DarkGate Malware Hits U.S. in Malspam Campaign, Chinese Cyber Espionage Groups Exposed, Snowflake Extortion Reveals Security Gaps, 82 Organizations Leaked, and CISA Updates Vulnerabilities Catalog
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Malspam Campaign Unleashes DarkGate Malware in U.S.
- 3 Chinese State-Sponsored Cyber Espionage Groups Uncovered in Coordinated Operation
- Snowflake Data Extortion Campaign Exposes Credential Security Gaps
- 82 Organizations Added to Leak Sites in a Week
- CISA Adds 2 to Known Exploited Vulnerabilities Catalog
Malspam Campaign Unleashes DarkGate Malware in U.S.
Malware – Malspam Campaign – DarkGate – AutoHotKey Scripts – Excel Attachments – All Industries
Cybercriminals have launched a phishing campaign targeting various U.S. industries, delivering DarkGate malware through malspam emails with Excel attachments.
This campaign, active since mid-March, highlights attackers’ evolving tactics and the significant risks posed to critical sectors, including healthcare, telecom, financial, educational, and manufacturing industries.
The Rundown
Malspam emails with Excel attachments utilize Template Injection to auto-download and execute malicious content. Recipients inadvertently download files from an attacker-controlled SMB share, leading to the execution of VBS or JavaScript files that deploy a PowerShell script.
The PowerShell script retrieves AutoHotkey.exe, script.ahk, and test.txt, with the latter containing a base64-encoded DarkGate payload. AutoHotkey runs the malicious script, decoding and executing the payload in memory.
A shortcut file is created in the Startup directory, pointing to the malicious files, ensuring the malware’s persistence.
DarkGate, first documented in 2018, has evolved significantly, now using AutoHotKey scripts instead of AutoIt files. Its capabilities include user-grade access via hidden VNC, keystroke logging, privilege escalation, and payload execution in memory.
Source Material: Cisco Talos, DarkGate switches up its tactics with new payload, email templates
3 Chinese State-Sponsored Cyber Espionage Groups Uncovered in Coordinated Operation
Threat Actors – Chinese Threat Groups – Cyber Espionage – Malware -STAC1248 – STAC1870 – STAC1305 – PowHeartBeat – PhantomNet – PocoProxy – EAGERBEE – Merlin – CCoreDoor – RUDEBIRD – Industry: Public Administration
Three Chinese state-sponsored cyber espionage groups infiltrated a Southeast Asian government, using advanced techniques and malware to steal sensitive military and technical information over two years.
This operation underscores the sophisticated capabilities and persistent efforts of Chinese cyber espionage groups, highlighting the severe risk to sensitive information in targeted organizations. These actors’ ability to maintain long-term access and evade detection poses a significant threat to operations and strategic interests.
The Rundown
The three distinct clusters — STAC1248 (Cluster Alpha), STAC1870 (Cluster Bravo), and STAC1305 (Cluster Charlie) — used unique malware and techniques. Still, their overlapping infrastructures and shared objectives highlight a high level of sophistication and strategic coordination in Chinese cyber espionage activities. This collaboration enabled the groups to access critical systems, perform extensive reconnaissance, and exfiltrate sensitive data, demonstrating a unified effort to target and compromise high-profile government entities.
STAC1248, also known as Cluster Alpha, operated from early March to at least August 2023. This cluster focused on deploying various malware strains to establish persistent command-and-control (C2) channels, performing reconnaissance, and escalating privileges to maintain long-term access within the target network.
Techniques Used:
- Multiple sideloading attempts to deploy various malware strains.
- Use of unique methods to disable AV protections.
- Registry key creation and service modification for persistence.
Key Activities:
- Comprehensive mapping of server subnets and enumeration of administrator accounts.
- Frequent use of valid administrator credentials for domain enumeration.
- Use of PowerShell scripts and renamed legitimate executables for malware deployment.
