Command Injection Vulnerability Exploits, Ransomware Surge, Data Leak Sites Multiply, and CISA Bolsters CVE Catalog
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Credential Harvesting, Cloud, and Malware Operations of Iranian Espionage Actor APT42
Threat Actor – Malware – Phishing – Espionage – Iran – APT42 – NICECURL – TAMECAT – Other Services – Educational Services – Professional, Technical, and Scientific Services
Insights & Determinations
- APT42’s social engineering techniques effectively leverage credential harvesting to gain access to cloud environments.
- The group’s persistent use of spear-phishing campaigns that mimic legitimate organizations underscores their strategic focus on high-value targets.
- The group’s custom malware demonstrates high technical sophistication, aiding persistent access and stealthy data exfiltration.
- APT42’s target selection aligns with Iran’s geopolitical aims, focusing on gathering intelligence to potentially influence regional stability.
- Continuous refinement of their social engineering tactics and selective use of compromised credentials are likely as APT42 adapts to enhanced cybersecurity measures.
Credential Harvesting Operations
APT42 poses as journalists and event organizers to build trust through ongoing correspondence with their targets and to deliver invitations to conferences or legitimate documents. These social engineering schemes enabled APT42 to harvest credentials and use them to gain initial access to cloud environments. Subsequently, APT42 operators exfiltrated data of strategic interest to Iran while relying on built-in features and open-source tools to avoid detection.
APT42 used at least three infrastructure clusters (Cluster A, B, and C) to harvest credentials from targets. They employed similar tactics, techniques, and procedures (TTPs) across all clusters to send spear-phishing emails, slightly varying the domains, decoys, themes, and masquerading patterns.
Cluster A
In this cluster, active since 2021, APT42 poses as news outlets and non-governmental organizations (NGOs). They are using this cluster to potentially target the credentials of journalists, researchers, and geopolitical entities in regions of interest to Iran. They have been known to impersonate the Washington Post (US), The Economist (UK), The Jerusalem Post (IL), Khaleej Times (UAE), Azadliq (Azerbaijan), and more news outlets and NGOs.
This impersonation often involves using typosquatted domains like washinqtonpost[.]press. APT42 is not known to have targeted or compromised these organizations; rather, it has impersonated them. APT42 likely sends, via spear-phishing, malicious links from typo-squatted domains masquerading as news articles that redirect users to fake Google login pages.
Cluster B
APT42 has used this cluster to masquerade as legitimate services to target individuals perceived as threats to the Iranian regime. Since 2019, APT42 operators have used this cluster to disguise their domains as generic login pages, file hosting services, and YouTube, favoring top-level domains such as .top, .online, .site, and .live.
These domains often feature URLs with several words separated by hyphens, like panel-live-check[.]online. Targets, including researchers, journalists, non-governmental organization (NGO) leaders, and human rights activists, are sent spear-phishing emails containing what appear to be legitimate links to conference invitations or documents hosted on cloud infrastructure. Once accessing the content sent to them, targets are prompted to enter their credentials, which the operators then collect.
The specificity of these attacks became apparent in March 2023, when APT42 targeted a freelance journalist using the domain ksview[.]top, which redirected to a fake Gmail login page hosted on honest-halcyon-fresher[.]buzz. This incident underscores the high degree of tailoring in APT42’s campaigns to deceive specific targets effectively. Following this, APT42’s activities continued to evolve with remarkable precision:
- March 2023: APT42 operators sent fake Google Meet invitations purportedly from Mona Louri, a fabricated identity posing as a human rights activist and researcher. Targets were directed to a fake Google Meet page hosted on Google Sites, which harvested their credentials.
- November to December 2023: APT42’s strategies included spear-phishing emails leveraging the URL shortening service “n9[.]cl” to direct targets to credential harvesting sites impersonating Google Drive, utilizing domains like review[.]modification-check[.]online.
- February 2024: Furthering their impersonation tactics, APT42 employed the domain nterview[.]site to redirect to admin-stable-right[.]top, a fake Gmail login page, specifically targeting a women’s rights activist. This domain also served a dual purpose by redirecting to a women’s rights-themed lure.
- March 2024: APT42 operators intensified their efforts with multiple campaigns:
- They used the domain shortlinkview[.]live to target a Persian-language news editor, redirecting to another fake Gmail login page hosted on panel-view[.]live.
- Leveraged the domain Reconsider[.]site in two separate campaigns; one redirected targets to a Dropbox-hosted document about the Gaza tunnels, utilizing the Israel-Hamas conflict as a lure, and another aimed at collecting credentials from academia in the US, Israel, and Europe through last-check-leave[.]buzz.
These instances illustrate how APT42 adapts its methods based on its targets’ profiles and continuously refines its deceptive techniques to maintain the effectiveness of its operations.
