Critical OpenSSH and Fortra FileCatalyst Vulnerabilities Exploited, Chinese APTs Blur Cybercrime Lines, P2Pinfect Botnet Upgraded, TeamViewer Breach Details, Velvet Ant Zero-Day Attack on Cisco, and CISA Updates
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Customer Advisory | PoCs Released for High Severity Vulnerability, CVE-2024-6387, in OpenSSH
- Proof-of-concept Exploit Code Released for Critical Fortra FileCatalyst Workflow Vulnerability
- Chinese APTs Deploy Ransomware, Blurring Cybercrime and Espionage
- P2Pinfect Botnet Updated with Ransomware and Crypto Miner Payloads
- TeamViewer Breach: What We Know So Far
- China-linked Velvet Ant Group Exploits Cisco Nexus Vulnerability CVE-2024-20399 as a Zero-Day
- Latest Additions to Data Leak Sites
- CISA Adds Cisco NX-OS Vulnerability to Known Exploited Vulnerabilities Catalog
PoCs Released for High Severity Vulnerability, CVE-2024-6387, in OpenSSH
Proof-of-Concept Released – OpenSSH CVE-2024-6387 – Unauthenticated Remote Code Execution – All Industries
The Rundown
Several unauthenticated remote code execution (RCE) proof-of-concept exploits have been released for a high-severity vulnerability (CVE-2024-6387, CVSS: 8.1), dubbed “regreSSHion” by Qualys, that impacts OpenSSH servers in glibc-based Linux systems.
The OpenSSH vulnerability CVE-2024-6387 poses a significant threat due to its ability to allow unauthenticated remote code execution.
Due to several PoCs arriving in the threat landscape, the likelihood of exploitation is high, and the potential impacts are severe, necessitating immediate patching and continuous monitoring to prevent possible breaches and ensure system integrity.
- An attacker could execute arbitrary code with the highest privileges, resulting in a complete system compromise, installation of malware, data manipulation, and the creation of backdoors for persistent access.
- It could also facilitate lateral movement, allowing attackers to traverse and exploit other vulnerable systems within the organization.
- Gaining root access could enable attackers to bypass critical security mechanisms to obscure their activities and access to all data on the system, including sensitive or proprietary information that could be stolen or publicly disclosed.
If you have questions or feedback about this intelligence, you can submit them here.
Vulnerability Details:
CVE-2024-6387 is a signal handler race condition vulnerability that allows for unauthenticated remote code execution in OpenSSH on glibc-based Linux systems. This vulnerability is due to changes or updates that were inadvertently reintroduced in October 2020 (OpenSSH 8.5p1) the previously patched CVE-2006-5051.
- OpenSSH versions from 8.5p1 up to, but not including, 9.8p1 are vulnerable.
- OpenSSH versions earlier than 4.4p1 are vulnerable unless they are patched for CVE-2006-5051 and CVE-2008-4109.
- Versions from 4.4p1 up to, but not including, 8.5p1 are not vulnerable due to a transformative patch for CVE-2006-5051.
- OpenBSD systems are unaffected.
But, Qualys points out that this vulnerability is difficult to exploit due to its remote race condition nature, which may require multiple attempts for a successful attack.
- In Qualys’s technical write-up, they stated “it takes 10,000 tries to win the race condition” and can take anywhere from a few hours to a week to obtain a root shell.
- Multiple attempts may cause memory corruption and necessitate overcoming Address Space Layout Randomization (ASLR).
- However, AI and ML may significantly increase the exploitation rate, potentially providing attackers with a substantial advantage in leveraging such security flaws.
Scale of the threat:
Based on searches using Censys and Shodan, Qualys has identified over 14 million potentially vulnerable OpenSSH server instances exposed to the Internet.
- Qualys internal data reveals that approximately 700,000 external internet-facing instances are vulnerable, accounting for 31% of all internet-facing instances with OpenSSH in their global customer base.
Public exploit code:
Within hours of Qualys publishing their discovery and technical details of the vulnerability, Deepwatch identified several proof-of-concept (PoC) for CVE-2024-6387 on GitHub. Even if some of these PoCs do not work, it provides attackers with a detailed guide to exploit the vulnerability.
