GitHub Abuse Delivers Lumma Stealer, XE Group Exploits VeraCore for Persistent Access, CISA Flags New Vulnerabilities, and Rising Ransomware and Extortion Trends Persist
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Lumma Stealer and SectopRAT Delivered via GitHub Release Management
- XE Group’s Multi-Year Exploitation of VeraCore: Persistent Access Through Webshells and Stolen Credentials
- Ransomware and Data Extortion Trends (January 27 – February 2)
- Exploited Vulnerabilities in Paessler, Microsoft, and Apache Added to CISA’s Catalog – Immediate Mitigation Recommended
Lumma Stealer and SectopRAT Delivered via GitHub Release Management
The Rundown
A malware campaign used GitHub’s release management features to distribute Lumma Stealer and other malware, evading detection by leveraging trusted platforms.
This campaign demonstrates how seemingly legitimate services can be abused to distribute malware, making it more difficult for users to identify and avoid threats.
The infection chain began with users clicking on GitHub links to download files. The downloaded files were initially signed by legitimate entities but were later revoked. Upon execution, the malware generated multiple files, including 7zip, to extract further components. It then connected to external command and control servers to send stolen information.
The malware also dropped additional tools and malware, such as SectopRAT, Vidar, and Cobeacon, creating multiple directories and staging data for further malicious activities. The malware also added files to the startup folder and created scheduled tasks for persistence.
Some tactics, techniques, and procedures (TTPs) used in this campaign overlap with those of the Stargazer Goblin group. The analysis revealed consistent URL patterns and the use of compromised websites for redirection to GitHub-hosted malicious payloads. The compromised sites were often legitimate websites that had been active for years.
The attackers inserted image and PHP script files into these sites, managing redirection and user interactions. The GitHub accounts used in the campaign were newly created and had minimal activity beyond hosting malicious files.
Source Material: Trend Micro
XE Group’s Multi-Year Exploitation of VeraCore: Persistent Access Through Webshells and Stolen Credentials
The Rundown
XE Group executed a multi-year attack from 2020 to 2024, exploiting zero-day vulnerabilities in VeraCore to deploy ASPX webshells and exfiltrating sensitive configuration files.
The XE Group’s prolonged exploitation of VeraCore vulnerabilities demonstrates the risks of persistent cyber intrusions. Their ability to return years later using stolen credentials underscores the dangers of poor credential hygiene, unpatched vulnerabilities, and the need for proactive security measures.
In the multi-year attack against an unidentified victim, XE Group compromised the organization in 2020, targeting an IIS server hosting the VeraCore application, exploiting previously undocumented vulnerabilities, now tracked as CVE-2024-57968 and CVE-2025-25181, to perform SQL injection and dropping webshells.
They returned in 2023 and interacted with a new webshell that was likely dropped by a webshell dropped in 2020. Then, in 2024, they used the webshell dropped in 2023 to execute a batch script and uploaded a variant of the webshell they dropped in 2023.
Source Material: Intezer
Ransomware and Data Extortion Trends (January 27 – February 2)
The Rundown
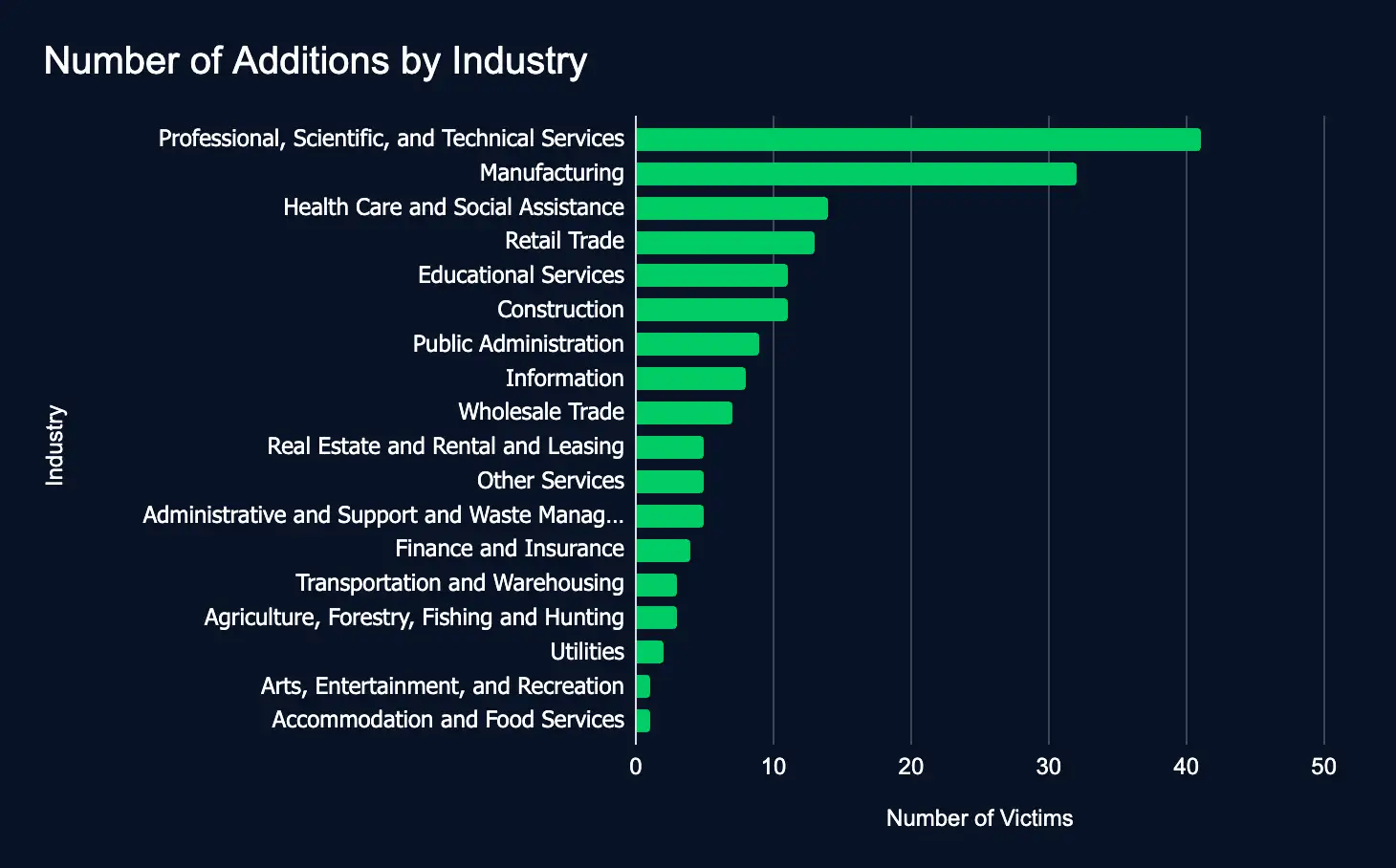
Between January 27 and February 2, 175 organizations across 18 industries were listed on 29 ransomware and data extortion leak sites.
The increase from 73 organizations the previous week to 175 this week highlights the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
Professional Services, Manufacturing, and Health Care and Social Assistance were the most listed industries. The United States, the United Kingdom, and Canada were the top countries. The top leak sites were Akira, Play, Medusa, INC Ransom, and Funksec.
Exploited Vulnerabilities in Paessler, Microsoft, and Apache Added to CISA’s Catalog – Immediate Mitigation Recommended
The Rundown
Between January 30 and February 5, four vulnerabilities affecting Paessler (CVE-2018-19410 and CVE-2018-9276), Microsoft (CVE-2024-29059), and Apache (CVE-2024-45195) products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share