Notable Malware:
- Deployed various malware, including PowHeartBeat backdoor and PhantomNet backdoor.
- Sideloading of DLLs using legitimate executables like vmnat.exe and mobpopup.exe.
C2 Infrastructure:
- Used domains like cloud.keepasses[.]com for C2 communications.
- Leveraged PhantomNet backdoor for establishing C2 and loading additional payloads.
STAC1870, also known as Cluster Bravo, was active for a shorter duration, primarily in March 2023. This cluster focused on lateral movement within the network, establishing persistent command-and-control (C2) communications, and conducting discovery activities using valid credentials and sophisticated malware.
Techniques Used:
- Sideloading of novel backdoors to establish C2 channels.
- Use of valid administrator accounts for lateral movement.
- Execution of PowerShell scripts for event log analysis and credential access.
Key Activities:
- Rapid creation and deletion of malicious files to evade detection.
- Execution of discovery commands targeting government domains and internal hosts.
- Credential dumping using Microsoft diagnostic tools like rdrleakdiag.exe.
Notable Malware:
- Deployment of the CCoreDoor backdoor for C2 and lateral movement.
- Execution of malicious PowerShell scripts embedded in legitimate executables.
C2 Infrastructure:
- Establishment of C2 sessions using administrator accounts and scheduled tasks.
- Use of CCoreDoor implants for internal and external C2 communications.
- Connection to attacker-controlled IPs for persistent network access.
STAC1305, also known as Cluster Charlie, operated the longest among the three clusters, from March 2023 to April 2024. This cluster prioritized access management, conducting extensive reconnaissance, and employing advanced evasion techniques to maintain persistence and exfiltrate sensitive data.
Techniques Used:
- Use of multiple variants of the PocoProxy malware for persistence.
- Execution of sophisticated evasion techniques, including DLL hijacking.
- Frequent rotation of C2 infrastructure to avoid detection.
Key Activities:
- Targeted user reconnaissance and mass analysis of event logs.
- Automated ping sweeps across the network to map users and endpoints.
- Credential dumping and lateral movement using valid administrator accounts.
Notable Malware:
- Deployment of PocoProxy malware to establish persistence and C2 communications.
- Use of McAfee File Lock to sideload an LSASS credential interceptor.
- Execution of PhantomNet and PowHeartBeat backdoors for data exfiltration.
C2 Infrastructure:
- Use of multiple PocoProxy samples to establish connections with various C2 IPs.
- Deployment of custom HUI loaders to stage Cobalt Strike payloads.
- Dynamic re-penetration of the network using web shells and scheduled tasks for persistent access.
This sophisticated cyber espionage operation shows evidence of related activities dating back to early 2022, underscoring these threat actors’ long-term strategic efforts and persistent nature.
- The earliest observed activity occurred in March 2022, where a tool was used to collect specific file types modified after 1 January 2021.
- The threat actors’ activities from early 2022 indicate a persistent threat, with continuous efforts to infiltrate, map, and compromise critical network systems, laying the groundwork for the more coordinated and intensive operations observed later on.
Organizations should implement a comprehensive cybersecurity strategy to mitigate the risks posed by these sophisticated cyber espionage groups. Here is a high-level overview of the recommended actions:
- Strengthen Access Controls
- Enhance Network Security
- Improve Endpoint Protection
- Conduct Regular Security Assessments
- Implement Robust Monitoring and Logging
- Educate and Train Employees
- Develop Incident Response Plans
- Implement Data Protection Measures
Source Material: Sophos Report 1, Operation Crimson Palace; & Sophos Report 2, Operation Crimson Palace: A Technical Deep Dive
Snowflake Data Extortion Campaign Exposes Credential Security Gaps
Data Breach – Frostbite – Infostealer – Compromised Credentials – Snowflake – Data Lake – All Industries
Hundreds of Snowflake customer instances were compromised through stolen credentials, leading to data theft and extortion attempts.