Read the full advisory here.
Proof-of-concept Exploit Code Released for Critical Fortra FileCatalyst Workflow Vulnerability
Critical Vulnerability – Proof-of-Concept – SQL Injection – Fortra FileCatalyst Workflow CVE-2024-5276 – All Industries
The Rundown
Proof-of-concept exploit code for CVE-2024-5276, a critical SQL injection vulnerability in Fortra FileCatalyst Workflow, is now public.
Why it matters:
Businesses using impacted versions of Fortra FileCatalyst Workflow are at significantly heightened risk. Immediate action is critical to prevent unauthorized data access and manipulation.
- Increased Risk: Public exploit code makes exploitation more likely.
- Potential Damage: Exploitation can lead to admin user creation and data alteration.
- Affected Versions: All versions of FileCatalyst Workflow from 5.1.6 Build 135 and earlier.
The software:
Fortra FileCatalyst Workflow is a managed file transfer solution organizations use to automate and streamline file transfers. It ensures secure, reliable, and accelerated file delivery and is often used in industries requiring large data transfers, such as media, entertainment, and finance.
Exploitation:
An attacker can perform SQLi via the JOBID parameter in various Workflow web application URL endpoints.
- Fortra notes that the Workflow system must have anonymous access enabled for an unauthenticated attacker to exploit this vulnerability. Otherwise, the attacker needs to be authenticated.
- An attacker can not exploit this vulnerability to exfiltrate data.
Outlook:
The public release of this exploit code will likely result in attacks, and potentially ransomware, on Fortra FileCatalyst Workflow. While exploitation can allow an attacker to create admin accounts, the inability to exfiltrate data could make this vulnerability less attractive.
Actions:
FileCatalyst Workflow users should upgrade to 5.1.6 build 139 or later.
Source Material: Fortra, SQL Injection Vulnerability in FileCatalyst Workflow 5.1.6 Build 135 (and earlier) and Tenable, Fortra FileCatalyst Workflow Unauthenticated SQLi
Chinese APTs Deploy Ransomware, Blurring Cybercrime and Espionage
Chinese Threat Actor – Cyberespionage – Ransomware – Credential Theft – Lateral Movement – Privilege Escalation – ChamelGang – APT41 – Ransomware – Remote Access Trojan (RAT) – CatB Ransomware – BeaconLoader – Cobalt Strike – SweetPotato – SharpToken – FRP (Fast Reverse Proxy) – Neo-reGeorg – China Chopper – miPing – Manufacturing – Critical Infrastructure – Professional, Scientific, and Technical Services – Health Care and Social Assistance – Transportation and Warehousing – Educational Services – Financial and Insurance Services – Public Administration
The Rundown
Chinese APT groups increasingly use ransomware to target critical infrastructure sectors, complicating attribution and enhancing their cyberespionage operations.
Why it matters:
Chinese APT groups’ use of ransomware can lead to significant financial and operational disruptions. It also masks their true intent, making it harder to defend against cyberespionage.
SentinelLabs and Recorded Future tracked two ransomware activity clusters targeting global government and critical infrastructure sectors between 2021 and 2023. One cluster involves ChamelGang, a suspected Chinese APT group, while the other uses BestCrypt and BitLocker, possibly linked to Chinese and North Korean APT groups.
While ransomware is commonly associated with cybercrime, its use by APT groups highlights a strategic blend of financial gain and cyberespionage, complicating response efforts.
ChamelGang has been linked to multiple high-profile intrusions, including attacks on the Presidency of Brazil and the All India Institute of Medical Sciences. Their use of publicly available tools and malware aids in privilege escalation and data exfiltration, making them a formidable threat.
From 2021 to 2023, 37 organizations across various sectors, primarily in the United States, were targeted using BestCrypt and BitLocker. These attacks involved credential theft, reconnaissance, and lateral movement using the RDP protocol, followed by data encryption.
