VPN RCEs Continue, LLMjacking, Social Engineering by Overload, Hundreds of Newly Published Data Leaks, and Chromium Vulns Added to the KEV Catalog
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Ivanti Pulse Secure Vulnerabilities Exploited to Deliver Malware
- LLMjacking: Using Stolen Accounts to Access Cloud-hosted AI Services
- Attacker Floods Company Inboxes, Calls Targets, Uses RMM to Steal Credentials
- Phorpiex Botnet Delivers LockBit Black Ransomware in Massive Email Campaign
- Latest Additions to Data Leak Sites
- CISA Adds Chromium Based CVEs to Known Exploited Vulnerabilities Catalog
Ivanti Pulse Secure Vulnerabilities Exploited to Deliver Malware
Vulnerability Exploitation – Malware – Ivanti Pulse Secure CVE-2023-46805 & CVE-2024-21887 – Mirai Botnet – All Industries
Insights & Determinations
- The combined exploitation of CVE-2023-46805 and CVE-2024-21887 highlights an attack where attackers bypass authentication and execute arbitrary commands.
- The ongoing exploitation of these vulnerabilities has broader implications, potentially affecting various industries. This could include immediate operational disruptions and long-term damage due to data breaches and system manipulations.
- We expect attackers to refine their tactics, targeting lesser-known vulnerabilities and employing more covert methods to evade detection.
- Rapid patch application, enhanced network monitoring, and rigorous incident response planning form the cornerstone of a proactive defense strategy.
Threat Analysis
Authentication Bypass Mechanism (CVE-2023-46805): This vulnerability allows attackers to circumvent authentication by exploiting a path traversal flaw in the “/api/v1/totp/user-backup-code” endpoint.
- Attackers can manipulate the URL to gain unauthorized access to restricted areas of the network, laying the groundwork for further malicious activities.
Command Injection Exploit (CVE-2024-21887): Chaining this vulnerability with CVE-2023-46805, attackers exploit a command injection vulnerability in the “/api/v1/license/key-status/;” endpoint.
- Attackers can send specially crafted requests to execute arbitrary commands directly on the server.
- This can involve downloading and executing malware, altering system configurations, or accessing sensitive data.
Example Attack Scenario: Utilizing the combined vulnerabilities, an attacker might send a request like GET /api/v1/totp/user-backup-code/../../license/keys-status/{injected command}.
- An observed command wiped system files and downloaded and executed a malicious script from an external server.
- The script contained commands to access various directories. Once a directory is accessed, it downloads the Mirai botnet malware.
Risk & Impact Assessment
The primary risk from these vulnerabilities lies in the potential for full network compromise. Attackers exploiting CVE-2023-46805 with CVE-2024-21887 can:
- Expose sensitive data, steal intellectual property, and cause the loss of personal information.
- Manipulate or shut down critical systems and operations, resulting in significant operational disruptions, from halting production lines to interrupting service delivery.
- Facilitate the spread of additional malware, including ransomware. This increases remediation costs and potentially turns infected networks into platforms for further attacks.
Beyond the immediate technical impacts, organizations suffering from such breaches face substantial reputational damage. Customers and partners may lose trust, leading to lost business opportunities and potential legal liabilities.
Once a vulnerability is known and exploited, it can set a precedent for future attacks unless organizations take comprehensive countermeasures.
Outlook
Organizations should anticipate an evolution in attack methodologies as cybercriminals adapt to the security measures implemented in response to these vulnerabilities. We expect attackers to:
- Look to exploit other lesser-known but similar vulnerabilities in different systems or software, broadening the scope of potential targets.
- Refine their tools and methods to avoid detection by standard security measures. This could include new or modified malware to evade signature-based detection tools.
- Use a different initial access vector, such as phishing, drive-by-download, external-facing remote services, or valid accounts.
Source Material: Juniper Networks, Protecting Networks from Opportunistic Ivanti Pulse Secure Vulnerability Exploitation
LLMjacking: Using Stolen Accounts to Access Cloud-hosted AI Services
LLMjacking – Account Theft – LLMs – AWS – Industries/All
Insights & Determinations
- The attack may have exploited a Laravel system vulnerable to CVE-2021-3129 to steal cloud account credentials. They used a script that may avoid detection using specific API parameters. This highlights the attackers’ desire to access LLMs and avoid detection.
- The attackers checked accounts to see if they could access an LLM and investigated service configurations to ensure malicious activities would not be logged. This highlights that the attackers didn’t want the malicious activity performed by stolen accounts to be logged.
