Vulnerability in JetBrains TeamCity Servers, Massive Attacks lead to Cryptomining and Backdoors, SSH Servers Offer Threat Actors Opportunities, and New Dual DLL Sideloading Technique Deploys QasarRat.
This week: North Korean threat actors exploit vulnerability in JetBrains TeamCity Servers; massive attacks lead to cryptomining and backdoor access; a story about blocking ransomware; and new dual DLL Sideloading technique deploys QasarRat–all of this plus the latest from data leak sites. And in a rare instance, CISA has no new CVEs to report this week!
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- North Korean Threat Actors Exploited Vulnerability in JetBrains TeamCity Servers to Deliver Malware
- 10,000 Attacks Lead to Cryptomining, Keylogging, and Backdoor Access
- Robust Defenses Block Threat Actor From Deploying Ransomware
- SSH Servers Offer Threat Actors a World of Opportunities
- Threat Actors Use Dual DLL Sideloading to Deploy QasarRAT
- Latest Additions to Data Leak Sites
- CISA Adds No CVEs This Week to Its Know Exploited Vulnerabilities Catalog
North Korean Threat Actors Exploited Vulnerability in JetBrains TeamCity Servers to Deliver Malware
JetBrains TeamCity Server CVE-2023-42793 – Diamond Sleet – Onyx Sleet – ForestTiger – HazyLoad – Vulnerability Exploitation – Public Administration – Information
Overview & Background
The blog post from Microsoft Threat Intelligence titled “Multiple North Korean threat actors exploiting the TeamCity CVE-2023-42793 vulnerability” details the exploitation of the TeamCity CVE-2023-42793 vulnerability by two North Korean nation-state threat actors, Diamond Sleet and Onyx Sleet. The blog post aims to inform and alert the cybersecurity community and affected organizations about the tactics, techniques, and procedures (TTPs) employed by these threat actors in their exploitation campaigns. The blog post analyzes the specific methods these threat actors use, the profile of victim organizations affected by these intrusions, and the tools and techniques following successful exploitation.
CVE-2023-42793 is a remote code execution vulnerability affecting JetBrains TeamCity server versions before 2023.05.4, a widely used DevOps and software development application for continuous integration/continuous deployment (CI/CD). Diamond Sleet is a North Korean nation-state threat actor with a history of espionage, data theft, financially motivated attacks, and network destruction. Their previous activities include targeting security researchers and the Information and Defense-related sectors and weaponizing open-source software. Onyx Sleet is another North Korean threat actor primarily targeting various countries’ Defense and Information sectors. They employ custom tools and frequently exploit known vulnerabilities (N-day) to gain initial access.
Threat Analysis
Two distinct attack paths characterize Diamond Sleet’s exploitation of the TeamCity CVE-2023-42793 vulnerability. In the first attack path, upon successful compromise, Diamond Sleet employed PowerShell to download the ForestTiger backdoor (Forest64.exe) and a configuration file (4800-84DC-063A6A41C5C) containing parameters such as the command and control (C2) infrastructure, hosted on previously compromised legitimate infrastructure. These files are saved to the C:\ProgramData directory. ForestTiger checks for the presence, reads, and decrypts the configuration file when executed. Then, ForestTiger creates a scheduled task and performs LSASS credential dumping.
Diamond Sleet’s second attack path uses PowerShell on compromised servers to download a malicious DLL from actor-controlled infrastructure. This DLL is then staged alongside a legitimate .exe file to execute a DLL search-order hijacking attack. Two combinations observed include DSROLE.dll loaded by wsmprovhost.exe and Version.dll loaded by clip.exe. The DSROLE.dll, when loaded, processes files in its executing directory, revealing an executable payload staged in memory. The functionality of DSROLE.dll is ultimately decided by whatever payload it launches; it has been observed launching a payload to communicate with C2 domains. The Version.dll, on the other hand, decrypts the contents of a file downloaded alongside the DLL named readme.md to decrypt code in Version.dll, which, when executed, launches the final-stage remote access trojan (RAT), which communicates with several URLs decrypted from a configuration file. After a successful compromise, Diamond Sleet dumped credentials via the LSASS memory. In some cases, Diamond Sleet utilized tools and techniques from both paths.