Outlook:
Cyberespionage threat groups will likely continue using ransomware to obscure their true motives and complicate attribution. This tactic allows them to cause disruptions while masking their espionage activities under the guise of cybercrime.
Actions:
To combat these sophisticated attacks, implementing robust cybersecurity measures is crucial to mitigate the risks posed by these ransomware attacks.
- Implement regular employee training.
- Implement continuous network monitoring.
- Enforce multi-factor authentication.
- Regularly update and patch systems.
- Segment critical networks.
- Deploy advanced threat detection tools.
- Ensure you have a robust backup and restore process.
Source Material: SentinelOne, Chamelgang & Friends | Cyberespionage Groups Attacking Critical Infrastructure with Ransomware
P2Pinfect Botnet Updated with Ransomware and Crypto Miner Payloads
Malware – Botnet – Ransomware – Cryptominer – Peer-to-Peer Botnet – Usermode Rootkit – P2Pinfect – Redis Replication Abuse – SSH – All Industries
The Rundown
P2Pinfect, a peer-to-peer botnet, now deploys ransomware and crypto miner payloads, posing new threats to Redis instances.
- Redis (Remote Dictionary Server) is an open-source, in-memory data structure server that’s used as a cache or database.
The new ransomware and crypto miner payloads in P2Pinfect amplify the threat to Redis instances, forcing security teams to urgently enhance defenses to protect against severe data breaches and operational disruptions.
- The ransomware payload locks Redis’s critical files, leading to disruptions and the potential for data loss.
- The cryptominer payload degrades system performance, impacting business operations.
- Redis replication features enable rapid propagation across networks.
Current activity:
The current state of P2Pinfect poses a multifaceted threat to Redis instances:
- Redis Exploitation: Redis’s replication features are used to spread infections.
- Ransomware: Locks critical files, demanding 1 XMR for decryption.
- Cryptominer: Drains system resources, impacting operational efficiency.
- SSH Manipulation: Alters SSH configurations to gain persistent access.
- Evasion Techniques: Implements usermode rootkit and dynamic obfuscation to avoid detection.
Outlook:
Security teams should prepare for further evolutions of the P2Pinfect botnet:
- Enhanced Evasion: Expect more sophisticated obfuscation and persistence mechanisms.
- Broader Targets: The botnet may expand to cloud environments and containerized applications.
- Increased Payload Diversity: Potential for new ransomware and cryptominer variants to emerge.
- Enhanced Distribution: Incremental improvements in SSH propagation could enhance its reach.
Mitigation actions:
To mitigate the risks posed by P2Pinfect, security teams should:
- Harden Redis Instances: Implement strict access controls and regularly update configurations.
- Monitor for Indicators: Watch for unusual activity, such as unexpected SSH configurations or high CPU usage.
- Deploy Endpoint Protection: Use advanced security tools to detect and block ransomware and cryptominer activities.
- Conduct Regular Audits: Regularly review system logs and network traffic for signs of infection.
Source Material: Cado Security, From Dormant to Dangerous: P2Pinfect Evolves to Deploy New Ransomware and Cryptominer
TeamViewer Breach: What We Know So Far
TeamViewer Compromise – Data Theft – Account Compromise – APT29 – Midnight Blizzard – Russia
The Rundown
TeamViewer’s recent security breach on June 26 underscores the persistent threat of such attacks and highlights the critical need for robust security measures and swift incident response.
Emphasizing the lessons learned, companies should implement robust security measures and maintain a swift incident response capability to protect sensitive information and ensure operational continuity.
TeamViewer is software used for remote access and remote control of computers and other devices. It was initially released in 2005 and has expanded its functionality over time. TeamViewer is proprietary software that requires registration and is free for non-commercial use. It has been installed on more than 2 billion devices.
What is known:
On June 26, 2024, TeamViewer detected an irregularity in its internal corporate IT environment. TeamViewer immediately activated its response team and began collaborating with Microsoft.
- TeamViewer and Microsoft attributed the attack to APT29/Midnight Blizzard.
- APT29/Midnight Blizzard leveraged a compromised employee account to copy employee directory data, which included names, corporate contact information, and encrypted employee passwords from the internal corporate IT environment.
