SolarWinds Vulnerability Exploited, Rafel RAT Targets Android, UNC3886 Accesses VMs, MOVEit Transfer Exploited, BMANAGER Malware Emerges, 76 New Leaks, and CISA Updates
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Customer Advisory | Active Exploitation Follows Public Release of PoC for MOVEit Transfer Vulnerability
- Critical SolarWinds Vulnerability Exploited in GreyNoise Honeypots, Public PoC Available
- Rafel RAT: Inside the Android Malware’s Espionage and Ransomware Capabilities
- UNC3886 Exploits Vulnerabilities to Access VMs for Cyber Espionage
- BMANAGER Modular Malware, an Emerging Malware Threat
- 76 Organizations Added to Data Leak Sites in the Past Week
- CISA Adds 3 Vulnerabilities to Exploited Catalog
Customer Advisory | Active Exploitation Follows Public Release of PoC for MOVEit Transfer Vulnerability
Active Vulnerability Exploitation – Progress MoveIT CVE-2024-5806 – Authentication Bypass – All Industries
The Rundown
A newly disclosed MOVEit Transfer vulnerability (CVE-2024-5806) is being actively exploited after a proof-of-concept (PoC) was released publicly on 24 June.
The vulnerability allows attackers to bypass authentication and gain access to MOVEit Transfer and Gateway systems, posing severe risks to sensitive data and system integrity. Immediate patching is necessary to prevent potential breaches.
Vulnerability details:
CVE-2024-5806 is an authentication bypass vulnerability in MOVEit Transfer and Gateway. This flaw allows attackers to impersonate any user without valid credentials. Progress Software has released patches to address this critical issue. Versions affected include:
- From 2023.0.0 before 2023.0.11.
- From 2023.1.0 before 2023.1.6.
- From 2024.0.0 before 2024.0.2.
Exploiting this vulnerability requires attackers to meet three criteria:
- Knowledge of an existing username (username spraying could identify valid accounts).
- The target account must be able to authenticate remotely.
- The SFTP service must be exposed.
Active exploitation:
The Shadowserver Foundation has observed increased scanning activity targeting MOVEit Transfer instances shortly after a proof-of-concept exploit code was made publicly available. This indicates that attackers seek out unpatched systems to exploit CVE-2024-5806.
- Observed POST /guestaccess.aspx exploit attempts.
Exploit code:
watchTowr Labs has publicly released a proof-of-concept (PoC) for CVE-2024-5806 on GitHub. The PoC provides attackers with a detailed guide to exploit the vulnerability.
Read the full Customer Advisory for additional information and details.
Source Material: Deepwatch, Active Exploitation Follows Public Release of PoC for MOVEit Transfer Vulnerability
Critical SolarWinds Vulnerability Exploited in GreyNoise Honeypots, Public PoC Available
Vulnerability Exploitation Attempts – Proof-of-Concept (PoC) – Path & Directory Traversal – SolarWinds Serv-U CVE-2024-28995 – All Industries
The Rundown
Attackers are exploiting a SolarWinds Serv-U path-traversal vulnerability tracked as CVE-2024-28995 in GreyNoise honeypots, potentially using publicly available proof-of-concept (PoC) exploits.
But, as of June 20, 2024, CISA has not added this vulnerability to their Known Exploited Vulnerabilities catalog.
Exploiting CVE-2024-28995 can expose sensitive data, potentially resulting in a prolonged compromise. This underscores the gravity of the risk posed by unpatched endpoints, emphasizing the immediate need to apply security updates.
The high-severity directory traversal vulnerability allows unauthenticated attackers to read arbitrary files from the filesystem by crafting specific HTTP GET requests. It results from insufficient validation of path traversal sequences, enabling attackers to bypass security checks and access sensitive files.
SolarWinds Serv-U products impacted:
- Serv-U FTP Server 15.4
- Serv-U Gateway 15.4
- Serv-U MFT Server 15.4
- Serv-U File Server 15.4.2.126 and earlier
Older versions (15.3.2 and earlier) are also affected but will reach the end of life in February 2025 and are already unsupported.
SolarWinds released the 15.4.2 Hotfix 2, version 15.4.2.157, on June 5, 2024, to address this vulnerability, introducing improved validation mechanisms.
