Google Domain Abuse and PLAYFULGHOST Threats Unveiled as CISA Adds Oracle and Mitel Vulnerabilities, and Professional Services Tops Data Leak Sites
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Exploiting Trust: Google Domain Abuse via Malicious JavaScript for Data Theft
The Rundown
Source Defense has uncovered that attackers are compromising legitimate domains to inject a script that uses trusted Google domains to execute malicious code.
This discovery highlights cybercriminals’ evolving strategies. They increasingly leverage reputable platforms to bypass security measures, complicating detection and mitigation efforts.
The attack begins with the injection of malicious JavaScript into legitimate websites, often through direct compromise or exploitation of third-party services, which send requests to trusted Google domains. By embedding the malicious code into Google’s response using a callback parameter, the browser executes the code automatically, enabling additional attacks. Source Defense has observed that this technique has been used to inject fake payment forms to steal credit card information.
By routing requests through legitimate Google domains, the method blends malicious actions with regular traffic, making it challenging to identify. The use of domain reputation and dynamic execution marks a significant evolution in attack tactics, emphasizing the need for updated security protocols and heightened vigilance. Defenders are advised to monitor specific suspicious requests to detect and prevent such exploits.
Source Material: Source Defense
Decoding PLAYFULGHOST: Attack Chain and Mitigation and Detection Strategies
The Rundown
Google’s recent blog post, “Finding Malware: Unveiling PLAYFULGHOST with Google Security Operations,” examines the PLAYFULGHOST backdoor malware. PLAYFULGHOST poses significant risks due to its advanced surveillance capabilities, deceptive distribution methods, and ability to persist undetected, enabling attackers to conduct extensive espionage and data theft.
PLAYFULGHOST shares functionalities with Gh0st RAT, a remote administration tool whose source code was publicly released in 2008, leading to numerous variants. It distinguishes itself through distinct traffic patterns and encryption, supporting commands such as keylogging, screen capture, audio capture, remote shell, and file transfer/execution. The malware is distributed via phishing attacks, using themes like “code of conduct” to trick users into downloading it, and through SEO poisoning, bundling it with popular applications like LetsVPN to appear as legitimate downloads.
The significance of PLAYFULGHOST lies in its ability to perform keylogging, capture screenshots and audio, execute remote commands, and transfer files, enabling attackers to conduct extensive surveillance and data exfiltration. Phishing and SEO poisoning for distribution increases the likelihood of successful infections, making implementing robust security measures and user awareness training imperative to mitigate such threats.
PLAYFULGHOST employs a multi-stage attack chain, beginning with delivering malicious executables through phishing emails or trojanized software installers. Upon execution, these executables download and execute the PLAYFULGHOST payload from a remote server. The malware maintains persistence via registry Run keys, scheduled tasks, startup folders, and Windows services. Its execution involves a legitimate executable vulnerable to DLL search order hijacking, a malicious launcher DLL, and a file containing the PLAYFULGHOST payload, allowing it to evade detection by loading the backdoor into memory.
Notably, PLAYFULGHOST has been observed accompanying other malware and utilities, such as BOOSTWAVE, shellcode acting as an in-memory dropper; TERMINATOR, an open-source tool terminating security processes; QAssist.sys, a rootkit capable of hiding registry entries, files, and processes; and CHROMEUSERINFO.dll, a DLL used to retrieve Google Chrome user data, including stored login credentials. These accompaniments enhance PLAYFULGHOST’s functionality and stealth, making it a more formidable threat requiring comprehensive detection and mitigation strategies.
