Ivanti Cloud Service Vulnerability, Ransomware Affiliates Stick to Proven Tactics, 73 Firms Hit, and CISA Flags JQuery, SonicWall, and Apple Flaws
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Vulnerabilities in Ivanti Cloud Service Applications Chained For Remote Code Execution, Credential Theft, and Webshell Deployment
- The Tried-and-True Ransomware Playbook: How Affiliates Use Proven Tools to Breach, Persist, and Exfiltrate
- Leak Sites: 73 Firms Listed, Manufacturing Tops the List
- CISA Adds JQuery, SonicWall, and Apple Vulnerabilities to Exploited List
Vulnerabilities in Ivanti Cloud Service Applications Chained for Remote Code Execution, Credential Theft, and Webshell Deployment
The Rundown
In September 2024, unknown attackers exploited Ivanti Cloud Service Appliances (CSA), chaining various vulnerabilities with CVE-2024-8963.
Even though exploitation occurred in September 2024, the vulnerabilities are still relevant, and organizations using affected versions of Ivanti CSA are still at risk. The Advisory further warns, “Credentials and sensitive data stored within the affected Ivanti appliances should be considered compromised.”
The chaining of these vulnerabilities led to unauthorized access, remote code execution, credential theft, and webshell deployment. All four vulnerabilities affect Ivanti CSA version 4.6x versions before 519, and two of the vulnerabilities (CVE-2024-9379 and CVE-2024-9380) affect CSA versions 5.0.1 and below; according to Ivanti, these CVEs have not been exploited in version 5.0. Ivanti CSA 4.6 has reached its End-of-Life (EOL) and no longer receives patches or third-party libraries.
Source Material: CISA
The Tried-and-True Ransomware Playbook: How Affiliates Use Proven Tools to Breach, Persist, and Exfiltrate
The Rundown
Ransomware affiliates still use tried-and-true methods and tools, such as Cobalt Strike, proxy malware, and Rclone, to exfiltrate data and deploy ransomware.
Despite familiarity with the tools and techniques, this attack exemplifies how threat actors can execute highly impactful attacks with tried-and-true tactics and methods. It highlights the importance of vigilance against even the most well-known threats, emphasizing the need for comprehensive detection and response strategies.
The attack began with the download and execution of a Cobalt Strike beacon that impersonated a Windows utility. The attacker established several persistent mechanisms within the environment throughout the intrusion, utilizing scheduled tasks, Run keys, GhostSOCKS and SystemBC proxies, and Cobalt Strike. The threat actor used Rclone to exfiltrate data from the environment. Initially, they attempted to use FTP transfers, which failed, so they switched to MEGA[.]io. A day later, they successfully carried out a second FTP exfiltration. On the 11th day of the intrusion, LockBit ransomware was deployed throughout the environment.
Source Material: The DFIR Report
Leak Sites: 73 Firms Listed, Manufacturing Tops the List
The Rundown
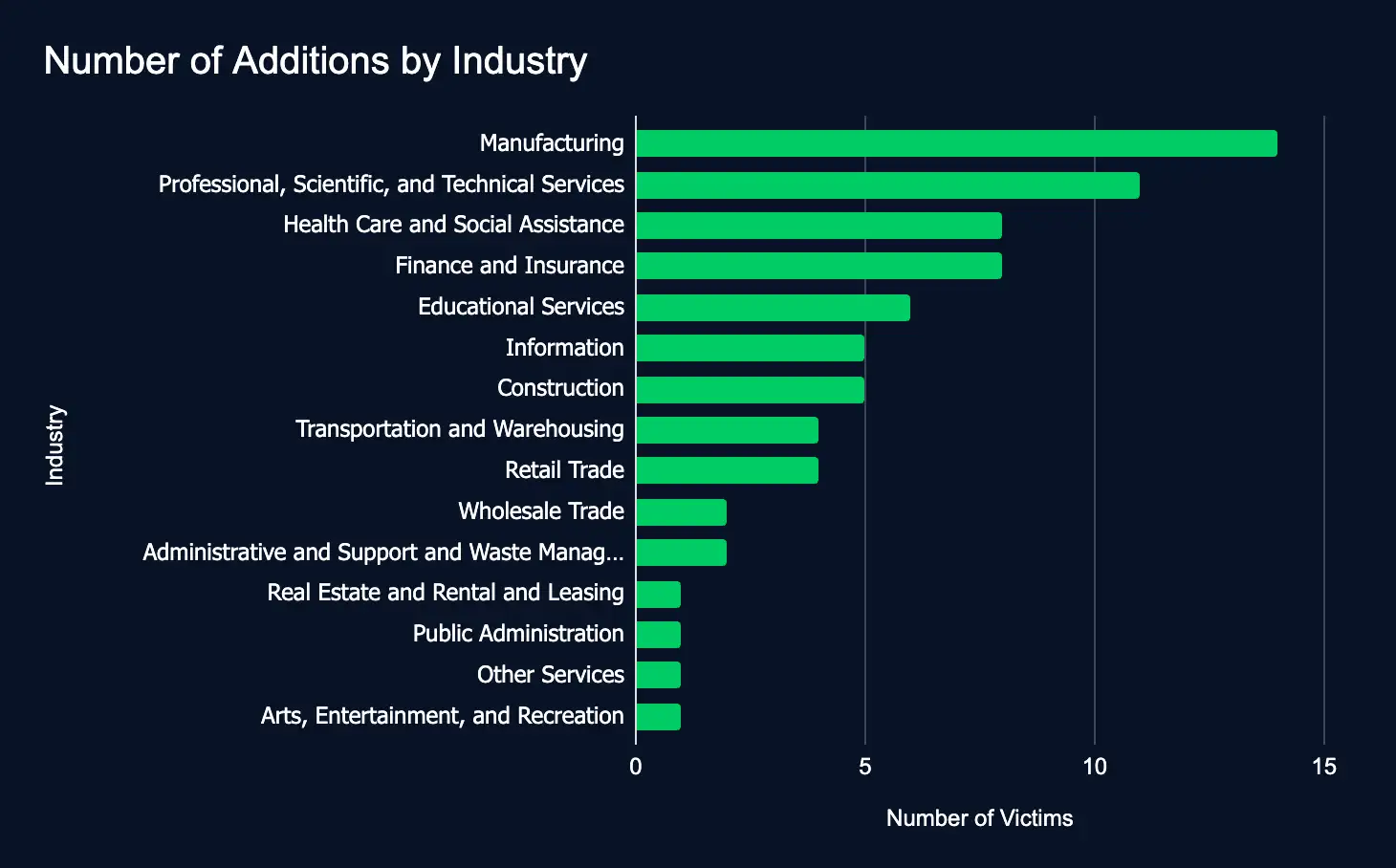
Between January 20 and 27, 73 organizations across 15 industries were listed on 24 ransomware and data extortion leak sites.
The drop from 167 organizations the previous week to 73 this week highlights the unpredictable nature of ransomware activity. It’s not likely a trend that will continue in the future. Therefore, with new additions listing organizations in nearly all industries, organizations must strengthen cybersecurity measures to bolster cyber resilience.
The most listed industries were Manufacturing, Professional Services, Health Care and Social Assistance, and Finance and Insurance. The top regions were the United States, India, and the United Kingdom. The top leak sites were Ransomhub, Space Bears, Medusa, Killsecurity, and Akira.
CISA Adds JQuery, SonicWall, and Apple Vulnerabilities to Exploited List
The Rundown
Between January 23 and 29, three vulnerabilities affecting JQuery (CVE-2020-11023), SonicWall (CVE-2025-23006), and multiple Apple (CVE-2025-24085) products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share