Onyx Sleet Indictments, Black Basta’s Dangerous Tactics, ESXi Exploited in Ransomware Attacks, 100 New Ransomware Victims, and CISA Adds VMware, ServiceNow, Acronis Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- KnowBe4 Uncovers North Korean State-Sponsored Insider Threat
- Daggerfly’s Evolving Arsenal: New Backdoor and Possible Links to Macma
- Exposing Onyx Sleet: Indictments, TTPs, and Arsenal
- Inside Black Basta: UNC4393’s Swift and Dangerous Operations
- ESXi Vulnerability Exploited in Ransomware Attacks to Escalate Privileges
- 100 Organizations Hit by Ransomware in a Week, Manufacturing and Healthcare Most Affected
- CISA Adds Vulnerabilities in VMware, ServiceNow, and Acronis to Exploited Catalog
KnowBe4 Uncovers North Korean State-Sponsored Insider Threat
State-sponsored Insider Threat – Corporate Espionage – North Korea – Fake Hire Scam – All Industries
The Rundown
In a concerning yet ultimately foiled attempt at corporate espionage, KnowBe4 recently discovered that a newly hired software engineer was actually a North Korean agent attempting to compromise the company’s systems. This incident, outlined in a recent blog post by KnowBe4, highlights the sophisticated methods state-sponsored actors use to infiltrate organizations and siphon resources to fund illicit activities.
The incident highlights the growing sophistication of state-sponsored cybercriminal operations and the critical need for enhanced security protocols in the hiring process. If an organization as security-conscious as KnowBe4 can be targeted, it can happen to any organization. This case underscores the importance of vigilance and robust security practices in the face of increasingly sophisticated cyber threats. Organizations are urged to review and strengthen their own security protocols to guard against similar infiltration attempts.
Source Material: KnowBe4
Daggerfly’s Evolving Arsenal: New Backdoor and Possible Links to Macma
Threat Actor – Malware – Backdoor – Windows Backdoor – macOS Backdoor – Daggerfly – Nightdoor/Suzafk – Macma – All Industries
The Rundown
Daggerfly, an advanced persistent threat group, has upgraded its espionage arsenal to include new malware. The updated arsenal highlights the group’s capabilities and resources, including the ability to quickly update its tools when they are exposed.
The updated arsenal highlights Daggerfly’s growing prowess in cyber espionage, which poses significant risks to critical infrastructures and organizations globally. This underscores the urgent need for heightened cybersecurity measures to protect sensitive data and operations from these evolving cyber threats.
Source Material: Symantec
Exposing Onyx Sleet: Indictments, TTPs, and Arsenal
Threat Actor – North Korea Threat Actor – Vulnerability Exploitation – Malware – Remote Access Trojan – Onyx Sleet – Andariel – Health Care and Social Assistance – Utilities – Defense- Transportation and Warehousing
The Rundown
The DOJ has indicted a North Korean hacker linked to the cyber threat group Onyx Sleet, known for sophisticated malware attacks targeting defense and energy sectors. To bolster organizations’ defenses against Onyx Sleet, Microsoft published a blog post detailing Onyx Sleet’s attack chain, operational tradecraft, targets, and recent malware campaigns. The following is our coverage of these events.
Onyx Sleet is a persistent threat, and its ability to develop and use a variety of tools in its attack chain makes it a potent threat, particularly to targets of interest to North Korea, such as organizations in the defense, engineering, and energy sectors.
Source Material: Microsoft, CISA, and DoJ
Inside Black Basta: UNC4393’s Swift and Dangerous Operations
Ransomware – Threat Actor – Black Basta – UNC4393 – QAKBOT – Cobalt Strike – SystemBC – Remote Monitoring and Management (RMM) – RCLONE – All Industries
The Rundown
In a recent blog post, Mandiant detailed the evolution of operational tactics and malware usage of Black Basta’s primary user, tracked as UNC4393. This evolution includes the cluster’s transition from readily available tools to custom malware development, reliance on initial access brokers, and diversification of initial access techniques.
With a median time to ransom of approximately 42 hours, UNC4393 has demonstrated proficiency in quickly performing reconnaissance, data exfiltration, and completing actions on objectives. UNC4393 poses considerable and severe risks to all organizations and necessitates immediate response.