- The potential use of the OAI Reverse Proxy suggests attackers wanted to manage and possibly sell unauthorized access to multiple LLMs.
- The abuse of stolen cloud accounts for accessing LLMs could incur substantial costs, estimated at up to $46,000 per day if quota limits are maximized, alongside disrupting business operations by blocking legitimate access to these models.
Threat Analysis
The attackers stole the accounts from a Laravel system vulnerable to CVE-2021-3129. The vulnerability allows unauthenticated remote attackers to execute arbitrary code. However, it’s unknown if the attackers exploited this vulnerability to steal the accounts.
With the accounts, they used a script to check if the accounts had access to ten different AI services:
- AI21 Labs
- Anthropic
- AWS Bedrock
- Azure
- ElevenLabs
- MakerSuite
- Mistral
- OpenAI
- OpenRouter
- GCP Vertex AI
The script used the InvokeModel API call request with the max_tokens_to_sample parameter set to -1 to test the account’s access without triggering any alarms. Setting the parameter value to -1 triggers either a ValidationException or AccessDenied error. If the error ValidationException is returned, this confirms that the account has access and the service is active.
The attackers also showed interest in how the service was configured by calling “GetModelInvocationLoggingConfiguration,” which returns S3 and Cloudwatch logging configuration details. The attackers conducted this check to ensure their activities were not logged.
However, Cloudtrail and S3 do not store prompts and their results by default, which requires additional configuration.
The script also references the open-source project OAI Reverse Proxy. During the attack, a useragent matching the OAI Reverse Proxy was seen. This project acts as a reverse proxy for LLM services, and allows users to manage accounts with access to LLMs without revealing the underlying pool of accounts. If the attackers wanted to sell the access, this project could allow them to monetize their efforts.
Risk & Impact Assessment
The primary risk from this attack lies in the potential for attackers to access costly cloud-hosted LLMs. Attackers with access can:
- Extract valuable data from LLMs, including training data and user queries, which may contain sensitive or proprietary information.
- Manipulate LLM training models to alter their behavior or outcomes, train the models to produce malicious responses, or refine their AI systems.
This attack could cost you a significant sum financially. In the following scenario, the total charges could reach $46,000 a day.
- According to AWS Bedrock pricing and quota limits for Claude 2, 1000 input tokens cost $0.008, and 1000 output tokens cost $0.024, averaging $0.016 for 1000 tokens.
- AWS Bedrock can process a max of 500,000 tokens per minute.
- (500K tokens/1000 * $0.016) * 60 minutes * 24 hours * 4 regions = $46,080 / day
Note: Claude has a 200,000 token context window. This translates to roughly 150,000 words.
Beyond these impacts, organizations suffering from such breaches could face reputational damage. Customers and partners may lose trust, leading to lost business opportunities and potential legal liabilities.
Once this attack vector is known, it can set a precedent for future attacks unless organizations take comprehensive countermeasures.
Source Material: Sysdig, LLMjacking: Stolen Cloud Credentials Used in New AI Attack
Attacker Floods Company Inboxes, Calls Targets, Uses RMM to Steal Credentials
Credential Theft – Spam Flooding – Voice Phishing (Vishing) – AnyDesk Abuse – Windows Quick Assist Abuse – Batch Script – All Industries
Insights & Determinations
- The attacker uses a multi-step social engineering approach, starting with a flood of spam emails and followed by vishing calls, tricking recipients into installing remote monitoring and management (RMM) tools like AnyDesk and Quick Assist.
- Upon gaining remote access, the attacker executes batch scripts to steal user credentials and establish a reverse shell connection via PowerShell and OpenSSH, maintaining persistence through Windows registry modifications.
- This method demonstrates a concerning trend that could inspire similar attacks from other threat actors, emphasizing the need for organizations to enhance their cybersecurity defenses and vigilance.
- To counter such attacks, organizations should implement multi-layered security measures, including regular employee training on phishing tactics, using secure remote access tools, network segmentation, and enforcing multi-factor authentication (MFA) for accessing sensitive systems and data.
Threat Analysis
In late April 2024, an affiliate (or affiliates) of the Black Basta ransomware sent hundreds of non-malicious spam emails to groups of users in a targeted company. The volume was significant enough to overwhelm the email security solution, allowing the emails to reach the users’ inboxes.
