‘Sleepy Pickle’ Targets ML Models, Scattered Spider Threatens Cloud Security, Copy-Paste Malware Rises, ShinyHunters Breach Snowflake, 87 New Leaks, and CISA Adds 3 Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- New ‘Sleepy Pickle’ Attack Targets ML Models
- Evolving Tactics of Scattered Spider Threaten SaaS and Cloud Security
- Copy-Paste Malware: A Growing Threat from TA571 and ClearFake
- ShinyHunters Claims They Compromised Contractor to Gain Access to Snowflake Accounts
- 87 Organizations Added to Leak Sites in a Week
- Three Vulnerabilities Added to CISA’s Exploited Catalog
New ‘Sleepy Pickle’ Attack Targets ML Models
New Technique – Sleepy Pickle – Machine Learning Model Attacks – All Industries
The Rundown
Cybersecurity researchers with Trail of Bits have identified a new attack technique called Sleepy Pickle. This technique targets machine learning models by exploiting insecurities in pickle files.
- Pickle files are used in Python to share trained ML Models which could be used to run malicious code.
Why it matters: The Sleepy Pickle attack demonstrates a critical insecurity in how machine learning (ML) models handle serialized data, potentially leading to severe security breaches.
- Many ML practitioners or engineers may not be aware of cybersecurity or best security practices when using shared ML models.
- Organizations using or developing ML models should review the MITRE Atlas matrix, which shows attack tactics tailored to ML.
Pickle files are used in Python to serialize and deserialize data. They are inherently insecure because they can execute arbitrary code during deserialization, making them a target for malicious exploitation.
Trail of Bits researchers discovered that Sleepy Pickle can execute malicious code during deserialization, a critical step in machine learning workflows.
- It also self-replicates by wrapping the payload in an encapsulating, persistent payload by hooking any function, automatically spreading to derivative models.
- This will not leave traces on the disk outside the original infected pickle file.
- Hooking any function in the Python interpreter allows for other attack variations, as the attacker can access training datasets and configuration files, amongst others.
How it works: Sleepy Pickle exploits the deserialization process in the following steps:
- Preparation:
- An attacker crafts a malicious pickle file containing harmful code. Tools like Fickling can create these malicious pickle files with a single command and have APIs for advanced attack techniques.
- Sleepy Pickle targets the ML model rather than the underlying system by injecting a custom function (payload) into a pickle file containing a serialized ML model.
- Delivery: The attacker delivers the malicious pickle file to the victim’s system via a Man-in-the-Middle (MITM) attack, supply chain compromise, social engineering, etc.
- Execution: When the file is deserialized on the victim’s system, the payload is executed, and the contained model is modified to insert backdoors, control outputs, or tamper with processed data before returning it to the user.
With Sleepy Pickle, there are two aspects of an ML model an attacker can compromise:
- Model parameters: Patch a subset of the model weights to change the model’s intrinsic behavior. This can be used to insert backdoors or control model outputs.
- In one test, a POC that compromises the GPT-2-XL model spreads harmful medical advice to users.
- In another test, the payload adds malicious links to its generated summary.
- More sophisticated attacks can make malicious link insertion seamless by customizing the link based on the input URL and content.
- If the app returns content in an advanced format containing JavaScript, the payload could also inject malicious scripts into the response sent to the user.
- In another test, the payload adds malicious links to its generated summary.
- In one test, a POC that compromises the GPT-2-XL model spreads harmful medical advice to users.
- Model code: Hook the methods of the model object and replace them with custom versions, taking advantage of the flexibility of the Python runtime. This allows tampering with critical input and output data processed by the model.
- In one test, the payload records private user data.
- This can not be prevented by traditional security measures because everything happens within the model code and through the application’s interface.
- In one test, the payload records private user data.
Sleepy Pickle attacks allow for advanced exploitation without presenting conventional indicators of compromise:
- No trace of exploitation is left on the disk when the file is loaded in the Python process, compromising the model.
- The attack doesn’t require local or remote access to other system parts and relies solely on one malicious pickle file.
- Changes to the model cannot be detected by a static comparison when the model is dynamically modified at deserialization time.
- The attack is difficult to detect and highly customizable because the payload can use Python libraries and activate itself only under specific circumstances, and allows attackers to target only specific systems or organizations.