Source Material: Google Cloud Security
Leak Sites: 50 Firms Listed, Professional Services Tops the List
The Rundown
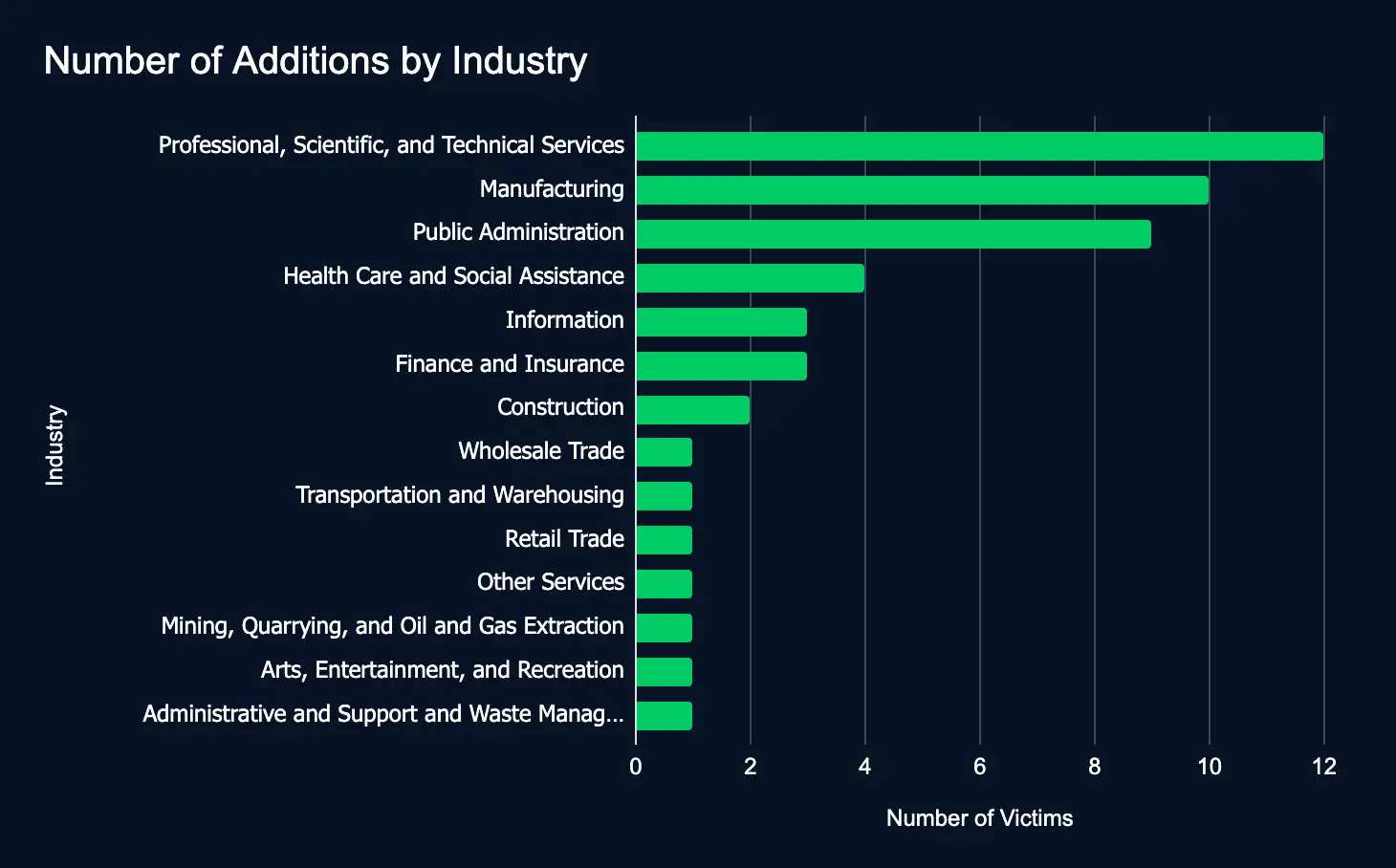
From December 30 to January 5, 17 ransomware and data extortion leak sites added 50 organizations from 14 industries. The top sectors were Professional Services, Manufacturing, and Public Administration. The top regions were the United States, India, and France. The top leak sites were Funksec, 8base, and Play. These new additions underscore the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
CISA Adds Oracle and Mitel Vulnerabilities to Exploited List
The Rundown
Between January 2 and 8, three vulnerabilities affecting Oracle (CVE-2020-2883) and Mitel (CVE-2024-55550 and CVE-2024-41713) products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share