Phishing Campaign Deploys RATs and Infostealers, Rhadamanthys Infection Chain Analyzed, 81 Firms Leaked, and CISA Adds North Grid, ProjectSend, and Zyxel Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Phishing Email Leads to Infection of Multiple RATs and an Infostealer
The Rundown
A recent Field Effect blog post explores the impact of undetected threats within organizational networks. It focuses on a simulated scenario in which a malicious email attachment is allowed to execute. The scenario illustrates the attack chain if it was not prevented.
The attack begins with an email containing an HTML attachment exploiting CVE-2024-38213. This vulnerability bypasses Windows’ “Mark of the Web” feature, allowing potentially unsafe files to execute without user warnings. Upon opening, a batch script deploying several Remote Access Trojans (RATs) and an infostealer, enabling remote surveillance, keystroke logging, and data exfiltration.
The malware, if undetected, introduces severe risks, including unauthorized surveillance, privilege escalation, lateral movement, and potentially leading to ransomware deployment. These threats underscore the importance of comprehensive cybersecurity, including effective threat detection and response (MDR), regular software updates, phishing awareness, and vigilant monitoring to counter similar types of attacks.
Source Material: Field Effect
Inside Rhadamanthys Infection Chain, and the Commands Executed
The Rundown
Binary Defense has published an analysis of Rhadamanthys Stealer, a malware targeting sensitive information across various endpoints. This info-stealer extracts browser-stored credentials, cryptocurrency wallet keys, and system information. The analysis identifies the malware’s operational mechanisms and provides detection opportunities for cybersecurity professionals.
Rhadamanthys Stealer employs evasion techniques, including code obfuscation and anti-analysis tools, to avoid detection by traditional security measures. It is primarily distributed through phishing emails, malicious attachments, and compromised websites, leveraging user interaction to initiate infection. Once executed, the malware establishes a connection to command-and-control servers to exfiltrate the stolen data.
The threat posed by Rhadamanthys Stealer is significant, given its ability to compromise critical assets such as financial information and authentication credentials. Its advanced stealth mechanisms increase the challenge for defenders, making early detection through network traffic monitoring and behavioral analysis essential. The malware’s reliance on phishing vectors underscores the importance of robust email security solutions and user education to mitigate risks.
This analysis highlights the necessity for proactive defense measures against emerging information-stealing malware. Organizations must integrate advanced detection tools to address this evolving threat effectively, educate users on identifying phishing attempts, and enhance network monitoring capabilities.
Source Material: Binary Defense
Leak Sites: 81 Firms Listed, Manufacturing Tops the List
The Rundown
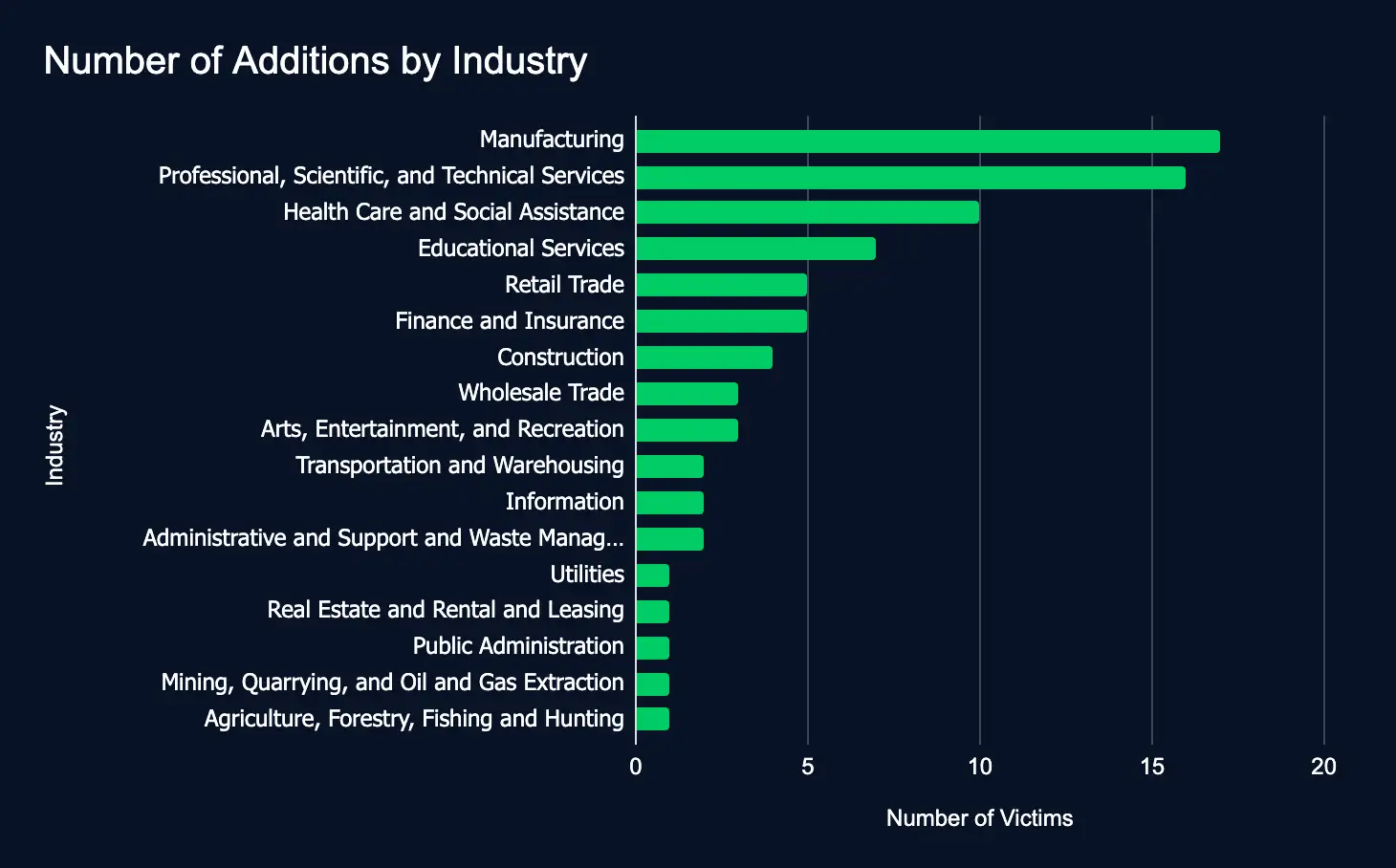
In just one week, 81 organizations spanning 17 industries were added to ransomware and data leak sites, a decrease of 48 from the previous week.
This week, critical sectors such as Manufacturing, Professional, Scientific, and Technical Services, as well as Health Care and Social Assistance, were most frequently affected, underscoring the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and ensure operational resilience globally.
CISA Adds North Grid, ProjectSend, and Zyxel Vulnerabilities to Exploited List
The Rundown
Between November 28 and December 04, three vulnerabilities affecting North Grid, ProjectSend, and Zyxel products were added to CISA’s Known Exploited Vulnerabilities catalog. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. Failure to patch these flaws could lead to data exposure, admin access, malware upload, and/or malicious code execution. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share