Source Material: Trail of Bits, Exploiting ML models with pickle file attacks: Part 1 & Trail of Bits, Exploiting ML models with pickle file attacks: Part 2
Evolving Tactics of Scattered Spider Threaten SaaS and Cloud Security
Threat Actor – SaaS Attacks – Cloud Security Attacks – Data Exfiltration – Scattered Spider – All Industries
The Rundown
Scattered Spider, a financially motivated threat group, is adapting its methods to exploit weaknesses in SaaS applications and cloud infrastructure, posing significant risks to organizations.
With attacks exploiting SaaS and cloud infrastructure by groups such as Scattered Spider, organizations must prioritize enhancing their security protocols to prevent costly data exfiltration and system compromises.
Since early 2024, Mandiant has observed Scattered Spider expanding its activities to include data theft from SaaS applications, abusing permissions for lateral movement, and creating new virtual machines for persistence.
Scattered Spider employs advanced social engineering tactics, uses publicly available tools like Mimikatz and ADRecon, and leverages cloud synchronization utilities for data exfiltration.
- Social Engineering: Scattered Spider uses detailed personal identifiable information (PII) to bypass identity verification processes, often targeting corporate help desks and conducting SMS phishing campaigns.
- Public Tools: They deploy widely available tools such as Mimikatz for credential harvesting, ADRecon for Active Directory reconnaissance, and Python libraries like IMPACKET for further exploitation.
- Cloud Synchronization: They exploit cloud synchronization utilities like Airbyte and Fivetran to move data from compromised environments to attacker-owned storage solutions.
- Persistence: They create new virtual machines using administrative privileges in environments like vSphere and Azure, employing tools like MAS_AIO and privacy-script.bat to disable security measures and maintain persistence.
- Exploitation: The group abuses SaaS permissions for lateral movement and conducts internal reconnaissance through platforms like Okta, enabling them to expand their access within a victim’s network.
To counter these evolving threats, organizations need to:
- Strengthen monitoring and logging for SaaS applications.
- Implement robust endpoint detection and response (EDR) solutions.
- Enhance help desk security protocols with multi-factor authentication (MFA) and social engineering awareness training.
- Deploy advanced threat intelligence capabilities to stay ahead of emerging tactics.
Expect Scattered Spider to continue refining its tactics and possibly expand its toolkit to include more sophisticated methods for exploiting cloud and SaaS vulnerabilities.
Source Material: Mandiant, UNC3944 Targets SaaS Applications
Copy-Paste Malware: A Growing Threat from TA571 and ClearFake
Threat Actor – Phishing – Fake Browser Update – TA571 – ClearFake – Malware Deployment – All Industries
The Rundown
Proofpoint reports increased attacks using copy-paste PowerShell scripts deployed by TA571 and ClearFake, infecting computers with DarkGate, Matanbuchus, NetSupport, and various infostealers.
These campaigns exploit user actions to run malicious scripts, bypassing many traditional detection methods, and highlight a sophisticated trend in malware distribution.
Recent TA571 phishing emails contain HTML attachments mimicking Microsoft Word with an error popup. The error message instructs users to copy a “fix,” which is actually a malicious PowerShell command. The command downloads and executes MSI or VBS files, leading to malware like Matanbuchus and DarkGate.
Recent ClearFake fake browser update campaigns have led users to paste clipboard scripts into PowerShell, deploying multi-stage payloads such as Lumma Stealer and cryptocurrency miners.
Technical details:
- Clipboard Exploitation: JavaScript in compromised websites or HTML attachments copies the malicious script to the clipboard.
- Multi-stage Payloads: Scripts often perform multiple actions, such as flushing DNS, downloading additional scripts, and executing payloads hidden in ZIP files.
- Detection Challenges: The manual nature of user execution and encoding of scripts in HTML make detection difficult for antivirus software and EDRs.
Risks & Impacts:
- Operational: Multi-stage malware can disrupt operations and steal sensitive data.
- Financial: Costs from data theft, downtime, and increased energy use from miners.
- Reputational: Breaches can damage trust and customer retention.
- Legal: Potential regulatory fines and legal actions from data protection violations.
Outlook:
Expect continued use of clipboard hijacking and more sophisticated evasion techniques over the next six months. Attackers will likely refine payloads, employ AI for social engineering, and target specific industries.