While UNC4393 is the only threat activity cluster deploying Black Basta that Mandiant tracks, there is a possibility that other vetted attackers may also be given access to the encrypter. Black Basta is not publicly marketed, and the operation does not appear to actively recruit affiliates to deploy the ransomware.
Instead, they focus on acquiring initial access via partnerships or purchases in underground communities. Mandiant suspects the Black Basta ransomware operation maintains a private or small, closed-invitation affiliate model whereby only trusted third-party actors are provided with the ransomware binary.
Source Material: Mandiant
ESXi Vulnerability Exploited in Ransomware Attacks to Escalate Privileges
Ransomware – Vulnerability Exploitation – Privilege Escalation – VMWare ESXi CVE-2024-37085 – Windows CVE-2023-28252 – All Industries
The Rundown
Microsoft has uncovered a vulnerability, CVE-2024-37085, in ESXi hypervisors being exploited by several ransomware groups, such as Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest, to obtain full administrative permissions on domain-joined ESXi hypervisors.
In a ransomware attack, an attacker with full administrative permission on an ESXi hypervisor can encrypt the file system, which could affect the ability of hosted servers to run and function. It also allows the attacker to access hosted VMs and possibly exfiltrate data or move laterally within the network. Microsoft recommends that ESXi server administrators apply the updates to protect their servers from related attacks.
Due to their popularity within corporate environments, ESXi hypervisors are becoming a favored target for ransomware attackers. Targeting ESXi hypervisors allows them to avoid detection because ESXi hypervisors typically have limited protection and visibility in security operations and allow one-click mass encryption. This enables attackers to spend more time on other malicious activity, such as lateral movement and credential and data theft.
Source Material: Microsoft
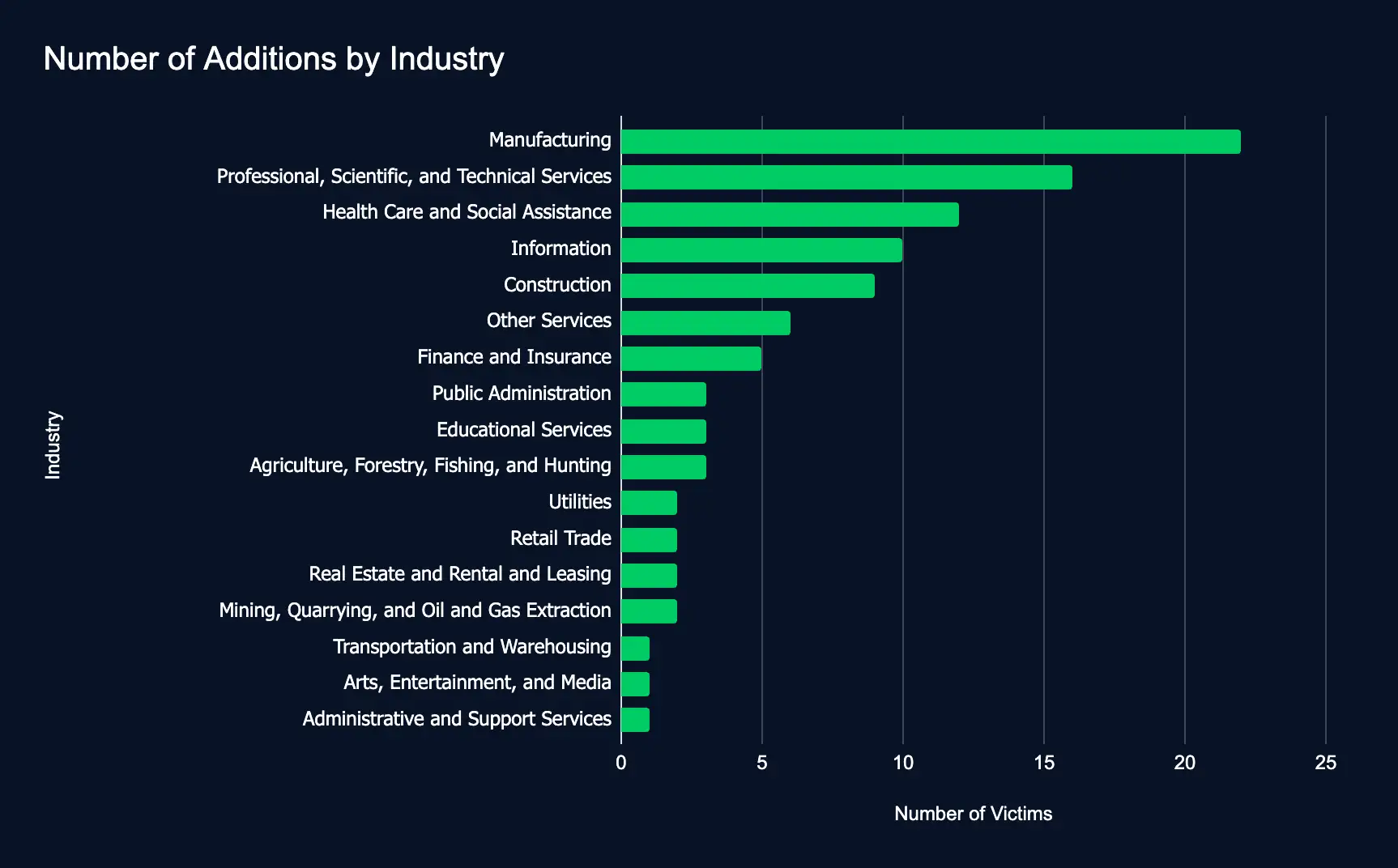
100 Organizations Hit by Ransomware in a Week, Manufacturing and Healthcare Most Affected
Manufacturing – Professional, Scientific, and Technical Services – Health Care and Social Assistance – Information – Construction
The Rundown
In just one week, 100 organizations across various industries and regions have been listed on ransomware data leak sites, indicating a slight escalation in cyberattacks over the previous reporting period.
This slight increase in ransomware leak site additions, reversing a trend of declining additions, underscores the growing cyber threat landscape. For organizations, staying vigilant, identifying potential third-party risks, and enhancing security measures are crucial to mitigate these escalating risks.