Cluster C
In this cluster, active since 2022, APT42 poses as a “Mailer Daemon,” URL Shortening Services, and non-governmental organizations (NGOs). APT42 used this cluster to target individuals and entities affiliated with various defense, foreign affairs, and academic issues in the US and Israel. Specifically, in November 2023, APT42 targeted a nuclear physics professor in a major Israeli university, by using the phishing URL hxxps://email-daemon[.]online/<university_acronym>365[.]onmicrosofl[.]com/accountID=<target_handle>, likely masquerading as a legitimate Microsoft 365 login.
Furthermore, APT42 leveraged this cluster to send legitimate links, likely via spear-phishing, posing as invitations to conferences or legitimate documents hosted on cloud infrastructure. Upon accessing the content, the target is prompted to enter their credentials, which are sent to the operators. APT42 encoded targets or lures using leet (“1337”) writing in these cases.
For example, the name of Tamir Pardo, the former head of the Israeli Mossad, was represented in the URL hxxps://bitly[.]org[.]il/t4m1rpa by replacing “a” with “4” and “i” with “1.” APT42 likely used lures related to the International Counter-Intelligence summit (“ICT-2023”) conducted in Israel, by deploying the following URLs:
- hxxps://bitly[.]org[.]il/J03p4y3r
- hxxps://youtransfer[.]live/ICT-2023/J03py3r
Cloud Operations
In addition to their credential harvesting operations, APT42 targeted public cloud infrastructure during 2022–2023 to exfiltrate documents of interest to Iran and sensitive information. APT42 targeted entities in the legal services and non-governmental organization (NGO) subsectors in the US and the UK. However, since the initial enabler of these operations originates with credential harvesting, APT42 may target a much broader base.
These operations began with enhanced social engineering schemes and credential harvesting to gain initial access to target networks, often involving ongoing trust-building correspondence with the target. Once they obtain the desired credentials, APT42 operators attempt to bypass multi-factor authentication (MFA) by serving a cloned website to capture the MFA token. If that fails, they will send MFA push notifications to the target. These techniques have allowed APT42 to access and compromise the target’s Microsoft 365 environment, relying on built-in features and open-source tools to decrease their chances of being detected.
This reliance on built-in features and open-source tools serves to harden attribution based on tooling and to blend in with the environment. They also cleared Google Chrome browser history after reviewing documents of interest. APT42 also attempted (and possibly succeeded) to exfiltrate files to a OneDrive account masquerading as the victim’s organization, using the fake email address <victim_org_name>@outlook[.]com. APT42 also searches and downloads files from the target’s OneDrive to disk, likely to access files of interest. Finally, they leverage anonymized infrastructure to interact with the target’s environment, including ExpressVPN nodes, Cloudflare-hosted domains, and ephemeral VPS servers.
Social Engineering
APT42 operators employed schemes involving decoys and trust building, which included masquerading as legitimate non-governmental organizations (NGOs) and conducting ongoing correspondence with the target, sometimes lasting several weeks. Operators sent emails from domains typosquatting the original NGO domains, such as aspenlnstitute[.]org.
To increase their credibility, APT42 impersonated high-ranking personnel working at the masqueraded organizations when creating the email personas. They also used decoy material to enhance the legitimacy of their invites to actual, relevant events and conferences. In one instance, APT42 hosted the decoy material on an operator-controlled SharePoint folder, accessible only after the target entered their credentials. The decoy documents did not contain malicious elements, suggesting the operators used them solely to gain the target’s trust.
Credential Harvesting and Bypassing MFA
Only after the operators built a certain level of trust with the target did they harvest the desired credentials by sending a link that would redirect them to a credential harvesting site, similar to the process described in the previously discussed credential harvesting section.
Credential Harvesting
APT42 operators used Javascript files to redirect targets from links to serve fake Microsoft 365 login pages. At least once, APT42 used several methods—both SharePoint login and fake LinkedIn login pages—to target multiple high-profile personnel of the target organization during the same campaign.
MFA Bypass
First, APT42 acquired MFA tokens by using fake DUO pages, using subdomains with prefixes such as “api-<generated_id>[.]…” or using words like “duo.” When this failed, the operator sent authentication prompts to targets upon attempts to log in. In a different intrusion, APT42 likely used a phishing site sent via SMS to capture the MFA token and leveraged the KMSI (Keep-me-Signed-In) feature to avoid re-authentication.
In at least one instance, APT42 established a “persistent” login mechanism, leveraging the Microsoft app password feature to create an app password for the compromised account. APT42 likely used this technique to preserve ongoing access for future logins without re-verifying their identity with MFA. However, there is no evidence suggesting APT42 used it.
Discovery
APT42 will attempt to locate specific files and data of interest to Iran. For example, in one intrusion, the operators searched for specific Iran-related documents with details about foreign affairs issues. In another case, the operators searched for files related to the Middle East and the Ukraine war.
