Weaver Ant Espionage Tactics Unveiled, Qilin Ransomware Targets MSPs via ScreenConnect, and CISA Flags New Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Covert Intrusions: How Weaver Ant (China-nexus) Exploits Networks for Espionage
- Qilin Ransomware Affiliates Exploit ScreenConnect in Targeted Cyberattacks on MSPs
- Ransomware and Data Extortion Trends (Mar. 24 – 30)
- Exploited Vulnerabilities in Apache Tomcat, Cisco Smart Licensing, and Google Chromium Mojo Products Added to CISA’s Catalog
Covert Intrusions: How Weaver Ant (China-nexus) Exploits Networks for Espionage
The Rundown
Weaver Ant is a newly identified China-nexus advanced persistent threat (APT) group that has been conducting a sophisticated cyber espionage campaign against an unnamed Asian telecommunications company for over four years. Discovered by Sygnia, this threat actor employed advanced techniques to infiltrate, navigate, and maintain a persistent presence within the targeted network, enabling continuous access to sensitive data.
One of Weaver Ant’s primary methods involved the use of web-shell tunneling, creating a covert command-and-control network within the victim’s infrastructure. By linking multiple web shells, such as the China Chopper variant and a custom-built web shell named INMemory, they routed traffic across different network segments, facilitating stealthy and resilient operations. Additionally, they leveraged compromised Zyxel CPE home routers as entry points, using these devices as operational relay boxes to proxy traffic and conceal their activities.
Weaver Ant’s tactics included exploiting SMB shares and high-privileged accounts with static passwords to move laterally within the network. They employed NTLM hashes for authentication, allowing them to maintain a low profile while mapping out the network environment and accessing internal servers through web-accessible gateways. Their ability to adapt to the evolving network environment and maintain continuous access to compromised systems underscores their sophistication and stealthiness.
Source Material: Sygnia
Qilin Ransomware Affiliates Exploit ScreenConnect in Targeted Cyberattacks on MSPs
The Rundown
In January 2025, a Managed Service Provider (MSP) administrator was targeted by a sophisticated phishing email that mimicked an authentication alert for their ScreenConnect Remote Monitoring and Management (RMM) tool. This deceptive email led the administrator to a counterfeit ScreenConnect login page, where their credentials and multi-factor authentication (MFA) inputs were intercepted by attackers. Consequently, the cybercriminals gained unauthorized access to the MSP’s ScreenConnect system, enabling them to deploy ransomware attacks on the MSP’s clientele.
This breach was part of a broader campaign by affiliates of the Qilin ransomware group, also known as STAC4365. This group has a history of employing similar phishing tactics since late 2022, using fake domains that closely resemble legitimate ScreenConnect URLs. By leveraging adversary-in-the-middle (AitM) techniques, they effectively bypass MFA protections, allowing them to infiltrate systems and execute ransomware attacks.
Qilin operates a Ransomware-as-a-Service (RaaS) model, recruiting affiliates through Russian-language cybercrime forums. They exert pressure on victims by hosting leaked data on platforms like “WikiLeaksV2,” accessible via the Tor network and the open internet. This incident underscores the critical need for businesses to enhance their cybersecurity measures, particularly in safeguarding against phishing attacks and ensuring the integrity of their remote management tools.
Source Material: Sophos
Ransomware and Data Extortion Trends (Mar. 24 – 30)
The Rundown
Ransomware and data extortion activity slightly dropped between March 24 – 30, with a 8% decrease in listed organizations compared to the previous week.
The small decline in new ransomware victims—8 fewer than the previous week—reflects the constantly shifting nature of ransomware operations targeting organizations. Since these attacks span nearly every industry, businesses must strengthen their cybersecurity strategies to bolster overall resilience against evolving threats..