Onyx Sleet’s attack path is distinct from Diamond Sleet’s methods. Following successful exploitation, Onyx Sleet creates a new user account on compromised systems, named krtbgt, and adds it to the Local Administrators Group. The threat actors likely used this name to evade detection by mimicking the legitimate Windows account name KRBTGT. Onyx Sleet also executes several system discovery commands on compromised systems, gathering information about users, running tasks associated with the term “Sec,” network connections, and system information. Then, they use PowerShell to download from actor-controlled infrastructure a unique payload. This payload, when launched, decrypts, loads, and executes an embedded payload (HazyLoad) directly in memory to establish a persistent connection between the compromised host and the actor-controlled infrastructure. Post-compromise activities observed include:
- Used the krtbgt account for remote desktop protocol (RDP) access.
- Stopped the TeamCity service.
- Dumped credentials from LSASS memory.
- Deployed tools to retrieve browser-stored credentials.
Diamond Sleet and Onyx Sleet have demonstrated a clear objective in exploiting the TeamCity CVE-2023-42793 vulnerability to gain an initial foothold in targeted systems. Their goals include compromising systems, maintaining access through user account creation, dumping LSASS memory for credential access, retrieving browser-stored credentials, and halting specific services. Their capabilities include exploiting known vulnerabilities, leveraging PowerShell for various tasks, access to or the resources to establish infrastructure, access to or the ability to compromise legitimate infrastructure, access to or the resources to develop and deploy ForestTiger and HazyLoad, and utilizing encryption and decryption techniques.
Given the nature of their activities, including credential dumping and system discovery, their intentions align with a focus on intelligence collection or a financial motive. If they intend to collect intelligence, they aim to gather sensitive information for political, economic, or strategic advantage. Their activities could result in data theft, extortion, or cryptomining if they have a financial motive. Their operations’ sophistication and the resources at their disposal further underscore their alignment with nation-state objectives and the strategic nature of their campaigns.
Risk & Impact Assessment
If threat actors successfully exploit the TeamCity CVE-2023-42793 vulnerability, organizations face significant operational, financial, and strategic risks and impacts. Operational disruptions from halted services can delay critical processes, increasing costs and inefficiencies. Concurrently, data breaches, marked by unauthorized access to sensitive information, can result in regulatory fines, legal actions, and substantial reputational damage. The potential theft of intellectual property jeopardizes an organization’s competitive edge. The immediate financial strain encompasses direct losses from disrupted operations and augmented costs of incident response, system remediation, and bolstered cybersecurity measures. These risks and impacts collectively underscore a successful cyberattack’s profound implications, emphasizing the imperative for robust preventive and responsive strategies.
Source Material: Microsoft Threat Intelligence: Multiple North Korean threat actors exploiting the TeamCity CVE-2023-42793 vulnerability
10,000 Attacks Lead to Cryptomining, Keylogging, and Backdoor Access
Cryptocurrency Mining – Keylogging – Backdoor – Public Administration – Agriculture, Forestry, Fishing and Hunting – Wholesale Trade – Retail Trade
Overview & Background
The blog post from Securelist (Kaspersky) titled “Money-making scripts attack organizations” details cybercriminal activities targeting various organizations, where a threat actor(s) downloaded malicious scripts onto victims’ devices. These scripts serve multiple malicious purposes: they harness company resources for cryptocurrency mining, capture data using keyloggers, and establish backdoor access to the compromised systems. The blog post aims to describe this multifaceted cyber threat and provide insights into its mechanics and implications. The blog post analyzes telemetry data, indicators of compromise, and specific malicious scripts and executables to understand this ongoing threat.
Threat Analysis
Following an FBI TLP:AMBER Flash advisory in April this year, Kaspersky, leveraging their telemetry data, investigated the Indicators of Compromise (IOCs) disseminated by the FBI. Kaspersky detected numerous scripts, executables, and associated links related to this campaign since late 2022. Indirect evidence suggests that the scripts penetrate the target infrastructure mainly due to exploiting vulnerabilities on servers and workstations. Among the scripts discovered, Securelist identified two previously unpublished malicious scripts (start.cmd and runxm1.cmd) that manipulate Windows Defender. The FBI Flash (publicly disclosed by Kaspersky) disseminated known IOCs and TTPs associated with attacks targeting products of an equipment distributor used by government, law enforcement, and non-profit organizations.