Data Exfiltration
APT42 exfiltrated data, including OneDrive documents, Outlook emails, and documents of potential interest to Iran, such as files about its foreign affairs or the Persian Gulf region from Microsoft 365 environments.
The M365 infiltration and data exfiltration included the following stages:
- Operators logged in to the victim’s email using the Thunderbird email client, whose usage was approved by the operator, altering the user permissions.
- Operators logged in to the victim’s Citrix application and used Windows Remote Desktop Protocol (RDP). Upon access, the operators explored, enumerated, and staged files for exfiltration in password-protected 7-ZIP archives.
- Operators performed host, network, and directory reconnaissance using Windows native commands, including:
“whoami,” “net view,” “cd,” “explorer,” “net share,” “hostname,” “ls,” “type,” “ping,” “net user,” “gci,” “mkdir,” “notepad,” “mv,” “exit,” “rm,” “dir,” and “del.”
- Operators used PowerShell cmdlets, including “set-ExecutionPolicy,” “Import-Module,” and “Invoke-HuntSMBShares,” a cmdlet from the open-source tooling module PowerHuntShares that can identify users with excessive network share permissions.
Malware Operations
Several APT42 campaigns can be tracked by their use of custom malware. Most recently, APT42 deployed two custom backdoors, NICECURL and TAMECAT. These backdoors were delivered with decoy content, likely via spear-phishing, and provided APT42 operators with initial access to the targets. The backdoors offer a flexible code-execution interface and can deploy additional malware or manually execute commands on infected systems. APT42 operators used these backdoors to target NGOs, governments, or intergovernmental organizations around the world, handling issues related to Iran and the Middle East, consistent with APT42 targeting profile.
NICECURL
NICECURL is a backdoor written in VBScript that communicates over HTTPS, can download additional modules to be executed, including a data mining module, and provides an arbitrary command execution interface. The backdoor’s accepted commands include “kill” to remove artifacts and end execution, “SetNewConfig” to set a new sleep value, and “Module” to download and execute additional files, potentially extending NICECURL’s functionality.
In January 2024, APT42 used a malicious LNK file (onedrive-form.pdf.lnk), which downloaded NICECURL and a PDF decoy masquerading as an Interview Feedback Form of the Harvard T.H. Chan School of Public Health. The decoy mentioned an interviewee named Daniel Serwer, possibly referring to the scholar and foreign policy researcher by the same name affiliated with the Middle East Institute.
The LNK file is downloaded from hxxps://drive-file-share[.]site/OneDrive-Form.pdf.lnk. APT42 uploaded this file to the command and control (C2) server on 14 January 2024. The LNK file contained a Curl command that downloaded and executed NICECURL hosted on prism-west-candy[.]glitch[.]me.
Another NICECURL sample ( Kuzen.vbs) connected to worried-eastern-salto[.]glitch[.]me and downloaded a decoy file (question-Em.pdf) about Empowering Women for Peace from an American think tank specializing in U.S. foreign policy and international relations. According to the contents of the decoy file, the attack possibly occurred in January or the beginning of February 2024 and targeted an Australian. A RAR file (“question_Empowering Women for Peace Gender Equality in Conflict Prevention and Resolution (6).rar”) with a similar name as the decoy PDF was likely used to target the same victim.
TAMECAT
TAMECAT is a PowerShell tool that can execute arbitrary PowerShell or C# content. It has been observed being dropped by malicious macro documents and communicating with its command-and-control (C2) server via HTTP. APT42 has used TAMECAT in a large-scale spear-phishing campaign targeting individuals or entities employed by or affiliated with NGOs, governments, or intergovernmental organizations around the world.
Execution begins with a small VBScript downloader that leverages Windows Management Instrumentation (WMI) to query anti-virus products running on the victim’s system. Download commands and URLs differ depending on the script used to determine if Windows Defender is running. If Windows Defender is running, the script will leverage Conhost to execute a PowerShell command that uses Wget to download content from the URL: hxxps://s3[.]tebi[.]io/icestorage/config/. For all other cases, the script uses Cmd.exe to execute a Curl command similar to the Curl commands used in the NICECURL execution.
One known file named a2.vbs downloaded the text file nconf.txt, which contained a PowerShell script containing an obfuscated and AES-encrypted TAMECAT backdoor. The script also downloads an additional PowerShell script, df32s.txt, which is used to decrypt the embedded AES-encrypted TAMECAT backdoor.
When downloading the AES decryption script, a hard-coded User-agent string is used. The script stores the URL for the AES decryption script as a Base64 string, with the first three characters are truncated and the remaining string decoded.
In addition to AES decryption, the script defines global variables, including a C2 domain, which the TAMECAT backdoor uses. Decryption reveals additional PowerShell that appends together a string obfuscated within nconf.txt, and AES decrypts the string. The decrypted results are the TAMECAT backdoor.
