BianLian Shifts Tactics Away from Ransomware, Chinese APT Earth Estries Expands Espionage Operations, 129 Firms Leaked, and CISA Highlights VMWare, Oracle, Apple, and Array Networks Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
BianLian’s New TTPs, No Longer Deploys Ransomware
The Rundown
The Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the Federal Bureau of Investigation (FBI) and the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), has issued an advisory updating the BianLian group’s techniques, highlighting new techniques. While they have historically employed a double-extortion model (data theft and encryption), the advisory reveals that they have recently shifted exclusively to exfiltration-based extortion.
BianLian’s activities have significantly impacted various industries, historically leading to operational disruptions, reputational damage, and financial losses. The group’s ability to adapt its techniques poses a persistent threat to organizations globally. The advisory emphasizes the importance of implementing robust cybersecurity measures to mitigate the risks associated with such ransomware groups.
Source Material: CISA
Inside the Espionage Operations of the Chinese APT Earth Estries
The Rundown
Trend Micro has released an analysis of Earth Estries’ command and control (C2) infrastructure, an advanced persistent threat (APT) group that has been conducting cyber espionage since at least 2020. Earth Estries has focused its efforts on telecommunications, technology, consulting, chemical, and transportation industries, government agencies, and non-profit organizations (NGOs), impacting entities in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the United States.
The report details the group’s use of multiple backdoors and advanced hacking tools to infiltrate and maintain long-term access to targeted systems. Earth Estries shares operational similarities with the APT groups FamousSparrow and GhostEmperor, showcasing overlaps in tactics, techniques, and procedures.
The group’s strategy of leveraging well-known public services underscores the risks posed by APTs exploiting legitimate infrastructure for malicious purposes, complicating detection efforts. The ongoing activity of Earth Estries highlights the persistence of nation-state-aligned actors targeting government and technology sectors worldwide.
Source Material: Trend Micro
Leak Sites: 129 Firms Listed, Professional Services Tops the List
The Rundown
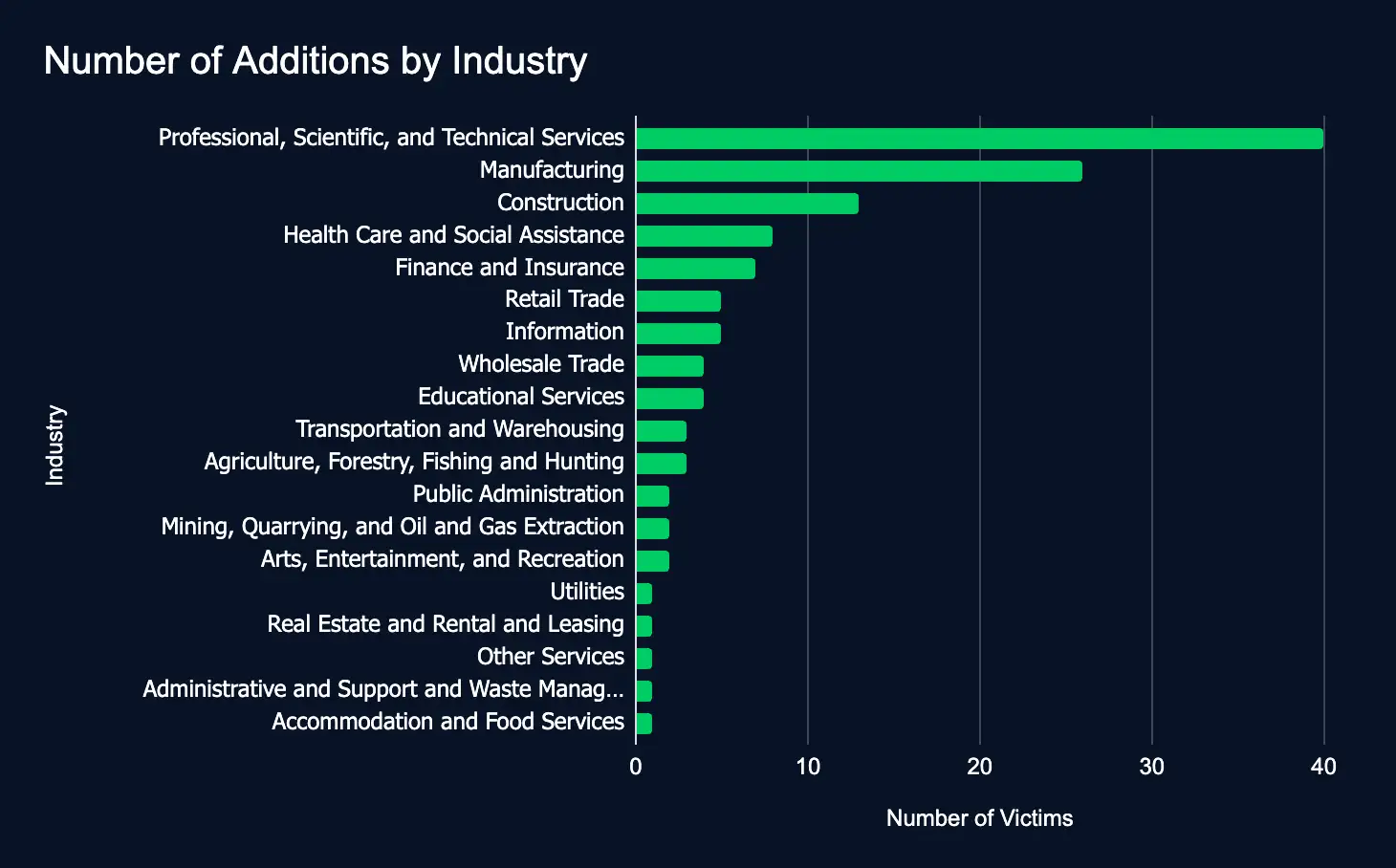
In just one week, 129 organizations spanning 19 industries were added to ransomware and data leak sites—an increase of 60 organizations from the previous week.
This week, critical sectors such as Professional, Scientific, and Technical Services, Manufacturing, and Construction were most frequently targeted, underscoring the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and ensure operational resilience globally.
CISA Adds VMWare, Oracle, Apple, and Array Networks Vulnerabilities to Exploited List
The Rundown
Between November 20 and 25, six vulnerabilities affecting VMWare, Oracle, Apple, and Array Networks products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. Failure to patch these flaws could lead to data exposure, privilege escalation, or code execution. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share