Attackers were able to access the instances by leveraging credentials from infostealer infections, some dating back four years, exploiting the lack of multi-factor authentication, non-rotated credentials, and the absence of network-allow lists.
The Rundown
Since April 2024, attackers have accessed Snowflake customer instances using stolen credentials, exfiltrating data, and attempting extortion. The compromised credentials, many obtained from infostealer malware infections, were often years old and not protected by multi-factor authentication.
The attackers gained access through several methods:
- Initial Access: Utilized stolen credentials from infostealer infections like VIDAR, REDLINE, and RACOON STEALER.
- Tools: Used Snowflake’s web-based UI, CLI tool, and a malicious utility named FROSTBITE for SQL reconnaissance.
- Data Exfiltration: Repeatedly executed SQL commands to stage and exfiltrate data, storing it on various VPS providers and MEGA cloud storage.
Source Material: Mandiant, UNC5537 Targets Snowflake Customer Instances for Data Theft and Extortion
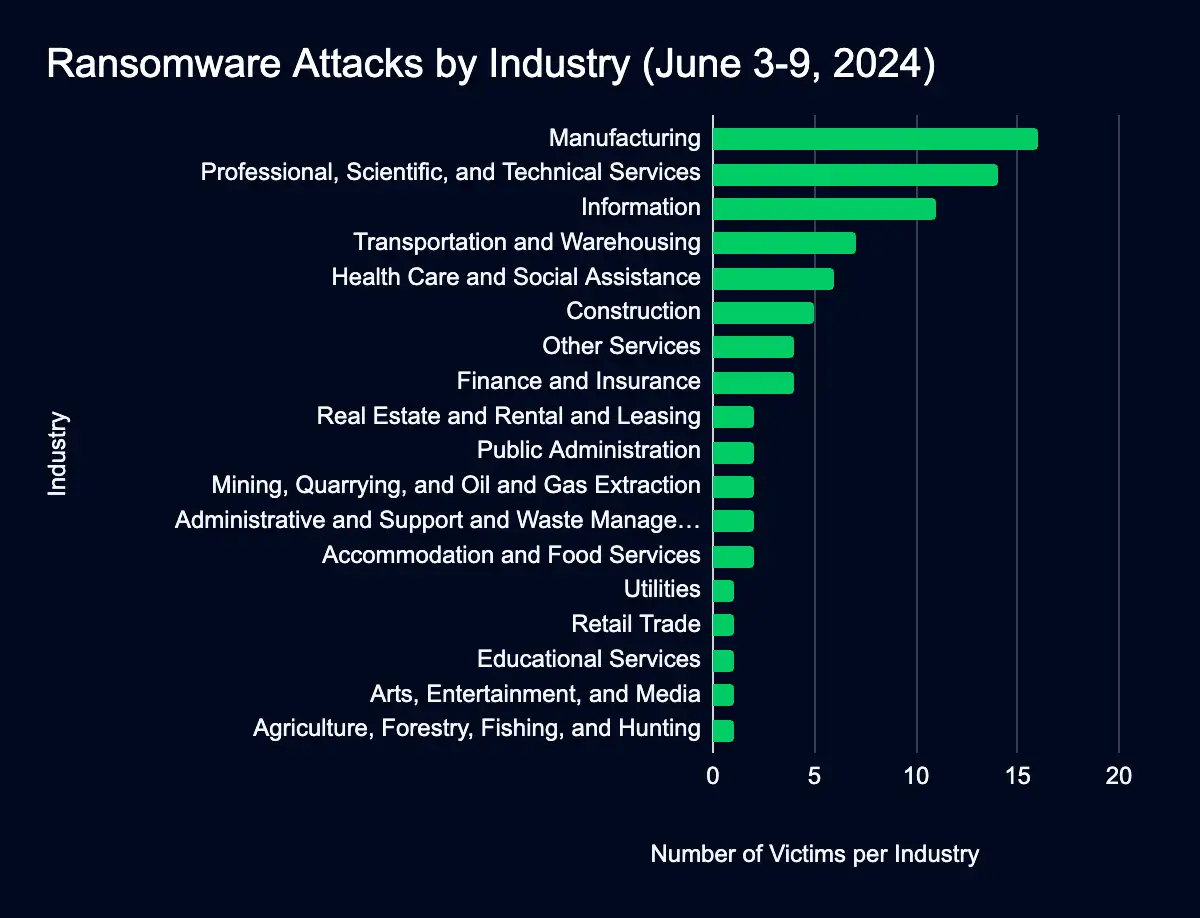
82 Organizations Added to Leak Sites in a Week
Manufacturing – Professional, Scientific, and Technical Services – Information – Transportation and Warehousing – Health Care and Social Assistance
Between June 3 and June 9, ransomware groups added 82 organizations to data leak sites, with Medusalocker leading the charge by listing 34 new victims.
