Ivanti Zero-Day CVE-2025-0282 Exploited as Macro Malware and Data Leaks Impact 103 Firms—CISA Flags Critical Vulnerabilities in Latest Update
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Ivanti Connect Secure Vulnerability CVE-2025-0282 Exploited: What You Need to Know
- Macros Still Abused: Macro Creates Malicious Doc to Deliver Malware
- Leak Sites: 103 Firms Listed, Professional Services Tops the List
- CISA Adds Ivanti, Qlik, BeyondTrust, Microsoft, and Fortinet Vulnerabilities to Exploited List
Ivanti Connect Secure Vulnerability CVE-2025-0282 Exploited: What You Need to Know
The Rundown
Threat actors exploited a zero-day vulnerability in Ivanti Connect Secure to deploy malware, harvest credentials, and exfiltrate sensitive data. If successfully exploited, the vulnerability, now tracked as CVE-2025-0282, allows unauthenticated remote code execution, potentially compromising downstream networks. This is a developing campaign that Mandiant and Ivanti are analyzing. As additional details are identified, Mandiant’s blog post will be updated.
The recent exploitation of CVE-2025-0282 in Ivanti Connect Secure appliances as a zero-day is a significant security concern for organizations. It also represents the risks posed by cyber threats targeting critical infrastructure components like VPN appliances. This exploitation demonstrates that the vulnerability is a viable entry point for attackers, increasing the likelihood that other threat actors may exploit it to gain unauthorized access. The involvement of sophisticated threat actors deploying advanced and unobserved malware underscores the necessity for heightened vigilance and proactive security measures. Organizations must swiftly mitigate these risks to protect their networks, data, and operational integrity.
Mandiant observed exploitation targeting multiple Connect Secure appliances from various organizations. On at least one appliance, threat actors deployed malware from the SPAWN malware family, which includes the SPAWNANT installer, SPAWNMOLE tunneler, the SPAWNSNAIL SSH backdoor, and the SPAWNSLOTH log tampering utility. In addition to the SPAWN malware family, previously unobserved malware, the PHASEJAM dropper, and the DRYHOOK credential harvester have been found on compromised appliances.
Mandiant attributed the exploitation to the China-nexus intrusion set UNC5337, a cluster of activity assessed with moderate confidence to be part of UNC5221. However, multiple actors may be responsible for creating and deploying these various malware families. UNC5337 is the only cluster known to have deployed SPAWN on Ivanti Connect Secure appliances.
They exploited Connect Secure in January 2024 when they exploited CVE-2024-21887. UNC5221 is a suspected China-nexus espionage-focused intrusion set that exploited CVE-2023-46805 and CVE-2024-21887 in Ivanti Connect Secure VPN and Ivanti Policy Security appliances as early as December 2023.
Source Material: Mandiant
Macros Still Abused: Macro Creates Malicious Doc to Deliver Malware
The Rundown
A recent Sekoia blog post details how attackers are using a unique technique to deliver malware. The method involves a macro-enabled Word document that, when activated, creates a malicious macro-enabled document that drops and executes a malicious HTML application file with embedded malware.
Using this technique to deliver malware poses a considerable security concern for organizations. The identification of documents employing this technique demonstrates that it can serve as a viable means to deliver malware, increasing the likelihood that cybercriminals will adopt it. Cybercriminals can easily adopt this technique to deploy malware for various financially motivated objectives, such as credential and data theft, and/or facilitate ransomware attacks. These factors underscore the necessity for heightened vigilance and proactive security measures. Organizations must swiftly mitigate these risks to protect their networks, data, and operational integrity.
As described in Sekoia’s blog post, this technique is known to have been used in documents masquerading as official communications from Republic of Kazakhstan government entities. The malware delivered by these documents was identified as the backdoors HATVIBE and CHERRYSPY. Based on the contents of the documents, Sekoia assessed that it’s possible that these documents were created by the Russian-nexus intrusion set UAC-0063, which overlaps with APT28.
These Word documents were likely delivered to targets as attachments to phishing emails. However, attackers are not limited to this vector. They can host the document through a third party, such as file-sharing services or compromised websites. Then, sharing a link to the document through forums, social media and messaging apps, drive-by downloads, or malvertising.