By the numbers:
CISA Adds Vulnerabilities in VMware, ServiceNow, and Acronis to Exploited Catalog
VMware ESXi CVE-2024-37085 – ServiceNow CVE-2024-4879 – ServiceNow CVE-2024-5217 – Acronis Cyber Infrastructure (ACI) CVE-2023-45249
The Rundown
Four newly exploited vulnerabilities in VMware, ServiceNow, and Acronis products have been added to CISA’s Known Exploited Vulnerabilities Catalog.
These newly identified vulnerabilities are critical because they can be exploited to gain unauthorized access and control over systems, leading to potential data breaches, disruptions, and ransomware attacks. Immediate action is required to apply security patches and implement mitigation measures to protect affected systems from these severe threats.
VMware ESXi:
CVE-2024-37085:
An authentication bypass vulnerability. An attacker with sufficient Active Directory permissions can gain full admin access to an ESXi host by adding or renaming an existing group to ESXi Admins. Exploitation details were covered in Deepwatch’s report titled “ESXi Vulnerability Exploited in Ransomware Attacks to Escalate Privileges.”
Mitigation Measures:
- Apply the latest security patches provided by VMware.
- Ensure robust Active Directory management practices to monitor and manage group deletions and recreations.
- Implement network segmentation to limit access to management interfaces.
ServiceNow:
CVE-2024-4879:
Improper input validation in jelly template injection in UI macros. This allows unauthenticated users to execute code remotely.
Mitigation Measures:
- Apply all available patches from ServiceNow.
- Implement strict input validation controls to prevent injection attacks.
CVE-2024-5217:
Incomplete list of disallowed inputs in the GlideExpression script, allowing unauthenticated remote code execution.
Mitigation Measures:
- Apply security patches provided by ServiceNow.
- Enhance input validation procedures to cover all potential inputs.
The exploitation of these vulnerabilities is detailed in Deepwatch’s customer advisory titled “Attackers Exploit Chain of Vulnerabilities in ServiceNow to Dump User List.”
Acronis Cyber Infrastructure:
CVE-2023-45249:
An insecure default password vulnerability allows unauthenticated users to execute commands remotely. Exploitation details have not been publicly released.
Mitigation Measures:
- Change all default passwords immediately upon deployment.
- Apply the latest security updates from Acronis.
- Conduct regular security audits to ensure compliance with password policies and other security protocols.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share