Attackers Exploit IoT for Ransomware, RMM Tools Become a Prime Target, and CISA Flags New Exploited Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Targeting IoT: Attackers Compromise Webcam to Bypass EDR and Spread Ransomware
- Remote Monitoring and Management (RMM) Tooling: Increasingly Attackers’ First Choice
- Ransomware and Data Extortion Trends (Mar. 3 – 9)
- Exploited Vulnerabilities in Microsoft, Ivanti, Advantive Added to CISA’s Catalog – Immediate Mitigation Recommended
Targeting IoT: Attackers Compromise Webcam to Bypass EDR and Spread Ransomware
The Rundown
S-RM identified a ransomware attack in which the attacker bypassed an Endpoint Detection and Response (EDR) solution by exploiting an unsecured webcam, leveraging it to deploy Akira ransomware to other servers.
This attack highlights a critical blind spot in cybersecurity defenses—unsecured Internet of Things (IoT) devices can serve as alternative attack vectors to bypass enterprise security measures, enabling lateral movement and ransomware deployment.
This attack demonstrates how cybercriminals can leverage non-traditional endpoints like IoT devices to bypass security controls and execute ransomware attacks. In this case, the attacker compromised an externally facing remote access solution to establish initial access and then deployed AnyDesk.exe to maintain persistence. After identifying a Windows server protected by an EDR solution, the attacker pivoted to an unprotected webcam running a lightweight Linux OS.
The attacker likely leveraged the webcam’s command-line interface (CLI) to execute a Linux-based variant of Akira ransomware, facilitating ransomware delivery to other networked systems via the Server Message Block (SMB) protocol.
This incident underscores the urgent need for organizations to reassess the security posture of their IoT devices. Many of these devices operate without security solutions, making them ideal targets for attackers seeking to evade detection. Security leaders must enforce strict access controls, patch vulnerabilities, and integrate IoT security into broader cybersecurity strategies. Network segmentation and comprehensive monitoring of all networked devices, including IoT endpoints, are crucial to preventing similar attacks. Organizations should also evaluate the effectiveness of their incident response plans in addressing attacks that leverage unconventional entry points.
Source Material: S-RM
Remote Monitoring and Management (RMM) Tooling: Increasingly Attackers’ First Choice
The Rundown
Cybercriminals are increasingly using remote monitoring and management (RMM) tools as an initial access vector, shifting away from traditional malware loaders and botnets.
This shift signals a significant adaptation in cybercriminal tactics, potentially driven by law enforcement crackdowns, making RMM tools a growing threat to organizations worldwide.
Proofpoint has observed a sharp rise in RMM usage, including AnyDesk, ScreenConnect, Atera, and NetSupport, in phishing campaigns since August 2024. This trend aligns with a decline in loader and botnet malware, particularly those linked to initial access brokers (IABs) such as TA577, TA571, and TA544. Law enforcement actions, including Operation Endgame, likely disrupted IAB operations, forcing them to retool or adopt new access methods.
Several threat actors, including TA583, TA2725, ZPHP, and UAC-0050, are now leveraging RMM tools for both initial access and post-compromise activity. These campaigns use phishing lures tied to government agencies, financial institutions, and utility providers, with distribution methods including malicious URLs, email attachments, and fake browser updates. Organizations must recognize the evolving role of RMM tools in cybercrime and implement robust monitoring and endpoint protections to mitigate the risk.
Source Material: Proofpoint
Ransomware and Data Extortion Trends (Mar. 3 – 9)
The Rundown
Ransomware and data extortion activity surged between March 3 and 9, with a 64% increase in listed organizations compared to the previous week.
This escalation reinforces the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and enhance cyber resilience.