The TAMECAT backdoor initially writes a likely victim identifier to % LOCALAPPDATA%config.txt. Then, it makes an initial POST request to the globally defined C2 domain hxxps://accurate-sprout-porpoise[.]glitch[.]me. The initial POST request contains information, such as computer names, that is AES encrypted and Base64 encoded.
Risk & Impact Assessment
APT42’s operations, characterized by sophisticated social engineering, credential harvesting, and cloud-based attacks, present significant cybersecurity challenges. These activities primarily target sectors like media, academia, legal services, and political activists within Western and Middle Eastern regions, jeopardizing both data integrity and organizational operations.
The extensive credential harvesting techniques employed by APT42 facilitate unauthorized access to environments, including cloud resources, leading to substantial risks of data breaches. This could result in the loss of sensitive data for organizations in the targeted sectors. Such breaches undermine the confidentiality of sensitive information and potentially the integrity and availability of data critical to daily operations.
Furthermore, successful breaches could disrupt service delivery, impair customer trust, and necessitate costly emergency response measures to restore normal operations. The impact could be particularly severe for educational and research institutions and non-governmental organizations, affecting sensitive research into Iran and the Middle East and potentially impacting national security and foreign affairs.
The financial repercussions of APT42’s activities are manifold. Direct costs may include remediation expenses, increased cybersecurity protection costs, potential fines from data protection regulatory violations, and litigation costs from affected parties. Indirect costs could involve lost revenue from disrupted operations and decreased stakeholder trust.
Persistent threats from APT42 necessitate continuous enhancements in cybersecurity defenses, potentially diverting resources from other strategic initiatives. Over time, this could lead to a degradation of overall security posture, making organizations more vulnerable to future attacks and less agile in their operational and strategic initiatives.
The risks and impacts outlined underscore the critical need for targeted sectors to fortify their defenses and remain vigilant against APT42’s evolving tactics. Understanding their trajectory becomes imperative for effective cybersecurity planning and response as these threats continue to adapt and potentially escalate.
Source Material: Mandiant, Uncharmed: Untangling Iran’s APT42 Operations
NSA, FBI, and State Warn: North Korean Phishing Leverage Weak Email Policies
Threat Actor – North Korea – Phishing – Kimsuky – DMARC Abuse – Industries/All
Insights & Determinations
- North Korean cyber operations, particularly those conducted by the Kimsuky group, continue to pose a significant threat through sophisticated spear-phishing campaigns. These campaigns target weak email security policies, leveraging poor DMARC configurations to impersonate legitimate entities and gain unauthorized access to sensitive geopolitical information.
- The advisory highlights that North Korean cyber tactics are not merely about immediate data theft but are part of broader strategies to influence global perceptions and policy, aiming to bolster North Korea’s position against international pressures. This integration of cyber operations into larger geopolitical strategies underscores the necessity for a vigilant and informed response from the global community.
- Organizations are urged to reassess and strengthen their email security systems, particularly by enhancing DMARC policies. Strengthening these policies is essential not just for technical security but as a crucial aspect of comprehensive organizational security strategies to mitigate risks of data breaches and espionage.
- The report suggests a multi-layered defensive strategy that includes regular security audits, advanced threat detection tools, continuous employee training, and rigorous incident response planning. These measures are vital to defend against the sophisticated and evolving nature of state-sponsored cyber threats.
Threat Analysis
The report details how North Korean operatives, particularly from the Kimsuky group, meticulously craft emails to appear as though they are coming from credible sources such as journalists and academics. Kimsuky is known for gathering intelligence that could benefit North Korean national interests. The group has been active for several years and is known for its sophisticated social engineering techniques and targeting of individuals who possess potentially valuable political or military information.
These emails often do not initially include malicious links or attachments, which helps them avoid early detection by security software. The actors behind these campaigns use personal and professional information about their targets, which they gather through extensive research, to increase the likelihood of a response. For instance, the report provides examples of these actors impersonating known entities within think tanks and educational institutions, thus exploiting their targets’ trust and professional connections.
One of the advisory’s revelations is that the actors exploit weakly configured DMARC (Domain-based Message Authentication, Reporting, and Conformance) policies. DMARC is an email authentication protocol designed to protect an owner’s domain from unauthorized use when sending email, commonly known as email spoofing. The protocol enables email senders and receivers to determine whether or not a given message is legitimately from the sender and what to do if it isn’t. This verification is done by checking the sender’s IP address against the SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) standards, which are other forms of email authentication.
Organizations that have set their DMARC policies to ‘none’ or poorly configured them are particularly vulnerable, allowing threat actors to spoof the organization’s legitimate email domain. This oversight grants North Korean actors tremendous success in delivering their spear-phishing emails directly to the inboxes of their intended victims, thereby increasing the risk of data breaches or espionage.
Risk & Impact Assessment
The cyber threats outlined in the joint advisory, particularly those associated with North Korean spear-phishing campaigns exploiting weak DMARC policies, pose significant potential consequences for businesses across various sectors.
