Threat Actors Exploit Teams, SharePoint, and OneDrive for Stealthy Malware Delivery, New ZIP File Tactic Unveiled, 142 Firms Leaked with Professional Services Hit Hardest, and CISA Adds Key Vendor Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Threat Actors Leverage Teams, SharePoint, and OneDrive to Bypass Detection and Deploy Malware
- New ZIP File Tactic Lets Malware Hide in Plain Sight
- Leak Sites: 142 Firms Listed, Professional Services Tops the List
- CISA Adds Android, Atlassian, Cisco, CyberPanel, Microsoft, Metabase, Nostromo, and Palo Alto Vulnerabilities to Exploited List
Threat Actors Leverage Teams, SharePoint, and OneDrive to Bypass Detection and Deploy Malware
The Rundown
A social engineering attack leveraged Microsoft Teams, SharePoint, and OneDrive to infiltrate a U.S. critical infrastructure organization. The attackers were able to deploy a remote access tool and Java-based malware.
This incident underscores the increasing sophistication of social engineering attacks. It potentially highlights a significant weakness in current detection frameworks, where cybercriminals leverage legitimate SaaS platforms to execute commands while evading advanced security measures.
Source Material: Hunters
New ZIP File Tactic Lets Malware Hide in Plain Sight
The Rundown
Attackers have found a way to hide malware within concatenated ZIP files, bypassing common detection tools and putting organizations at risk of undetected attacks.
This ZIP concatenation tactic could represent an emerging evasion technique and reveal a troubling gap in popular ZIP readers and security tools. If successful, it could pose a significant cybersecurity threat, and security teams must adapt to counter hidden payloads embedded in routine attachments.
Source Material: Perception Point
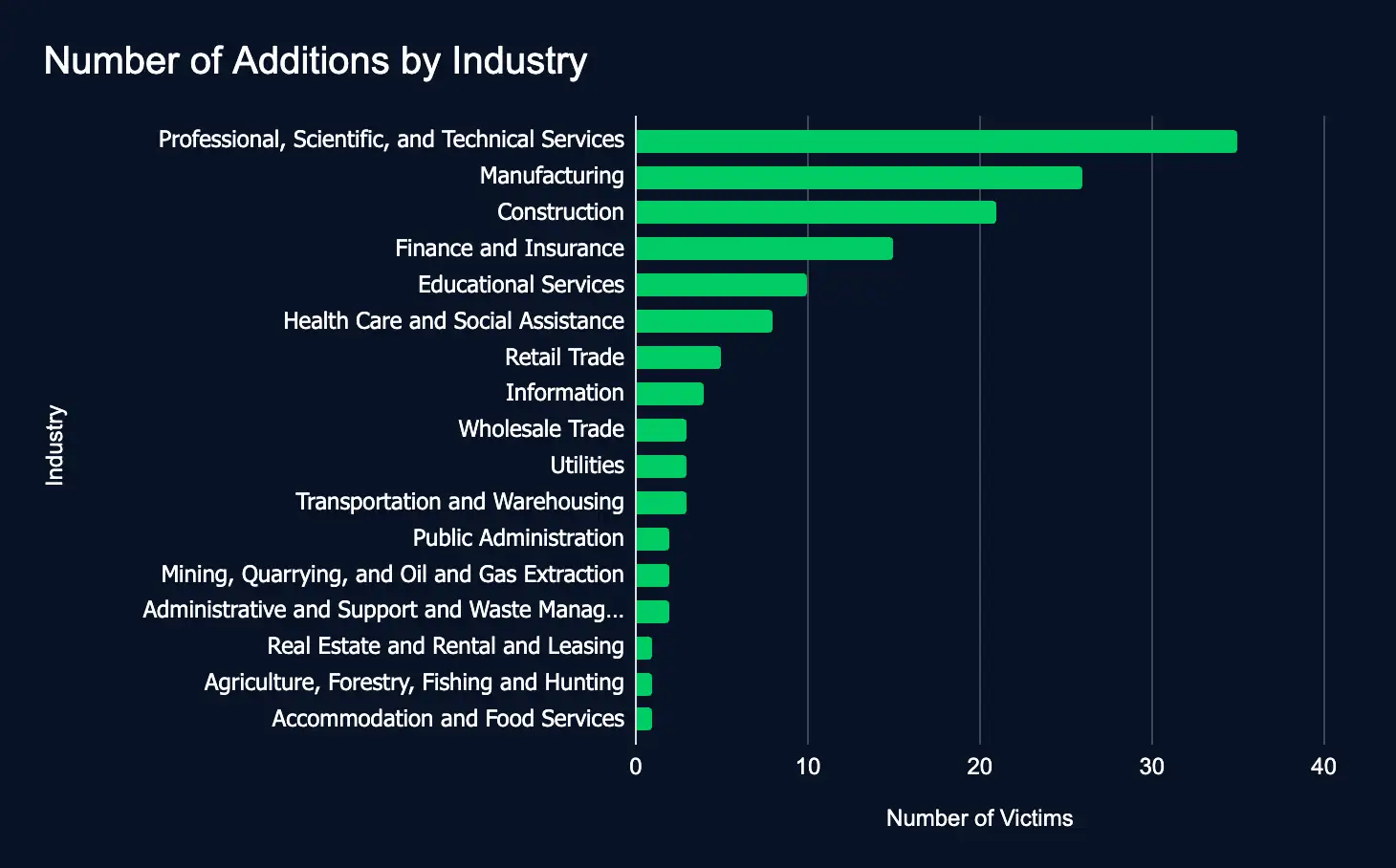
Leak Sites: 142 Firms Listed, Professional Services Tops the List
The Rundown
In just one week, 142 organizations spanning 17 industries were added to ransomware and data leak sites—an increase of 35 from the previous week.
This week, critical sectors such as Professional, Scientific, and Technical Services, Manufacturing, and Construction were most frequently targeted, underscoring the pressing need for comprehensive cybersecurity measures to safeguard sensitive data and ensure operational resilience globally.
CISA Adds Android, Atlassian, Cisco, CyberPanel, Microsoft, Metabase, Nostromo, and Palo Alto Vulnerabilities to Exploited List
The Rundown
Between November 7th and 13th, nine vulnerabilities affecting Android, Atlassian, Cisco, CyberPanel, Microsoft, Metabase, and Palo Alto products were added to CISA’s Known Exploited Vulnerabilities catalog. Without prompt mitigation, these vulnerabilities could leave organizations vulnerable to cyberattacks.
These newly exploited vulnerabilities underscore significant risks for organizations relying on widely used technologies. Failure to address these flaws could result in privilege escalation, data exposure, or arbitrary code execution. With state-sponsored actors and cybercriminals potentially targeting these weaknesses, swift action will be essential to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share