The first script (start.cmd) tries to disable protection through the registry. If this is successful, the second (runxm1.cmd) adds several files to exceptions, which are used at different stages of the attack, obtains administrator rights, and renames folders of known security solutions to prevent them from running on the infected device. Both scripts then access a domain hosting a real-time cryptocurrency exchange rate platform, from which they attempt to download various executable and configuration files. These files include intelsvc.exe, View.exe, rtkaudio.exe/rtkaudio.txt, and config.txt.
Upon further analysis, start.cmd was observed trying to run RtkAudio.exe using the configuration file config.txt. This configuration file explicitly refers to a Monero cryptocurrency (XMR) miner. Another executable, View.exe, ran by start.cmd saves several files to the path C:\Users\Public, including copies of IntelSvc and RtkAudio, among others. One of these other files, Systemfont.exe, was identified as a keylogger, capturing keystrokes and saving them in an archive named tempfont.rar.
Furthermore, IntelSvc.exe, also run by start.cmd, behaves like a backdoor and is capable of executing a variety of commands. Once started, it creates a folder to store configuration files and logs in the ProgramData directory named USOShared. Some files saved in USOShared are log.json and web.ttf. The backdoor sends a request to its command and control (C2) server approximately once a minute and overwrites the file log.json while waiting for commands. The web.ttf file contains the IP address of the C2 server (89.40.115[.]70:5665).
Kaspersky found that since May 2023, over 10,000 attacks have been detected, impacting more than 200 users worldwide. These attacks predominantly target the business-to-business (B2B) sector, encompassing large enterprises and small to medium-sized businesses across various sectors, including Public Administration, Agriculture, Forestry, Fishing and Hunting, and Wholesale and Retail Trade. The most affected countries include the Russian Federation, Saudi Arabia, Vietnam, Brazil, and Romania, with isolated attacks in the United States, India, Morocco, and Greece.
The threat actor(s) demonstrated a multifaceted approach, potentially leveraging exploits in servers and workstations, thereby gaining unauthorized access to deploy self-developed or acquired malware. They aim to manipulate Windows Defender, harness compromised resources for Monero cryptocurrency mining, capture sensitive data through keyloggers, and maintain access and perform other malicious activities through a backdoor. Given the attacks’ scale and objectives, it’s evident that the intention revolves around financial gain and/or intelligence collection, with the capability and potential intent for broader disruption.
Risk & Impact Assessment
If the threat actor(s) successfully deploys the described scripts, organizations face significant risks that could materially impact their operations, data, and assets. The deployment of crypto miners strains system resources, leading to operational disruptions and delays. Keyloggers threaten data confidentiality, increasing the risk of data breaches with associated legal, regulatory, and reputational implications. While there’s a remote chance of accidental data modification or destruction, the primary financial impacts would stem from increased operational costs, potential loss of business, regulatory fines, and increased security expenditures for mitigation and recovery. These risks underscore the potential for substantial short-term operational challenges and long-term financial and reputational repercussions.
Source Material: SecureList/Kaspersky: Money-making scripts attack organizations
Robust Defenses Block Threat Actor From Deploying Ransomware
BlackDog 2023 Ransomware – Adobe ColdFusion – Vulnerability Exploitation – Cobalt Strike – Industries/All
Overview & Background
The blog post from Sophos X-Ops titled “Ransomware actor exploits unsupported ColdFusion servers—but comes away empty-handed” details the efforts of a previously unknown actor attempting to exploit vulnerabilities in obsolete, unsupported versions of Adobe’s ColdFusion Server software. Their objective was to gain access to Windows servers and subsequently deploy ransomware. The blog post aims to shed light on these unsuccessful attacks, providing insights into the tactics, techniques, and procedures (TTPs) used by the threat actor. The blog post analyzes telemetry from targeted servers, the actors’ tools and techniques, and the payloads they attempted to deploy.
