APT40’s Espionage Techniques, FIN7’s Vast Network Exposed, CRYSTALRAY’s Credential Theft and Cryptomining, New APT41-Linked Malware, Snowflake Data Theft Impact, and Ransomware Leak Sites
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Inside APT40: Techniques of China’s Cyber Espionage Group
- FIN7 Resurfaces: Over 4,000 Domains and a Front Company Uncovered
- Exposing CRYSTALRAY’s Credential Theft and Cryptomining Operations
- Zscaler Discovers New Malware with Possible Ties to APT41
- Who Has Been Impacted by the Snowflake Data Theft Campaign? What We Know So Far
- Ransomware Leak Sites List 42 Organizations Amid Ongoing Decline
- Newly Exploited Vulnerabilities Added to CISAs Exploited Vulnerabilities Catalog: Adobe, SolarWinds, VMware, OSGeo
Inside APT40: Techniques of China’s Cyber Espionage Group
Threat Actor – Chinese Threat Actor – Vulnerability Exploitation – Valid Account Abuse – Data Exfiltration – Educational Services – Transportation and Warehouse – Manufacturing – Professional, Technical, and Scientific Services – Public Administration – Health Care and Social Assistance
The Rundown
On July 8, 2024, a multi-nation Cybersecurity Advisory revealed the evolving and sophisticated techniques of APT40, a Chinese state-sponsored hacking group, posing a significant global cybersecurity threat.
APT40’s advanced cyber attack methods and persistent exploitation of vulnerabilities in widely used software highlight an urgent need for enhanced defensive measures among cybersecurity professionals worldwide. Its success in exploiting vulnerabilities from 2017 to the present underscores the persistent threat it poses.
Source Material: CISA
FIN7 Resurfaces: Over 4,000 Domains and a Front Company Uncovered
Threat Actor – Phishing – Malicious Domains – Front Company – FIN7 – Finance and Insurance – Professional, Scientific, and Technical Services – Manufacturing – Information – Utilities – Retail Trade – Transportation and Warehousing – Accommodation and Food Services
The Rundown
Silent Push has uncovered over 4,000 FIN7 phishing-related domains impersonating numerous organizations, with almost 2,000 still active and a suspected cybersecurity front company, cybercloudsec[.]com, which is likely being used to facilitate FIN7 activity, in line with tactics.
Thought to have been eliminated by the DOJ, FIN7’s reemergence with new phishing domains and a fake cybersecurity front company is a significant development that necessitates heightened vigilance and robust cybersecurity measures to protect critical industries from their sophisticated attacks.
Source Material: Silent Push
Exposing CRYSTALRAY’s Credential Theft and Cryptomining Operations
Threat Actor – Vulnerability Exploitation – Credential Theft – Cryptomining – Open-source Tools – CRYSTALRAY – All Industries
The Rundown
Sysdig’s latest research exposes CRYSTALRAY’s extensive credential theft and cryptomining operations, primarily targeting the United States, highlighting their recent mass scanning, multi-vulnerability exploitation, and backdoors using open-source security tools.
CRYSTALRAY’s activities pose significant threats to various organizations by compromising sensitive data and infrastructure, showcasing the urgent need for enhanced defense mechanisms against sophisticated cybercriminal operations.
Source Material: Sysdig
Zscaler Discovers New Malware with Possible Ties to APT41
Threat Actor – Malware – Loader – Backdoor – APT41 – Earth Baku – DodgeBox – MoonWalk – StealthVector – Health Care and Social Assistance – Professional, Scientific, and Technical Services – Information
The Rundown
In April, Zscaler ThreatLabz discovered a new loader tracked as DodgeBox that resembles APT41/Earth Baku’s StealthVector loader and a new backdoor tracked as Moonwalk. Due to DodgeBox’s similarities with StealthVector and MoonWalk sharing commonalities with DodgeBox, Zscaler attributes these new malware families to APT41/Earth Baku with moderate confidence.
The discovery of DodgeBox and MoonWalk underscores the persistent and evolving threat from APT41, highlighting the increasing complexity of nation-state cyber threats and emphasizing the need for robust, adaptive security strategies and heightened vigilance to protect sensitive data against sophisticated malware tactics.
Source Material: Zscaler 1 and Zscaler 2
Who Has Been Impacted by the Snowflake Data Theft Campaign? What We Know So Far
Data Breach – Snowflake – Compromised Credentials – Data Exfiltration – All Industries
The Rundown
Mandiant and Snowflake have notified 165 potentially exposed organizations. Six companies confirmed data theft from their Snowflake instances, with four more suspected. Attackers used stolen credentials from infostealer infections to access and steal customer data, then extorted victims and attempted to sell the data on cybercriminal forums.
The Snowflake data theft and extortion campaign exposes critical cybersecurity weaknesses and risks associated with third-party cloud platforms and how stolen credentials can lead to significant data breaches, underscoring the need for robust authentication measures and regular credential updates.
The attacker, tracked as UNC5537 by Mandiant, used credentials obtained from multiple infostealer infections of non-Snowflake-owned systems to access organizations’ Snowflake instances. These credentials allowed UNC5537 attackers to access and steal customer data from the organization’s Snowflake instance. In some cases, the attackers extorted the victim and attempted to sell the stolen data on cybercriminal forums.
According to Mandiant, successful compromises were due to:
- Compromised accounts only needed a valid username and password, as multi-factor authentication was not enabled.
- Compromised credentials had not been rotated or updated, but they were still valid, in some cases years later.
- Impacted Snowflake customer instances did not restrict access to trusted locations, which could have been achieved through a network-allow list.