Businesses could suffer substantial financial damage as a result of successful spear-phishing attacks. Financial loss can occur through direct theft of funds, fraud, or through the costly processes of remediation after a data breach, including fines, legal fees, and compensation payments. Moreover, if sensitive strategic information is stolen, it could lead to lost revenue from compromised competitive advantages.
Cyber attacks like those carried out by the Kimsuky group often aim to infiltrate networks to steal data, but they can also result in significant disruptions to business operations. Once inside a network, malicious actors could deploy ransomware, corrupt data, or even sabotage critical infrastructure. The downtime and operational delays caused by such incidents can hinder business productivity and service delivery, potentially leading to long-term reputational damage.
The theft of intellectual property (IP) poses a severe risk for industries involved in research and development, such as pharmaceuticals, technology, and manufacturing. North Korean actors targeting these sectors could gain access to proprietary information, leading to significant strategic losses and undermining competitive positions in the market.
A business’s reputation is crucial to its success and customer trust. A breach that exposes customer data or sensitive corporate information can severely damage a company’s reputation. This impact can be amplified if the business is seen as having failed to adequately protect itself against known vulnerabilities, such as those related to DMARC policies.
Strategic risks are heightened for businesses that operate internationally, especially those involved in regions or topics of interest to North Korea. Information stolen in spear-phishing campaigns could be used to manipulate geopolitical situations or policy decisions, indirectly affecting businesses involved in those regions.
In response to the threats highlighted in the advisory, businesses will likely need to invest more in their cybersecurity defenses. This could include spending on advanced security software, enhanced monitoring and response systems, and employee training programs. While necessary, these investments represent an additional cost burden that businesses must manage.
Outlook
State-sponsored cyber operations, such as those conducted by North Korea, extend beyond immediate tactical gains to fulfill broader strategic objectives. This report illuminates the role of North Korean cyber tactics within wider efforts to shape global perceptions and policies. The aim is not merely the acquisition of information but leveraging that data to bolster North Korea’s position amidst international pressures. As these activities continue to evolve, the global community must remain vigilant and responsive to these sophisticated strategies.
Given the enduring and adaptive threat posed by North Korea’s cyber operations, which are designed to exploit vulnerabilities within digital defenses, it is anticipated that North Korea will persist in its strategic deployment of cyber espionage. This approach is integral to its strategy to counteract geopolitical isolation and the impact of economic sanctions. The advisory serves as a critical reminder of the ongoing necessity for vigilance and adaptive defense strategies in the face of these persistent threats.
Organizations must view this advisory as a call to action to reevaluate and fortify their email security protocols. The exploitation of previously unrecognized vulnerabilities by North Korean entities highlights the urgent need for robust security measures. Enhancing DMARC policies transcends mere technical upkeep; it is a fundamental aspect of a comprehensive organizational security strategy that prepares and protects against future cyber threats.
Source Material: The National Security Agency (NSA) joins the Federal Bureau of Investigation (FBI) and the U.S. Department of State, North Korean Actors Exploit Weak DMARC Security Policies to Mask Spear-phishing Efforts
Cuttlefish Malware Hits SOHO Routers, Steals Credentials
Malware – Credential Theft – Web Request Eavesdropping – DNS and HTTP Hijacking – SOHO Router Targeting – Cuttlefish – Industries/All
Insights & Determinations
- While the initial access method is unknown, once access is achieved, the threat actor deploys a bash script, which collects specific host-based data and retrieves the Cuttlefish payload.
- Cuttlefish employs a multifaceted approach, featuring modules for credential harvesting, data hijacking, and encrypted communication. It captures and encrypts outbound traffic data using sophisticated packet filtering to extract sensitive information and manipulates HTTP traffic to reroute internal communications.
- By monitoring web requests over local networks, Cuttlefish captures credentials and hijacks DNS and HTTP connections, potentially leading to significant data breaches.
- Cuttlefish could spearhead a pivotal shift in cyber threats, potentially ushering in a new era of infostealers focused on internal network traffic.
- Given its innovative attack methods, organizations are advised to investigate suspicious login attempts from internal IP addresses, encrypt network traffic with TLS/SSL, inspect SOHO devices for abnormal files, and implement certificate pinning when remotely connecting to high-value assets to counteract and adapt to this threat effectively.
Threat Analysis
The initial access method is unknown. Once access is achieved, the threat actor deploys a bash script. This script collects specific host-based data, compressing the data into a file. This file is sent to the command and control (C2) server. After sending, the file is deleted. The script then retrieves the Cuttlefish payload from the C2 server. It hides this payload in the tmp directory by adding a “.” to the file name. The script changes the permissions, allowing the payload to execute.