Threat Analysis
The threat actor initiated their attack by targeting an unknown vulnerability in an unsupported version of Adobe’s ColdFusion Server. On 20 September, after gaining initial access, the threat actor began their infiltration by testing the server’s vulnerability to remote attacks. At 4:30 AM EST, they executed a ping command directed at an “oastify[.]com” subdomain connected to the Burp Collaborator Server to determine if it was susceptible to a remote attack. The server’s endpoint protection silently detected and permitted this ping command.
By 04:38, having confirmed the server’s connectivity to a remote domain, the actor executed an “Invoke EXpression” (IEX) PowerShell command to run a remote PowerShell script to download and deploy a Cobalt Strike “beacon.” However, a behavioral rule blocked this action. Despite multiple attempts, the actor’s efforts to deploy the Cobalt Strike Beacon were consistently thwarted by the same rule.
At 7:37 AM EST, the actor performed another “ping” command for a different oastify[.]com subdomain; again, this was permitted. By 7:45, they tried using certutil.exe (the Windows command-line Certificate Services utility) to launch an executable version of the CobaltStrike beacon, which the behavioral rule blocked. The actor persisted, attempting multiple deployment methods, including an interactive reverse PowerShell and loading an encoded Cobalt Strike Beacon loader directly into memory, but these attempts were blocked.
Five days later, on 25 September, the actor returned, trying their original attack method, which was again blocked. They initiated a “ping” test against another oastify[.]com subdomain the following day. Despite further code modifications to evade detection, their attempts to load an encoded Cobalt Strike Beacon into memory were again thwarted. They also tried leveraging certutil.exe to deploy another newly compiled beacon but to no avail.
In a final series of attempts on 26 September, the actor used an HTA (HTML Application) file to initiate PowerShell to deploy a Cobalt Strike Beacon, which another behavioral rule blocked. Growing increasingly desperate, the actor made numerous additional attempts using HTA files and Cobalt Strike binaries. However, all their efforts were consistently blocked.
Further investigation into the actor’s activities revealed an inadvertent exposure on their part. They had unintentionally left directory listings enabled on the web server hosting their repository of tools. This oversight allowed for a deeper exploration of its contents. Within this repository, not only were all the artifacts the actor had tried to deploy in the targeted environment discovered, but also the final ransomware payload they intended to deploy. This ransomware variant, “BlackDog 2023,” seemed to be based on the leaked source code of Lockbit 3.0. This association was evident when examining both the static executable file’s properties and the similarities in the unpacked code in memory. The ransom note accompanying the ransomware demanded a payment of 205 Monero, equivalent to approximately $30,000 US. The ransom note threatened that failure to pay would result in the threat actor publishing the stolen data on a TOR website.
The threat actor’s focus on exploiting vulnerabilities in unsupported versions of Adobe’s ColdFusion Server software presents a significant risk to organizations still utilizing outdated systems. Their demonstrated technical proficiency, adaptability, and persistence amplify the potential impact of a successful breach. While their primary intention appears to be financial gain, the threat of data exfiltration and publication could see other threat actors accessing the data for intelligence collection to facilitate their malicious activities. Additionally, the inadvertent exposure of their tool repository suggests that while they possess advanced capabilities, defensive measures can exploit operational security lapses.
Risk & Impact Assessment
Organizations face profound operational, financial, and reputational repercussions if the threat actors successfully exploit vulnerabilities, deploy ransomware, and exfiltrate and disclose sensitive data. Operational disruptions could halt essential services, leading to direct financial losses from ransom payments, system restorations, and potential legal fees. Such disruptions might also result in significant revenue declines as customers seek alternatives due to service unavailability or eroded trust. The unauthorized disclosure of sensitive data, especially if made public, could tarnish an organization’s reputation, leading to long-term trust issues with stakeholders and potential legal and regulatory sanctions. Additionally, post-incident costs, including bolstered cybersecurity measures and support for affected parties, could further strain organizational resources and finances.
