. 3 – 9)
- Exploited Vulnerabilities in Linux, Sophos, Microsoft, Audinate, 7-Zip, Trimble, Zyxel, Apple, and Mitel Added to CISA’s Catalog
Threat Actor Leverages Public ASP.NET Machine Keys for Persistent Access in IIS Environments
The Rundown
In December 2024, an unattributed threat actor leveraged a publicly accessible ASP.NET machine key to conduct a ViewState code injection attack. The malicious ViewState payload reflectively loaded a Godzilla post-exploitation framework DLL, followed by additional plugin modules.
During their investigation, Microsoft identified over 3,000 publicly disclosed ASP.NET machine keys. Their availability poses a significant risk, as they can be found in various code repositories and may have been incorporated into development code without any modifications.
- Developers may incorporate machine keys from publicly accessible resources, such as code documentation and repositories.
- If threat actors obtain these keys, they can create a malicious ViewState and send it to the target website via a POST request.
Source Material: Microsoft
Persistent Credential-Stuffing Attack Targets Mobile App
The Rundown
A four-day credential-stuffing attack targeted a major US-based Administrative and Support Services company’s mobile application, resulting in over 558,000 login attempts.
This incident underscores the persistent threat of credential-stuffing attacks on mobile platforms, highlighting the need for robust security measures to protect user accounts. While this particular attack targeted an Administrative and Support Services company, the tactics and techniques could be used to target any organization.
Between December 27 and 30, 2024, attackers executed a credential-stuffing attack against the on-demand staffing company’s mobile app login endpoint, peaking at 14,400 attempts per hour. The attack comprised two waves: an initial test phase and a more extensive assault. Attackers employed proxies, including data centers and low-quality free proxies from developing countries, to distribute the attack across 18,287 IP addresses, circumventing simple IP-based rate-limiting.
They mimicked legitimate mobile app behavior by forging HTTP headers and using consistent device fingerprints, likely extracted and replayed from valid login payloads. Despite these tactics, the attack was mitigated through a multi-layered detection approach, including replay attack detection and analysis of anomalous behavior patterns.
Credential stuffing is an automated attack where threat actors use previously compromised username-password pairs to gain unauthorized access to user accounts. Attackers typically source these credentials from past data breaches and test them at scale against login endpoints, exploiting users’ tendency to reuse passwords across multiple services.
These attacks leverage botnets, proxy networks, and tools that mimic legitimate user behavior to evade detection. Because credential stuffing relies on valid stolen credentials, it is highly effective if multi-factor authentication (MFA) and anomaly detection measures are not in place.
Source Material: Castle
Ransomware and Data Extortion Trends (Feb. 3 – 9)
The Rundown
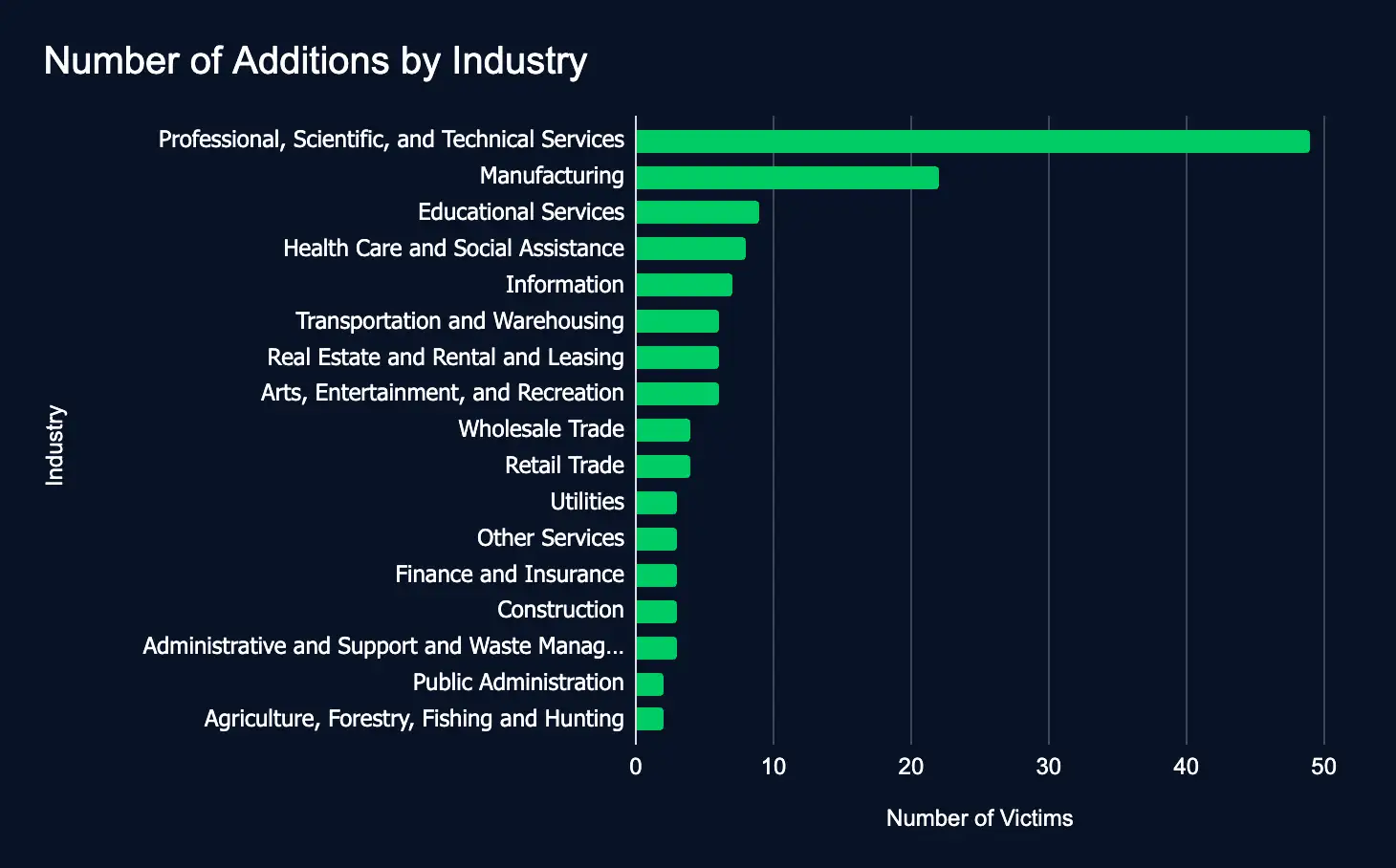
Between February 3 and 9, 140 organizations across 17 industries were listed on 24 ransomware and data extortion leak sites.
The 35-listing drop from last week’s 175 highlights the unpredictable nature of ransomware activity. It’s almost certainly not a trend that will continue in the future. Therefore, with new additions listing organizations in nearly all industries, organizations must strengthen cybersecurity measures to bolster cyber resilience.
Professional, Scientific, and Technical Services, Manufacturing, and Educational Services were the most listed industries. The top countries were the United States, Canada, Sweden, and Germany. The top leak sites were Akira, Ransomhub, Fog, and Qilin.
Exploited Vulnerabilities in Linux, Sophos, Microsoft, Audinate, 7-Zip, Trimble, Zyxel, Apple, and Mitel Added to CISA’s Catalog
The Rundown
Between February 5 and 12, 13 vulnerabilities affecting Linux, Sophos, Microsoft, Audinate, 7-Zip, Trimble, Zyxel, Apple, and Mitel products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share