Once executed, Cuttlefish is deleted from the file system. It uses several file paths to obtain a payload for all major router architectures. It also opens and binds to port 61235 on the localhost. This ensures that only one instance is running by displaying an error message if another process uses this port. After verifying that only one instance is running, Cuttlefish checks for commandline arguments passed during execution.
Then, Cuttlefish sets up a secure connection to the C2. It uses an embedded RSA certificate. It downloads and updates the configuration from the URL “hxxps://205[.]185[.]122[.]121:443/rules?uuid=UUID_CREATED_EARLIER,” saving it as “/tmp/config.js.”
Once it has the configuration file, Cuttlefish creates two threads. One thread tracks the heartbeat time to check for periodic updates. The second thread monitors traffic across the selected interfaces specified via the command line upon execution.
Credential Harvesting Functionality
Cuttlefish utilizes libpcap to set up an eBPF ( Berkeley Packet Filter) for sniffing and capturing IP ranges. It checks outbound traffic against a list of ports and protocols, looking for predefined credential markers such as “username,” “password,” “aws_secret_key,” etc. Matches are logged and sent to the C2, with HTTP messages Base64 encoded. Details are on our Github, highlighting cloud service markers like AWS and CloudFlare, which store sensitive data.
Despite rules for port 443 TCP traffic, there’s no mechanism to bypass TLS encryption, questioning the filter’s effectiveness given TLS’s prevalence. The focus may be more on hijacking functionalities.
Logger and Data Transmission Function
Once a log file of filtered traffic reaches the size supplied on the command line or the maximum size set, Cuttlefish will gzip and upload the file to the C2 using the previously computed uuid and a hardcoded value of “tid.”
Hijack Functionality
Once Cuttlefish activates its two threads, it looks for two conditions to initiate a hijack: private IP addresses and TCP connections to port 80 or UDP connections to port 53. It exploits HTTP by manipulating the “302” response error code, substituting requests to internal IPs with values from its configuration file.
This ability lets Cuttlefish redirect internal “east-west” traffic across routers or VPN-connected sites and access to web requests that do not traverse the public internet. This capability is evidenced by the threat actors using a self-signed X.509 certificate with a private IP in the subject common name. With hijacked HTTP credentials, the threat actor can access the targeted LAN via a VPN embedded in the malware.
VPN Functionality
The VPN functionality is based on the open-source project n2n. The VPN function starts by running the three commands. Next, Cuttlefish will get the IP of a hardcoded domain using CloudFlare’s DNS API. It then downloads the configuration from the C2 and saves the output as /tmp/n2nconfigjs.
If the status is set to 1, it creates a thread to join an n2n community and process connections. This connection could allow the actors to impersonate legitimate victims’ genuine IP addresses when accessing public cloud services or even interact with the local LAN from a private IP address, thus bypassing some perimeter-based security measures.
Private Proxy Functionality
The proxy functionality is an alternative to the VPN, allowing the threat actors to weaponize the stolen credential material from an IP address associated with a known user. This function appears to be based on the open-source project called “socks_proxy.” Cuttlefish will bind to all external interfaces on what seems to be a random port and uses a hardcoded username and password for the socks5 proxy authentication. Unlike other proxy malware, such as TheMoon, where the proxy services are sold to other actors, this proxy pool is only used by Cuttlefish actors.
Risk & Impact Assessment
This malware aims to collect cloud-based authentication material by targeting networking equipment to gain access to cloud environments. Gaining access to cloud environments allows threat actors to access materials hosted internally and grant long-term persistent access without worrying about security controls.
Threat actors seek to gain and maintain access to systems and materials for several reasons:
- Data Extraction: Accessing sensitive or proprietary information can provide national strategic advantages, be sold, or used for extortion. Internal documents, personal data, and intellectual property are prime targets.
- Surveillance: Persistent access allows ongoing monitoring of an organization’s activities. This can be valuable for cyber espionage in gathering intelligence on operations.
- Infrastructure Leverage: Compromised systems can be used as part of a botnet or for further attacks, serving as pivot points to other connected networks or systems.
The impacts of such unauthorized access include:
- Financial Loss: Direct losses from theft, ransom payments, and the cost of response efforts and system restoration. Indirect costs can include increased insurance premiums and compliance costs.
- Reputational Damage: Public awareness of a security breach can erode trust among clients, partners, and stakeholders, affecting business relationships and market value.
- Operational Disruption: Attacks might target critical infrastructure components, leading to downtime, loss of productivity, and impaired service delivery.
- Legal and Regulatory Consequences: Non-compliance with data protection regulations can result in fines and sanctions, compounding financial losses and damaging relations with regulators.
Source Material: Lumen, Eight Arms To Hold You: The Cuttlefish Malware
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Finance and Insurance – Construction – Transportation and Warehousing – Retail Trade
In the past week, 52 organizations were listed on various data leak sites, with the majority operating in the Manufacturing sector.