Recommendations:
- Monitoring & Detection: Enhance IDS/IPS to analyze JavaScript and clipboard activities.
- User Training: Regular sessions on recognizing phishing and avoiding unknown scripts.
- Clipboard Inspection: Develop tools for inspecting clipboard content for threats.
- Browser Security: Enforce strict content security policies and regularly update browsers.
The Bottom Line:
Organizations must stay vigilant and adapt to these evolving threats by enhancing their cybersecurity measures and educating users on the risks of executing unknown scripts.
Source Material: Proofpoint, From Clipboard to Compromise: A PowerShell Self-Pwn
ShinyHunters Claims They Compromised Contractor to Gain Access to Snowflake Accounts
Threat Actor – Data Breach – Third Party Risks – Snowflake Data Breach – ShinyHunters – All Industries
The Rundown
ShinyHunters claims they accessed Snowflake accounts by compromising an EPAM Systems employee’s device. EPAM is an American third-party contracting company specializing in software engineering services, digital platform engineering, and digital product design.
If their claims are true, the compromise of a single device directly led to the compromise of potentially hundreds of Snowflake instances.
About 165 Snowflake customer accounts were potentially affected in the recent hacking campaign targeting Snowflake’s customers, but only a few of these have been identified so far. To date, companies affected by this breach include:
- Ticketmaster
- Santander
- Lending Tree
- Advance Auto Parts
According to a post published by the attackers, Santander’s stolen data included bank account details for 30 million customers, including 6 million account numbers and balances, 28 million credit card numbers, and human resources information about staff.
They also claim to have compromised EPAM Systems, a publicly traded software engineering and digital services firm founded in Belarus.
Contrary to previous reports that the attackers gained access to Snowflake accounts using credentials likely obtained through infostealers, one of the attackers who spoke with WIRED says his group, ShinyHunters, used data found on an EPAM Systems employee device to gain access to some of the Snowflake accounts.
The attacker who spoke with WIRED says that a computer belonging to one of EPAM System’s employees in Ukraine was infected with an infostealer through a spear-phishing attack. The hacker says that once on the worker’s system, they installed a Remote Access Trojan (RAT).
- It’s unknown if ShinyHunters conducted this initial breach or just purchased access to the infected system.
According to the attacker, they found unencrypted Snowflake account usernames and passwords the worker used for EPAM customers, including an account for Ticketmaster.
- They claimed that the credentials were stored in Jira.
- In some cases, where the credentials were stored, they could directly access the Snowflake account of EPAM customers because they didn’t require multifactor authentication (MFA).
- In cases where the credentials were not stored, the attacker claims they sifted through stockpiles of old credentials stolen by infostealers, including ones harvested from the machine of the same EPAM worker in Ukraine.
- The attackers say they were able to use credentials stolen by an infostealer in 2020 to access Snowflake accounts.
- The attacker provided WIRED with a file that appears to be a list of EPAM worker credentials lifted from the company’s Active Directory database.
Supporting the attacker’s claims, an independent security researcher helping to negotiate the ransom transactions between ShinyHunter and victims pointed WIRED to an online repository of data harvested by an infostealer.
- The repository includes data siphoned from the computer of the EPAM worker in Ukraine.
- The data includes the worker’s browser history, an internal EPAM URL pointing to Ticketmaster’s Snowflake account, and the username and password in plaintext that the EPAM worker uses to access the Ticketmaster Snowflake account.
However, EPAM Systems told WIRED that it does not believe it played a role in the breaches and suggested the hacker had fabricated the tale.
In an email to WIRED, an EPAM System spokesperson stated, “Hackers frequently spread false information to advance their agendas. We maintain a policy of not engaging with misinformation and consistently uphold robust security measures to protect our operations and customers. We are continuing our exhaustive investigation and, at this time, see no evidence to suggest that we have been affected or involved in this matter.”
Note: EPAM Systems, a software developer and provider of various managed services for customers worldwide, assists customers with using and managing their Snowflake accounts to store and analyze their data.
- EPAM Systems claims it has some 300 workers who are experienced in using Snowflake’s data analytics tools and services.
- In early August 2022, they announced they had attained “Elite Tier Partner“ status.
WIRED also followed up by providing the name, username, and password of the Ukrainian worker whose machine the attackers allegedly compromised to access Ticketmaster’s Snowflake account, but the spokesperson did not answer any additional questions.
