RansomHub Deploys Betruger Backdoor, Oracle Cloud Data Leak Raises Concerns, and CISA Flags New Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- RansomHub’s New Weapon: Betruger Backdoor Exposed
- Oracle Cloud Security Scare: 140K Tenants Allegedly Affected in Data Leak
- Ransomware and Data Extortion Trends (Mar. 17 – 23)
- Exploited Vulnerabilities in GitHub Action Reviewdog and Sitecore CMS and Experience Platform (XP) Products Added to CISA’s Catalog
RansomHub’s New Weapon: Betruger Backdoor Exposed
The Rundown
RansomHub has been identified using a new, custom backdoor named Betruger to bolster its ransomware operations. This backdoor provides attackers with a range of capabilities, such as stealing sensitive data and executing remote commands on compromised systems. Its design allows attackers to maintain persistent access to targeted networks, making it a crucial tool in RansomHub’s cyberattacks.
The Betruger backdoor is highly adaptable, allowing it to be used for various malicious activities based on the attackers’ goals. Its modular nature helps it evade detection and stay undetected for long periods. This flexibility increases the complexity and potential impact of RansomHub’s attacks, as the backdoor can adjust to specific situations.
Security experts are concerned about the evolving nature of ransomware attacks, with groups like RansomHub using more advanced techniques. They stress the importance of organizations enhancing their security measures to defend against such persistent and sophisticated threats. Vigilant monitoring and proactive defense strategies are essential to counter these emerging risks.
As ransomware tactics continue to evolve, experts warn that organizations must stay ahead of the curve by strengthening their cybersecurity posture. The deployment of advanced tools like Betruger signals a growing sophistication in cybercriminal activity. Continuous vigilance and improved threat detection are necessary to prevent breaches and minimize the impact of such attacks.
Source Material: Symantec
Oracle Cloud Security Scare: 140K Tenants Allegedly Affected in Data Leak
The Rundown
A massive cybersecurity incident has surfaced involving Oracle Cloud, with claims that a supply chain hack has led to the exfiltration of 6 million records affecting over 140,000 tenants. Reports from CloudSEK indicate that sensitive data, including user credentials and corporate information, has been put up for sale on underground forums. The breach allegedly exploited vulnerabilities in Oracle Cloud’s federated Single Sign-On (SSO) mechanism, allowing attackers to gain unauthorized access to multiple accounts and data repositories. If confirmed, this incident could be one of the largest cloud-based supply chain attacks in recent history.
However, Oracle Cloud has firmly denied the allegations, refuting CloudSEK’s findings and insisting that no breach of their infrastructure has occurred. In response to CloudSEK’s follow-up analysis, Oracle stated that the security of its cloud services remains intact and that no evidence supports claims of a widespread data compromise. Meanwhile, cybersecurity firm Sygnia has provided an independent assessment, suggesting that while an incident affecting federated SSO authentication was observed, its direct connection to the alleged data breach remains uncertain.
This conflicting information has fueled further debate within the cybersecurity community, with experts calling for greater transparency from both Oracle and the researchers investigating the incident. If the breach is validated, it would raise significant concerns about cloud security, third-party integrations, and the broader implications for enterprises relying on Oracle Cloud. As the situation unfolds, affected organizations are urged to strengthen their security posture, monitor for potential data leaks, and seek further clarification from Oracle regarding the alleged breach.