Analysis
Eleven ransomware data leak sites reported new organizational entries last month, with RA Group, Black Basta, and Lockbit leading in activity.
The number of organizations added to ransomware data leak sites in a single week underscores a critical threat to cybersecurity, impacting the stability and security of organizations across multiple sectors.
RA Group led the entries, responsible for 17 new additions, accounting for 33% of all newly listed organizations.
- Black Basta followed with 10 new additions, accounting for 19%.
- Lockbit added 9 new organizations, accounting for 17%.
- Ransomhub, Qilin, and Everest each added 3 new organizations, each accounting for 6%.
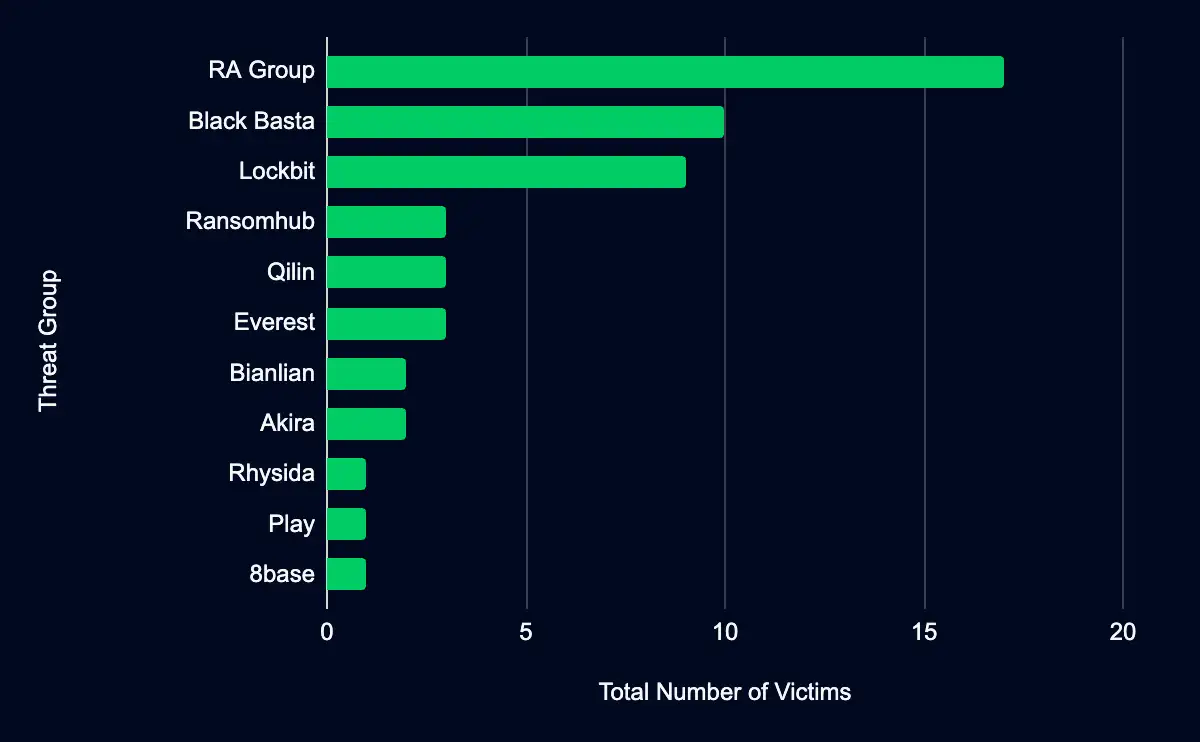
Ransomware groups are continuously evolving, targeting diverse industries, emphasizing the persistent and escalating challenge to cybersecurity defenses worldwide.
The prominence of groups like RA Group indicates a trend towards more aggressive data theft and extortion tactics, likely spurred by the lucrative returns of such cybercrimes.
Being listed on a data leak site can lead to significant operational disruptions and severe reputational damage for the affected organizations, pushing the need for advanced countermeasures and robust data protection strategies.
Furthermore, the organization’s suppliers and partners could inadvertently be impacted, potentially leaking sensitive data related to these third-party organizations, exacerbating the breach’s ripple effect across the supply chain.
The uptick in organizations listed on ransomware data leak sites in the past month highlights a critical ongoing battle in cybersecurity, urging companies to reinforce their defenses against sophisticated cyber extortion schemes.
Industry Analysis
The manufacturing sector has become a primary target for ransomware groups, with 23% (12) of organizations listed in recent data leaks coming from this industry.
Manufacturing firms, integral to supply chains and economic stability, are increasingly vulnerable to cyberattacks that can halt production lines, trigger supply shortages, and inflate consumer prices.
The targeting of the manufacturing sector suggests a strategic strategy by cybercriminals for industries that are less likely to have robust digital defenses but are critical to economic operations.
12 out of 52 recently listed organizations on ransomware data leak sites are manufacturing firms.