- Due to TeamViewer’s network segmentation strategies, the threat actors were confined to the internal corporate IT network, which is separated from the product, the TeamViewer connectivity platform, or any customer data.
- Collaborating with Microsoft, TeamViewer mitigated the risk associated with the encrypted passwords.
- TeamViewer has implemented hardened authentication procedures and is rebuilding the IT environment.
APT29/Midnight Blizzard is a threat group attributed to Russia’s Foreign Intelligence Service (SVR).
- Operated since 2008, often targeting government networks in Europe and NATO member countries, research institutes, and think tanks.
- They reportedly compromised the Democratic National Committee starting in the summer of 2015.
Actions:
Organizations should monitor for emerging details about the breach from TeamViewer’s Trust Center, especially if new findings reveal the attack’s technical information, such as the threat actors’ behavior.
Lessons learned:
Security teams should ensure robust credential management practices, including regular updates and multi-factor authentication.
- Ensure networks are segregated, keeping all servers, networks, and accounts strictly separate to help prevent unauthorized access and lateral movement between different environments.
- Implement hardened and robust authentication procedures.
Source Material: TeamViewer | Alternative Sources: The Record 1, 2, & 3
China-linked Velvet Ant Group Exploits Cisco Nexus Vulnerability CVE-2024-20399 as a Zero-Day
Chinese Threat Actor – Vulnerability exploitation – Remote Command Execution – Malware Deployment – File Uploads – Cisco Nexus CVE-2024-20399 – Velvet Ant – All Industries
The Rundown
A sophisticated China-nexus threat group, Velvet Ant, has exploited a vulnerability, CVE-2024-20399, in Cisco Nexus devices as a zero-day, deploying custom malware, which enabled them to gain remote access, upload additional files, and execute code.
- Cisco’s advisory states that in April 2024, they became aware of attempted exploitation of this vulnerability in the wild.
- Velvet Ant’s exploitation of CVE-2024-20399 as a zero-day implies that they exploited this vulnerability in April 2024 or earlier.
- The custom malware that enabled remote access could potentially be a remote access trojan or backdoor.
Velvet Ant’s ability to exploit CVE-2024-20399 underscores the ongoing threat posed by sophisticated adversaries who can leverage unknown vulnerabilities for espionage and prolonged network access. This incident highlights the critical need for timely patching and robust network security measures.
What happened:
The Velvet Ant threat group exploited the vulnerability now tracked as CVE-2024-20399 in Cisco Nexus devices to execute commands on the underlying operating system.
- This led to deploying previously unknown custom malware, remote access, file uploads, and code execution.
The group:
Velvet Ant is known for maintaining a prolonged presence in victims’ on-premises networks, sometimes for up to three years, primarily for espionage purposes.
- They establish multiple footholds within victims’ environments and pivot to others once one is discovered.
- A previous persistence mechanism was a legacy F5 BIG-IP appliance, which was leveraged as an internal Command and Control (C&C) device.
Vulnerability details:
This vulnerability affects several Cisco products, including various Nexus series switches running older NX-OS versions.
- Exploiting CVE-2024-20399 requires valid administrator-level credentials and network access to the Nexus switch.
- Cisco NX-OS Software releases 9.3(5) and later are not affected, except for specific platforms listed in the advisory.
Risks & impacts:
The combination of Velvet Ant’s capabilities and the identified vulnerability necessitates immediate and comprehensive defensive measures.
- Likelihood: Roughly even chance. The need for administrator-level credentials to exploit CVE-2024-20399 reduces the probability but may increase the potential for credential theft.
- Impact: Severe. Velvet Ant’s activities lead to persistent access, network compromise, data exfiltration, and disruption of critical services.
Outlook:
Velvet Ant is expected to continue exploiting CVE-2024-20399 and similar vulnerabilities. Their tactics, techniques, and procedures (TTPs) may see incremental enhancements to evade detection and maintain access within compromised networks. The group may also exploit other entry points within network infrastructure, leveraging their comprehensive understanding of target environments.