Detailed steps to exploit the vulnerability to read arbitrary files from the affected system were published in a Rapid7 technical write-up and blog post on June 11.
- On June 12, a proof-of-concept (PoC) exploit and a bulk scanner for CVE-2024-28995 were released on GitHub.
- Rapid7 notes that the flaw is trivial to exploit.
- They estimated the number of internet-exposed and potentially vulnerable instances between 5,500 and 9,500.
Observations of CVE-2024-28995 exploitation attempts were published by GreyNoise on June 18.
- They set up an experimental honeypot mimicking a vulnerable Serv-U system to monitor and analyze exploitation attempts.
- They observed both hands-on and automated attempts.
- Attackers used platform-specific path traversal sequences using incorrect slashes, which the Serv-U system later corrects, allowing unauthorized file access.
- In some attempts, the attackers appeared to copy-paste exploits without testing, resulting in failed attempts.
Attackers most frequently targeted the following files to escalate their privileges or explore secondary opportunities in the breached network:
- \etc\passwd: Contains user account data on Linux. GreyNoise saw attackers attempt to access this file 25 times.
- /ProgramData/RhinoSoft/Serv-U/Serv-U-StartupLog.txt: Contains startup logs info for the Serv-U FTP server). GreyNoise saw attackers attempt to access this file 24 times.
- /windows/win.ini: An initialization file containing Windows configuration settings. GreyNoise saw attackers attempt to access this file 21 times.
In the hands-on keyboard activity, GreyNoise noted that the attacker experimented with different payloads and formats for four hours and adjusted their approach based on server responses.
- The attack originated from an IP address that geolocates to Shenzhen, China.
- The attacker appended a non-English UTF-8 character hex code, which converts to an idiographic comma used in Chinese and Japanese.
Source Material: Rapid 7 Blog Post, Rapid7 Technical Write-up, GitHub PoC, and GreyNoise
Rafel RAT: Inside the Android Malware’s Espionage and Ransomware Capabilities
Android Malware – Android Remote Access Trojan – Android Data Theft – Android Data Encryption – Android Locking – Rafel RAT – All Industries
The Rundown
Rafel RAT, a sophisticated Android remote access trojan, poses a significant threat with its espionage and ransomware capabilities. It has been deployed in around 120 malicious campaigns targeting users globally, predominantly in the United States, China, and Indonesia.
Rafel RAT’s sophisticated capabilities allow it to steal sensitive data and manipulate devices, posing a severe threat to organizational security. Understanding this malware’s features and distribution methods is crucial for developing effective mitigation strategies and protecting critical infrastructure.
Rafel RAT boasts a range of sophisticated features:
- Data Theft: It can steal sensitive information, including passwords, contacts, messages, and multi-factor authentication (MFA) codes.
- Device Manipulation: It can control device functions like screen capture and microphone activation.
- Command and Control: It can execute commands remotely via a C2 server.
- Ransomware: It can encrypt files, change the screen lock code, and lock the screen on infected devices.
- Destructive Actions: It can delete files, uninstall apps, and factory reset devices to cause significant data loss and destruction.
Rafel RAT was designed to spread through phishing campaigns, leveraging deceptive tactics to manipulate user trust. The malware is often disguised as a legitimate app or impersonates a legitimate entity.
- Check Point uncovered numerous phishing operations utilizing Rafel RAT but does not provide further details on these campaigns.
Rafel RAT campaigns have predominantly targeted users in the United States, China, and Indonesia, but the malware’s reach is global. Key insights include:
- Most victims had Samsung phones, followed by Xiaomi, Vivo, and Huawei users.
- The most affected Android versions were:
- Android 11 (21.4%)
- Android 8 (17.9%)
- Android 5 (17.9%)
It is worth noting that each of these top impacted versions of Android are all out of support, with Android 11 support having ended in February of 2024.
To protect against Rafel RAT, organizations should implement the following strategies:
- Employee Training: Educate staff on recognizing phishing attempts and avoiding suspicious links or downloads.
- Regular Updates: Ensure all devices are running the latest version, version 14.
- Mobile Security: Deploy robust mobile antivirus and anti-malware solutions to detect and prevent infections.
Rafel RAT’s advanced capabilities and widespread use in phishing campaigns make it a formidable threat. Organizations must stay vigilant, employing robust security measures to enhance cyber resilience and protect against this threat.