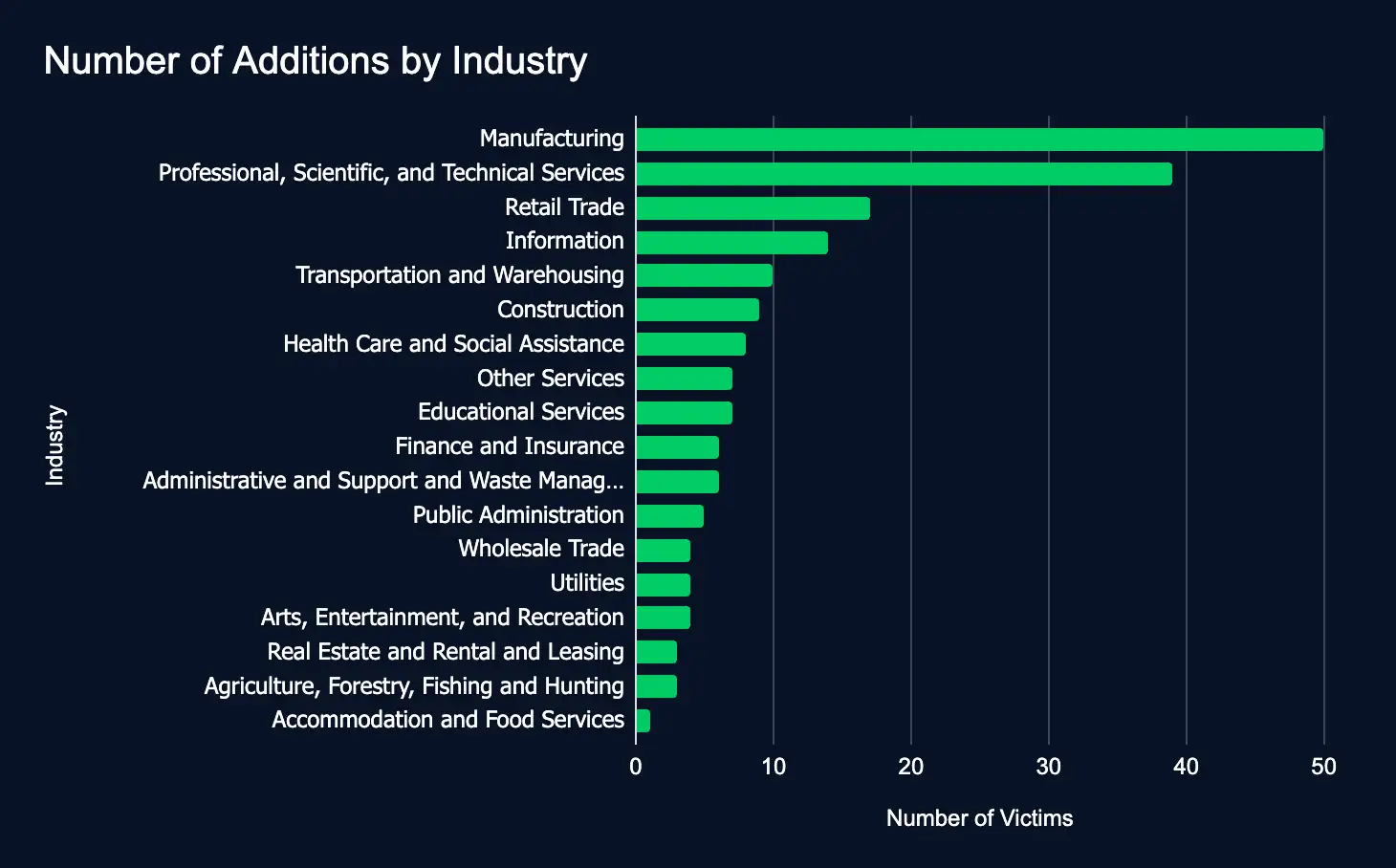
In the reporting time frame, 197 organizations across 18 industries were listed on 24 ransomware and data extortion leak sites, marking an increase from the previous week’s 120 victims.
Key Trends:
- Most targeted industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Retail Trade
- Most affected countries:
- United States
- Canada
- Germany
- Most active leak sites:
- Clop
- Fog
- Ransomhub
Exploited Vulnerabilities in Microsoft, Ivanti, Advantive Added to CISA’s Catalog – Immediate Mitigation Recommended
The Rundown
Between March 6 and 12, 11 vulnerabilities affecting Microsoft, Ivanti, Advantive products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share