Ransomware Leak Sites List 42 Organizations Amid Ongoing Decline
Professional, Scientific, and Technical Services – Manufacturing – Utilities – Other Services – Health Care and Social Assistance – Real Estate and Rental and Leasing – Agriculture, Forestry, Fishing, and Hunting
The Rundown
Forty-two organizations were added to ransomware leak sites last week, continuing a downward cyberattack trend.
This snapshot of ransomware activity reveals which sectors and regions ransomware attackers most frequently targeted, providing cybersecurity professionals with crucial insights. With professional, scientific, and technical services bearing the brunt and the United States leading as the most affected country, this data underscores the persistent and evolving threat landscape.
By understanding the distribution and frequency of these attacks, cybersecurity teams can identify third-party, potential data exposure, and ransomware risks.
Industry Impact:
Organizations operating in the professional services, manufacturing, and utilities sectors were listed the most.
By the numbers:
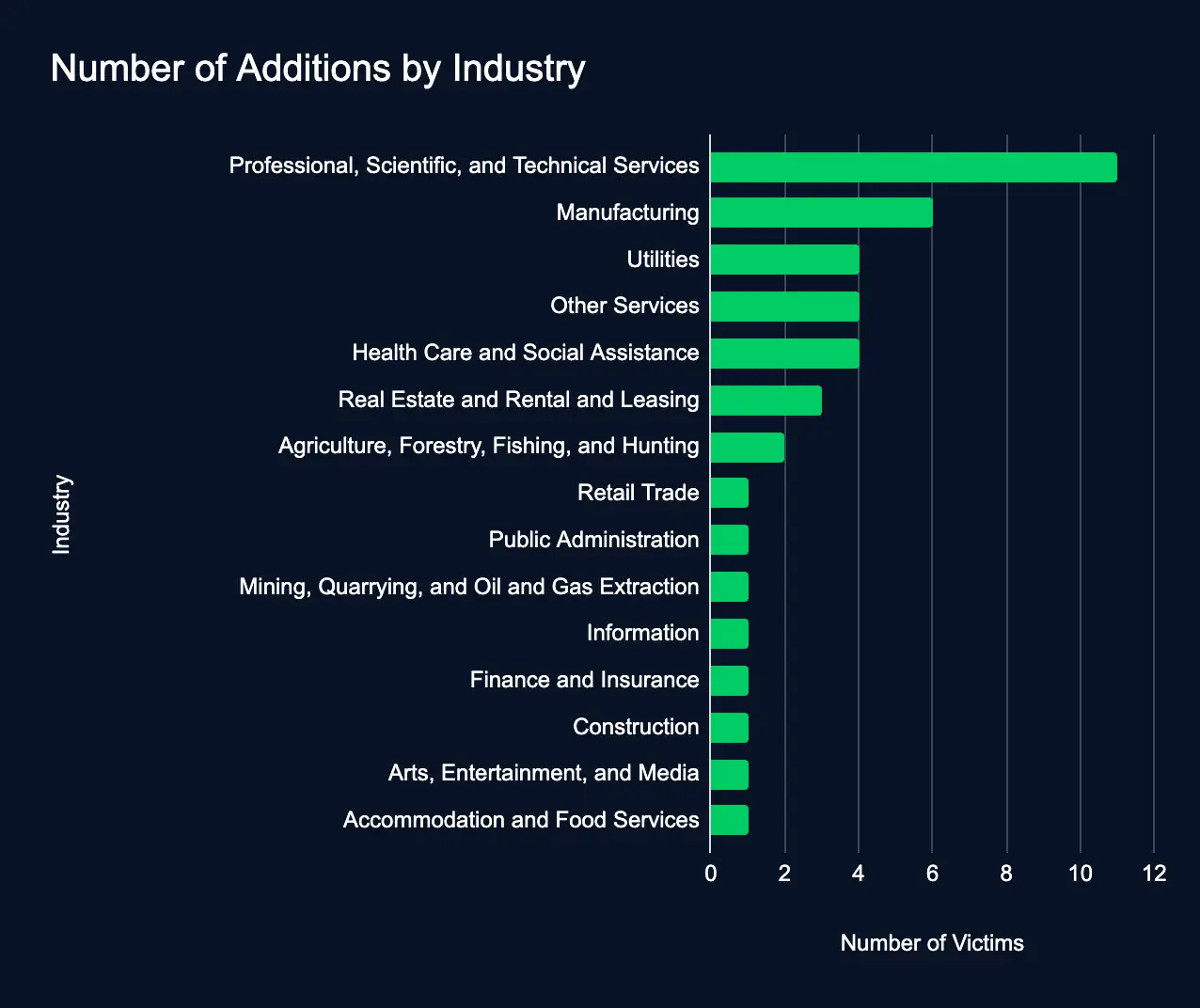
Geographic Distribution:
Organizations headquartered in the United States experienced the highest number of ransomware attacks.
Newly Exploited Vulnerabilities Added to CISAs Exploited Vulnerabilities Catalog: Adobe, SolarWinds, VMware, OSGeo
Adobe Commerce, Magento Open Source, and Commerce Webhooks Plugin CVE-2024-34102 – SolarWinds Serv-U CVE-2024-28995 – VMware vCenter Server CVE-2022-22948 – OSGeo GeoServer GeoTools CVE-2024-36401
The Rundown
The Cybersecurity and Infrastructure Security Agency (CISA) has added several high-risk vulnerabilities to its Known Exploited Vulnerabilities catalog, indicating that these flaws in Adobe Commerce, SolarWinds Serv-U, VMware vCenter, and OSGeo GeoServer have been actively exploited.
Exploitation of these vulnerabilities poses significant threats to systems running Adobe, SolarWinds, VMware, and OSGeo products. This highlights the urgent need for organizations to update their systems and apply necessary patches to protect against potential breaches and data loss.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share