This ransomware activity underscores the escalating threat to organizations worldwide, emphasizing the urgent need for enhanced cybersecurity measures to protect against such attacks.
The Rundown
Following Medusalocker, which accounted for 41% of the new additions, Black Basta added 7 organizations, while Arcusmedia and APT73 each added 6.
By the numbers:
- Medusalocker: 34 organizations (41%)
- Black Basta: 7 organizations
- Arcusmedia: 6 organizations
- APT73: 6 organizations
Industry Impact
Out of the 82 organizations listed, the manufacturing and professional services sectors experienced the highest number of ransomware attacks, with 16 and 14 organizations affected, respectively.
The concentration of ransomware attacks in critical sectors highlights their attractiveness to attackers, as these industries may be willing to pay large amounts to resolve disruptions.
By the numbers:
- Manufacturing: 16 organizations (20%)
- Professional, scientific, and technical services: 14 organizations (17%)
- Information sector: 11 organizations (13%)
Geographic Distribution
Out of the 82 organizations listed, those headquartered in the United States experienced the highest number of ransomware attacks from June 3 to June 9, 2024, with 38 organizations affected.
The high number of ransomware attacks targeting U.S.-based organizations reflects the country’s large number of businesses and economic activities, highlighting the need for enhanced cybersecurity measures.
By the numbers:
- United States: 38 organizations (46%)
- Germany: 7 organizations (9%)
- United Kingdom: 6 organizations (7%)
Ransomware groups continue to expand their reach, targeting a wide range of industries and geographies. Organizations must stay vigilant and strengthen their defenses to combat this ongoing menace.
CISA Adds 2 to Known Exploited Vulnerabilities Catalog
Arm Mali GPU Kernel Driver CVE-2024-4610 – PHP-CGI OS CVE-2024-4577
Two critical vulnerabilities, CVE-2024-4610 in Arm Mali GPU drivers and CVE-2024-4577 in PHP have been added to CISA’s Known Exploited Vulnerabilities Catalog.
These vulnerabilities, now known to have been exploited or are currently under active exploitation, pose severe cybersecurity risks, including data breaches, unauthorized access, and ransomware attacks.
The Rundown
CVE-2024-4610, a use-after-free vulnerability in Arm Mali GPU drivers, allows attackers to access freed memory, which could lead to potential data breaches and ransomware attacks.
Arm has released fixes for CVE-2024-4610 in Bifrost and Valhall GPU Kernel Driver r41p0.
CVE-2024-4577, an OS command injection vulnerability in PHP used in CGI mode on Windows, enables arbitrary code execution and has been used to spread the “TellYouThePass” ransomware.
PHP has addressed CVE-2024-4577 in versions 8.1.29, 8.2.20, and 8.3.8. Organizations are urged to update immediately to mitigate these risks.
CISA recommends that mitigation be completed by July 3, 2024, so affected organizations can apply the necessary updates and protect their systems from these critical vulnerabilities.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share