Source Material: Check Point, RAFEL RAT, ANDROID MALWARE FROM ESPIONAGE TO RANSOMWARE OPERATIONS
UNC3886 Exploits Vulnerabilities to Access VMs for Cyber Espionage
Threat Actor – Chinese Threat Actor – Cyber Espionage – Vulnerability Exploitation – Malware – Credential Harvesting – Lateral Movement – Reconnaissance – VMware vCenter CVE-2023-34048 & CVE-2022-22948 – VMware Tools CVE-2023-20867 – Fortinet FortiOS CVE-2022-41328 & CVE-2022-42475 – Rootkit – Backdoor – Sniffer – REPTILE – MEDUSA – MOPSLED – RIFLESPINE – LOOKOVER – NMAP – UNC3886 – Public Administration – Information – Manufacturing – Professional, Scientific, and Technical Services – Utilities
The Rundown
Since 2021, UNC3886, a China-nexus cyber espionage group, has exploited several vulnerabilities in VMware and FortiOS to gain access to guest virtual machines, enabling persistent cyber espionage across multiple sectors globally.
UNC3886’s sophisticated techniques and persistent access pose significant risks to critical sectors worldwide, highlighting the urgent need for proactive and adaptive cybersecurity measures.
Intrusion Path
- Initial Access: UNC3886 exploits vulnerabilities (CVE-2023-34048, CVE-2022-41328, CVE-2022-22948, and CVE-2023-20867) in VMware vCenter, VMware Tools, and FortiOS to gain initial access without credentials.
- Post-access Malware Deployment: After gaining control, UNC3886 deploys rootkits on compromised guest virtual machines to maintain access and evade detection. These rootkits provide backdoor access, command execution, and file transfer capabilities.
- Follow-on Malware: UNC3886 uses custom-developed malware for persistence and command-and-control, leveraging platforms like GitHub and Google Drive to avoid detection.
- Lateral Movement: The group harvests SSH credentials for lateral movement within networks using modified SSH clients and daemons, facilitating widespread network access and data breaches.
- Reconnaissance: UNC3886 conducts aggressive network scans using tools like NMAP and deployed sniffers to capture authentication credentials.
UNC3886 is expected to continue targeting sectors critical to national security and economic stability, expanding its operations and refining its tactics to evade detection and enhance intrusion capabilities.
UNC3886’s advanced cyber espionage techniques and persistence necessitate robust and adaptive cybersecurity measures to protect critical sectors and infrastructure from significant geopolitical and economic risks.
Mitigation Strategies
- Patch Management: Ensure all systems, especially VMware and FortiOS, are updated with the latest security patches.
- Advanced Threat Detection: Deploy advanced threat detection tools and intrusion detection systems (IDS) to monitor network traffic and endpoints.
- Network Segmentation: Implement VLANs and firewalls to segment the network based on function and sensitivity, restricting communication to necessary traffic only.
- Zero Trust Security: Adopt a zero-trust security model to minimize unauthorized access, enforce least-privilege access controls, and monitor user activities continuously.
- Robust Authentication: Implement multi-factor authentication (MFA) and enforce robust authentication mechanisms for all users.
- Continuous Training: Conduct regular cybersecurity training and awareness programs to enhance staff’s detection and response capabilities.
- Monitoring and Alerts: Configure alerts for suspicious activities related to exploiting VMware and FortiOS vulnerabilities, the presence of known malware signatures, and unusual network connections.
Source Material: Mandiant, Cloaked and Covert: Uncovering UNC3886 Espionage Operations
BMANAGER Modular Malware, an Emerging Malware Threat
Threat Actor – Malware – Malware Modules – SQL Injection – Compromised Websites – Boolka – BMANAGER – BMREADER – BMLOG – BMHOOK – BMBACKUP – All Industries
The Rundown
Since March 2024, an attacker has been injecting a new malware delivery platform into vulnerable websites that deliver the BMANAGER modular malware.
Why it matters:
BMANAGER malware exploits vulnerable websites, using HTTP(S) traffic and unmonitored local SQL databases to avoid detection and ensure persistence. This attack can steal sensitive data, posing a high risk to organizations’ end-users and websites’ unsuspecting visitors.