Source Material: Sophos X-Ops: Ransomware actor exploits unsupported ColdFusion servers—but comes away empty-handed
SSH Servers Offer Threat Actors a World of Opportunities
SSH – Brute Force Attacks – Phishing Campaigns – Cryptomining – Industries/All
Overview & Background
The blog post from Aqua Nautilus titled “Exploited SSH Servers Offered in the Dark Web as Proxy Pools,” drawing on data derived from Aqua’s SSH honeypot servers, details how threat actors can abuse SSH servers for malicious activity. The blog post aims to shed light on the long-standing threat to SSH in the cloud, particularly how threat actors harness SSH servers to use as proxies and pass traffic through them. The blog post analyzes the techniques of SSH tunneling and the implications of these attacks on organizations and businesses and provides evidence from honeypots that observed these SSH campaigns.
SSH tunneling is a technique used to establish secure and encrypted network connections between two servers, allowing data to traverse safely over an untrusted network. Its primary purpose is to create a secure communication channel between a local and a remote host, which can then be utilized to tunnel various network protocols and services. Threat actors abuse this secure communication method for malicious purposes and offer them on the dark web as part of proxy pool packages, which threat actors can use for various malicious activities, including spam dissemination.
Honeypots are designed to attract and deceive threat actors by simulating real systems that threat actors may target. Sometimes, they may be vulnerable or poorly configured, providing easy access for threat actors. The purpose of a honeypot is to gather information about threat actor methods, techniques, and objectives. There are different types of honeypots, including low-interaction, high-interaction, and hybrid honeypots. Low-interaction honeypots simulate only a few services, such as a web or email server. High-interaction honeypots simulate an entire system, including the operating system and applications. Hybrid honeypots combine elements of both. Cybersecurity professionals can gain valuable insights by analyzing the activities conducted on honeypots.
Threat Analysis
Threat actors can gain initial access primarily through brute-force attacks on SSH servers or conduct post-exploitation lateral movements to establish SSH connections. Threat actors can use various SSH versions, such as OpenSSH, Paramiko, libssh, NmapSSH, WinSCP, etc, in their attacks.
Threat actors can use compromised SSH servers for spam email campaigns using online web services or ESMTP and SMTP protocols, allowing threat actors to hide the true origin of the emails. Many of the connections observed by Aqua communicated with domains such as Gmail, iCloud, Microsoft, and Discord. Aqua also observed cryptomining activities and various scripts being run.
Threat actors can also execute domain lookup requests to retrieve ‘Whois’ data and geolocation requests for IP addresses and API requests to obtain information about the server or user. Many threat actors will use the seemingly benign request to identify potential targets. Threat actors can also sell access to compromised SSH servers on the dark web as part of proxy pool packages. These packages allow threat actors to route their malicious traffic through, making attribution and detection exceedingly more difficult as the traffic originates from a legitimate source. Chinese APTs are known for using extensive multi-tiered proxy networks to filter their traffic through.
Risk & Impact Assessment
Threat actors can gain complete control over a server through compromised SSH access. Even if you are dealing only with SSH tunneling, it can have a significant impact. The organization’s IP address’s reputation can be severely tarnished, potentially leading to IP address bans that disrupt outbound email, data, or other traffic. Your business reputation may also suffer due to associations with fraudulent or malicious activities. Therefore, even without experiencing a data breach, these types of attacks can still negatively affect your business.
Source Material: Aqua: Exploited SSH Servers Offered in Dark Web as Proxy Pools
Threat Actors Use Dual DLL Sideloading to Deploy QasarRAT
QasarRat – DLL Sideloading – Remote Administration Tool – Process Hollowing – Industries/All
Overview & Background
The blog post from Uptycs titled “Double Trouble: Quasar RAT’s Dual DLL Sideloading in Focus” provides an in-depth analysis of a sophisticated cyber threat involving QuasarRAT, a well-known remote administration tool. The threat actors behind this campaign have ingeniously implemented a novel dual DLL sideloading technique, leveraging two commonly trusted Microsoft files: “ctfmon.exe” and “calc.exe.” This method not only exploits the inherent trust placed in these files within the Windows ecosystem but also poses a significant challenge to threat detection mechanisms. The blog post aims to dissect the intricate design and execution of these sideloading techniques, shedding light on how they stealthily introduce, deploy, and run malicious payloads while evading detection.