- Anticipate additional attacks targeting unpatched Cisco Nexus devices and legacy systems.
- Velvet Ant may refine their custom malware as more information is released.
- Velvet Ant will likely adopt more advanced methodologies to maintain and expand their footholds within target networks.
- They may develop more advanced persistence mechanisms and malware variants and diversify their attack vectors, potentially exploiting new vulnerabilities as they are discovered.
Mitigation actions:
To counter threats related to CVE-2024-20399 and similar vulnerabilities, implement the following strategies:
- Update systems promptly: Apply Cisco’s software updates that address CVE-2024-20399 immediately.
- Restrict administrative access: Use Privileged Access Management (PAM) solutions or dedicated, hardened jump servers with multi-factor authentication (MFA).
- Centralize user management: Use TACACS+ and Cisco ISE to enhance security and ensure local user accounts are not scattered.
- Enforce strong password policies: Ensure administrative users have complex, securely stored passwords and consider using a Privileged Identity Management (PIM) solution.
- Limit outbound internet access: Restrict switches from initiating outbound connections and implement strict firewall rules.
Source Material: Sygnia, China-Nexus Threat Group ‘Velvet Ant’ Exploits Cisco Zero-Day (CVE-2024-20399) to Compromise Nexus Switch Devices – Advisory for Mitigation and Response and Cisco, Cisco NX-OS Software CLI Command Injection Vulnerability
Latest Additions to Data Leak Sites
Manufacturing – Information – Health Care and Social Assistance – Finance and Insurance – Professional, Scientific, and Technical Services
The Rundown
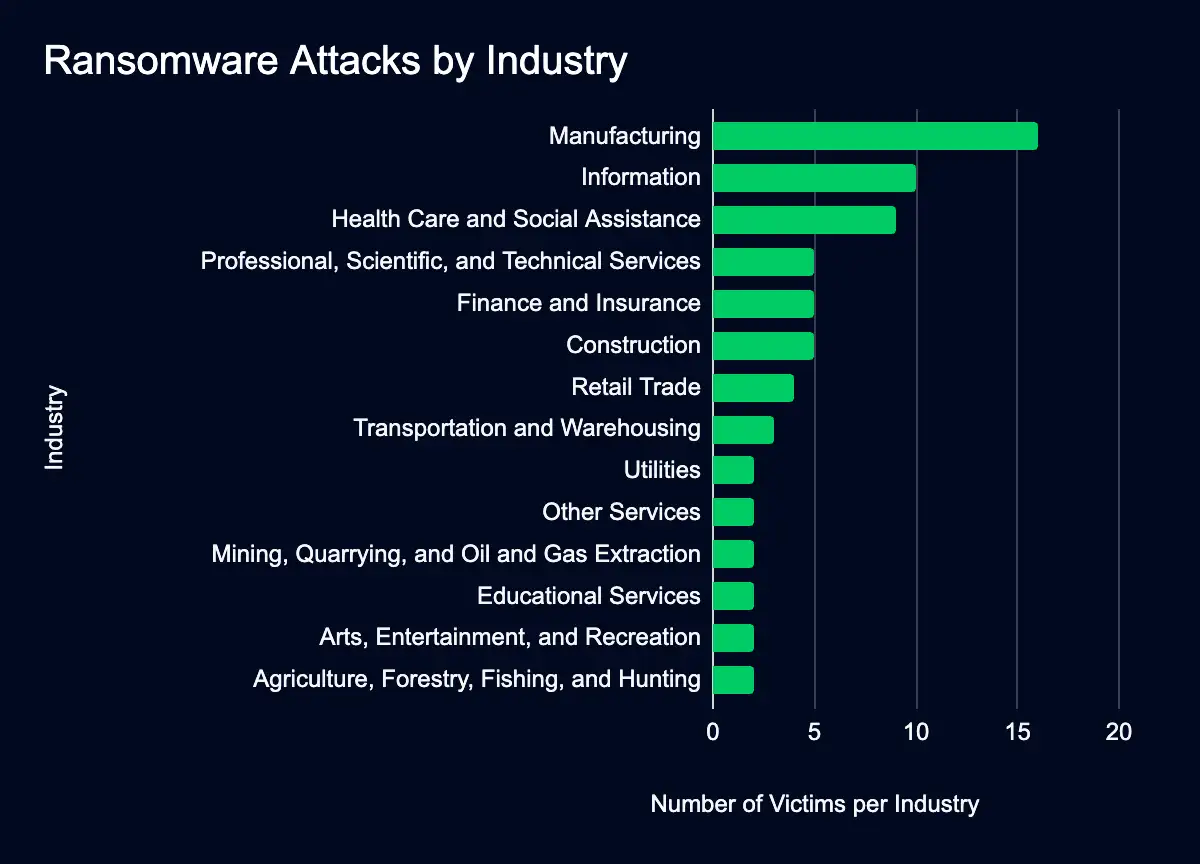
From June 24th through July 1st, ransomware groups added 69 organizations to data leak sites. For the seventh week, monitored leak sites listed organizations in the manufacturing sector the most.