- Industries such as professional services, finance, and retail are also heavily impacted, making up 15% and 12% of new listings, respectively.
- To a lesser extent, construction, and transportation and warehousing accounted for 8 % of new listings.
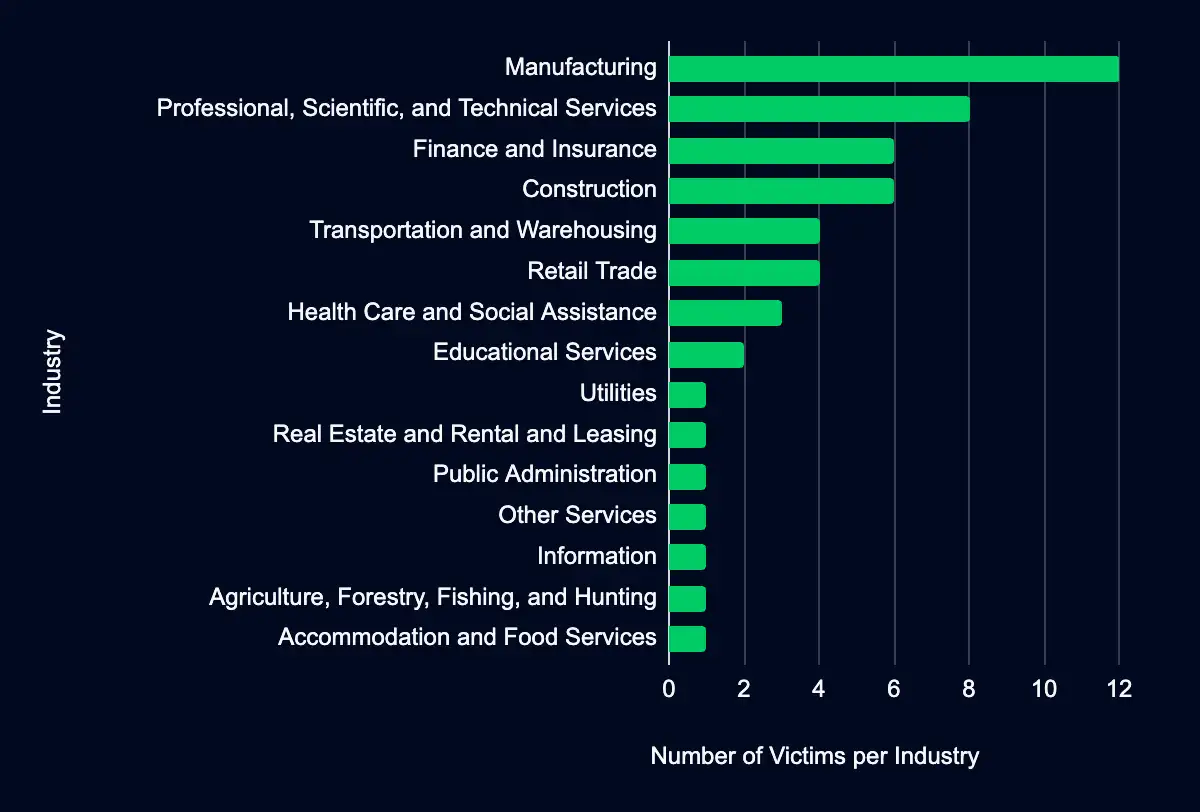
As ransomware attacks diversify, critical infrastructure sectors like manufacturing are facing new risks that could have ripple effects on trade and market stability.
These attacks and the pivotal role of the targeted sectors underscore the need for heightened cybersecurity measures and proactive threat intelligence.
Ransomware attacks on the manufacturing, professional services, finance, and retail sectors are a stark reminder of the growing cyber threats facing industries that form the backbone of the economy.
Geographic Analysis
The United States leads in the number of organizations listed on ransomware data leak sites, with 25 new entries last month.
As the primary target, the U.S. faces heightened risks to its corporate and governmental digital infrastructures, potentially affecting the economic stability of involved organizations.
Organizations in the U.S. represent 25 of the 52 entries, accounting for 48% of the total new listings.
- Germany and the United Kingdom follow with 9 (17%) and 4 (8%), respectively.
- However, organizations listed on the leak sites are located across the globe, including Italy, Switzerland, Spain, Netherlands, and Mexico.
The U.S. being the prime target underscores the strategic focus of cybercriminals on economies with significant global influence and substantial digital assets.
The concentration of cyberattacks in the U.S. and other major economies suggests that ransomware groups target regions with dense technological infrastructures, many potential targets, and potentially lucrative ransom payouts.
The persistent targeting of U.S. organizations indicates not only the weaknesses but also the high stakes involved in securing them against escalating cyber threats.
The prominence of the U.S. in ransomware data leak statistics highlights the critical need for enhanced cybersecurity measures and international collaboration to combat these persistent threats.
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share