MedusaLocker Variant BabyLockerKZ Spreads Globally, Zimbra RCE Exploited in Phishing Attacks, 64 Firms Leaked with Professional Services Hit Hardest, and CISA Adds Synacor, Microsoft, and Qualcomm Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
MedusaLocker Variant BabyLockerKZ Spreads Globally
The Rundown
A financially-motivated attacker has been targeting over 100 organizations monthly since 2022, using a new MedusaLocker ransomware variant, BabyLockerKZ, and a collection of custom and publicly available tools to steal credentials and spread within compromised networks.
Ransomware like BabyLockerKZ can cripple a business by locking vital systems and encrypting data, demanding payment for their release, often leading to severe financial loss, operational disruption, and damage to reputation.
Source Material: Cisco Talos
Critical Zimbra RCE Vulnerability Exploited in Phishing Attacks
The Rundown
A critical vulnerability in Zimbra mail servers, CVE-2024-45519, has been exploited by attackers through phishing emails. One day after a technical analysis was published, attackers launched remote code execution attacks.
With a CVSS score of 10.0, this vulnerability threatens organizations using outdated Zimbra systems. Remote attackers can exploit it to execute commands, compromising systems and signaling a pressing need for immediate security updates.
Source Material: Proofpoint
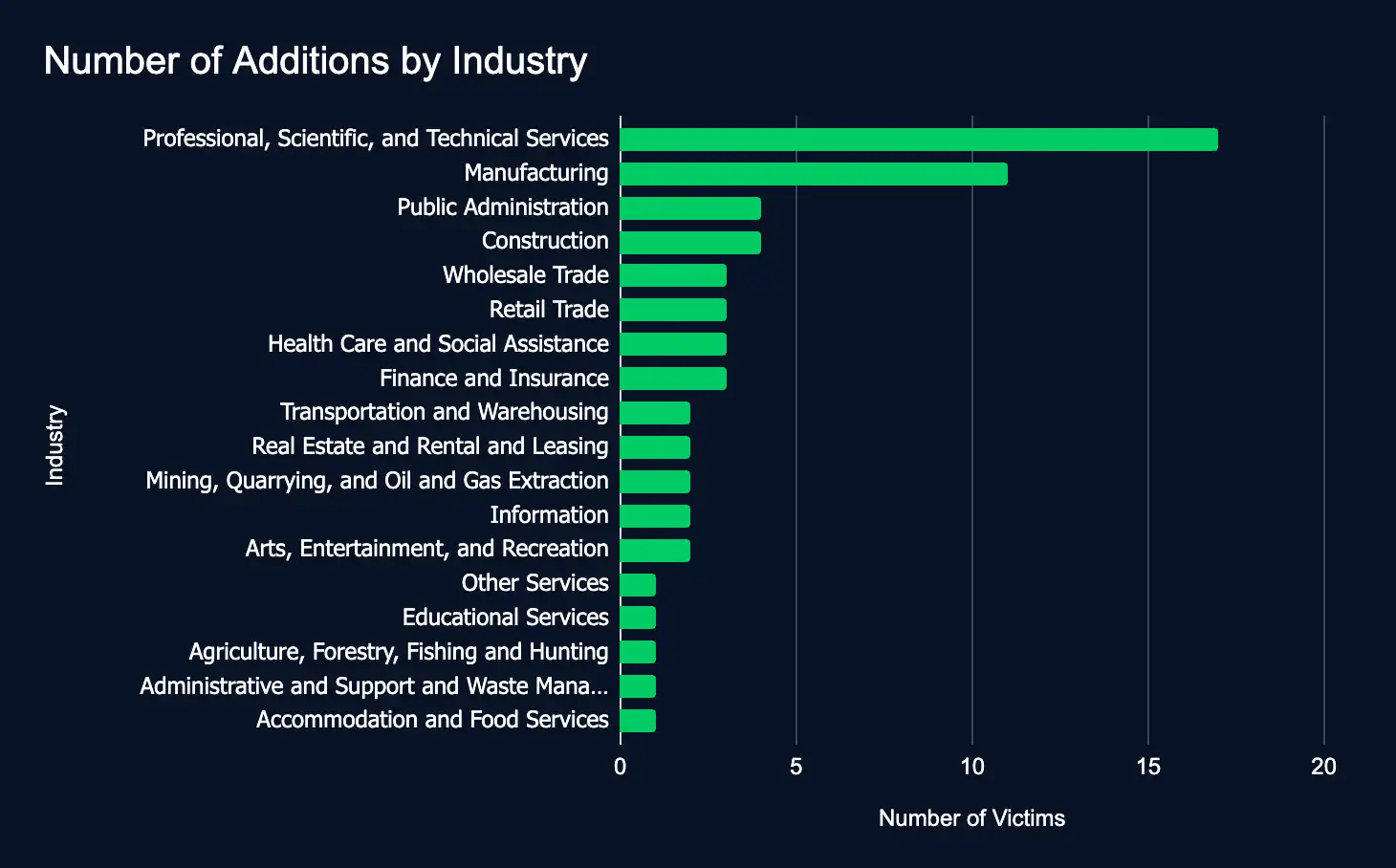
Leak Sites: 64 Firms Listed, Professional Services Tops the List
The Rundown
Between September 30th and October 6th, 64 organizations across 18 industries and 16 countries were listed on ransomware and data extortion leak sites, with the professional, scientific, and technical services industry being listed the most.
This trend highlights the increasing vulnerability of various sectors to cyberattacks, particularly in manufacturing, healthcare, and professional services, and emphasizes the urgent need for robust cybersecurity measures to protect sensitive data.
CISA Adds Synacor, Microsoft, and Qualcomm Vulnerabilities to Exploited List
The Rundown
Four critical vulnerabilities, including one with a CVSS score of 10, were added to CISA’s Known Exploited Vulnerabilities catalog in the first week of October 2024. If left unpatched, these vulnerabilities expose widely used platforms like Zimbra, Microsoft Windows, and Qualcomm chipsets to attacks.
These vulnerabilities highlight the increasing danger of remote code execution and data theft, particularly in essential communication and device management platforms. Including these exploits in phishing attacks and commercial spyware underscores the urgent need for mitigation to prevent widespread damage.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share