However, it’s possible the ShinyHunter did not compromise the EPAM worker and simply gained access to the Snowflake accounts using usernames and passwords they obtained from old repositories of credentials stolen by infostealers.
- However, anyone can sift through those repositories for these and other credentials stolen from EPAM accounts.
- EPAM has customers across critical industries, including banks and other financial services, health care, broadcast networks, pharmaceuticals, energy and other utilities, insurance, software, and hi-tech.
- Prominent EPAM customers include Microsoft, Google, Adobe, and Amazon Web Services.
Credentials harvested by infostealers are often posted online or made available for sale on hacker forums.
- If victims don’t change their login credentials after a breach or don’t know their data has been stolen, those credentials can remain active and available for years.
- This is especially problematic if those credentials are used across multiple accounts. If that person reuses the same password, attackers can simply try those credentials in multiple accounts.
The Snowflake campaign also highlights the growing security risks from third-party companies and infostealers.
- As previously reported, multiple contractors were breached to gain access to Snowflake accounts.
- Contractors—often known as business process outsourcing (BPO) companies—are a potential gold mine for attackers.
- Compromising a contractor’s machine with access to multiple customers’ accounts can give them direct access to many customer accounts.
Employees of contractors who assist their customers in using Snowflake may utilize personal and/or non-monitored laptops, which exacerbates this initial entry vector.
- These devices, often used to access the systems of multiple organizations, present a significant risk.
- If compromised by an infostealer, a single contractor’s laptop can facilitate an attacker’s access across multiple organizations, often with IT and administrator-level privileges.
- Accompanied by the fact that these accounts may not use MFA, escalates the potential risks and impacts.
In a conversation with WIRED, Brad Jones, Snowflake’s CISO, said they are working on giving its customers the ability to mandate that users of their accounts employ multifactor authentication in the future, and they’ll be looking in the future to MFA the default setting.
Source Material: WIRED, Hackers Detail How They Allegedly Stole Ticketmaster Data From Snowflake
87 Organizations Added to Leak Sites in a Week
Manufacturing – Professional, Scientific, and Technical Services – Retail Trade – Information – Health Care and Social Assistance – Construction
The Rundown
Between June 10 and June 16, ransomware groups added 87 organizations to data leak sites. Play led this week’s new additions, with 25 new victims.
