Medusa Ransomware Evolves, Tomcat RCE Exploited in the Wild, and CISA Warns of Newly Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Medusa Ransomware: Tactics, Operational Evolution, and Strategic Threats in the RaaS Landscape
- Weaponizing PUT: Tomcat CVE-2025-24813 Remote Code Execution Under Active Exploitation
- Ransomware and Data Extortion Trends (Mar. 10 – 16)
- Exploited Vulnerabilities in Juniper, Apple, Github, Fortinet, SAP NetWeaver, NAKIVO, and Edimax Added to CISA’s Catalog – Immediate Mitigation Recommended
Medusa Ransomware: Tactics, Operational Evolution, and Strategic Threats in the RaaS Landscape
The Rundown
Medusa, a ransomware-as-a-service (RaaS) operation active since June 2021, has compromised over 300 victims across healthcare, education, legal, technology, and manufacturing sectors. Its affiliates use phishing and vulnerability to gain access, leverage lateral movement and data exfiltration techniques, and execute data encryption and extortion schemes.
Medusa’s transition from a closed operation to a RaaS model increases Medusa’s threat and amplifies ransomware risks across industries. Its adoption of sophisticated tools, credential theft, and direct victim engagement, including potential triple extortion tactics, escalates the threat landscape.
Medusa affiliates leverage initial access brokers (IABs) and exploit public-facing applications to infiltrate networks, often using phishing campaigns and credential theft. Once inside, they employ “living off the land” techniques with tools like PowerShell, WMI, and legitimate remote access software like AnyDesk and ConnectWise to evade detection. Medusa affiliates use PsExec to execute batch scripts that modify firewall and registry settings, facilitating unrestricted RDP access for lateral movement. Mimikatz is used to extract credentials, and Rclone enables large-scale data exfiltration before encryption.
The ransomware encryptor (gaze.exe) is deployed through PsExec or PDQ Deploy, terminating security, database, and backup services before encrypting files using AES-256 and appending the .medusa extension. Victims receive ransom notes demanding communication via Tor or Tox, with a 48-hour deadline before data leaks begin.
Medusa’s leak site enables public shaming, ransom tracking, and direct cryptocurrency payments, offering victims an option to delay data release by paying $10,000 per additional day. Notably, some victims report fraudulent second ransom demands from actors claiming the initial payment was stolen—suggesting possible triple extortion schemes.
Mitigation recommendations include patching vulnerabilities, enforcing least privilege and multi-factor authentication, restricting RDP and scripting tools, and deploying advanced monitoring for suspicious command execution and credential access. Organizations should implement robust endpoint detection and response (EDR), network segmentation, and proactive threat-hunting strategies to mitigate Medusa’s impact.
Source Material: CISA
Weaponizing PUT: Tomcat CVE-2025-24813 Remote Code Execution Under Active Exploitation
The Rundown
A newly discovered critical security flaw (CVE-2025-24813) in Apache Tomcat, a widely used web server technology. This vulnerability allows attackers to take control of a Tomcat server remotely by sending a simple web request, putting business systems and sensitive data at risk. Exploitation of this flaw has already been seen in real-world attacks, making it a serious concern for organizations relying on Tomcat for their applications.
For businesses, this means a potential breach could happen quickly and with minimal effort from attackers. If exploited, the vulnerability could lead to unauthorized access, service disruptions, data theft, or further compromises within the organization’s IT environment. Since Tomcat servers often host critical business applications, the impact could extend to customer trust, regulatory compliance, and financial losses.
The article stresses the need for immediate action. Businesses are advised to update their Tomcat servers to patched versions and review their security practices. Timely mitigation reduces exposure to this high-risk threat and protects vital digital assets.