Most spam emails were confirmations for newsletter sign-ups from various legitimate organizations. The attacker then began to call the spam email recipients directly, pretending to be IT team members and offering support to fix their email issues.
During these calls, the attacker attempted to trick the user into providing remote access to their computer by having them install AnyDesk or use the built-in Windows remote support utility Quick Assist. If the attacker failed to convince the user to install AnyDesk or use Quick Assist, they immediately moved on to another targeted user.
Once the attacker successfully gains access to a user’s computer, they send the user a series of batch scripts, presented as updates, and begin executing them.
The first batch script verifies connectivity to their command and control (C2) server. Then, it downloads a zip archive containing a legitimate copy of OpenSSH for Windows, its dependencies, several RSA keys, and other Secure Shell (SSH) configuration files.
Most batch scripts have hard-coded C2 servers, while others are written so that the C2 server and listening port can be specified on the command line as an override.
The script establishes persistence via run key entries in the Windows registry. The run keys created by the batch script point to additional batch scripts that are created at run time. Each batch script executes SSH via PowerShell in an infinite loop to attempt to establish a reverse shell connection to the specified C2 server using the downloaded RSA private key.
However, there are several variations of the batch scripts, some of which also conditionally establish persistence using other remote monitoring and management solutions, including NetSupport and ScreenConnect.
In all observed cases, the attackers used a batch script to steal the victim’s credentials from the command line using PowerShell. The script was delivered to the user under the false premise that the file was needed to update their systems and required user credentials.
In most batch script variations, the credentials are immediately exfiltrated to the attacker’s server via a Secure Copy command (SCP). The attacker saved the credentials to an archive in at least one script variant, requiring manual retrieval.
In one incident, the attacker deployed the NetSupport remote access trojan (RAT). After successfully gaining access to the compromised asset, the attacker used Impacket to deploy a legitimate Dynamic Link Library (DLL), named 7z.dll, to other assets within the same network as the compromised asset. The attackers altered 7z.dll so it could use a hard-coded key to XOR-decrypt a Cobalt Strike beacon and then execute it.
The attacker then executed 7zG.exe and passed a command line argument to sideloaded 7z.dll, executing the embedded Cobalt Strike beacon. Upon successful execution, the beacon injected the newly created process choice.exe.
While the attackers were not observed exfiltrating data or deploying ransomware, based on Rapid7 internal and open-source intelligence, the indicators of compromise are consistent with the Black Basta ransomware group.
Risk & Impact Assessment
The primary risk from this attack lies in the potential for attackers to access critical systems, steal sensitive data, and deploy ransomware.
The direct impacts stemming from these risks include:
- The exposure of confidential business information, personal data, and other sensitive materials that could be exploited for identity theft, competitive advantage, or leaked.
- Direct financial losses, including the costs associated with incident response, ransom payments, and potential fines and penalties for failing to protect data under regulations.
- Critical systems and data can be rendered inaccessible, leading to operational downtime, lost productivity, and the costs associated with restoring systems and data from backups.
Beyond these risks and impacts, organizations suffering from such attacks could face other risks and impacts, such as:
- Loss of trust among customers, partners, and stakeholders could severely damage an organization’s reputation and lead to a business decline and difficulty acquiring new customers.
- Legal risks associated with data breaches, including litigation from affected parties and penalties from regulatory bodies for failing to comply with data protection laws.
- Beyond the immediate consequences, there can be long-term strategic impacts, such as the need to overhaul cybersecurity practices, implement new security technologies, and possibly retrain staff, all of which require significant investment.
Source Material: Rapid7, Ongoing Social Engineering Campaign Linked to Black Basta Ransomware Operators
Phorpiex Botnet Delivers LockBit Black Ransomware in Massive Email Campaign
Ransomware – Spam Phishing – ZIP File – Lockbit – Phorpiex Botnet – All Industries
Insights & Determinations
- The first-stage payload is ransomware, which is rare in the threat landscape but not completely unheard of.
- This is, at least, the second campaign; in an earlier campaign, the ransomware was directly executed. No network activity was observed, preventing network detections or blocks.
- This campaign likely has a low overhead, suggesting a continuance of similar tactics in future campaigns.
- Given the sheer volume of emails, future campaigns may target the same users. It’s also possible that the same targets will receive multiple phishing emails over the campaign’s lifespan.
Threat Analysis
Beginning on 24 April and continuing daily for about a week, an attacker sent millions of emails, facilitated by the Phorpiex botnet, to deliver the LockBit Black ransomware, likely built from the LockBit builder leaked in the summer of 2023.