This ransomware activity underscores the escalating threat to organizations worldwide, emphasizing the urgent need for enhanced cybersecurity measures to protect against such attacks.
Following Play, Malek, RansomHub, Qilin, and Cactus were each significant contributors to new additions.
By the numbers:
- Play: 25 organizations (29%)
- Malek: 10 (11%)
- RansomHub: 5 (6%)
- Qilin: 5 (6%)
- Cactus: 5 (6%)
Industry Impact:
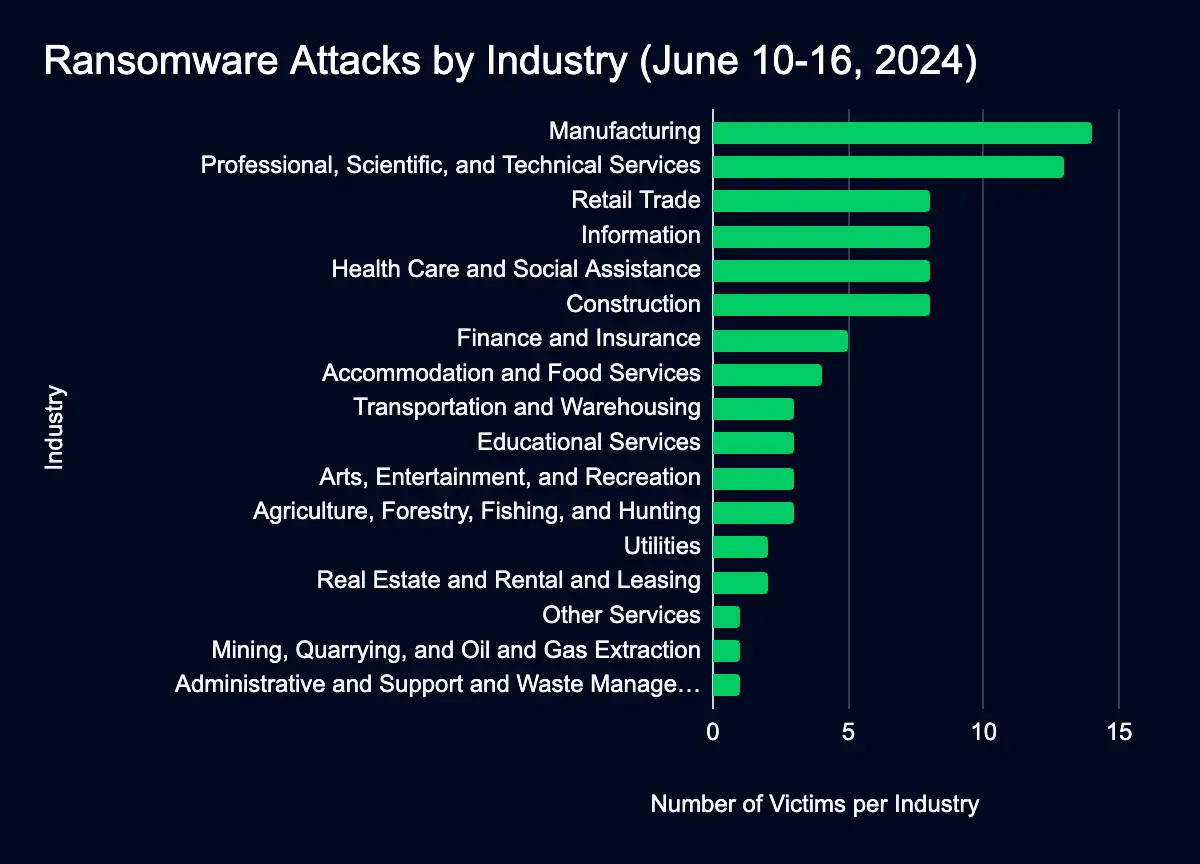
Out of the 87 organizations listed, the manufacturing and professional services sectors experienced the highest number of ransomware attacks.
The concentration of ransomware attacks in critical sectors highlights their attractiveness to attackers, as these industries may be willing to pay large amounts to resolve disruptions.
By the numbers:
- Manufacturing: 14 organizations (16%)
- Professional, scientific, and technical services: 13 (15%)
- Retail Trade: 8 (9%)
- Information: 8 (9%)
- Health Care and Social Assistance: 8 (9%)
- Construction: 8 (9%)
Geographic Distribution:
Out of the 87 organizations listed, those headquartered in the United States experienced the highest number of ransomware attacks.
The high number of ransomware attacks targeting U.S.-based organizations reflects the country’s large number of businesses and economic activities, highlighting the need for enhanced cybersecurity measures.
By the numbers:
- United States: 41 organizations (47%)
- Israel: 10 (11%)
- United Kingdom: 7 (8%)
- Canada: 7 (8%)
Ransomware groups continue to expand their reach, targeting a wide range of industries and geographies. Organizations must stay vigilant and strengthen their defenses to combat this ongoing menace.
Three Vulnerabilities Added to CISA’s Exploited Catalog
Android Pixel CVE-2024-32896 – Microsoft Windows Error Reporting Service CVE-2024-26169 – Progress Telerik Report Server CVE-2024-4358
The Rundown
Three vulnerabilities, CVE-2024-32896 in Android Pixel, CVE-2024-26169 in Microsoft Windows Error Reporting Service, and CVE-2024-4358 in Progress Telerik Report Server, have been added to CISA’s Known Exploited Vulnerabilities Catalog.
These vulnerabilities, now known to have been exploited or are currently under active exploitation, pose severe cybersecurity risks, including:
- CVE-2024-32896 allows for privilege escalation.
- CVE-2024-26169 allows for privilege escalation.
- CVE-2024-4358, when chained with CVE-2024-1800, could lead to remote code execution.
CVE-2024-32896 has been fixed in the June 2024 security update. CISA has recommended a July 4, 2024 deadline to resolve this issue.
CVE-2024-26169 was patched on March 12, 2024. CISA has recommended a July 4, 2024 deadline to address this issue.
CVE-2024-4358, an authentication bypass by spoofing vulnerability, was addressed via an update (Telerik Report Server 2024 Q2 10.1.24.514) on May 15. CISA has recommended a deadline of July 4, 2024, to fix this issue.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share