The attacker, Boolka, has been active since at least 2022 and uses SQL injection attacks to implant malicious JavaScript on vulnerable websites. In March 2024, this evolved into developing a new malware delivery platform based on the Browser Exploitation Framework (BeEF) to deliver the BMANAGER malware, which downloads additional modules BMREADER, BMLOG, BMHOOK, and BMBACKUP to enhance its capabilities.
Module overview:
BMANAGER malware extends its functionality through additional modules. These modules enable comprehensive data theft and persistent surveillance of infected systems.
- BMREADER exfiltrates data by sending stolen information stored in the local SQL database to the Command and Control (C2) server.
- BMLOG captures keyboard inputs by logging keystrokes and storing them in the local SQL database.
- BMHOOK tracks application interactions by recording which applications have keyboard focus and storing this data in the local SQL database.
- BMBACKUP exfiltrates specific files by copying them to a temporary directory, reading them in chunks, and sending them to the C2 server.
Outlook:
Following Boolka’s success with BMANAGER, malware campaigns using delivery platforms based on the open-source framework BeEF could increase. Security teams should anticipate more web-based exploitation attempts and prepare for evolving tactics to maintain persistence and evade detection.
Mitigation actions:
Organizations must stay vigilant and proactive in their cybersecurity measures to combat the risks posed by Boolka and similar actors. Implementing robust defenses and monitoring strategies is crucial to protect sensitive data and maintain system integrity.
- Implement traffic analysis tools to monitor HTTP(S) traffic for unusual patterns indicative of malware communication.
- Use web application firewalls (WAFs) to inspect and filter potentially malicious HTTP(S) requests.
- Monitor the Windows Task Scheduler to identify the creation of suspicious tasks and ensure local SQL databases are monitored for unusual activities and unauthorized entries.
Source Material: Group-IB, Boolka Unveiled: From web attacks to modular malware
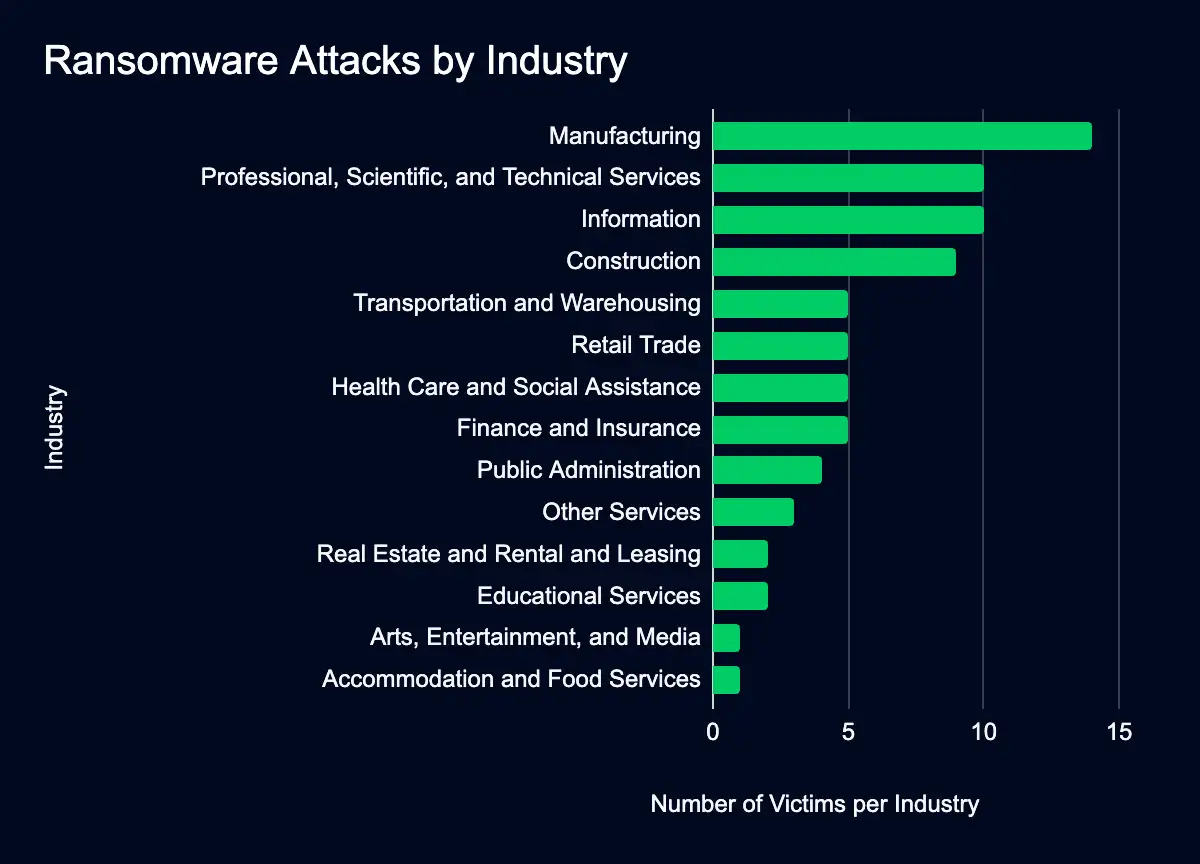
76 Organizations Added to Data Leak Sites in the Past Week
Manufacturing – Professional, Scientific, and Technical Services – Information – Construction
The Rundown
From June 17th through the 23rd, ransomware groups added 76 organizations to data leak sites. Organizations operating in the manufacturing sector are the most listed.
This ransomware activity underscores the escalating threat to organizations worldwide, emphasizing the urgent need for enhanced cybersecurity measures to protect against such attacks.
Industry Impact:
Of the organizations listed, those in the manufacturing, professional services, and information sectors were listed the most.