Emails were from “Jenny Green” with the email address jenny@gsd[.]com. The email’s subject line read “Your Document” and had a ZIP file attached (Document.zip) containing a compressed executable (.exe). The email body read:
“Hello, you can find your document in the attachment.
Please reply as soon as possible.
Kind regards, GSD Support.”
The emails were sent to organizations in multiple sectors across the globe, appearing to be opportunistic rather than targeted. While the attack chain was not complex, the high volume of the emails and the use of ransomware as a first-stage payload are notable.
When the user clicks on the executable, it connects to the Phorpiex botnet infrastructure. If successful, it downloads the LockBit Black sample and executes it.
Once executed, the ransomware exfiltrated data, encrypted files, and terminated services. In earlier campaigns, the ransomware was directly executed, and no network activity was observed, preventing network detections or blocks.
This campaign has not been attributed to a known attacker due to its use of Phorpiex, and the ransomware payload was likely built with the leaked builder.
Risk & Impact Assessment
The primary risk from this attack lies in the deployment of ransomware to encrypt critical systems and steal sensitive data. The direct impacts stemming from these risks include:
- Critical systems and data can be rendered inaccessible, leading to operational downtime, lost productivity, and the costs associated with restoring systems and data from backups.
- Attackers can leverage the exposure of sensitive materials for extortion and exploit them for various malicious purposes.
- Direct financial losses, including the costs associated with incident response, ransom payments, and potential fines and penalties for failing to protect data under regulations.
Beyond these risks and impacts, organizations suffering from such attacks could face other risks and impacts, such as:
- Loss of trust among customers, partners, and stakeholders could severely damage an organization’s reputation and lead to a business decline and difficulty acquiring new customers.
- Legal risks associated with data breaches, including litigation from affected parties and penalties from regulatory bodies for failing to comply with data protection laws.
- Beyond the immediate consequences, there can be long-term strategic impacts, such as the need to overhaul cybersecurity practices, implement new security technologies, and possibly retrain staff, all of which require significant investment.
Source Material: Proofpoint, Security Brief: Millions of Messages Distribute LockBit Black Ransomware
Latest Additions to Data Leak Sites
In the past week, 205 organizations were listed on various data leak sites, with the majority operating in the Professional, Scientific, and Technical Services sector.
Analysis
Twelve ransomware data leak sites reported new organizational entries last month, with Lockbit, Play, and Medusa leading.
The vast number of organizations added to ransomware data leak sites in a single week underscores a critical threat to cybersecurity, impacting the stability and security of organizations across multiple sectors.
Lockbit led the entries, responsible for 153 new additions, accounting for 75% of all newly listed organizations.
- Play followed with 13 new additions, accounting for 6%.
- Medusa added 10 new organizations, accounting for 5%.
- Nine leak sites, from Blacksuit to Hunters International, added a combined 29 organizations, accounting for 14%.
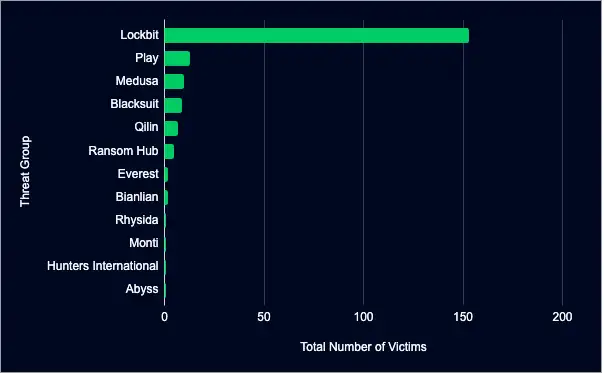
Ransomware groups are continuously evolving, targeting diverse industries, emphasizing the persistent and escalating challenge to cybersecurity defenses worldwide.
The number of organizations added indicates a trend towards high volume, where the attackers play the numbers game. The more victims, the more likely someone will pay the ransom.
Being listed on a data leak site suggests the companies faced significant operational disruptions and potentially reputational damages, highlighting the need for advanced countermeasures and robust data protection strategies.
Furthermore, the organization’s suppliers and partners could inadvertently be impacted, potentially leaking sensitive data related to these third-party organizations, exacerbating the breach’s ripple effect across the supply chain.
The significant increase in organizations listed on ransomware data leak sites in the past week highlights a critical ongoing battle in cybersecurity, urging companies to reinforce their defenses against sophisticated cyber extortion schemes.