Source Material: Wallarm
Ransomware and Data Extortion Trends (Mar. 10 – 16)
The Rundown
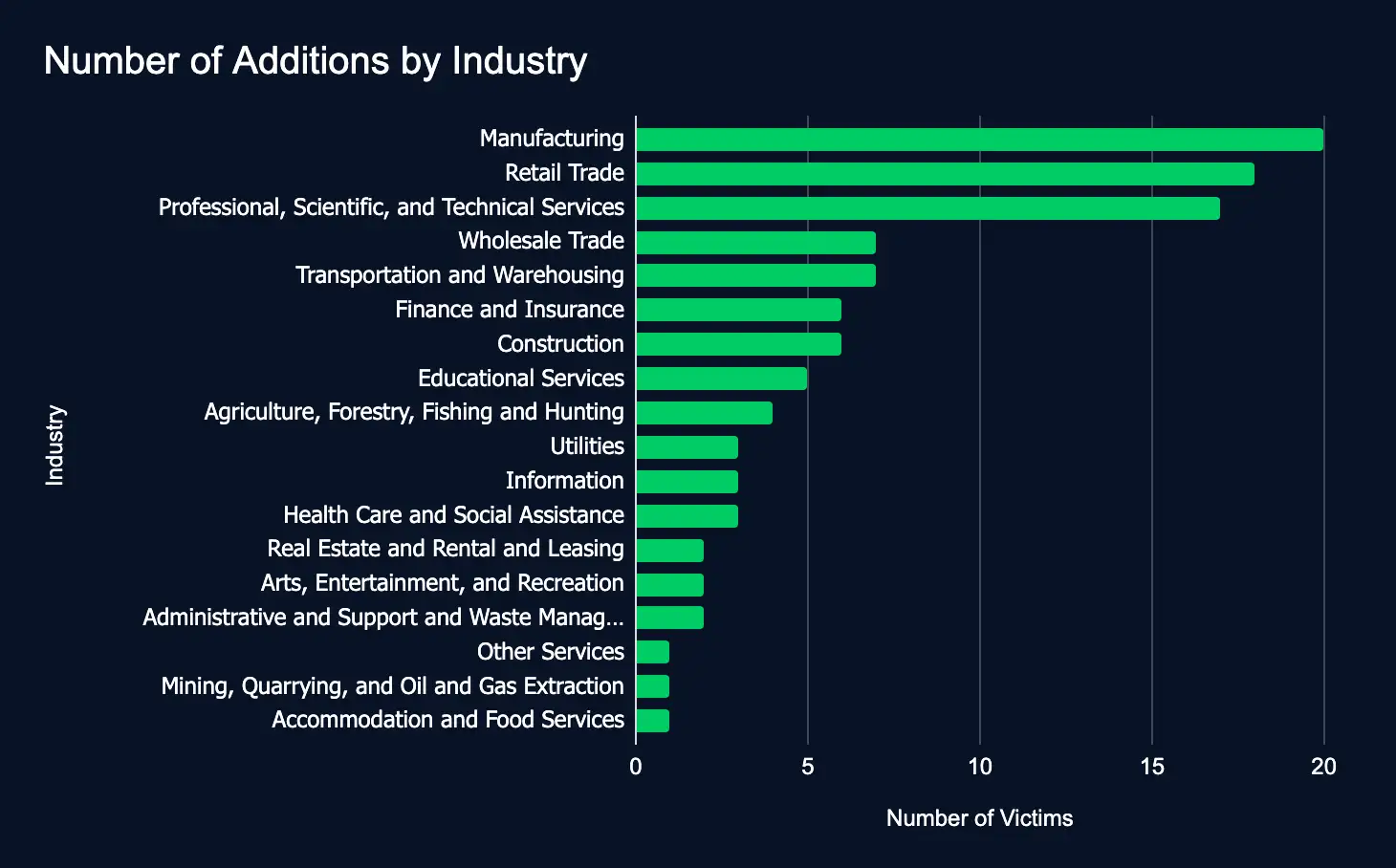
Ransomware and data extortion activity dropped between March 10 – 16, with a 45% decrease in listed organizations compared to the previous week.
This decline reinforces the unpredictable nature of ransomware activity. It’s almost certainly not a trend that will continue in the future. Therefore, with new additions listing organizations in nearly all industries, organizations must strengthen cybersecurity measures to bolster cyber resilience.
In the reporting time frame, 108 organizations across 18 industries were listed on 23 ransomware and data extortion leak sites, marking a decrease from the previous week’s 197 victims.
Key Trends:
- Most affected industries:
- Manufacturing
- Retail Trade
- Professional, Scientific, and Technical Services
- Most affected countries:
- United States
- Canada
- Italy
- Most active leak sites:
- Akira
- Clop
- Lynx
Exploited Vulnerabilities in Juniper, Apple, Github, Fortinet, SAP NetWeaver, NAKIVO, and Edimax Added to CISA’s Catalog
The Rundown
Between March 13th and 19th, 7 critical vulnerabilities affecting Juniper Junos OS, Apple Multiple Products, Github Action, Fortinet FortiOS and FortiProxy, SAP NetWeaver, NAKIVO Backup and Replication, and Edimax IC-7100 IP Camera products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share