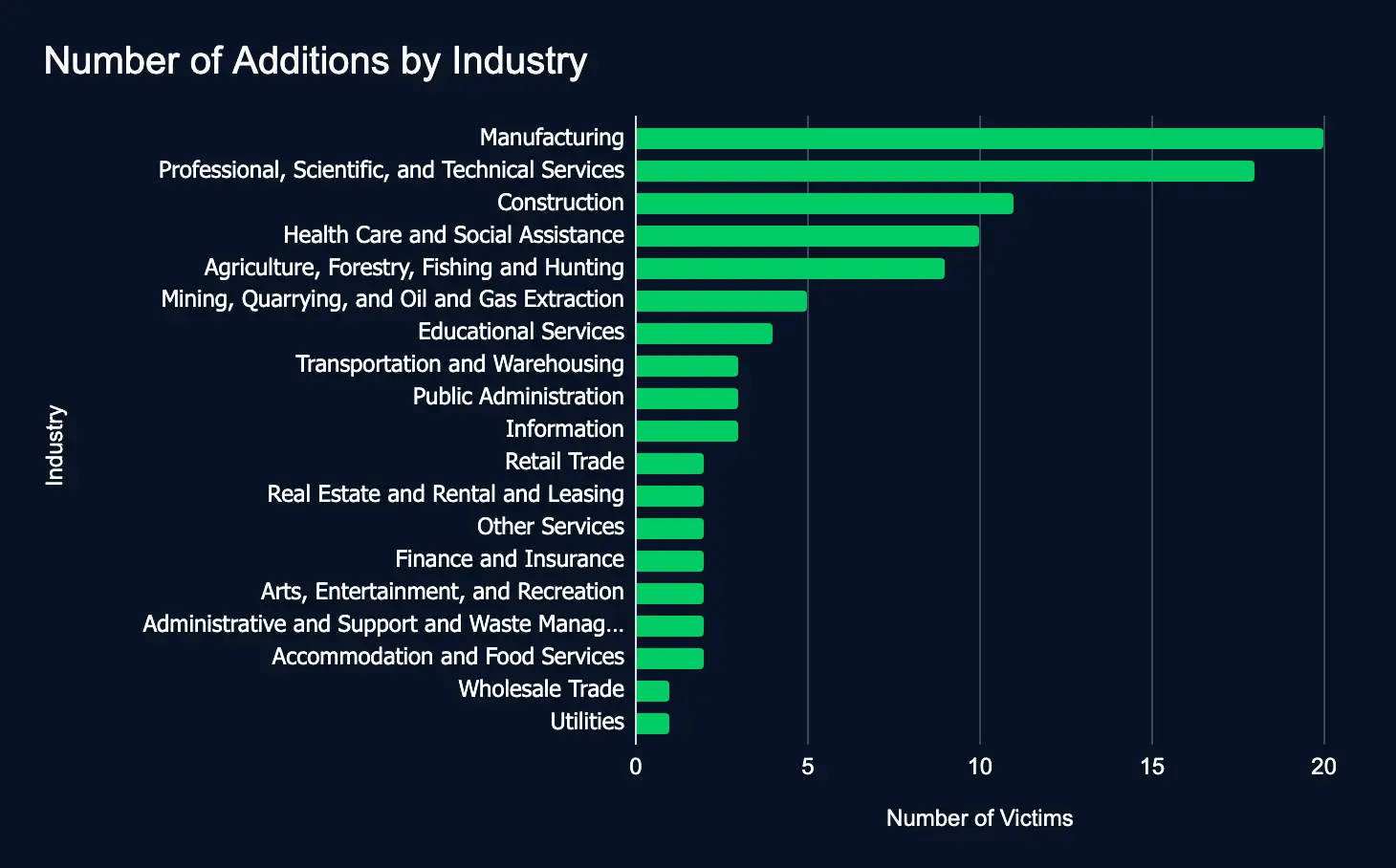
In the reporting time frame, 102 organizations across 19 industries were listed on 18 ransomware and data extortion leak sites, marking a slight decrease from the previous week’s 110 victims.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Construction
- Most affected countries:
- United States
- Canada
- Brazil
- Most active leak sites:
- Ransomhub
- Qilin
- Akira
Exploited Vulnerabilities in Apache Tomcat, Cisco Smart Licensing, and Google Chromium Mojo Products Added to CISA’s Catalog
The Rundown
Between March 27th and April 2nd, 3 critical vulnerabilities affecting products Apache Tomcat, Cisco Smart Licensing, and Google Chromium Mojo products were added to CISA’s Known Exploited Vulnerabilities catalog. If left unpatched, these vulnerabilities could leave organizations vulnerable to cyberattacks.
These newly discovered vulnerabilities highlight critical risks for organizations dependent on widely used technologies. Given the potential targeting by state-sponsored and cybercriminal actors, swift action is crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share