Industry Analysis
These ransomware groups primarily targeted the Professional, Scientific, and Technical Services sectors. Of the 205 recently listed organizations, 44 are professional, scientific, and technical services firms.
- Industries such as manufacturing and information are also heavily impacted, making up 18% and 8% of new listings, respectively.
- To a lesser extent, finance and insurance and health care and social assistance accounted for 7% of new listings.
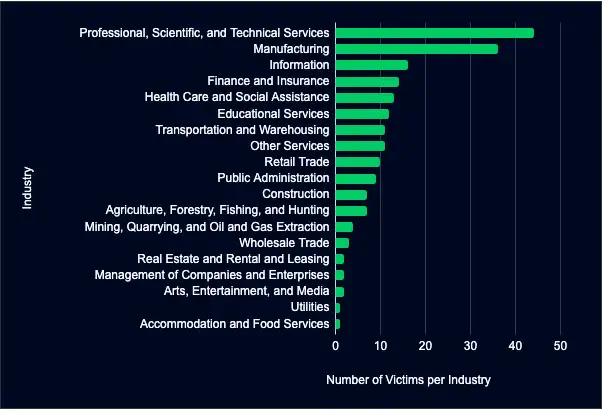
Professional, Scientific, and Technical Services firms are integral to a nation’s economy because they drive innovation, provide high-value jobs, and support various industries. They are increasingly vulnerable to cyberattacks due to the high value of their data, complex IT infrastructures, resource constraints, and the evolving threat landscape.
The increased targeting of this sector suggests a strategic strategy by cybercriminals for industries vulnerable to operational disruptions and the leaking of sensitive information.
As ransomware attacks grow in volume, critical infrastructure sectors like professional services and manufacturing face risks that could have ripple effects on trade and market stability.
- The pivotal role of the targeted sectors underscores the need for heightened cybersecurity measures and proactive threat intelligence.
- Ransomware attacks on these sectors are a stark reminder of the growing cyber threats facing industries that form the backbone of the economy.
Geographic Analysis
The United States leads in the number of organizations listed on ransomware data leak sites. These organizations represent 94 of the 205 entries, accounting for 46% of new listings.
- The United Kingdom and Canada follow with 14 (7%) and 8 (4%), respectively.
- However, organizations listed on the leak sites are located worldwide, including in Italy, Germany, Spain, the Netherlands, and Mexico.
- 19 countries have more than two listings, and 26 countries have at least one.
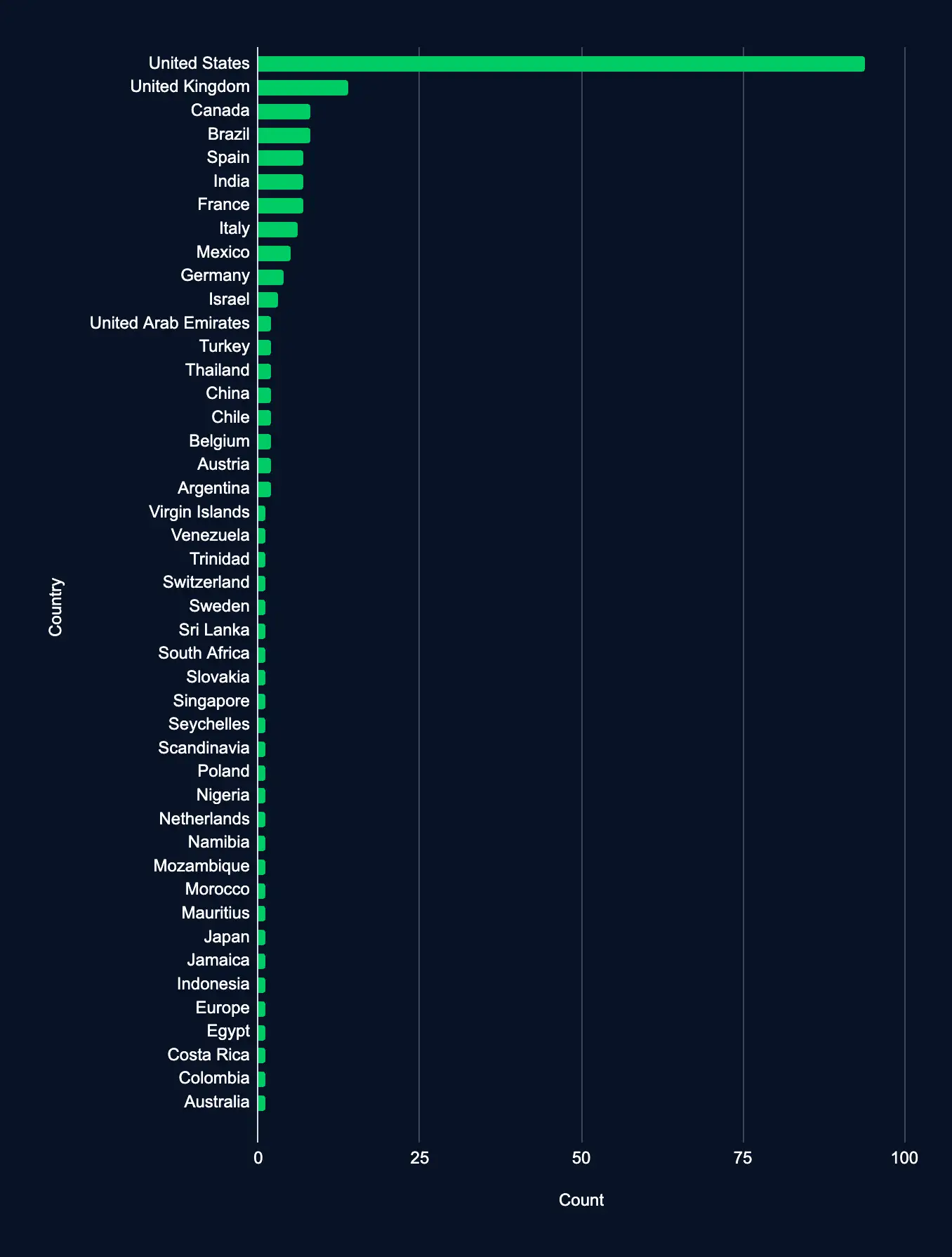
CISA Adds New Vulnerabilities to Exploited List Impacting Microsoft and Google Chromium
Microsoft DWM Core Library CVE-2024-30051 – Microsoft Windows MSHTML CVE-2024-30040 – Google Chromium Visuals CVE-2024-4671 – All Industries
The Cybersecurity and Infrastructure Security Agency (CISA) has flagged three critical vulnerabilities in Microsoft and Google Chromium as being actively exploited, escalating concerns over future cyber-attacks.
