SocGholish Backdoor Powers Ransomware Attacks, Email Bombing and Teams Threats Persist, 167 Firms Listed on Leak Sites, and CISA Flags Aviatrix Vulnerability
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
SocGholish Backdoor, Allowing Remote Access and Proxying, Used in Ransomware Attack
The Rundown
GuidePoint Security incident responders discovered that a RansomHub affiliate used a modified version of a previously reported Python-based backdoor. Evidence suggests that the backdoor is deployed in SocGholish (FakeUpdate) campaigns. The script functions as a proxy and leverages SOCKS5-like tunneling, allowing attackers to hide their infrastructure and mask the malicious traffic’s source, potentially evading detection. With the access gained from the backdoor, the RansomHub affiliate deployed the encryptors across the victim environment.
These findings underscore how attackers are evolving their tradecraft. The backdoor’s flexibility, combined with the potential for minimal detection from security tools, allows attackers to accelerate attacks, broaden their reach, and complicate defenders’ responses.
Source Material: GuidePoint Security
Ransomware Attackers Still Targeting Users via Email Bombing and Teams
The Rundown
Attackers are still targeting organizations using email bombing and Teams vishing to gain initial access. In one case, deploying ransomware.
Organizations using Teams need to be more vigilant. These tactics exploit trust and overwhelm defenses, increasing the risk of breaches.
Sophos’ recent blog post documents two activity clusters, STAC5777 and STAC5143, targeting Microsoft Office 365 (now known as Microsoft 365 Copilot) via email bombing and Teams-based vishing, using actor-controlled Microsoft tenants, various malware delivery methods, and tools. Both clusters take advantage of a default Microsoft Teams configuration that allows external users to initiate chats or meetings with internal users. Sophos has observed these tactics used in 15 incidents in the past three months, with half occurring in the last two weeks.
Source Material: Sophos
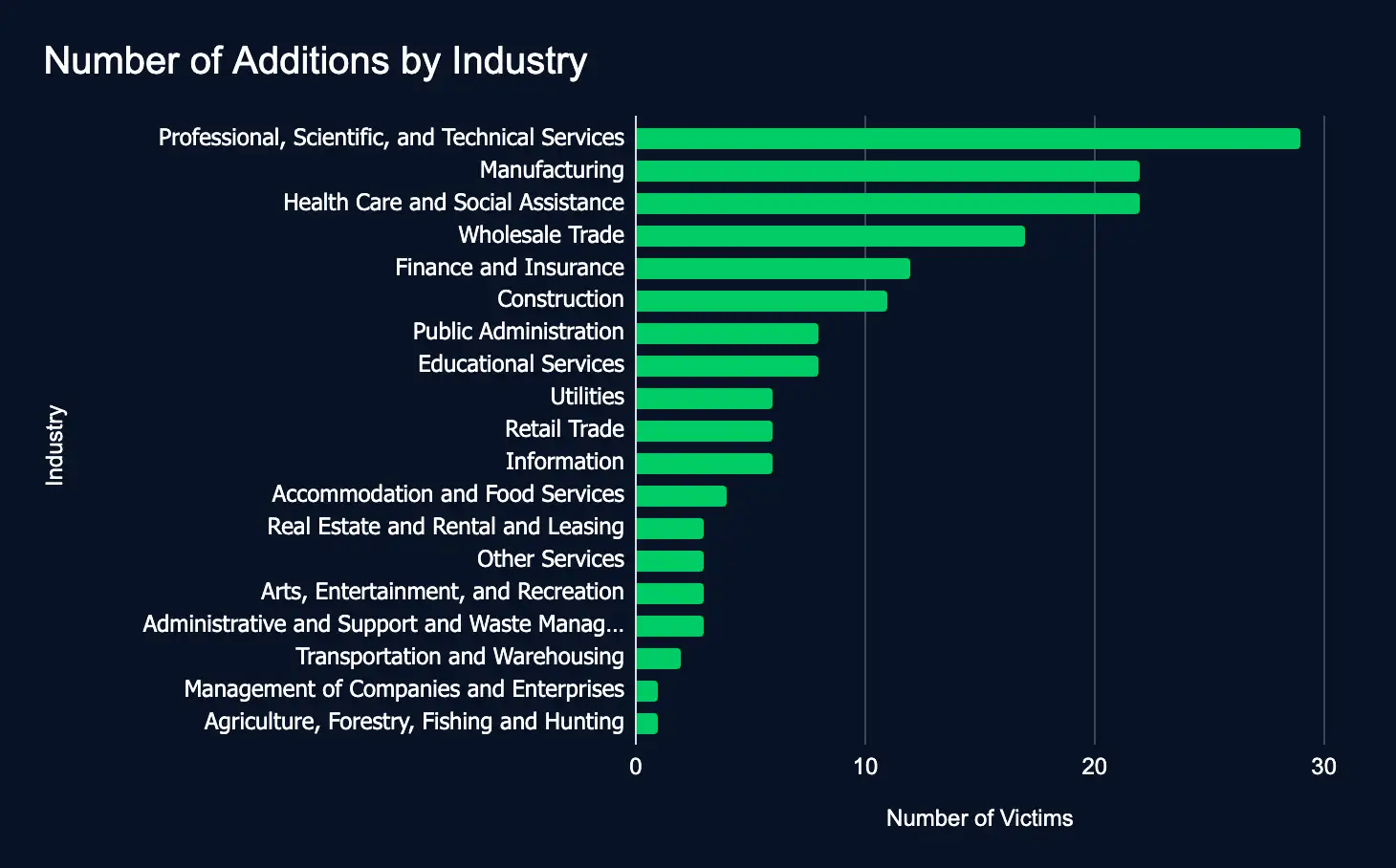
Leak Sites: 167 Firms Listed, Professional Services Tops the List
The Rundown
Between January 13 and 19, 167 organizations across 19 industries were listed on 22 ransomware and data extortion leak sites. The top sectors were Professional, Scientific, and Technical Services, Manufacturing, Health Care and Social Assistance, and Wholesale Trade. The top regions were the United States, India, and Brazil. The top leak sites were KillSecurity, Lynx, and INC Ransom.
The increase in new additions, 64 above the previous week, underscores the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
In addition to a detailed list of leak site additions to help identify potential data exposure from third-party breaches, this intelligence aids organizations in staying informed about the most recent ransomware and data leak threat landscape.
CISA Adds Aviatrix Vulnerability to Exploited List
The Rundown
Between January 16 and 22, one Aviatrix vulnerability (CVE-2024-50603) was added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, this vulnerability could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share