QuasarRAT is a lightweight remote administration tool written in C#. It is openly accessible as a GitHub project, making it easily obtainable by cybercriminals. QuasarRAT allows threat actors to gather system information, run applications, log keystrokes, execute shell commands, and perform various other malicious activities on the infected machines. It is known for its versatility, and multiple threat groups have used it due to its public availability. QuasarRAT can be customized and modified by different actors to add extra capabilities or tailor it to their specific needs. The dual DLL sideloading technique highlighted in the Uptycs blog post represents a significant evolution in the deployment of QuasarRAT, underscoring the need for advanced threat detection and response mechanisms to counteract this evolving threat.
Threat Analysis
The attack commences with the threat actor utilizing DLL sideloading techniques, using “ctfmon.exe,” a trusted Microsoft file, to initiate their malicious activities. This strategic choice exploits the file’s inherent trust within the Windows ecosystem, setting a deceptive stage. Upon execution of “ctfmon.exe,” a disguised malicious DLL is loaded, marking the deployment of the ‘stage 1’ payload and paving the way for further malicious actions.
The ‘stage 1’ payload plays a crucial dual role in this attack. It is responsible for releasing both the legitimate “calc.exe” file and an additional malicious DLL into the system, intricately weaving the attacker’s malicious intent into the fabric of the compromised environment. The second phase of the attack sees the execution of “calc.exe,” but this is no ordinary calculator application. Alongside it, the malicious DLL springs into action, facilitating the infiltration of the QuasarRAT payload into the computer’s memory. This maneuver demonstrates the attacker’s adeptness at circumventing established security mechanisms, showcasing a high level of sophistication.
With the QuasarRAT payload now residing in the computer’s memory, the attacker employs a technique known as ‘process hollowing.’ This technique allows the payload to embed itself within a legitimate system process, effectively camouflaging its malicious nature and complicating detection efforts. This level of obfuscation speaks volumes about the complexity of the attack, highlighting the lengths to which the threat actors are willing to go to remain undetected.
A technical malware analysis reveals a meticulous design, with encrypted data stored within a DLL file. The attacker utilizes a series of API calls to access resources, decrypt data, and inject the payload into memory, ultimately leading to the execution of the final payload. This analysis describes the attacker’s methodology but also underscores the necessity for advanced threat detection and response mechanisms capable of identifying and mitigating such evolved and stealthy cyber threats.
The QuasarRAT’s dual DLL sideloading technique represents a significant evolution in cyber threat tactics, demonstrating a high level of sophistication and posing a formidable challenge to traditional threat detection mechanisms. The analysis underscores the importance of remaining vigilant and employing advanced security measures to protect against such complex and elusive threats.
The threat actors behind this QuasarRAT campaign exhibit a clear intention to compromise and control targeted systems, demonstrating advanced capabilities in malware deployment and evasion. Their objective is to stealthily infiltrate systems, utilizing the dual DLL sideloading technique to bypass traditional security measures and establish a persistent presence. By employing trusted Microsoft files as part of their attack vector, they aim to exploit the inherent trust placed in these files, thereby reducing the likelihood of detection. The use of QuasarRAT, a versatile and widely accessible remote administration tool, further indicates their capability to perform a variety of malicious activities ranging from data exfiltration to system manipulation. The meticulous design and execution of the attack, coupled with the use of advanced techniques such as process hollowing, highlight the threat actors’ proficiency and adaptability, marking them as a significant threat in the cyber landscape.
Risk & Impact Assessment
This QuasarRAT campaign, leveraging its novel dual DLL sideloading technique, introduces substantial risks to targeted systems, predominantly threatening the confidentiality, integrity, and availability of organizational data and operations. The exploitation of trusted Microsoft files significantly elevates the chance of successful infiltration, potentially leading to unauthorized access to sensitive information, thereby compromising confidentiality. The extensive capabilities of Quasar RAT enable threat actors to manipulate system processes and data, posing a direct threat to the integrity of the compromised system. Additionally, the ability to execute arbitrary commands and potentially disrupt critical operations puts the availability of organizational resources at risk. The material impact of such a compromise is considerable, with potential repercussions including severe data breaches, loss of intellectual property, disruption of operations, and damage to the organization’s reputation. The sophistication of the attack, coupled with advanced evasion techniques, necessitates a robust and proactive cybersecurity posture to mitigate these risks and safeguard the organization against the potentially severe impacts of this threat.