If exploited, these vulnerabilities could grant attackers high-level access and control over affected systems, posing severe organizational security and data integrity risks.
If you have questions or feedback about this intelligence, you can submit them here.
Analysis
CVE-2024-30051 – A privilege escalation flaw in Microsoft’s DWM Core Library could allow attackers to gain SYSTEM privileges. While its potential use in ransomware campaigns remains unclear, the urgency to patch this vulnerability by June 4, 2024, underscores its severity.
This vulnerability has been actively exploited as part of a QakBot malware campaign. The exploitation process for CVE-2024-30051 involves complex mechanisms that Kaspersky identified in early April 2024 through a sample uploaded to VirusTotal. The exploit allows attackers to escalate system privileges, indicating a sophisticated level of threat actor capability.
Kaspersky plans to publish technical details about this vulnerability once users have had time to update their Windows systems.
This vulnerability poses a significant risk, especially when linked with QakBot malware, suggesting that multiple cybercriminal groups could leverage it. Prompt patching and vigilance are crucial.
CVE-2024-30040 – An unspecified vulnerability in the Microsoft Windows MSHTML Platform enables security feature bypass. This issue also carries a June 4, 2024, deadline for mitigation.
This vulnerability opens doors for bypassing security features, which are critical for maintaining secure environments. The lack of details on its exploitation only adds to the urgency for organizations to apply swift mitigations, highlighting the unpredictable nature of security threats that could be lurking unseen.
CVE-2024-4671 – A use-after-free issue in Google Chromium Visuals affects multiple browsers, including Google Chrome and Microsoft Edge. This vulnerability allows remote heap corruption via a crafted HTML page, with a mitigation deadline of June 3, 2024.
This vulnerability impacts a broad range of browsers and, therefore, a vast user base. The absence of detailed exploitation information creates a pressing need for widespread awareness and immediate action among users and administrators to prevent potential attacks.
With cyber threats rising in complexity, these new entries to CISA’s catalog of known exploited vulnerabilities are a stark reminder of the continuous need for vigilance and prompt action in cybersecurity protocols.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share