The concentration of ransomware attacks in critical sectors highlights their attractiveness to attackers, as these industries may be willing to pay large amounts to resolve disruptions.
Industries With the Most New Published Breaches:
- Manufacturing: 14 organizations (18%)
- Professional, scientific, and technical services: 10 (13%)
- Information: 10 (13%)
- Construction: 9 (12%)
Geographic Distribution:
Out of the organizations listed, those headquartered in the United States experienced the highest number of ransomware attacks.
The high number of ransomware attacks targeting U.S.-based organizations reflects the country’s large number of businesses and economic activities, highlighting the need for enhanced cybersecurity measures.
Countries With the Most New Published Breaches:
- United States: 36 organizations (47%)
- United Kingdom: 6 (8%)
- Italy: 4 (5%)
Ransomware groups continue to expand their reach, targeting a wide range of industries and geographies. Organizations must stay vigilant and strengthen their defenses to combat this ongoing menace.
CISA Adds 3 Vulnerabilities to Exploited Catalog
GeoSolutionsGroup JAI-EXT CVE-2022-24816 – Linux Kernel’s nft_object CVE-2022-2586 – Roundcube Webmail CVE-2020-13965
The Rundown
The Cybersecurity and Infrastructure Security Agency (CISA) has flagged three critical vulnerabilities, CVE-2022-24816, CVE-2022-2586, and CVE-2020-13965, as actively exploited in the wild.
These vulnerabilities impact widely used open-source components, posing significant risks of remote code execution and privilege escalation, necessitating urgent action to mitigate potential threats.
Vulnerabilities:
- CVE-2022-24816: A code injection vulnerability in GeoSolutionsGroup JAI-EXT, used by GeoServer, could allow remote code execution via jt-jiffle scripts. Despite ongoing exploitation, details of the attacks remain unclear. The patched version is 1.1.22, with a CISA-recommended fix deadline of July 17, 2024.
- CVE-2022-2586: A use-after-free vulnerability in the Linux Kernel’s nft_object allows local attackers to escalate privileges. Exploited by the ExCobalt cyber espionage group, this vulnerability has been used against Russian targets. Affected systems must be patched by July 17, 2024.
- CVE-2020-13965: A cross-site scripting (XSS) vulnerability in Roundcube Webmail permits data manipulation via malicious XML attachments. Although technical details of the attacks are unknown, exploitation in the wild has been confirmed. The fix is required by July 17, 2024.
Organizations should prioritize patching these vulnerabilities to prevent potential exploits. Monitoring for unusual activity associated with these products is crucial to mitigate risks effectively.
Keep an eye on vendor updates for any new information. To avoid exposure, ensure all relevant systems are patched before the July 17, 2024 deadline.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share