This ransomware activity underscores the escalating threat to organizations worldwide, emphasizing the urgent need for enhanced cybersecurity measures to protect against such attacks.
Industry Impact:
Of the organizations listed, those in the Manufacturing, Information, Health Care, and Social Assistance sectors were listed as the most impacted.
The concentration of ransomware attacks in critical sectors highlights their attractiveness to attackers, as these industries may be willing to pay large amounts to resolve disruptions.
By the numbers:
- Manufacturing: 16 organizations (22%)
- Information: 10 (14%)
- Health Care and Social Assistance: 9 (12%)
Geographic Distribution:
Out of the organizations listed, those headquartered in the United States experienced the highest number of ransomware attacks.
The high number of ransomware attacks targeting U.S.-based organizations reflects the country’s large number of businesses and economic activities, highlighting the need for enhanced cybersecurity measures.
By the numbers:
- United States: 29 organizations (39%)
- Italy: 5 (7%)
- Germany: 4 (5%)
RansomHub and Black Suit led this week, with 13 new organizations listed on their leak sites. Following RansomHub and Black Suit, Black Basta, Dark Vault, Cloak, and Arcusmedia contributed to new additions.
By the numbers:
- RansomHub and Black Suit: 13 organizations each (18%)
- Black Basta: 6 (8%)
- Dark Vault, Cloak, and Arcusmedia: 4 each (5%)
Ransomware groups continue to expand their reach, targeting a wide range of industries and geographies. Organizations must stay vigilant and strengthen their defenses to combat this ongoing menace.
CISA Adds Cisco NX-OS Vulnerability to Known Exploited Vulnerabilities Catalog
Cisco NX-OS CVE-2024-20399
The Rundown
CISA added the high-severity vulnerability CVE-2024-20399 in Cisco NX-OS, which Cisco uses in its Nexus switches, to its Known Exploited Vulnerabilities (KEV) catalog. This addition follows the disclosure that the Chinese Nexus threat group Velvet Ant exploited the vulnerability as a zero-day.
The exploitation of CVE-2024-20399 underscores the ongoing threat posed by sophisticated adversaries who can leverage unknown vulnerabilities. This incident highlights the critical need for timely patching and robust network security measures.
For further details on the exploitation of this vulnerability, see our report titled “China-linked Velvet Ant Group Exploits Cisco Nexus Vulnerability CVE-2024-20399 as a Zero-Day.”
The KEV catalog is a valuable resource for organizations. It enables them to prioritize remediation efforts for the subset of vulnerabilities causing immediate harm based on adversary activity.
CISA strongly recommends that all organizations review and monitor the KEV catalog and prioritize the remediation of the listed vulnerabilities to reduce the likelihood of compromise by known threat actors. CISA recommends organizations implement mitigations for CVE-2024-20399 by July 23rd.
Additionally, organizations should incorporate the KEV catalog into their vulnerability management framework and consider using automated vulnerability and patch management tools that automatically integrate and flag or prioritize KEV vulnerabilities.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share