Source Material: Uptycs: Double Trouble: Quasar RAT’s Dual DLL Sideloading in Focus
Latest Additions to Data Leak Sites
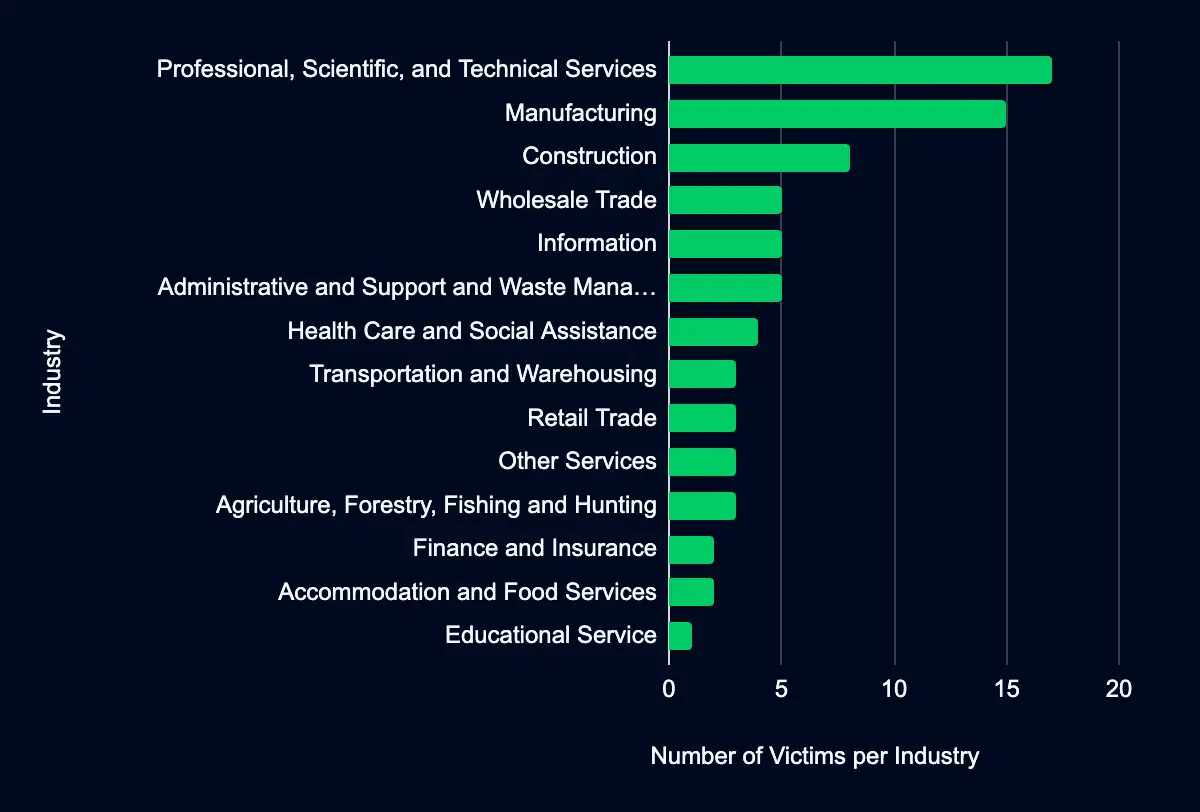
Professional, Scientific, and Technical Services – Manufacturing – Construction – Wholesale Trade – Information
In the past week, monitored data extortion and ransomware threat groups added 76 victims to their leak sites. Of those listed, 47 are based in the USA. Professional, Scientific, and Technical Services was the most affected industry, with 17 victims. Fifteen victims follow this industry in Manufacturing, eight victims in Construction, and five victims in Wholesale Trade and Information. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds No CVEs This Week to Its Know Exploited Vulnerabilities Catalog
In a rare instance, CISA did not add a single new CVE to its Known Exploited Vulnerabilities Catalog. They’re still out there, they just haven’t been reported yet.
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share