Source Material: CloudSek, CloudSek-Part2
Ransomware and Data Extortion Trends (Mar. 17 – 23)
The Rundown
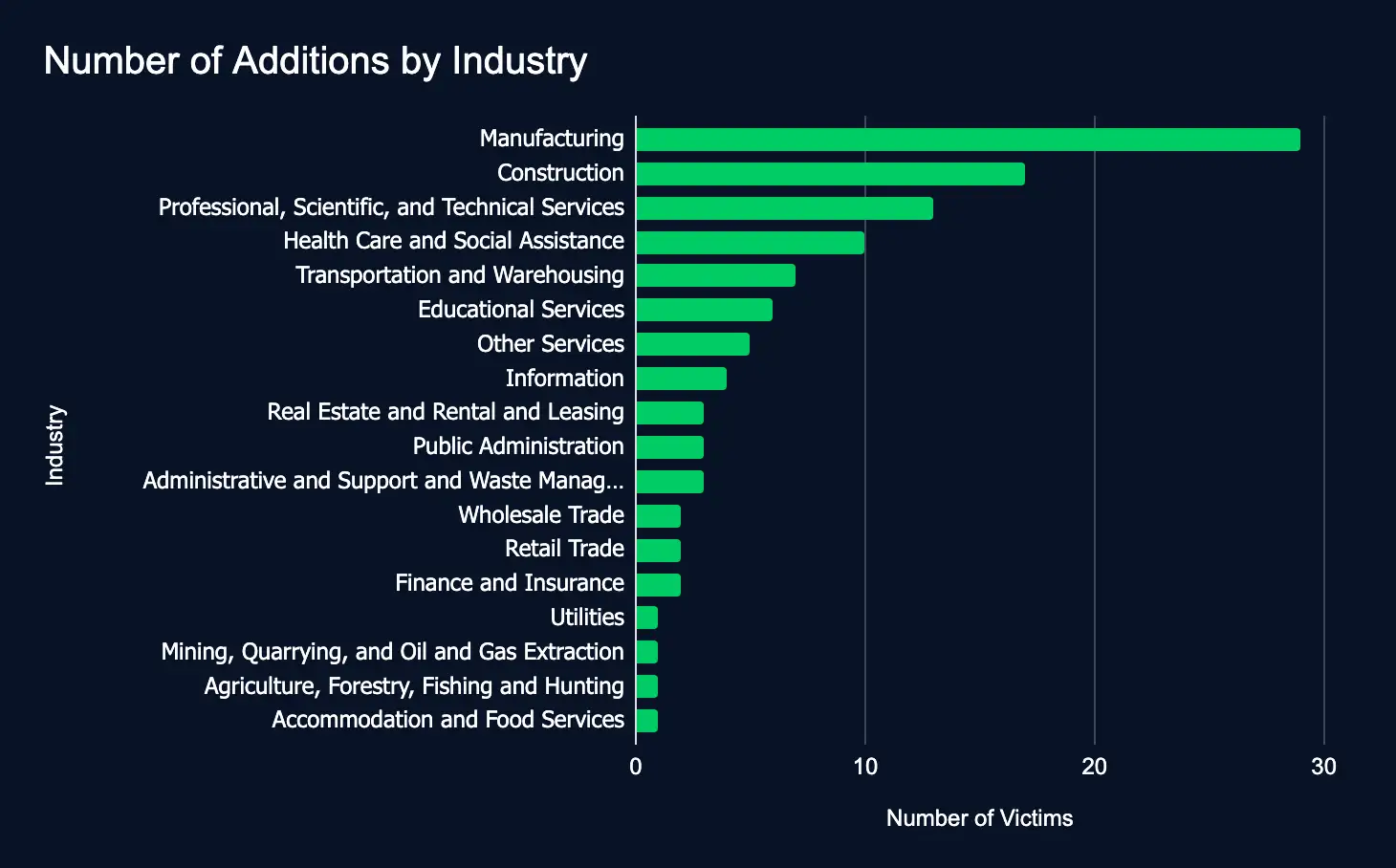
Ransomware and data extortion activity dropped between March 17 – 23, with a 2% increase in listed organizations compared to the previous week.
The slight increase in new additions, 2 above the previous week, shows the steady operational nature of ransomware activity against organizations. As new additions include organizations across almost every industry, businesses must enhance their cybersecurity measures to improve overall cyber resilience.
In the reporting time frame, 110 organizations across 18 industries were listed on 24 ransomware and data extortion leak sites, marking a slight increase from the previous week’s 108 victims.
Key Trends:
- Most affected industries:
- Manufacturing
- Construction
- Professional, Scientific, and Technical Services
- Most affected countries:
- United States
- Canada
- Brazil
- Most active leak sites:
- Ransomhub
- killsecurity
- Akira
Exploited Vulnerabilities in GitHub Action Reviewdog and Sitecore CMS and Experience Platform (XP) Products Added to CISA’s Catalog – Immediate Mitigation Recommended
The Rundown
Between March 20th and 26th, 3 critical vulnerabilities affecting products GitHub Action Reviewdog and Sitecore CMS and Experience Platform (XP) were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly identified vulnerabilities underscore significant risks for organizations relying on widely used technologies. With state-sponsored and cybercriminal attackers potentially targeting these flaws, prompt action will be essential to mitigate exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share