Source Material: Sekoia
Leak Sites: 103 Firms Listed, Professional Services Tops the List
The Rundown
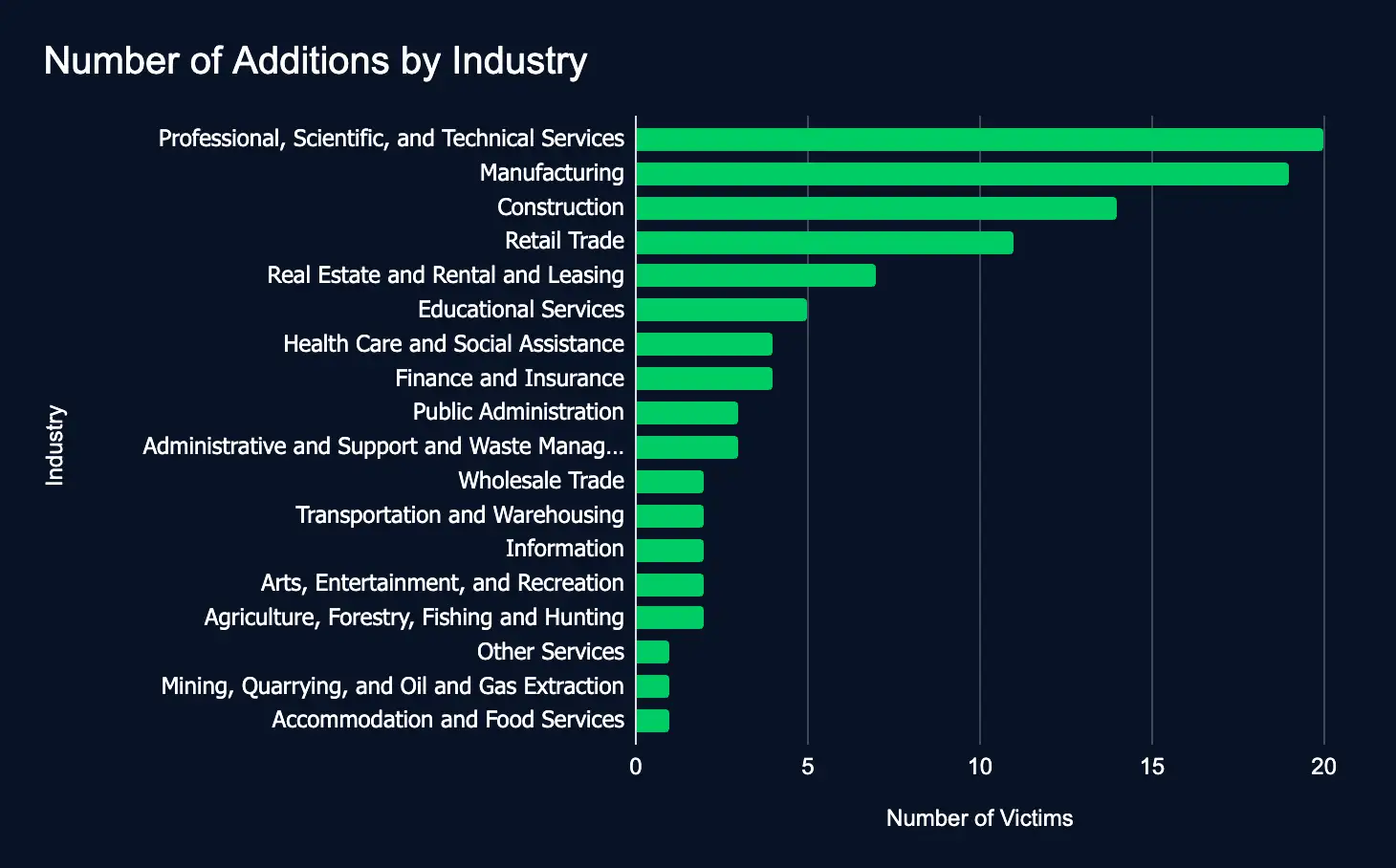
From January 6 to January 12, 23 ransomware and data extortion leak sites added 103 organizations from 18 industries. The top sectors were Professional Services, Manufacturing, and Construction. The top regions were the United States, Canada, the United Kingdom, and Thailand. The top leak sites were Akira, Ransomhub, Medusalocker, and 8base. The increase in new additions, 53 above the previous week, underscores the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
CISA Adds Ivanti, Qlik, BeyondTrust, Microsoft, and Fortinet Vulnerabilities to Exploited List
The Rundown
Between January 8 and 15, seven vulnerabilities affecting Ivanti (CVE-2025-0282), Qlik (CVE-2023-48365), BeyondTrust (CVE-2024-12686), Microsoft (CVE-2025-21333, CVE-2025-21334, & CVE-2025-21335), and Fortinet (CVE-2024-55591) products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share